SpecterOps
@SpecterOps
Followers
39K
Following
2K
Media
1K
Statuses
3K
Creators of BloodHound | Experts in Adversary Tradecraft | Leaders in Identity Attack Path Management
Joined January 2017
BloodHound v8.0 is here! 🎉. This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID. Read more from @JustinKohler10: 🧵: 1/7
5
61
152
Check out this blog post from @Jonas_B_K and learn more about one of the more prevalent AD CS attack paths. 👉 🧵: 4/4.
specterops.io
Learn about ADCS attack paths in BloodHound, focusing on ESC1 domain escalation. Find out how to detect and prevent potential Active Directory abuses.
0
0
1
Learn more about vulnerabilities in AD CS - check out @harmj0y's blog post 👉 🧵: 3/4.
specterops.io
Uncover the overlooked vulnerabilities in Active Directory Certificate Services. Read our in-depth whitepaper and learn about essential auditing tools.
1
1
4
RT @PardonMyTake: Tuesday night max woke Big Cat up with a flashlight at 2am because he thought we were going to get sued. @forthepeople ht….
0
13
0
Happy #BloodHoundBasics day from @sec_distilled!. Unsure what Active Directory Certificate Services (AD CS) Escalation (ESC) Attack Paths are? These depend heavily on certificate template configurations that may lead to the abuse of any principal in your forest. 🧵: 1/4
1
5
16
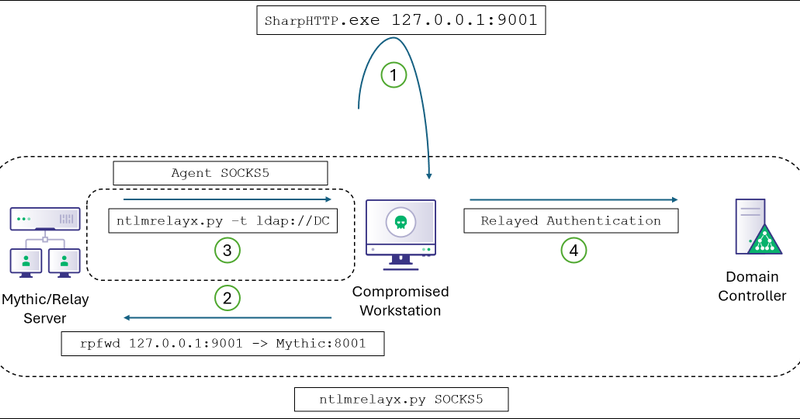
Trying to fly under EDR's radar?. @_logangoins explains how to use HTTP-to-LDAP relay attacks to execute tooling completely off-host through the C2 payload context. Perfect for when you need LDAP access but want to avoid being caught stealing creds.
specterops.io
TL;DR When operating out of a ceded access or phishing payload with no credential material, you can use low-privilege HTTP authentication from the current user context to perform a proxied relay to...
2
70
201
Mythic's browser scripting lets operators customize data analysis beyond raw output. Alexander DeMine shows how smart agent design + structured responses transform the operator experience. ⬇️
specterops.io
Mythic's browser scripting is a powerful feature enabling operators to turn raw text data into actionable intelligence for cyber operations.
0
17
46
New blog post just dropped!. West Shepherd breaks down extending the Mythic Poseidon agent for ARM64 Dylib injection on Apple Silicon. Details include:. ✅ Shellcode construction.✅ Memory allocation .✅ Runtime patching.✅ Thread creation. Read more ⤵️
specterops.io
This post details how the Mythic Poseidon agent was extended to support ARM64 Dylib injection on Apple Silicon
3
34
95
Are you leveraging Mythic's BrowserScript? @its_a_feature_ shows how it transforms plain outputs into interactive tables, buttons, & links, dramatically improving your operational efficiency!. 👀:
0
3
17
Join our webinar, happening next Thursday and get a full break down of the report from authors @jaredcatkinson, @AndrewChiles, and @elad_shamir. Register at
0
1
2
RT @helpnetsecurity: LudusHound: Open-source tool brings BloodHound data to life - - @SpecterOps @GitHub #GitHub #O….
0
11
0
WATCH: @JustinKohler10 & @_wald0 recently joined @_JohnHammond to talk all about BloodHound v8.0 and OpenGraph. Learn how with these updates you can now map attack paths across your entire tech stack. 👉
0
4
23
Hosts running the WebClient service are prime targets for NTLM relay attacks, and it may be possible to start the service remotely as a low-privileged user. @0xthirteen breaks down the service startup mechanics, plus the protocols and technologies.
specterops.io
A walkthrough to answer the question: "Can you start the WebClient service remotely as a low privileged user?"
0
58
170
You can now map attack paths throughout your entire tech stack with BloodHound OpenGraph. @JustinKohler10, @jaredcatkinson, @_wald0 & @StephenHinck chatted about this & other new features in BloodHound v8.0 during our recent webinar. 👀 Watch on demand:
0
3
14
BloodHound OpenGraph allows you to map attack paths across ANY platform. @jaredcatkinson spoke with @DarkReading during #BHUSA about how you can now connect the dots between Active Directory, GitHub repositories, and other sensitive assets. 👀:
1
6
22
New #BloodHoundBasics post c/o @ScoubiMtl!. BloodHound v8 introduced Table View. It is the default view when the query returns only nodes. But did you know ANY query result can be viewed as table & exported?. Simply click on 'Layout' at the bottom of the screen & select 'Table'!
0
4
7
Manual recon commands eating up your time? 🕐. @atomiczsec breaks down how Mythic Eventing automates those repetitive reconnaissance tasks during RTOs, complete with starter YAML scripts you can customize.
specterops.io
Mythic Eventing automates repetitive tasks during red team operations (RTO). Gavin Kramer documents this eventing system and provides a collection of starter YAML scripts for the community.
0
22
78
See how Mythic leverages MITRE ATT&CK to map your agents' capabilities & track techniques you've executed in your operations. Watch the tutorial from @its_a_feature_ 👉
0
10
57
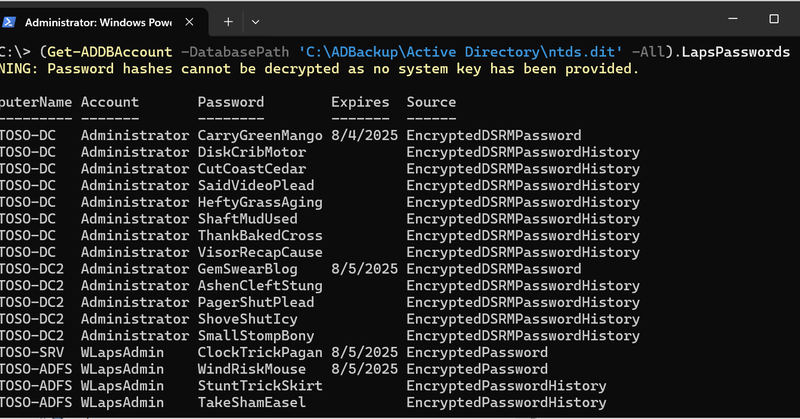
The DSInternals PowerShell module just got an upgrade! 🔥. Updates include:.✅ Golden dMSA Attack.✅ Full LAPS support.✅ Trust password & BitLocker recovery key extraction.✅ Read-only domain controller database compatibility. Read more from @MGrafnetter.
specterops.io
Discover the latest enhancements to the DSInternals PowerShell module, including the Golden dMSA Attack and support for LAPS, trust passwords, or BitLocker recovery keys.
0
40
105