Steven
@0xthirteen
Followers
3K
Following
1K
Media
6
Statuses
507
Working to become smarter everyday. Adversary Simulation Service Architect @SpecterOps.
Joined December 2011
RT @_logangoins: I Just documented a cool way to authenticate proxied tooling to LDAP in an AD environment using C2 payload auth context, w….
specterops.io
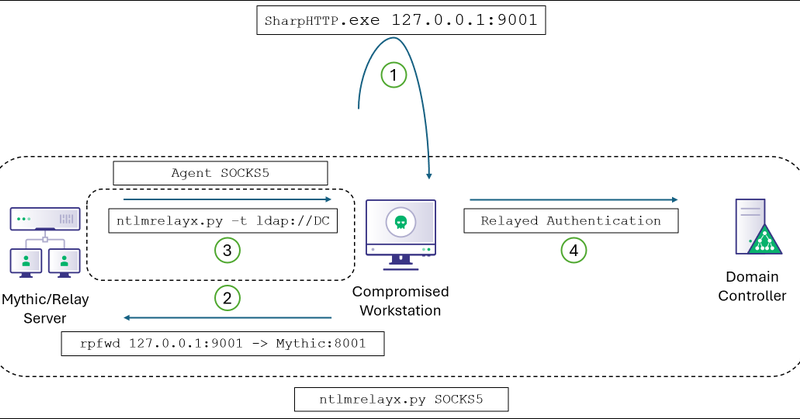
TL;DR When operating out of a ceded access or phishing payload with no credential material, you can use low-privilege HTTP authentication from the current user context to perform a proxied relay to...
0
69
0
RT @SpecterOps: New blog post just dropped!. West Shepherd breaks down extending the Mythic Poseidon agent for ARM64 Dylib injection on App….
specterops.io
This post details how the Mythic Poseidon agent was extended to support ARM64 Dylib injection on Apple Silicon
0
31
0
I wanted to find out if you could start the WebClient service remotely, so I ended up digging into it
specterops.io
A walkthrough to answer the question: "Can you start the WebClient service remotely as a low privileged user?"
1
55
111
RT @GrayHatKiller: Wrote a BOF that extracts access tokens from .tbres files by decrypting DPAPI blobs in the current user context, this to….
github.com
Contribute to grayhatkiller/wambam-bof development by creating an account on GitHub.
0
26
0
RT @JonnyJohnson_: Have you ever wondered if there was a way to deploy a "Remote EDR"? Today I'm excited to share research I've been workin….
0
127
0
RT @M_alphaaa: I'm finally releasing a project that I've been working on for a little while now. Here's Boflink, a linker for Beacon Object….
blog.cybershenanigans.space
Intro This is a blog post written for a project I recently released. The source code for it can be found here on Github. Background The design of Cobalt Strike’s Beacon Object Files is rather unique...
0
66
0
RT @AndrewOliveau: RemoteMonologue - A Windows credential harvesting attack that leverages the Interactive User RunAs key and coerces NTLM….
ibm.com
The IBM X-Force Red team covers the fundamentals of COM and DCOM, dives into the RunAs setting and why authentication coercions are impactful and introduces a new credential harvesting tool.
0
178
0
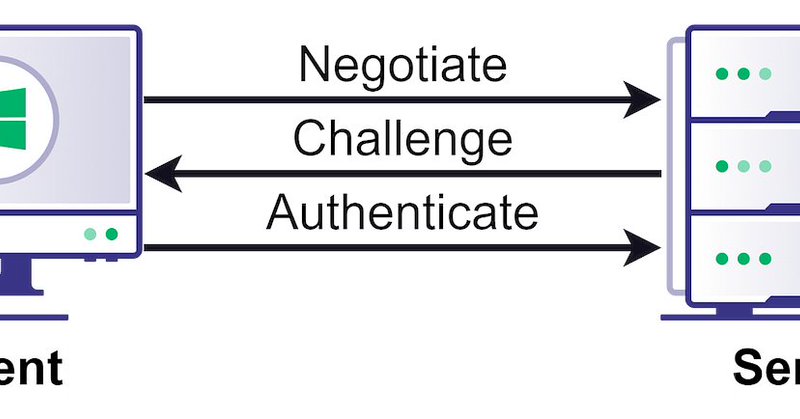
RT @elad_shamir: NTLM relay is still a major threat and is now even easier to abuse. We just added new NTLM relay edges to BloodHound to he….
specterops.io
NTLM relay attacks have been around for a long time. While many security practitioners think NTLM relay is a solved problem, or at least a not-so-severe one, it is, in fact, alive and kicking and...
0
110
0
RT @hotnops: A new fun way to set shadow credentials.
posts.specterops.io
This is part one in a two (maybe three…) part series regarding attacker tradecraft around the syncing mechanics between Active Directory…
0
51
0
I’ve always thought Seatbelt was a great situational awareness tool, I created a python implementation of it. Due to the nature of how I expect it to run, it only implements the remote modules, but I hope someone finds it useful.
github.com
Python implementation of GhostPack's Seatbelt situational awareness tool - 0xthirteen/Carseat
3
77
166
RT @Tw1sm: New blog up to cover manual AD CS enumeration using ldapsearch and the new release of bofhound 🔍 .
posts.specterops.io
TL;DR: BOFHound can now parse Active Directory Certificate Services (AD CS) objects, manually queried from LDAP, for review and attack path…
0
59
0
Looking around I hadn’t seen any python tools to interact with the registry that doesn’t use remote registry. So I made one that implements all StdRegProv methods
github.com
Python tool to interact with WMI StdRegProv. Contribute to 0xthirteen/reg_snake development by creating an account on GitHub.
1
32
67
RT @_xpn_: New tool published which is proving to be useful. Cred1py allows execution of the CRED-1 SCCM attack published by @Raiona_ZA ove….
github.com
A Python POC for CRED1 over SOCKS5. Contribute to SpecterOps/cred1py development by creating an account on GitHub.
0
162
0
RT @FKasler: Dropping another "Phishing School" post. Learn how to select and categorize domains for phishing so you don't get blocked by r….
posts.specterops.io
How to Give your Phishing Domains a Reputation Boost
0
21
0
RT @jaredcatkinson: My On Detection series is back! In this edition I explore how the same behavior (operation chain) can be implemented us….
posts.specterops.io
At Shmoocon 2015, Will Schroeder (Harmj0y) gave a talk titled “I Hunt Sys Admins,” describing how attackers can hunt (or find the location of) system administrators throughout the network. The talk…
0
52
0
RT @jsecurity101: Without further ado - here is EtwInspector! . This is a C++ tool to help users interact with ETW providers. This tool sup….
github.com
Contribute to jonny-jhnson/ETWInspector development by creating an account on GitHub.
0
126
0
RT @FKasler: Want to be better at phishing? I'm dropping the first two blogs in my "Phishing School" series today. The whole series is desi….
posts.specterops.io
I’ll Make You Great at Phishing or Your Money Back
0
36
0
RT @synzack21: Curious about Intune's new EPM feature? So were we. In this blog @subat0mik and I explore the internals of EPM and share som….
posts.specterops.io
Written by Zach Stein & Duane Michael
0
40
0