Elad Shamir
@elad_shamir
Followers
5K
Following
327
Media
4
Statuses
112
Check out my latest research "Wagging the Dog: Abusing Resource-Based Constrained Delegation to Attack Active Directory". New attack techniques and live 0days inside. MSRC’s response: "this is not an issue which will be addressed via a security update".
shenaniganslabs.io
Back in March 2018, I embarked on an arguably pointless crusade to prove that the TrustedToAuthForDelegation attribute was meaningless, and that “protocol transition” can be achieved without it. I...
17
346
597
RT @0xthirteen: I wanted to find out if you could start the WebClient service remotely, so I ended up digging into it .
specterops.io
A walkthrough to answer the question: "Can you start the WebClient service remotely as a low privileged user?"
0
55
0
RT @SpecterOps: Hosts running the WebClient service are prime targets for NTLM relay attacks, and it may be possible to start the service r….
specterops.io
A walkthrough to answer the question: "Can you start the WebClient service remotely as a low privileged user?"
0
58
0
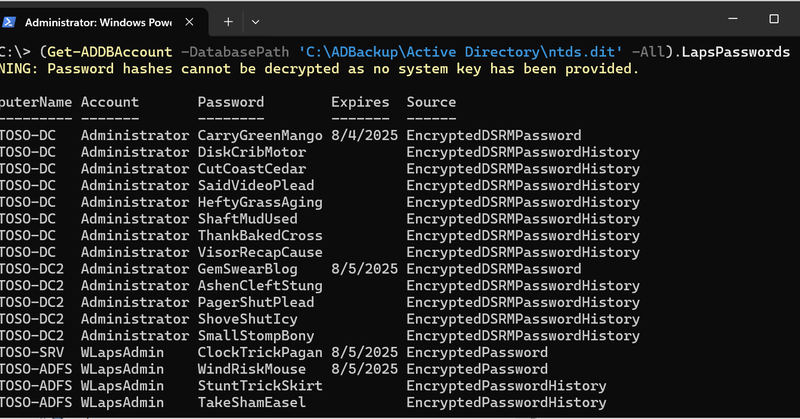
RT @SpecterOps: The DSInternals PowerShell module just got an upgrade! 🔥. Updates include:.✅ Golden dMSA Attack.✅ Full LAPS support.✅ Trust….
specterops.io
Discover the latest enhancements to the DSInternals PowerShell module, including the Golden dMSA Attack and support for LAPS, trust passwords, or BitLocker recovery keys.
0
40
0
RT @SpecterOps: We are breaking down our State of Attack Path Management report. Join @jaredcatkinson, @AndrewChiles, & @elad_shamir as th….
0
6
0
RT @SpecterOps: The AD CS security landscape keeps evolving, and so does our tooling. 🛠️. @bytewreck drops info on Certify 2.0, including a….
specterops.io
Certify 2.0 features a suite of new capabilities and usability enhancements. This blogpost introduces changes and features additions.
0
97
0
RT @SpecterOps: Entra Connect sync accounts can be exploited to hijack device userCertificate properties, enabling device impersonation and….
specterops.io
How Entra Connect and Intune can be abused via userCertificate hijacking to bypass conditional access and compromise hybrid domains
0
59
0
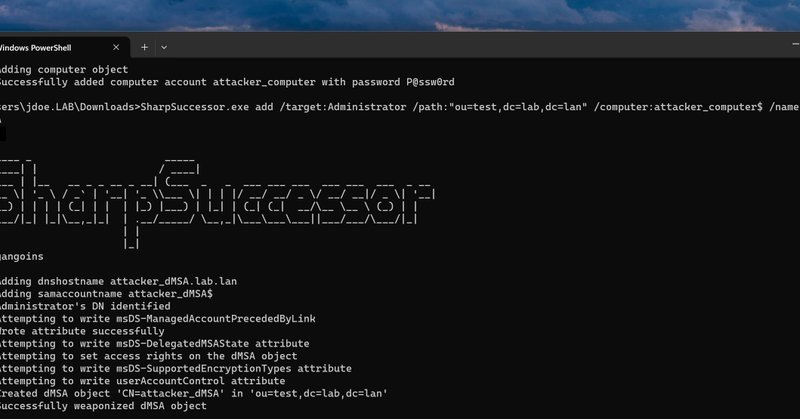
RT @_logangoins: I'm super happy to announce an operationally weaponized version of @YuG0rd's BadSuccessor in .NET format! With a minimum o….
github.com
SharpSuccessor is a .NET Proof of Concept (POC) for fully weaponizing Yuval Gordon’s (@YuG0rd) BadSuccessor attack from Akamai. - logangoins/SharpSuccessor
0
170
0
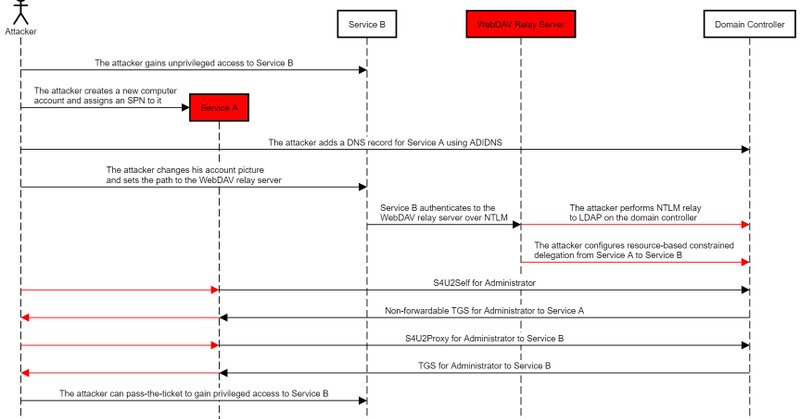
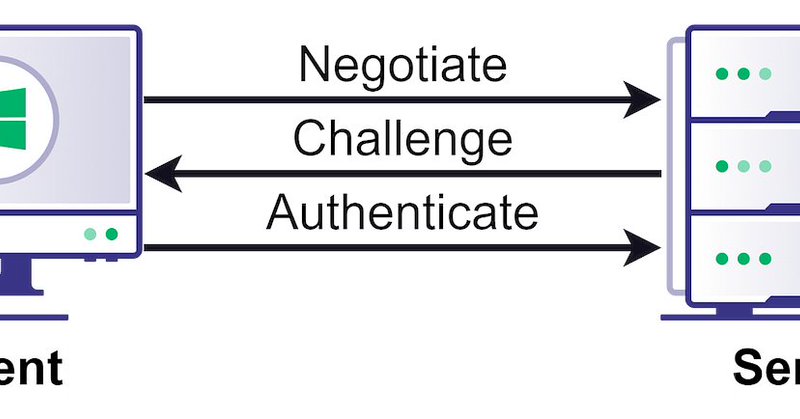
NTLM relay is still a major threat and is now even easier to abuse. We just added new NTLM relay edges to BloodHound to help defenders fix and attackers think in graphs. Read my detailed post - the most comprehensive guide on NTLM relay & the new edges:.
specterops.io
NTLM relay attacks have been around for a long time. While many security practitioners think NTLM relay is a solved problem, or at least a not-so-severe one, it is, in fact, alive and kicking and...
6
110
259
RT @SpecterOps: Think NTLM relay is a solved problem? Think again. Relay attacks are more complicated than many people realize. Check out….
specterops.io
NTLM relay attacks have been around for a long time. While many security practitioners think NTLM relay is a solved problem, or at least a not-so-severe one, it is, in fact, alive and kicking and...
0
94
0
RT @__mez0__: Attended this remotely for Identity-Driven Offensive Tradecraft from @elad_shamir. 10/10 course, the @SpecterOps team had ins….
0
4
0
RT @SpecterOps: The CFP for #SOCON2025 is now open! 🙌. If you have an idea for a talk delving into the complexities of identifying, executi….
0
14
0
RT @_Mayyhem: If you liked RTO from @SpecterOps or have attack/defense experience, check out the continuation, Identity-driven Offensive Tr….
0
7
0
RT @SpecterOps: New blog post just dropped! 😎. In this installment of our blog series on Identity-Driven Offensive Tradecraft, @elad_shamir….
0
60
0
RT @jaredcatkinson: Yesterday, I wrote a thread describing the ESXi vulnerability and how you can use BloodHound's Attack Path Management a….
0
13
0
RT @SpecterOps: Kicking this week off with a new blog post from @elad_shamir introducing our new Identity-Driven Offensive Tradecraft train….
0
21
0
RT @jaredcatkinson: My On Detection series continues. In part 14 I look at a “special” subset of operations that require a bit more detail….
0
23
0
RT @jaredcatkinson: I've released another post in my On Detection series. This edition builds on the previous post where I introduced "exec….
posts.specterops.io
In my previous post, I explored the idea that different tools can implement the same operation chain (behavior) in various ways. I referred to these various ways as execution modalities. In that…
0
28
0
RT @jaredcatkinson: My On Detection series is back! In this edition I explore how the same behavior (operation chain) can be implemented us….
posts.specterops.io
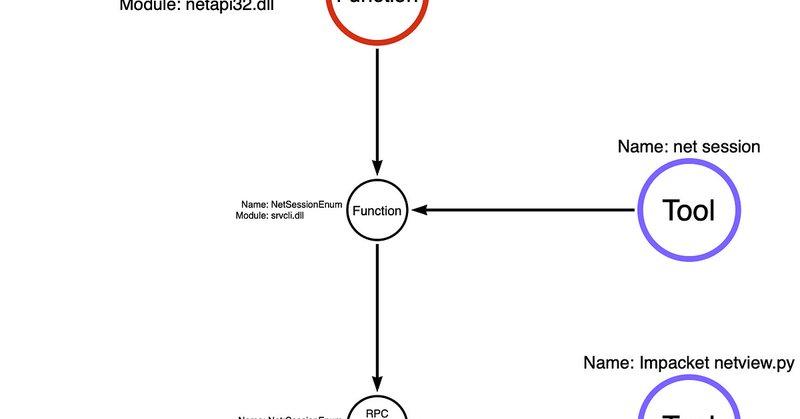
At Shmoocon 2015, Will Schroeder (Harmj0y) gave a talk titled “I Hunt Sys Admins,” describing how attackers can hunt (or find the location of) system administrators throughout the network. The talk…
0
52
0
RT @harmj0y: It's a big day- @tifkin_, @0xdab0, and I are proud to announce that Nemesis 1.0.0 has landed! We have a ton of awesome new fea….
github.com
An offensive data enrichment pipeline. Contribute to SpecterOps/Nemesis development by creating an account on GitHub.
0
62
0