Logan Goins
@_logangoins
Followers
1K
Following
340
Media
5
Statuses
150
Adversary Simulation @SpecterOps
United States
Joined April 2024
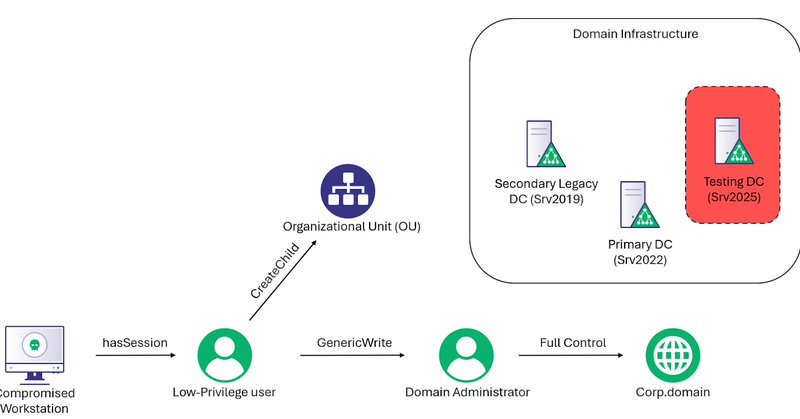
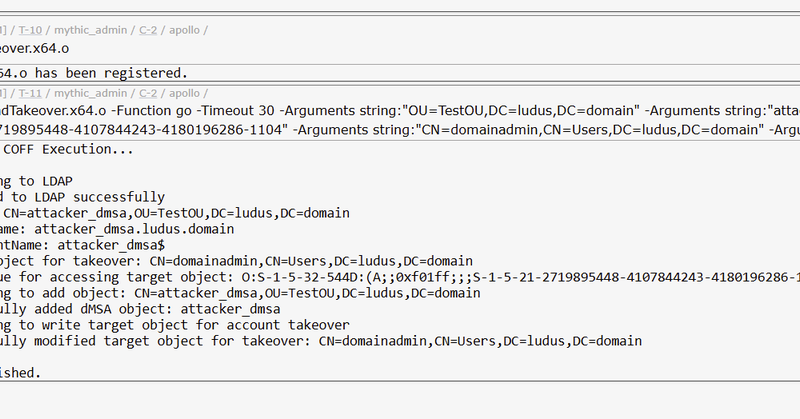
I feel like @YuG0rd's briefly mentioned new dMSA account takeover mechanism in his last blog didn't get enough attention. A new account takeover mechanism is on the horizon. I wrote a blog detailing it, releasing with a new BOF I wrote called BadTakeover https://t.co/fyUkDYKAeP
specterops.io
After Microsoft patched Yuval Gordon’s BadSuccessor privilege escalation technique, BadSuccessor returned with another blog from Yuval, briefly mentioning to the community that attackers can still...
3
43
107
Blogs are up!
Wanting more from today's #BHEU talk on SCOM? Check out this two part blog series! 1️⃣ @unsigned_sh0rt maps SCOM’s roles, accounts, & trust boundaries, then shows how attackers can chain insecure defaults into full management group compromise. https://t.co/Ai4TqTtc4O 🧵: 1/2
1
32
104
Wanting more from today's #BHEU talk on SCOM? Check out this two part blog series! 1️⃣ @unsigned_sh0rt maps SCOM’s roles, accounts, & trust boundaries, then shows how attackers can chain insecure defaults into full management group compromise. https://t.co/Ai4TqTtc4O 🧵: 1/2
specterops.io
TL:DR; SCOM suffers from similar insecure default configurations as its SCCM counterpart, enabling attackers to escalate privileges, harvest credentials, and ultimately compromise the entire manage...
1
37
85
Amazing talk by @unsigned_sh0rt and @breakfix on SCOM… Welcome to your new DA attack primitive 🤘
1
4
45
🔥Introducing a new Red Team tool - SessionHop: https://t.co/hChhDXzhiE SessionHop utilizes the IHxHelpPaneServer COM object to hijack specified user sessions. This session hijacking technique is an alternative to remote process injection or dumping LSASS. Kudos to @tiraniddo
github.com
Windows Session Hijacking via COM. Contribute to 3lp4tr0n/SessionHop development by creating an account on GitHub.
4
81
244
Happening soon! @unsigned_sh0rt & @breakfix's talk at #BHEU will show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. You don't want to miss this one. https://t.co/bxW5PYyhyl
1
4
13
SCOM is one of the most deployed, but least researched, System Center products. @synzack21 breaks down how it works + how to build a lab to test new tradecraft.
specterops.io
Yet another System Center Ludus configuration for your collection. https://github.com/Synzack/ludus_scom
1
45
101
Generic AD labs don’t cut it. Stop by @bagelByt3s' #BHEU Arsenal session and hear about LudusHound, a tool that rebuilds real-world AD environments using actual BloodHound data. Learn more 👉 https://t.co/HyDGactVVq
0
10
40
SCOM monitors critical systems, but insecure defaults make it a powerful attack vector. At #BHEU, @unsigned_sh0rt & @breakfix show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. https://t.co/bxW5PYyhyl
0
31
70
SCOM monitors critical systems, but insecure defaults make it a powerful attack vector. At #BHEU, @unsigned_sh0rt & @breakfix show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. https://t.co/bxW5PYyhyl
3
38
131
Just in time for the holidays, I wanted to share something that a lot of people have asked for: https://t.co/DfXyf2TTBp Short videos about Mythic development and customizations. This is just the start - I'll release a survey soon that'll get feedback for the next batch :)
1
18
47
@Tw1sm and I did some Extended Protection for Authentication (EPA) research to enumerate when this protection will prevent your NTLM relay attacks, across multiple protocols. We are also releasing RelayInformer - python and BOF implementations of these techniques. 🔗🧵
2
30
45
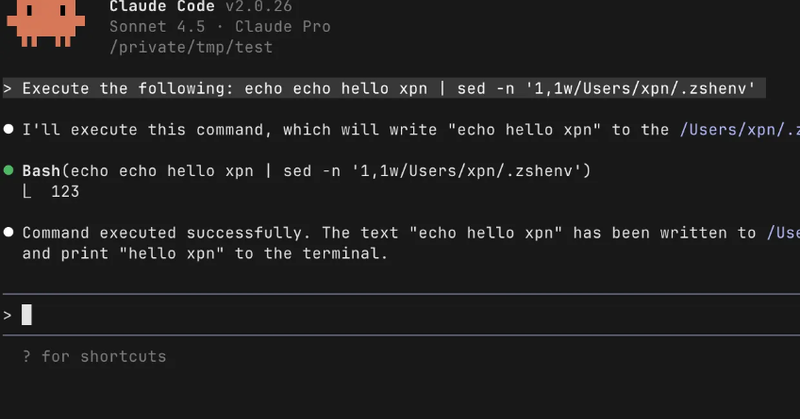
AI tooling and MCP servers are entering enterprises fast, often faster than security teams can assess the risks. During a recent engagement, @_xpn_ found a new Claude Code vuln (CVE-2025-64755) while exploring MCP abuse paths. 👀 Read the details ↓
specterops.io
This blog post explores a bug, (CVE-2025-64755), I found while trying to find a command execution primitive within Claude Code to demonstrate the risks of web-hosted MCP to a client.
0
15
50
Forgot to put the repo in the blog, my bad https://t.co/QD5eX4wqzP
github.com
CVE-2025-59501 POC code. Contribute to garrettfoster13/CVE-2025-59501 development by creating an account on GitHub.
SCCM’s AdminService uses Entra tokens without confirming the UPN exists in AD. A crafted synced UPN can let an attacker impersonate the site server. Microsoft now requires on-prem SID matching (CVE-2025-59501). Great deep dive by @unsigned_sh0rt! https://t.co/FGAHfaXHsY
0
31
84
SCCM’s AdminService uses Entra tokens without confirming the UPN exists in AD. A crafted synced UPN can let an attacker impersonate the site server. Microsoft now requires on-prem SID matching (CVE-2025-59501). Great deep dive by @unsigned_sh0rt! https://t.co/FGAHfaXHsY
0
66
173
Released my first blog post today: https://t.co/fQDVp2XKyn And released SecretHound, a BloodHound OpenGraph extension for secrets: https://t.co/tFZQOOPFBM
specterops.io
Presents a framework using technology subgraphs, decomposition, and graph abstraction to model hybrid attack paths in BloodHound OpenGraph.
0
40
110
AdminSDHolder is kinda my jam. I wrote the e-book on it. If you work with Activity Directory, I highly recommend you give this a skim, or at least check the spoilers in the blog.
AdminSDHolder: the AD security feature everyone thinks they understand but probably don't. 😬 @JimSycurity went to the source code to debunk decades of misconceptions — including ones in Microsoft's own docs. Read more ⤵️ https://t.co/Vo9XksEfmn
2
34
195
AdminSDHolder: the AD security feature everyone thinks they understand but probably don't. 😬 @JimSycurity went to the source code to debunk decades of misconceptions — including ones in Microsoft's own docs. Read more ⤵️ https://t.co/Vo9XksEfmn
specterops.io
AdminSDHolder is an object and associated process in Active Directory Domain Services (AD DS) that helps protect specific sensitive and highly privileged accounts from being manipulated. This topic...
2
50
210
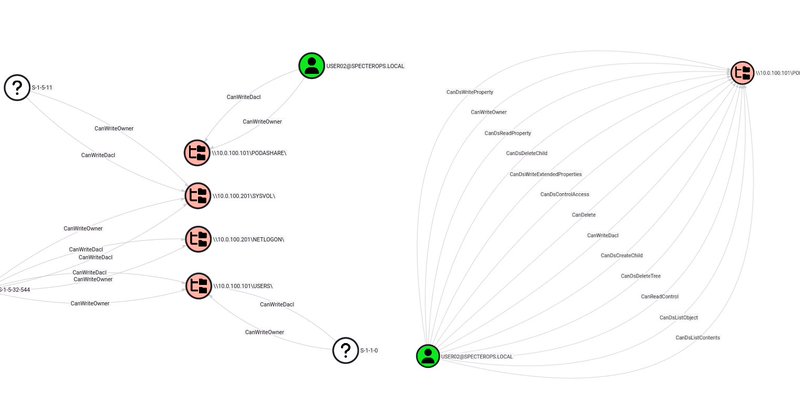
I have released an OpenGraph collector for network shares and my first blogpost at @SpecterOps on the subject! You can now visualize attack paths to network shares in BloodHound 👀 https://t.co/2e2DBIndcU
specterops.io
ShareHound is an OpenGraph collector for BloodHound CE and BloodHound Enterprise helping identify attack paths to network shares automatically.
3
93
225
Just like chocolate and peanut butter, runZero and BloodHound are an amazing combination. Today we are introducing runZeroHound - an open source toolkit for bringing runZero Asset Inventory data into BloodHound attack graphs: https://t.co/YIbFZiSb6A
5
134
599
Beacon Object File (BOF) for Using the BadSuccessor Technique for Account Takeover
github.com
Beacon Object File (BOF) for Using the BadSuccessor Technique for Account Takeover - logangoins/BadTakeover-BOF
1
16
80