Jared Atkinson
@jaredcatkinson
Followers
10K
Following
8K
Media
283
Statuses
7K
| CTO @specterops | Host @dcpthepodcast | Ex PowerShell MVP | USAF Vet | FC Bayern Supporter | Language Learner 🇳🇴 🇮🇹 🇧🇷 |
Las Vegas, NV
Joined July 2013
💡 WHAT IS PURPLE TEAMING AT SPECTEROPS? SpecterOps recently introduced our Purple Team service offering, but what is it? We define it as "the evaluation of security control efficacy through atomic testing using deliberately selected test cases." https://t.co/SSwnzSxUGK
specterops.io
SpecterOps announced new Purple Team Assessment Services, a two-week assessment that evaluates how well an organization’s security controls can detect and prevent common attack techniques...
2
31
91
Ever wonder why we call them "Cmdlets" in PowerShell instead of just "Commands"? https://t.co/PTxB02yXmY
#PowerShell
jsnover.com
I’ve spent a lot of time, and acquired a lot of scar tissue, in this industry, and if there is one thing I’ve learned, it’s that most people are terrified of looking different. People hug the cente…
4
24
94
We’re excited to announce Kevin Mandia as the keynote speaker for #SOCON2026! 🎉 His keynote will focus on how the threat landscape has evolved in the face of modern adversary tradecraft. Secure your spot ➡️ https://t.co/DnlUAv9tRY
0
3
14
2️⃣ Next, @Breakfix dives into the SCOM agent. This post uncovers how RunAs creds reach endpoints, how they’re recovered off-host, and how rogue enrollment exposes sensitive data. Plus: introducing SharpSCOM for automated RunAs recovery. https://t.co/1KS5VVcxWc 🧵: 2/2
specterops.io
We found that SCOM RunAs credentials could be obtained on-host and also off-host in certain configurations and wrote a tool to help automate their recovery. To skip straight to the tool, go here...
0
16
33
Wanting more from today's #BHEU talk on SCOM? Check out this two part blog series! 1️⃣ @unsigned_sh0rt maps SCOM’s roles, accounts, & trust boundaries, then shows how attackers can chain insecure defaults into full management group compromise. https://t.co/Ai4TqTtc4O 🧵: 1/2
specterops.io
TL:DR; SCOM suffers from similar insecure default configurations as its SCCM counterpart, enabling attackers to escalate privileges, harvest credentials, and ultimately compromise the entire manage...
1
48
116
INTRODUCING THE UNITY BAG Designed by Alexandra Gucci Zarini in honor and support of FOSTERING THE FUTURE. The Unity Bag carries a quiet message of hope and shared vision: that we must come together �� in unity for our children — to protect and uplift them toward a brighter
304
462
3K
Attackers can bypass identity controls and pivot from on-prem to cloud with ease. Join @JustinKohler10 & @jaredcatkinson at #GartnerIAM as they break down recent breaches and how Identity Attack Path Management helps teams eliminate exploitable paths. https://t.co/FrqCKBnrcB
0
2
9
Network shares are an overlooked attack surface. Misconfigs & permissive rights can enable lateral movement, data theft, & escalation. Join @podalirius_ for a ShareHound demo → discover shares, export to OpenGraph, & run Cypher analysis. Register 👉 https://t.co/uOuKC1N3Dx
0
7
46
How does PingOne’s architecture shape real attacker movement? In our new #KnowYourAdversary, @_wald0 & @pingidentity’s Bjorn Aannestad discuss RBAC, environment design, & cross-platform risks. https://t.co/K8WsxzQLx0 Visit booth #736 at #GartnerIAM to learn about PingOneHound.
0
1
5
#MDE custom collection is finally in public preview! It's a centrally managed solution to improve visibility and detection opportunities. We're releasing a management tool and rule repository in YAML format to share new rules with the community. https://t.co/kxit8fFjhU
5
45
172
Identity is the new battleground. @jaredcatkinson talks with @thecyberwire about how attackers chain misconfigurations and identity relationships to reach critical assets, and how Attack Path Management stops them. 🎧: https://t.co/3yGAg4ZSqx
0
2
11
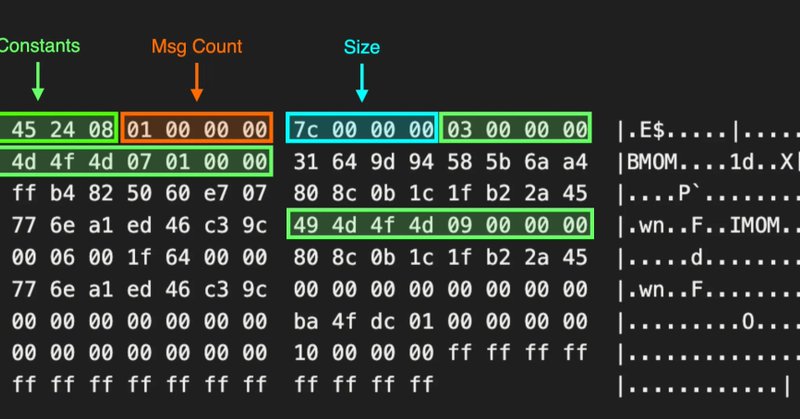
SCCM’s AdminService uses Entra tokens without confirming the UPN exists in AD. A crafted synced UPN can let an attacker impersonate the site server. Microsoft now requires on-prem SID matching (CVE-2025-59501). Great deep dive by @unsigned_sh0rt! https://t.co/FGAHfaXHsY
0
67
173
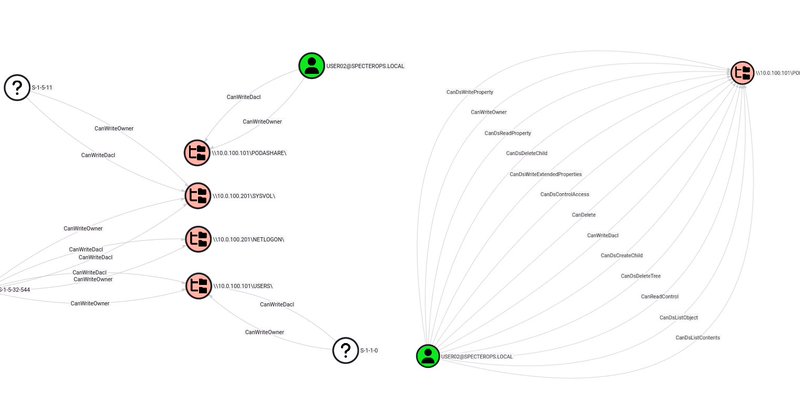
ShareHound: An OpenGraph Collector for Network Shares - @podalirius_
https://t.co/A3bLg9Pxca
specterops.io
ShareHound is an OpenGraph collector for BloodHound CE and BloodHound Enterprise helping identify attack paths to network shares automatically.
1
17
62
Modern attack surfaces are chaos. Let’s make sense of them. Join the runZero Hour TOMORROW as @jaredcatkinson joins @runZeroInc's @todb, Rob King, & @hdmoore in exploring how graph-based analysis transforms defense. https://t.co/PiUrdwonIV
0
2
4
Run, don’t walk! 🏃♂️ The #SOCON2026 CFP closes tomorrow! Share your research, your stories, your “aha” moments — before the clock runs out. 📝: https://t.co/0YvPbfVtXc
0
1
4
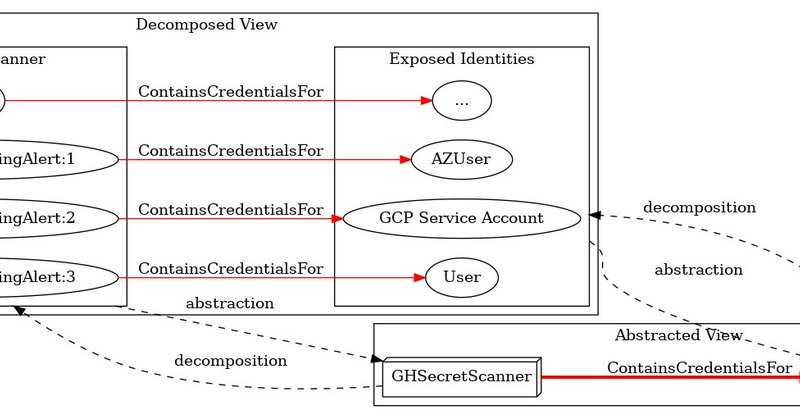
Released my first blog post today: https://t.co/fQDVp2XKyn And released SecretHound, a BloodHound OpenGraph extension for secrets: https://t.co/tFZQOOPFBM
specterops.io
Presents a framework using technology subgraphs, decomposition, and graph abstraction to model hybrid attack paths in BloodHound OpenGraph.
0
40
110
How do you model hybrid attack paths that span GitHub, GCP, Azure, and AD? @c0kernel has released SecretHound, a new BloodHound OpenGraph extension for secrets 🤫 — enabling modeling of “credential watering holes” across tech platforms.
specterops.io
Presents a framework using technology subgraphs, decomposition, and graph abstraction to model hybrid attack paths in BloodHound OpenGraph.
0
14
38
runZero Hour is one week away! Join us on Nov 19: @todb, Rob King, @hdmoore, and @jaredcatkinson (@SpecterOps) break down attacker movement, graph analysis, runZeroHound, and this month’s top vulnerabilities. 👉 Register: https://t.co/5mb8jagJA3
0
1
3
This is (probably) the last time I‘ll nag you with TaskHound. Since my org doesn’t allow me to use memes in our official blogs I finally took the hint and stopped procrastinating. My personal Blog is now live :). https://t.co/Sp2aj2Y0EO (Disclaimer: may contain sarcasm and memes)
2
20
84
AdminSDHolder: the AD security feature everyone thinks they understand but probably don't. 😬 @JimSycurity went to the source code to debunk decades of misconceptions — including ones in Microsoft's own docs. Read more ⤵️ https://t.co/Vo9XksEfmn
specterops.io
AdminSDHolder is an object and associated process in Active Directory Domain Services (AD DS) that helps protect specific sensitive and highly privileged accounts from being manipulated. This topic...
2
51
211
See your network shares the way attackers do. 👀 Meet ShareHound, an OpenGraph collector for BloodHound CE & Enterprise that reveals share-level attack paths at scale. @podalirius_ unpacks all the details in our latest blog post.
specterops.io
ShareHound is an OpenGraph collector for BloodHound CE and BloodHound Enterprise helping identify attack paths to network shares automatically.
0
47
187
This is a really exciting extension of the BloodHound attack graph. I view this as a way to increase the resolution with which organizations can see/assess their exposure to ransomware attacks. In a ransomware incident, the point of initial access is relatively random. With
I have released an OpenGraph collector for network shares and my first blogpost at @SpecterOps on the subject! You can now visualize attack paths to network shares in BloodHound 👀 https://t.co/2e2DBIndcU
1
2
20