📔 Michael Grafnetter
@MGrafnetter
Followers
3K
Following
251
Media
67
Statuses
357
Principal Security Researcher @SpecterOps, Microsoft MVP Identity & Access
Prague, Czech Republic
Joined October 2015
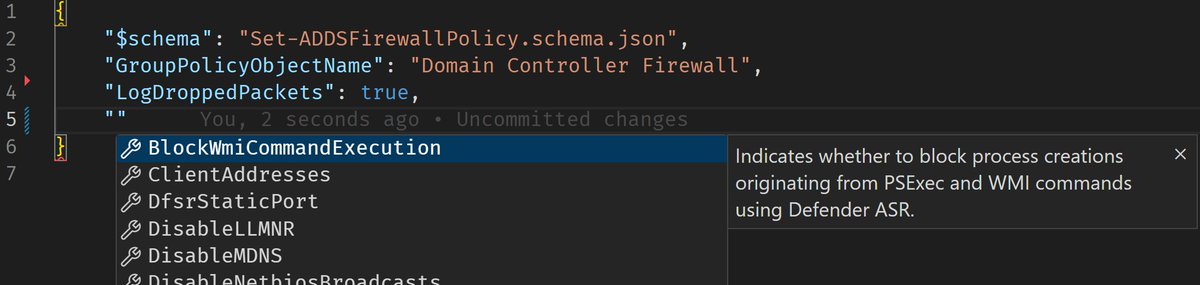
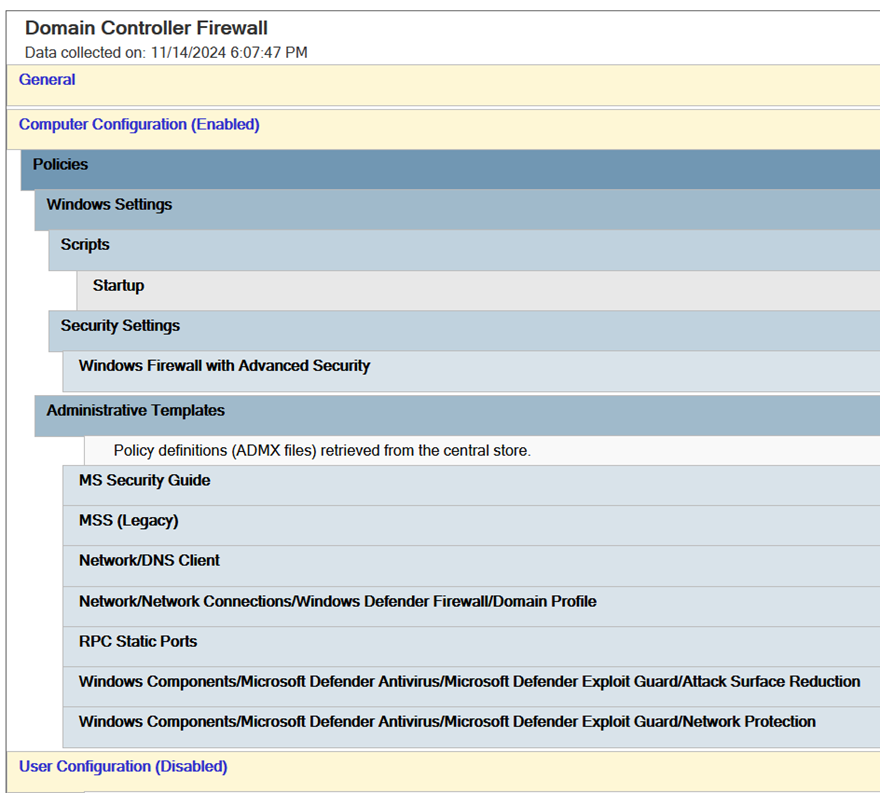
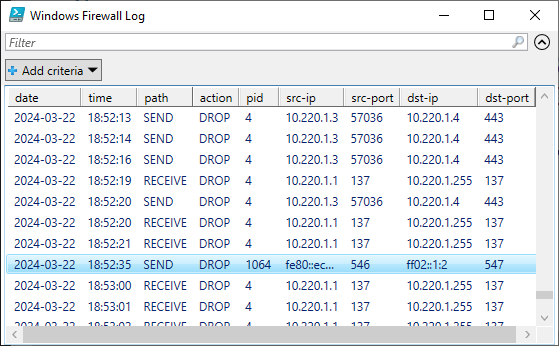
Together with @pavelfor, we have created the ultimate guide and tooling for configuring host-based firewalls on #ActiveDirectory domain controllers in enterprise environments. Blocks most remote command execution and authentication coercion techniques.
7
70
233
New blog post covering the end-to-end automation of OAuth 2.0 service/daemon application registration in Microsoft Entra ID using PowerShell Graph SDK.
dsinternals.com
Introduction It is best practice to register applications in Entra ID using PowerShell (or another automation tool that utilizes the Microsoft Graph API), rather than adding them manually through...
0
12
51
RT @CQUREAcademy: Here’s a recap from the CyberGen Conference with our expert @MGrafnetter 👀. Michael was there with a workshop on AD secur….
0
1
0
RT @DrAzureAD: My new blog post on getting plaintext gMSA secrets available at Credits to @PyroTek3, @MGrafnetter,….
0
72
0
New Indicator of Compromise (IoC) by the NTLM Relay Attack with Shadow Credentials, thanks to bugs in Impacket, a popular Python implementation. Will probably be fixed in the near future.
dsinternals.com
TL;DR The current implementation of the shadow credentials attack in the Impacket framework, most notably used by the ntlmrelayx.py script, contains multiple bugs, leaving unique signatures on...
1
53
154
#DSInternals 5.0 is out. Supports recovery of BitLocker keys, LAPS passwords, DNS zone files, contact information, organizational structure, and OS versions from #ActiveDirectory ntds.dit files. Includes some performance improvements as well. Examples:
6
71
244
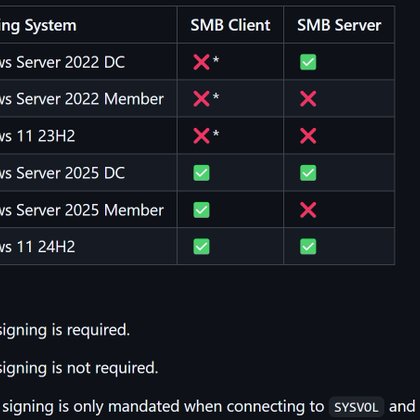
Here is a summary of the changes to SMB signing enforcement defaults in Windows Server 2025 and Windows 11 24H2:
dsinternals.com
In the recently released Windows Server 2025 and Windows 11 24H2, several network protocols have been reconfigured to be more secure by default. One of the affected protocols is the Server Message...
1
35
86
Administrative registration of Passkeys (i.e. FIDO2 security keys or Microsoft Authenticator app) on behalf of other Microsoft Entra ID users is now possible using the new DSInternals.Passkeys #PowerShell module. #Passwordless
2
17
72
When I was offered a ride to Heidelberg, I wasn't expecting this. See you at @WEareTROOPERS Roundtables!
1
1
21
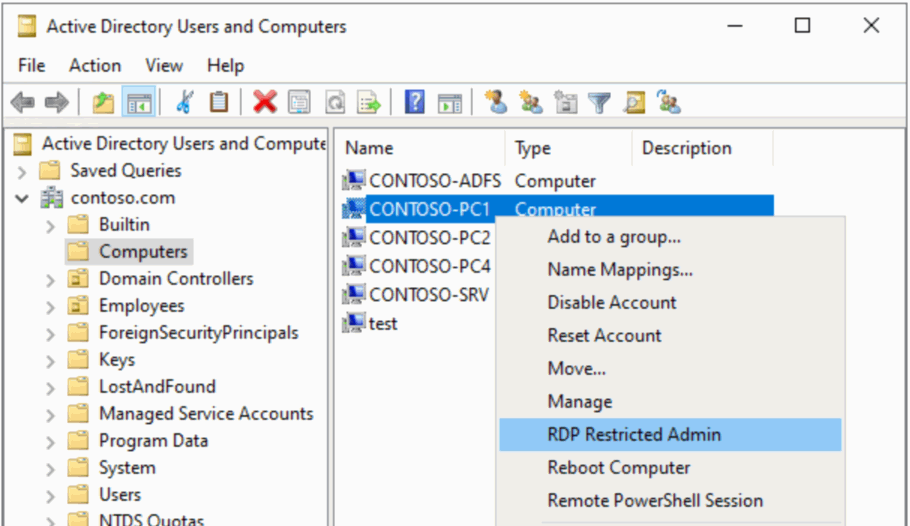
RT @PyroTek3: Domain Admin credentials delivered across the network to workstations and servers.
0
14
0
RT @SagieDulce: @MGrafnetter directed my attention to a new RPC filter capability!. Good job by @MSFTResearch / @Microsoft for this. I Hope….
0
5
0
Has anyone else noticed this ntdsutil typo, which has been present in Windows Server for as long as I can remember? It always catches my eye while creating #ActiveDirectory IFM backups, but is too silly to report to Microsoft Support. CC: @SteveSyfuhs
0
0
10
RT @CQUREAcademy: Meet @MGrafnetter, our Cybersecurity Expert, during his #MSBuild session taking place in Riyadh, Saudi Arabia. 📅 May 7.⏰….
0
1
0
Listing all #FIDO2 security keys / #Passkeys registered in Microsoft Entra ID using Microsoft Graph #PowerShell SDK.#Passwordless
0
11
31