SpecterOps
@SpecterOps
Followers
40K
Following
2K
Media
2K
Statuses
4K
Creators of BloodHound | Experts in Adversary Tradecraft | Leaders in Identity Attack Path Management
Joined January 2017
We’re excited to announce Kevin Mandia as the keynote speaker for #SOCON2026! 🎉 His keynote will focus on how the threat landscape has evolved in the face of modern adversary tradecraft. Secure your spot ➡️ https://t.co/DnlUAv9tRY
0
2
12
BloodHound OpenGraph isn’t just about AD anymore. In his latest Risky Biz interview, @jaredcatkinson breaks down how OpenGraph now maps attack paths across GitHub, AWS, SaaS, CI/CD, and beyond, allowing defenders to see what attackers see. 🎧: https://t.co/RrzPKgQmJD
0
3
7
The BloodHound Query Library, launched by @martinsohndk & @joeydreijer, democratizes tradecraft with a shared, searchable ecosystem. With 180+ Cypher queries & counting, the library is an increasingly valuable tool for the BloodHound community! Browse ➡️ https://t.co/tHTjcFQ8s4
0
2
16
TFW the cookie expired, but the attack path didn’t. 😒 Andrew Gomez explains how BloodHound graph analysis and Azure Seamless SSO enabled pivoting into the cloud. Read more ⤵️
specterops.io
The cookie crumbled when it expired, but the attack path didn’t. Learn how BloodHound graph analysis and Azure Seamless SSO enabled pivoting into the cloud.
0
16
51
Happening soon! 🔜 Don't miss today's webinar with @podalirius_ on ShareHound, a tool that automates discovery of network shares across a domain and exports the share objects and their access rights into BloodHound OpenGraph. Grab your spot 👉 https://t.co/uOuKC1N3Dx
0
2
9
Can it really be a coincidence? Smart Investors Hold Gold. Find out more at Goldhub
59
160
2K
Identity Attack Path Management took a major step forward in 2025. The APM Maturity Model + CISO Guide give teams clear frameworks to assess posture and put APM into practice. Maturity Model → https://t.co/FORJgjCRym CISO Guide → https://t.co/98mxvA1xhl
0
0
5
2️⃣ Next, @Breakfix dives into the SCOM agent. This post uncovers how RunAs creds reach endpoints, how they’re recovered off-host, and how rogue enrollment exposes sensitive data. Plus: introducing SharpSCOM for automated RunAs recovery. https://t.co/1KS5VVcxWc 🧵: 2/2
specterops.io
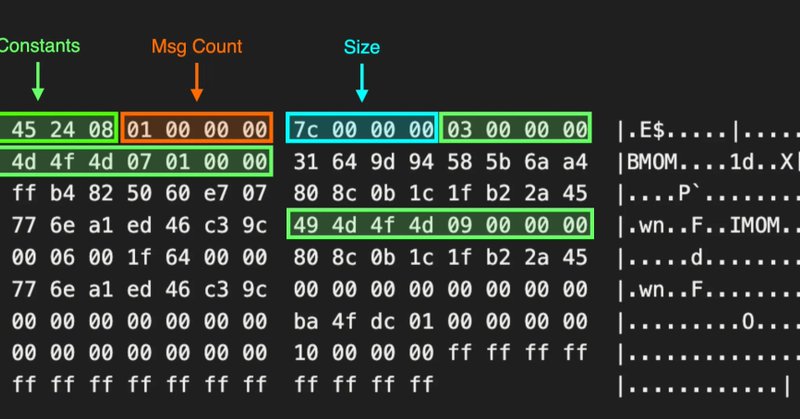
We found that SCOM RunAs credentials could be obtained on-host and also off-host in certain configurations and wrote a tool to help automate their recovery. To skip straight to the tool, go here...
0
16
32
Wanting more from today's #BHEU talk on SCOM? Check out this two part blog series! 1️⃣ @unsigned_sh0rt maps SCOM’s roles, accounts, & trust boundaries, then shows how attackers can chain insecure defaults into full management group compromise. https://t.co/Ai4TqTtc4O 🧵: 1/2
specterops.io
TL:DR; SCOM suffers from similar insecure default configurations as its SCCM counterpart, enabling attackers to escalate privileges, harvest credentials, and ultimately compromise the entire manage...
1
43
101
Happening soon! @unsigned_sh0rt & @breakfix's talk at #BHEU will show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. You don't want to miss this one. https://t.co/bxW5PYyhyl
1
4
14
Lenders can more easily work with state and local agencies to find grants and programs that may help borrowers afford a home thanks to our streamlined resources. Learn how.
0
4
46
🏃 Run, don't walk! @klezvirus will be speaking soon at #BHEU on how modern detection still breaks, and unveils the first CET-compliant stack spoofing framework. Learn more ➡️ https://t.co/3ffbujgNPE
0
1
5
Start making your way over to #BHEU Arsenal Station 5 for @bagelByt3s' session on LudusHound, a tool that rebuilds real-world AD environments using actual BloodHound data. 👉 https://t.co/HyDGactVVq
0
3
5
Day 1 at #BHEU is off to a great start! 🙌 Stop by booth 409 today and tomorrow to chat with our team about the latest in Identity Attack Path Management & see BloodHound Enterprise in action.
0
0
1
Good morning #BHEU! Kick off your day with BloodHound Quest happening soon. 🔜 Navigate identity relationships & attack paths in this digital treasure hunt using BloodHound Enterprise. Winners receive an in-person seat in an upcoming ADSF or RTO training. https://t.co/BfFa4BD0in
0
0
1
The latest Microsoft Research Forum episode is now available on-demand. Explore purposeful research and its real-world impact.
4
3
40
☝️This blog post is the perfect primer ahead of @unsigned_sh0rt & @breakfix's #BHEU talk TOMORROW. https://t.co/bxW5PYyhyl
0
4
15
SCOM is one of the most deployed, but least researched, System Center products. @synzack21 breaks down how it works + how to build a lab to test new tradecraft.
specterops.io
Yet another System Center Ludus configuration for your collection. https://github.com/Synzack/ludus_scom
1
46
104
Our first State of Attack Path Management Report dropped this year, highlighting why #IdentitySecurity is getting more complex, and why Attack Path Management is essential. It’s the clearest view yet of the adversary’s perspective. Read → https://t.co/lKwGBSQgCT
0
0
7
Our team is back at it again today at #GartnerIAM! Come see us at Booth 736 and learn how Identity Attack Path Management and BloodHound Enterprise reveal the real routes attackers use across environments and how to eliminate them. Stop by and meet the team. 👋
0
2
5
Stuck on holiday gifts? Skip the stress. USDA Prime steaks delivered to their door = instant win. Get 8 FREE steak burgers + free shipping ($145 value) with your order. Watch →
3
10
81
Happening now! @JustinKohler10 & @jaredcatkinson are speaking at #GartnerIAM on how Identity Attack Path Management helps teams eliminate exploitable paths.
0
1
8
Don't miss @JustinKohler10 & @jaredcatkinson at #GartnerIAM TODAY as they break down recent breaches and how Identity Attack Path Management helps teams eliminate exploitable paths. ➡️ https://t.co/FrqCKBnrcB
1
1
5
Wrapping up 2025 with a look at the work that shaped the year. 🎁 BloodHound OpenGraph expanded visibility across AWS, GCP, GitHub & more, and sparked projects like PingOneHound, JamfHound, ShareHound & MSSQLHound. Explore OpenGraph → https://t.co/WMcXisB30F
0
1
10