Andy Robbins
@_wald0
Followers
36K
Following
5K
Media
737
Statuses
5K
Co-founder of SpecterOps. Co-creator of BloodHound. https://t.co/rub1i3Fs9g
Seattle, WA
Joined March 2011
Stack spoofing isn’t dead. Hear from @klezvirus at #BHEU on how modern detection still breaks, and unveils the first CET-compliant stack spoofing framework. Learn more ➡️ https://t.co/3ffbujgNPE
2
20
44
SCOM monitors critical systems, but insecure defaults make it a powerful attack vector. At #BHEU, @unsigned_sh0rt & @breakfix show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. https://t.co/bxW5PYyhyl
3
38
133
SCOM monitors critical systems, but insecure defaults make it a powerful attack vector. At #BHEU, @unsigned_sh0rt & @breakfix show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. https://t.co/bxW5PYyhyl
0
31
70
Bring the LTX-2 API into real production pipelines, powering 4K, 50fps, synchronized-audio video generation
2
18
169
Just in time for the holidays, I wanted to share something that a lot of people have asked for: https://t.co/DfXyf2TTBp Short videos about Mythic development and customizations. This is just the start - I'll release a survey soon that'll get feedback for the next batch :)
1
18
47
Credential Guard was supposed to end credential dumping. It didn't. @bytewreck just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️
specterops.io
Uncovering the protection mechanisms provided by modern Windows security features and identifying new methods for credential dumping.
4
307
657
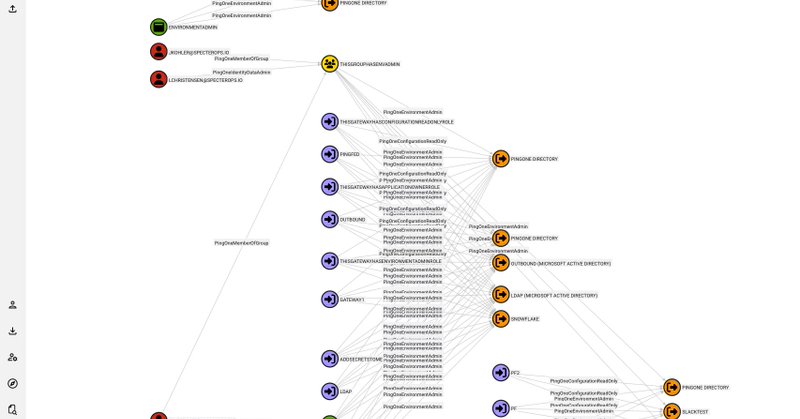
In this post @_wald0 introduces PingOneHound, a BloodHound OpenGraph extension that allows users to visualize, audit, and remediate attack paths in their PingOne environment. The blog post also serves as an introduction to the PingOne architecture. https://t.co/BjD5DPiih1
specterops.io
You can use PingOneHound in conjunction with BloodHound Community Edition to discover, analyze, execute, and remediate identity-based attack paths in PingOne instances.
0
24
50
BloodHound isn't just for Active Directory anymore. 🤯 @SadProcessor dives into the BloodHound OpenGraph functionality & demonstrates the new PowerShell cmdlets added to the BloodHound Operator module to work with the OpenGraph feature.
specterops.io
A Technical Dive Into BloodHound OpenGraph With BloodHound Operator & Master Yoda… TL;DR: The latest version of BloodHound introduces BloodHound OpenGraph. This new feature allows for ingestion of...
1
22
79
ICYMI: BloodHound OpenGraph, introduced with BloodHound v8.0, allows you to map attack paths across your entire tech stack. @JustinKohler10 & @_wald0 recently joined @_JohnHammond to discuss the new feature and share a demo. Watch the conversation 👉 https://t.co/Hq7bs6HAIN
0
3
17
🚨 New #BloodHound shirt alert 🚨 ✅ - Unisex and ladies sizes available ✅ - Cool design :) ✅ - ALL profits go to charity: Hope for HIE, which supports families suffering the effects of hypoxic ischemic encephalopathy Get your shirt here:
1
11
22
Another delay on crypto rules and all eyes are on @SenLummis. Is this about policy… or a generational gap in understanding tech? https://t.co/easJqaldUa
dailycaller.com
President Donald Trump came into office promising to bring forth a golden age. He has sought to modernize American industry.
2
4
36
We are back with our BloodHound t-shirt fundraiser! 🙌 Grab your BloodHound 8.0 shirt today. All funds raised will go directly to @HopeforHIE, the global voice for families affected by Hypoxic Ischemic Encephalopathy. 👕: https://t.co/qG7e34U7mh
0
12
33
Check out my new blog on nested app authentication and brokered authentication.
Why should Microsoft's Nested App Authentication (NAA) should be on your security team's radar? @Icemoonhsv breaks down NAA and shows how attackers can pivot between Azure resources using brokered authentication.
2
17
42
Dear fellow pentesters & red teamers, How often do you run into a vCenter in your client’s environment? 🖥️ I just built one for vCenter - meet vCenterHound 🐾😉 This is just the beginning… more collectors and surprises are on the way. #Pentesting #RedTeam #BloodHound #vCenter
1
38
158
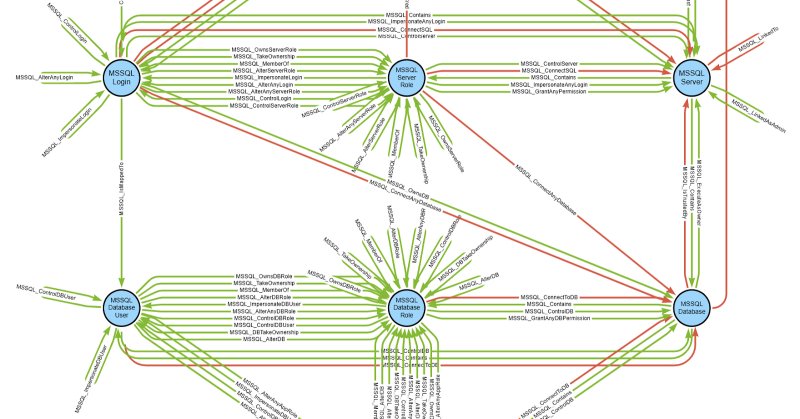
This post about MSSQLHound, a PowerShell collector that adds 7 new nodes and 37 new edges to BloodHound, details my experience and lessons learned designing and implementing the tool using OpenGraph and provides examples of how to research and discover MSSQL attack paths.
MSSQLHound leverages BloodHound's OpenGraph to visualize MSSQL attack paths with 7 new nodes & 37 new edges, all without touching the SharpHound & BloodHound codebases. @_Mayyhem unpacks this new feature in his blog post. 👇
0
30
93
MSSQL support just landed in BloodHound! You can now map out how attackers might use SQL servers to move laterally. This is incredibly useful in hybrid and legacy heavy environments. Let us know what you find. Learn more ➡️ https://t.co/30pNgVHvBj
1
20
64
MSSQLHound leverages BloodHound's OpenGraph to visualize MSSQL attack paths with 7 new nodes & 37 new edges, all without touching the SharpHound & BloodHound codebases. @_Mayyhem unpacks this new feature in his blog post. 👇
specterops.io
TL;DR MSSQLHound is a standalone PowerShell collector that adds 7 new nodes and 37 new MSSQL attack path edges to BloodHound using the new OpenGraph feature that was released in version 8.0. This...
1
52
132
More on BH OpenGraph: Ran into some issues when attempting to map objects collected with partial info back to existing BH objects. Built out a small tool that allows for connecting objects in a more flexible manner:
github.com
Middleware utility for enriching and uploading data gathered with arbitrary collectors - G0ldenGunSec/OpenImporter
1
24
60
Take the Ferry to NYC. Kids Ride Free Thru Jan 4. All Terminals & Routes. Free Shuttles to Attractions. Watch Video. Click for Routes & Schedules.
0
5
25
In this blog post I explain the fundamental building blocks, vocabulary, and principles of attack graph design for BloodHound:
specterops.io
TL;DR OpenGraph makes it easy to add new nodes and edges into BloodHound, but doesn’t design your data model for you. This blog post has everything you need to get started with proper attack graph...
1
42
95
Entra Connect sync accounts can be exploited to hijack device userCertificate properties, enabling device impersonation and conditional access bypass. @hotnops explores cross-domain compromise tradecraft within the same tenant. Read more ⤵️
specterops.io
How Entra Connect and Intune can be abused via userCertificate hijacking to bypass conditional access and compromise hybrid domains
2
59
118
I'm SO hyped to finally make MSSQLHound public! It's a new BloodHound collector that adds 37 new edges and 7 new nodes for MSSQL attack paths using the new OpenGraph feature for 8.0!. Let me know what you find with it! - https://t.co/Hh089SaVOS - https://t.co/geO0HXTykf
6
215
632
Join us for the BloodHound v8.0 deep dive this Thursday! @JustinKohler10, @_wald0, @jaredcatkinson & @StephenHinck will walk through all the new features & show you how to implement these updates in your environment. Register at https://t.co/gKyorlMSDz 🧵: 7/7
0
2
8