Lars Karlslund - mucking around with your AD
@lkarlslund
Followers
4,574
Following
1,363
Media
2,371
Statuses
11,676
Curious security octopus | Adalanche | Sarcasm level 11 | Fond of LEGO | 8.7B hashes | All thoughts, no leadership | I'm here for Justin
Danmark
Joined February 2010
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
jaemin
• 386688 Tweets
Norawit with L'Oreal Paris
• 233469 Tweets
Will Still
• 116792 Tweets
PP is WORTH IT
• 67424 Tweets
プロフェッショナル
• 43245 Tweets
Tina
• 33326 Tweets
SDカード
• 26809 Tweets
YOASOBI
• 25307 Tweets
高利貸し
• 24593 Tweets
GW後半戦
• 24492 Tweets
カメムシ
• 22593 Tweets
金利60
• 21275 Tweets
中条きよし参院議員
• 20704 Tweets
#素のまんま
• 18926 Tweets
出資法違反の疑い
• 18587 Tweets
Princess Charlotte
• 16741 Tweets
物語シリーズ
• 15120 Tweets
ウマチュン
• 14035 Tweets
外国人嫌い
• 14004 Tweets
東京地検特捜部
• 13139 Tweets
#モニタリング
• 12900 Tweets
FORCE LOVE SEALECT
• 11380 Tweets
排外主義的
• 10918 Tweets
#びりーぶ
• 10624 Tweets
Last Seen Profiles
When the Linux kernel is about to run out of entropy, it could just check the current licensing terms for Microsoft products, as they are always changing in a random way. Problem solved, next please!
4
94
654
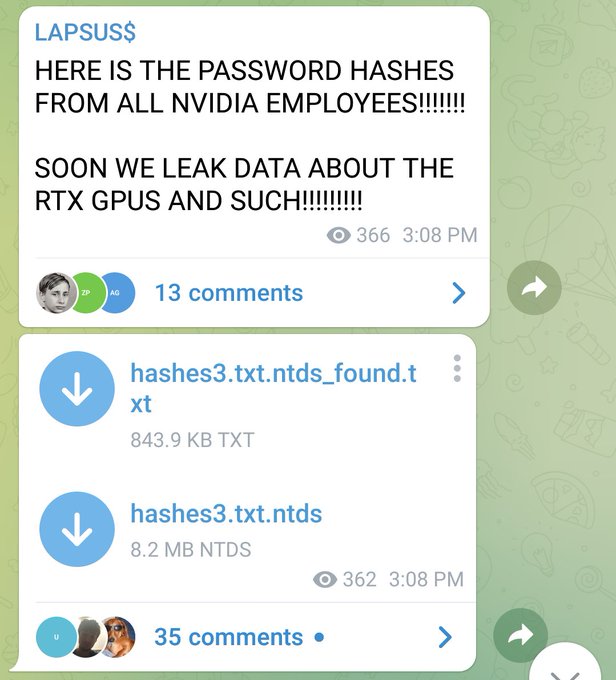
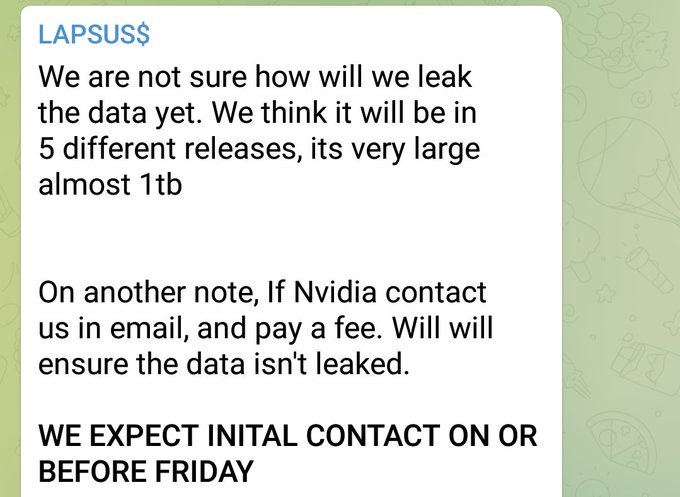
LAPSUS is threatening to release 1TB of stolen data from NVIDIA, which is the equivalent of the last three driver updates I downloaded for my graphics card
12
89
653
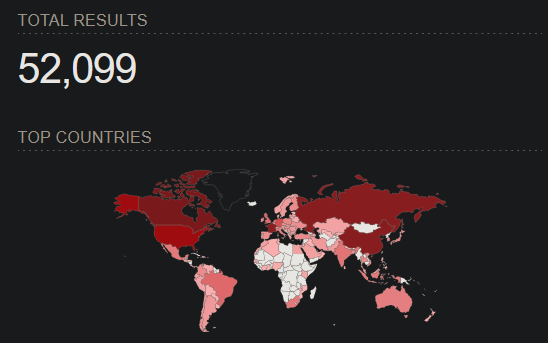
Today I did some dorking on
@shodanhq
, looking for Active Directory controllers exposed directly on the internet. Results after searching for "ldap GSS-SPNEGO" yielded a whopping 52K servers. Mind blowing!
13
137
597
@krlntpd
@SwiftOnSecurity
Wonderful comparison ... it's all fun and games until some virus finds an exploit in your obsolete DNA
2
3
352
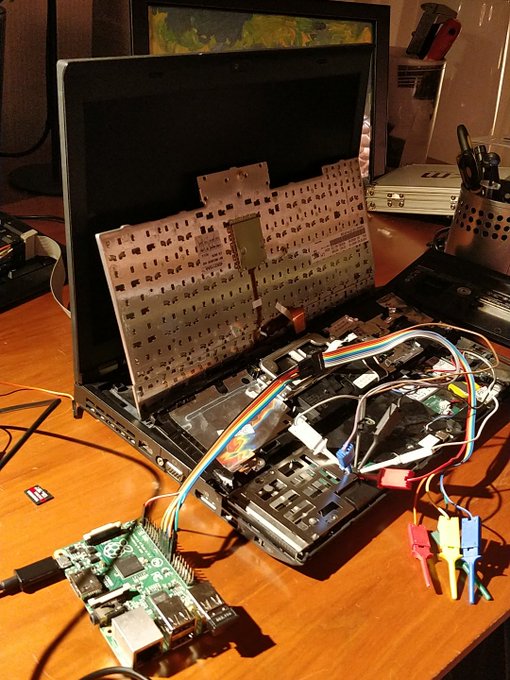
This ThinkPad X220 is waving goodbye to Intel ME and wherever stuff Lenovo put in there. Thanks to
@coreboot_org
8
85
294
Cool LDAP utility for Red Teamers! Easy to do simple lookups and some modifications - it has great potential and I'm sure more features will come. I had a similar tool planned, but never found the time to do it - fortunately
@synzack21
did!
1
82
283
@MalwareTechBlog
No, but I did successfully nuke Emotet from a large international company when 2 other companies failed, then deployed our EDR software and prevented a ransomware attack 9 months later. The thanks was they cancelled our software because it was too "noisy" in their alert mailbox.
6
3
186
Getting pwned twice: first by ransomware, then by not reporting it and the feds finding evidence of it on the ransomware servers
2
28
181
If you feel like Active Directory is daunting, but you want to learn more, and not feel like a total idiot at the same time ... read this: ... it wins because it's written concisely and in an easy to consume language (from
@Nutritionist_AP
feed, thanks 👏)
1
44
170
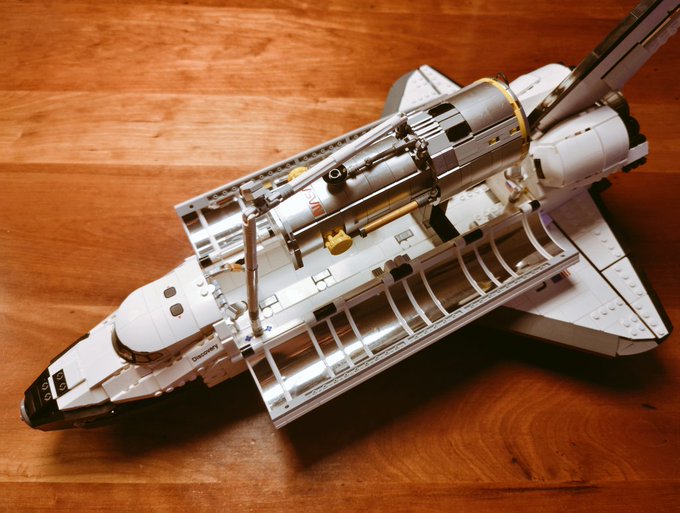
I know it's "just" a LEGO set, but for me it's a fond childhood memory of dreaming of going to space. I really loved building this one. Thanks
@LEGO_Group
for making stuff for us old kids.
4
2
161
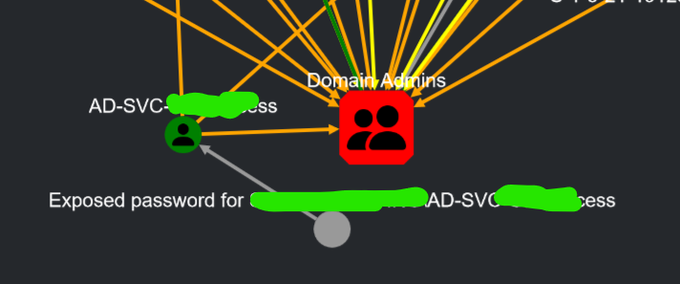
You can harden your Active Directory against wrong owners and permissions on Computer objects, which is a typical scenario with devastating results if it's a Domain Controller object. I've written about this problem earlier here. 1/11
3
43
137
Highly underrated GitHub repo from
@DebugPrivilege
here - if you do lowlevel-ish coding or just want to learn about Windows internal stuff, it's a real gold mine with knowledge that is reasonably easy to pick up. Can't believe it only has so few stars.
2
36
126
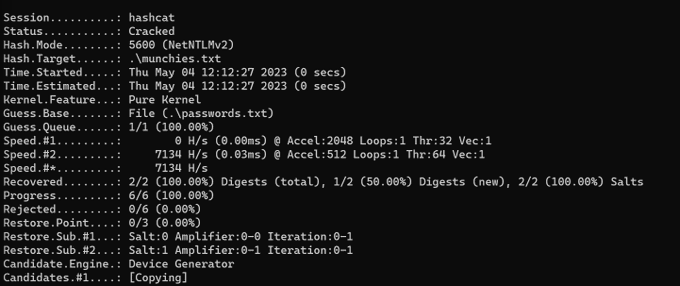
New offensive security tool: Hash Muncher. It dumps incoming NTLM authentication hashes from SMB/file share access. It's based on ultra cool research from
@Nettitude_Labs
, great work!
2
42
120
The amount of work put into the latest Game Of AD is just crazy. Super work,
@M4yFly
and contributors ♥️
4
22
114
If you have internet facing Windows machines, this is a good option to bring down attack surface a bit.
There is also the
@Crowd_Security
Windows agent which is an early alpha (for test systems!)
Or wait a bit for
@UK_Daniel_Card
to release his RDP guard.
4
40
102
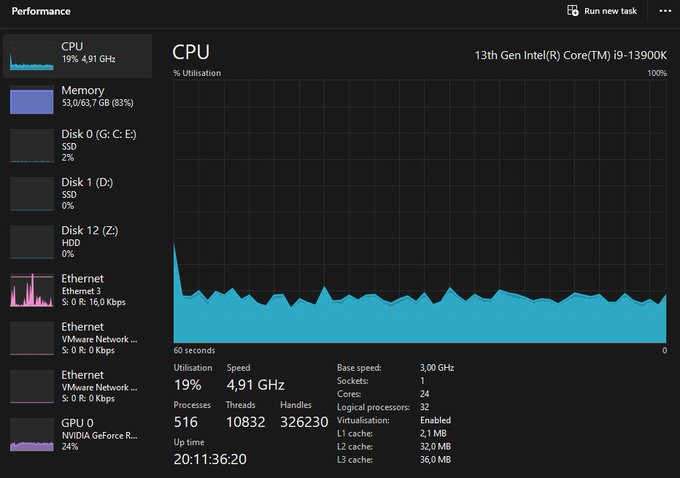
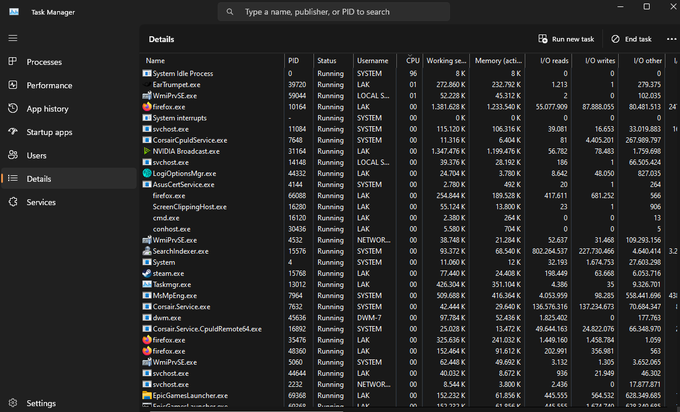
I will keep whining about the task manager being hosed in Windows 11 until someone from Microsoft fixes it. CPU usage @ 20% yet details show 96% idle. Current best option is asking
@SwiftOnSecurity
to help the mothership.
14
3
91
Android RCE+root via browser nets you $7.700,- at TianfuCup.
The same exploit will get you up to $500.000 at Zerodium.
You'd have to have pretty high morals combined with your technical skills to not just sell your exploit quietly.
6
17
80
@SwiftOnSecurity
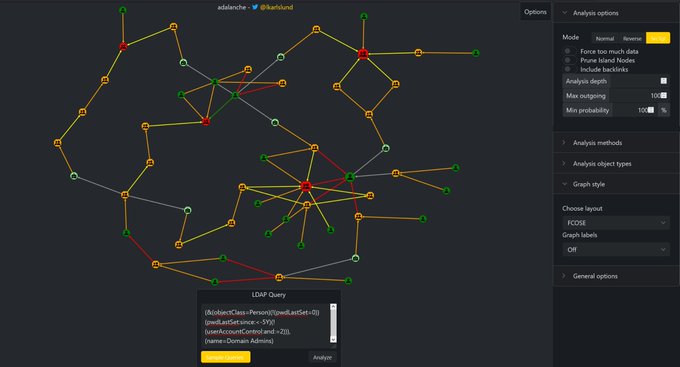
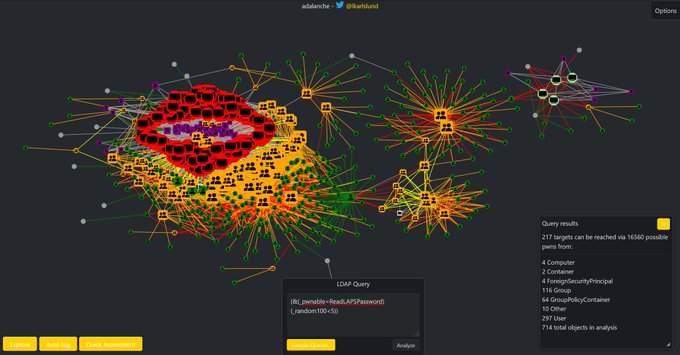
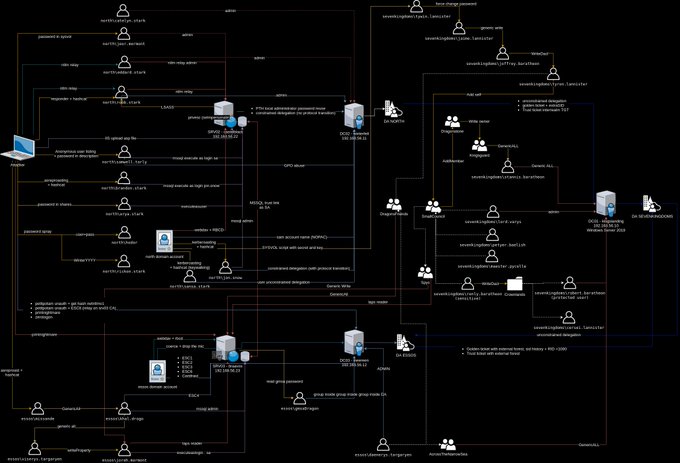
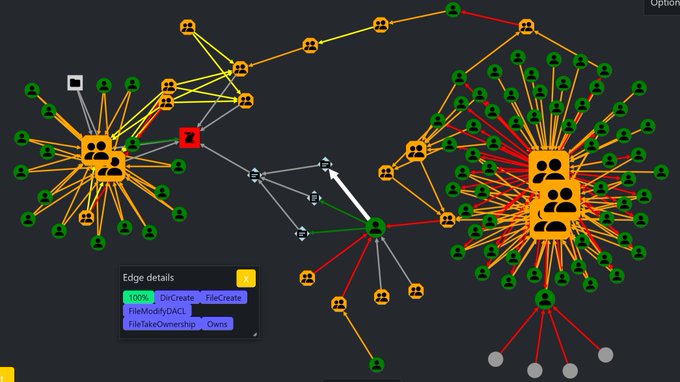
Adalanche is my AD analysis tool. It shows graphs that visualize attack paths and other access methods in AD and Windows systems. It will take you less than 5 minutes to get results.
1
17
74
If your SCCM server controls your AD controllers -> SCCM servers are Tier 0 ... and if the SQL server storing the SCCM DB contains push credentials for Tier 0 -> that makes the SQL server Tier 0 as well.
Attack paths are so much fun, but hard to lock down.
0
19
74
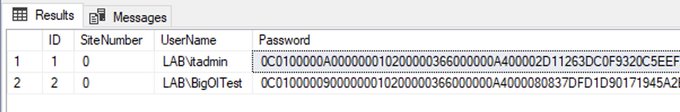
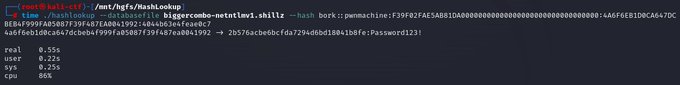
Insta-crack NetNTLMv1 .... works with any challenge, even ESS/SSP - as long as the password is in the database (cc
@vysecurity
)
1
8
66
@AntJanus
@SwiftOnSecurity
Look here, second tool listed will probably show you the responsible driver
1
5
57
@Eric0Lawton
@kcolbin
@JacquelynGill
I did one project, to fix a door security system written in Turbo Pascal in 1992. Not all code was available, and different parts of code on random disks. I spent at least 2 months on that in total. Doors wouldn't have unlocked 1/1/2000 if I hadn't. This is just a tiny example.
0
7
53