Mayfly
@M4yFly
Followers
7K
Following
3K
Media
58
Statuses
548
Former Dev and DevOps| Pentester and red teamer at orange cyberdefense | OSCE³| Tweet are my own| discord: m4yfly
Joined November 2017
RT @SpecterOps: Cookie theft has evolved. 🍪. Over the last year, stealing cookies on Windows devices has changed significantly for Chromium….
specterops.io
Explore how cookie theft has evolved in Chromium browsers with the shift from DPAPI to App-Bound encryption. This post breaks down modern cookie stealing techniques via COM, remote debugging, and...
0
76
0
RT @0xthirteen: I wanted to find out if you could start the WebClient service remotely, so I ended up digging into it .
specterops.io
A walkthrough to answer the question: "Can you start the WebClient service remotely as a low privileged user?"
0
57
0
RT @_dirkjan: It's been almost a year since my last blog. So, here is a new one: Extending AD CS attack surface to the cloud with Intune….
dirkjanm.io
Active Directory Certificate Services (AD CS) attack surface is pretty well explored in Active Directory itself, with *checks notes* already 16 “ESC” attacks being publicly described. Hybrid certif...
0
195
0
RT @badsectorlabs: Ludushound shows the power of community driven innovation in cybersecurity. @bagelByt3s created an awesome tool to conve….
specterops.io
LudusHound is a tool for red and blue teams that transforms BloodHound data into a fully functional, Active Directory replica environment via the Ludus framework for controlled testing.
0
90
0
CVE-2025-33073 is really insane 🤯.Reproduce this attack in GOAD in 3 commands.
Microsoft just released the patch for CVE-2025-33073, a critical vulnerability allowing a standard user to remotely compromise any machine with SMB signing not enforced! Checkout the details in the blogpost by @yaumn_ and @wil_fri3d.
8
127
487
Great course, definitely worth it! Thanks @mariuszbit 🙏, now I have weeks of homework to do 😅.
We're frying brains with Initial Access lore for the forth time at x33fcon! I have a blast having a great class! 🔥 Also, completely overhauled the agenda ☢️.
1
4
33
RT @Synacktiv: Microsoft just released the patch for CVE-2025-33073, a critical vulnerability allowing a standard user to remotely compromi….
0
261
0
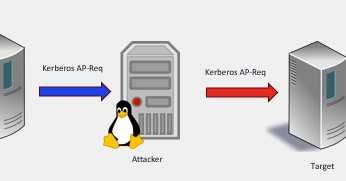
RT @RedTeamPT: 🚨 Our new blog post about Windows CVE-2025-33073 which we discovered is live:. 🪞 The Reflective Kerberos Relay Attack - Remo….
blog.redteam-pentesting.de
It is a sad truth in IT security that some vulnerabilities never quite want to die and time and time again, vulnerabilities that have long been fixed get revived and come right back at you. While...
0
176
0
RT @_CPResearch_: Zero-Day used by Stealth Falcon APT group in a spear-phishing campaign: .💥 .URL file exploitation (assigned CVE-2025-3305….
research.checkpoint.com
Check Point Research uncovers Stealth Falcon's cyber espionage campaign exploiting a Microsoft Zero Day Vulnerability
0
108
0
RT @hacknspeak: 🇫🇷🎙️Nouvel épisode du podcast Hack'n Speak accompagné de @shadow_gatt 🔥. On aborde le sujet du redteam, des missions, un re….
creators.spotify.com
Twitter: https://x.com/shadow_gattTwitter: https://x.com/mpgn_x64Talk lehack https://www.youtube.com/watch?v=7itLKu4f1XQ
0
10
0
RT @decoder_it: I just published a blog post where I try to explain and demystify Kerberos relay attacks. I hope it’s a good and comprehens….
decoder.cloud
While I was reading Elad Shamir recent excellent post about NTLM relay attacks, I decided to contribute a companion piece that dives into the mechanics of Kerberos relays, offering an analysis and …
0
149
0
RT @SpecterOps: New blog post just dropped! 🙌. Read the latest from @Tw1sm on how an operator can perform situational awareness steps prior….
specterops.io
I’m not sure if the frequency at which I encounter cloud/hybrid joined devices has recently increased or if I was sleeping on this capability for literal years (more likely), but this tradecraft has...
0
51
0
RT @0xBoku: As promised. this is Loki Command & Control! 🧙♂️🔮🪄.Thanks to @d_tranman for his work done on the project and everyone else o….
github.com
🧙♂️ Node.js Command & Control for Script-Jacking Vulnerable Electron Applications - boku7/Loki
0
238
0
RT @GuilhemRioux: Glad to publish a blog post on a critical vulnerability I found some months ago on GLPI, that impacts all default install….
github.com
GLPI vulnerabilities checking tool . Contribute to Orange-Cyberdefense/glpwnme development by creating an account on GitHub.
0
44
0
RT @0xBoku: Loki C2 blog drop! Thank you for all those who helped and all the support from the community. Big shoutout to @d_tranman and @c….
ibm.com
Microsoft offers a bug bounty for qualifying bypasses into Windows Defender Application Control. Learn how IBM's X-Force team found a bypass using Loki C2.
0
133
0
📩 Exchange Exploitation - Part 1 (Without Credentials) . Explore Exchange exploitation in Game of Active Directory and learn about attacks without valid credentials.
mayfly277.github.io
On GOAD v3 Update: A New Addition appear : EXCHANGE! Huge thanks to aleemladha for his pull request and invaluable help in integrating Exchange into the GOAD lab! I’ve been wanting to write an...
2
56
170