Garrett
@unsigned_sh0rt
Followers
2K
Following
3K
Media
165
Statuses
1K
Research at @SpecterOps
Portland, OR
Joined August 2009
Non-infosec post this time. I try to stray away from talking about my personal life here as much as I can especially when it comes to my family. In November 2023 my son Oliver was diagnosed with level 3 Autism Spectrum Disorder.
3
7
38
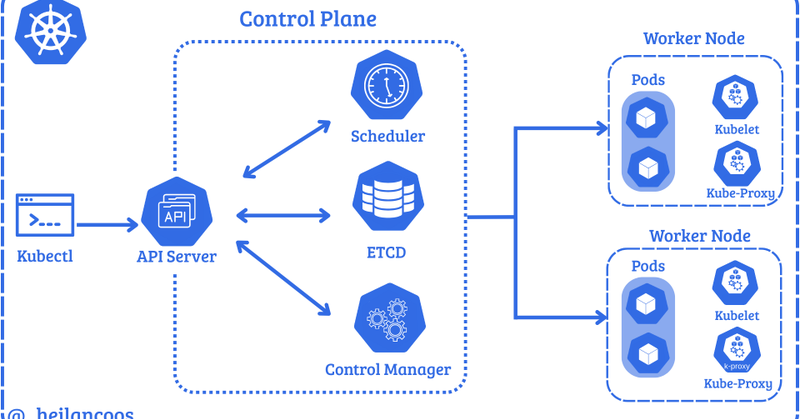
I fell down the Kubernetes security rabbit hole. So I wrote a deep-dive on attack techniques, detection engineering, and scripts to test everything in a lab. Shoutout to @GrahamHelton and @raesene for their previous work! https://t.co/5wlHqIZD8X
heilancoos.github.io
What attackers do in Kubernetes and how to catch them.
4
76
349
Moonwalk++ stack telemetry bypass (@KlezVirus), a pile of Mediatek CVEs (@hyprdude), AppleScript decompiler (@__pberba__pberba__>__), SCOM hacking (@unsigned_sh0rt + @breakfix), and more!
blog.badsectorlabs.com
Moonwalk++ stack telemetry bypass (@KlezVirus), a pile of Mediatek CVEs (@hyprdude), AppleScript decompiler (@__pberba__), SCOM hacking (@unsigned_sh0rt + @breakfix), .NET SOAP disaster (@chudyPB),...
1
2
25
[RELEASE] As promised, I’m releasing the first blog post in a series. It covers the gaps still present in current stack-based telemetry and how Moonwalking can be extended to evade detection logic and reach “on-exec” memory encryption. Enjoy ;) https://t.co/4Yf28y7cT4
klezvirus.github.io
TL;DR
8
99
312
New NTLM relay dropped for MSSQL. Should see some SCCM modules to use it next. @unsigned_sh0rt gave me all kinds of ideas.
0
17
84
0
2
23
Wow, @secbughunter sharing some big news from @msftsecresponse: Critical vulnerabilities are now in-scope for bounties by default 🔥 The small print: https://t.co/5rNlPBautP
0
4
13
Check out our two part blog series with @unsigned_sh0rt following our BlackHat EU talk
Wanting more from today's #BHEU talk on SCOM? Check out this two part blog series! 1️⃣ @unsigned_sh0rt maps SCOM’s roles, accounts, & trust boundaries, then shows how attackers can chain insecure defaults into full management group compromise. https://t.co/Ai4TqTtc4O 🧵: 1/2
0
2
9
Some interesting talks from @BlackHatEvents #BHEU today: ▪️You Win Some, You CheckSum by @EliranPartush ▪️SCOMmand And Conquer by @unsigned_sh0rt & @breakfix ▪️SOAPwn by @chudyPB
2
5
20
Blogs are up!
Wanting more from today's #BHEU talk on SCOM? Check out this two part blog series! 1️⃣ @unsigned_sh0rt maps SCOM’s roles, accounts, & trust boundaries, then shows how attackers can chain insecure defaults into full management group compromise. https://t.co/Ai4TqTtc4O 🧵: 1/2
1
42
128
Hope to see you there!!
Happening soon! @unsigned_sh0rt & @breakfix's talk at #BHEU will show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. You don't want to miss this one. https://t.co/bxW5PYyhyl
0
1
15
Start making your way over to #BHEU Arsenal Station 5 for @bagelByt3s' session on LudusHound, a tool that rebuilds real-world AD environments using actual BloodHound data. 👉 https://t.co/HyDGactVVq
0
3
6
☝️This blog post is the perfect primer ahead of @unsigned_sh0rt & @breakfix's #BHEU talk TOMORROW. https://t.co/bxW5PYyhyl
0
4
15
SCOM is one of the most deployed, but least researched, System Center products. @synzack21 breaks down how it works + how to build a lab to test new tradecraft.
specterops.io
Yet another System Center Ludus configuration for your collection. https://github.com/Synzack/ludus_scom
1
46
103
Generic AD labs don’t cut it. Stop by @bagelByt3s' #BHEU Arsenal session and hear about LudusHound, a tool that rebuilds real-world AD environments using actual BloodHound data. Learn more 👉 https://t.co/HyDGactVVq
0
10
40
Don't forget to grab yer tickets for WWHF @ Mile High 2026! -> https://t.co/QLA9JGyq6Q Check out Jason Haddix's talk, "Attacking AI - The New Frontier," from Wild West Hackin' Fest @ Deadwood 2025!
0
1
7
SCOM monitors critical systems, but insecure defaults make it a powerful attack vector. At #BHEU, @unsigned_sh0rt & @breakfix show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. https://t.co/bxW5PYyhyl
3
40
135
SCOM monitors critical systems, but insecure defaults make it a powerful attack vector. At #BHEU, @unsigned_sh0rt & @breakfix show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. https://t.co/bxW5PYyhyl
0
31
70
Stack spoofing isn’t dead. Hear from @klezvirus at #BHEU on how modern detection still breaks, and unveils the first CET-compliant stack spoofing framework. Learn more ➡️ https://t.co/3ffbujgNPE
2
21
44
Anyone else seeing this behavior with Claude? I'll start a new chat without extending thinking but in the response to a message it's enabled. I skimmed settings to see if I could stop it but didn't see anything. Not a huge issue just an annoyance.
1
0
2