The DFIR Report
@TheDFIRReport
Followers
64K
Following
711
Media
490
Statuses
2K
Real Intrusions by Real Attackers, the Truth Behind the Intrusion.
thedfirreport.com/contact
Joined April 2020
➡️ The above is from a recent Private Threat Brief: "Signed Malware, PowerShell Abuse, and Azure Exfiltration in Fake WinSCP Intrusion" ➡️➡️Interested in receiving reports like this one? Contact us for a demo or pricing -
thedfirreport.com
Sales inquiries If you are looking for anything related to sales (pricing, quotes, renewals, trials, or demos), please contact sales@thedfirreport dot com DFIR Labs / Training If you are looking fo…
0
0
4
We identified a malvertising campaign targeting users searching for legitimate software, leading to the download of a trojanized WinSCP installer that deployed Broomstick/OysterLoader. All files involved in the initial access phase were signed with valid certificates.
1
17
57
Extracting VNC screenshots and keylog data from #Latrodectus 🕷️ BackConnect https://t.co/GIAcl9Dfit
netresec.com
I recently learned that the great folks from The DFIR Report have done a writeup covering the Latrodectus backdoor. Their report is titled From a Single Click: How Lunar Spider Enabled a Near...
1
11
43
🎉 BLACK FRIDAY DEAL IS LIVE! 🎉 Now until December 1st, all swag in our store is 50% OFF — shirts, hoodies, and stickers, while supplies last! 🎁 Bonus: Every order comes with 2 FREE DFIR Report stickers! Don’t miss it — once it’s gone, it’s gone. https://t.co/5atl6q2ke0
0
4
19
Small space, big comfort. Wayfair has stylish tables and seating that make every corner count.
0
20
430
🎉 BLACK FRIDAY DEAL IS LIVE! 🎉 Now until December 1st, all swag in our store is 50% OFF — shirts, hoodies, and stickers, while supplies last! 🎁 Bonus: Every order comes with 2 FREE DFIR Report stickers! Don’t miss it — once it’s gone, it’s gone. https://t.co/5atl6q2ke0
0
4
19
➡️ The above is from a recent Private Threat Brief: "Signed Malware, PowerShell Abuse, and Azure Exfiltration in Fake WinSCP Intrusion" ➡️➡️Interested in receiving reports like this one? Contact us for a demo or pricing -
thedfirreport.com
Sales inquiries If you are looking for anything related to sales (pricing, quotes, renewals, trials, or demos), please contact sales@thedfirreport dot com DFIR Labs / Training If you are looking fo…
0
0
3
"...It's unclear why they scanned these external IPs. An interesting observation is that they scanned public IP ranges which hosted the C2 addresses used by Supper:"
1
0
1
"Checking the registry and network traffic, we could identify ranges they scanned. They most likely ran several scans in Advanced IP scanner. We found evidence of scans for private IP ranges as well as multiple public IP ranges belonging to Microsoft and other entities..."
1
1
9
@TheDFIRReport has been a huge resource throughout my DFIR journey, so it’s a real highlight to finally contribute to one of their reports. Really excited to share this one, hope you enjoy! :)
🐈 Cat’s Got Your Files: Lynx Ransomware 🎉New report out by @Friffnz, Daniel Casenove & @MittenSec!🎉 Attackers used stolen creds to access RDP, quickly pivoted to a DC with a second compromised admin, created impersonation accounts, mapped the environment, and more.
1
4
21
🐈 Cat’s Got Your Files: Lynx Ransomware 🎉New report out by @Friffnz, Daniel Casenove & @MittenSec!🎉 Attackers used stolen creds to access RDP, quickly pivoted to a DC with a second compromised admin, created impersonation accounts, mapped the environment, and more.
3
27
89
@Friffnz @MittenSec ...and hosts were successfully enumerated using the domain admin credentials during scanning." Want a heads-up when we drop a new report? Sign up here: https://t.co/oPX1ir9O13 2/2
thedfirreport.com
If you would like to receive an email when we publish a new report, please type your email address below and press subscribe. If you do not receive the confirmation email within a few minutes, plea…
1
0
5
🎉New report out Monday 11/17 by @Friffnz, Daniel Casenove & @MittenSec! "Artifacts of this SMB enumeration were left behind in the smb.db database stored by NetExec in C:\Users\%UserProfile%\nxc\workspaces\smb.db. This database confirms that a number of domains... 1/2
1
15
109
@Friffnz @MittenSec ...discovered share. These actions generated Windows Security Event ID 5145 object access entries referencing the delete[.]me file." Want a heads-up when we drop a new report? Sign up here:
thedfirreport.com
If you would like to receive an email when we publish a new report, please type your email address below and press subscribe. If you do not receive the confirmation email within a few minutes, plea…
0
2
5
🎉New report out Monday 11/17 by @Friffnz, Daniel Casenove & @MittenSec! "In this case, Netscan was run with domain administrator privileges, so all discovered shares were writable. As a result, NetScan was able to create and delete the delete[.]me file on each... 1/2
2
4
24
@Friffnz @MittenSec ...legitimate accounts already present in the environment. For the rest of the report we will refer to these accounts as: "administratr", "Lookalike 1", and "Lookalike 2"." Want a heads-up when we drop a new report? Sign up here: https://t.co/oPX1ir9O13 2/2
thedfirreport.com
If you would like to receive an email when we publish a new report, please type your email address below and press subscribe. If you do not receive the confirmation email within a few minutes, plea…
0
1
3
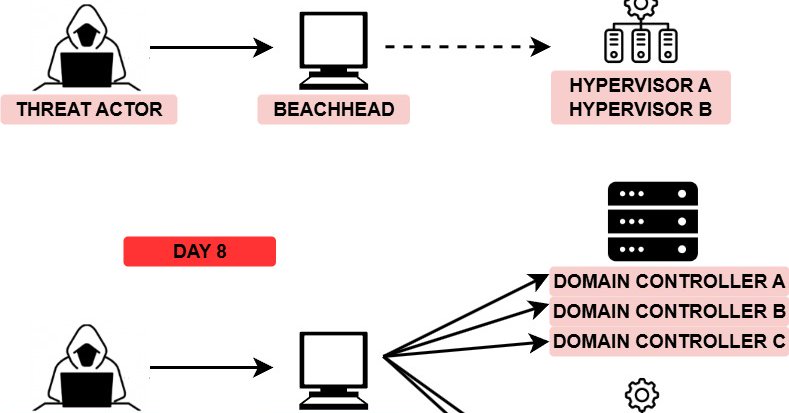
🎉New report out Monday 11/17 by @Friffnz, Daniel Casenove & @MittenSec! "On the domain controller, they used the "Active Directory Users and Computers" snap-in (dsa.msc) to create three users for persistence. All of the newly created accounts have usernames that mimic... 1/2
1
5
24
@Friffnz @MittenSec ...beachhead host without performing any credential access activities, indicating these credentials were also obtained prior to initial access." Want a heads-up when we drop a new report? Sign up here: https://t.co/oPX1ir9O13 3/3
thedfirreport.com
If you would like to receive an email when we publish a new report, please type your email address below and press subscribe. If you do not receive the confirmation email within a few minutes, plea…
0
0
5
@Friffnz @MittenSec ...there was no indication of brute force or password spraying occurring, indicating these credentials were obtained prior to the intrusion. The threat actor was also observed using credentials for a second account with domain administrator privileges to pivot from the... 2/3
1
0
5
🎉New report out Monday 11/17 by @Friffnz, Daniel Casenove & @MittenSec! "The first instance of unauthorized access by the threat actor was a successful RDP logon to the beachhead host, a publicly exposed RDP server. The logon was performed using valid credentials, and... 1/3
1
6
14
Traditional RAG searches data—next-gen RAG gives you knowledge. Meet Microsoft Foundry IQ—powered by Azure AI Search—delivering the right context to agents, all from a single knowledge base.
0
1
9