NSA Cyber
@NSACyber
Followers
134,025
Following
17
Media
206
Statuses
433
We protect our nation’s most sensitive systems against cyber threats. Likes, retweets, and follows ≠ endorsement.
Joined November 2019
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Champions
• 233722 Tweets
Dortmund
• 202198 Tweets
Senna
• 181279 Tweets
Sancho
• 154550 Tweets
Gustavo Petro
• 141735 Tweets
Mbappé
• 96629 Tweets
#BVBPSG
• 85865 Tweets
Madonna
• 85332 Tweets
Boulos
• 80968 Tweets
Paco Villa
• 61660 Tweets
CRIME ELEITORAL
• 52843 Tweets
Rio Grande do Sul
• 42412 Tweets
Flopou
• 37656 Tweets
Ramos
• 34224 Tweets
Dembele
• 32965 Tweets
Canelo
• 26669 Tweets
Kolo Muani
• 23227 Tweets
باريس
• 21324 Tweets
دورتموند
• 17584 Tweets
Adeyemi
• 16890 Tweets
Fabian Ruiz
• 15631 Tweets
Fullkrug
• 15600 Tweets
Nuno Mendes
• 15299 Tweets
Hakimi
• 13536 Tweets
フジコ・ヘミングさん
• 12695 Tweets
Timmy
• 12336 Tweets
Luis Enrique
• 11463 Tweets
De La Hoya
• 11076 Tweets
#TierraDeNadie8
• 10895 Tweets
Barcola
• 10461 Tweets
Last Seen Profiles
Malicious cyber actors are using two sets of
#TTPs
to access protected data in the
#cloud
. Detect and mitigate against this activity by reviewing our latest
#cybersecurity
advisory:
60
838
2K
Russian Foreign Intelligence Service (SVR) cyber actors are exploiting five publicly known vulnerabilities to target U.S. and allied critical networks. Review our joint
#cybersecurity
guidance with
@CISAgov
and
@FBI
and apply the mitigations to stop them:
96
1K
2K
The Russian GRU 85th GTsSS, sometimes publicly known as
#APT28
or
#FancyBear
, is using a previously undisclosed
#Linux
malware called Drovorub for cyber espionage operations.
For full details and mitigations, review our
#cybersecurity
advisory with
@FBI
:
70
1K
2K
If malicious cyber actors gain initial access to networks through the
#SolarWinds
compromise, the TTPs noted in our advisory may be used to forge credentials and maintain persistent access. Our guidance helps detect and mitigate against this, no matter the initial access method.
Malicious cyber actors are using two sets of
#TTPs
to access protected data in the
#cloud
. Detect and mitigate against this activity by reviewing our latest
#cybersecurity
advisory:
60
838
2K
36
391
863
Today our
#Ghidra
team pushed a preview debugger on
@GitHub
.
#Developers
and testers, check out this long awaited feature:
41
317
966
NSA urges applying critical Microsoft patches released today, as exploitation of these
#vulnerabilities
could allow persistent access and control of enterprise networks.
31
741
1K
Russian state-sponsored cyber actors are exploiting
#vulnerability
CVE-2020-4006 affecting VMware Workspace ONE Access. We recommend patching immediately. Read our latest
#cybersecurity
advisory for details, including detection and mitigation actions:
21
466
747
We collaborated with
@CISAgov
&
@FBI
on our
#cybersecurity
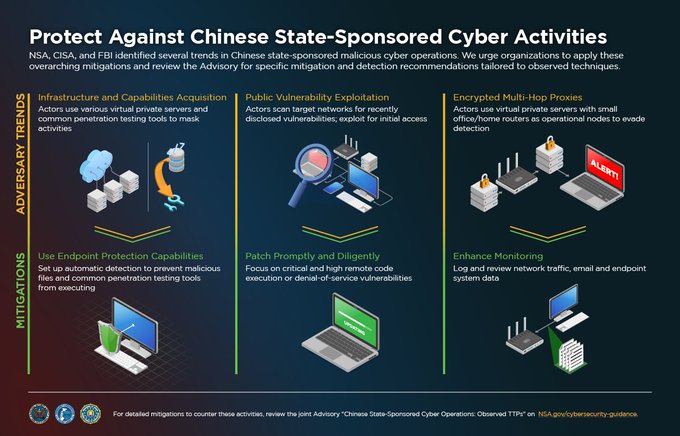
advisory, detailing Chinese state-sponsored actor
#TTPs
used against U.S. and allied networks. For a thorough understanding of this cyberthreat, read our overview, observed TTPs & mitigations.
40
429
767
D3FEND, a MITRE research project funded by the NSA, improves the
#cybersecurity
of NSS, DoD, and the DIB by providing defensive countermeasures for common offensive techniques. Learn more here:
16
389
721
Zero Trust assumes all users, devices, and network components to be untrusted until verified as legitimate. For more on how
#ZeroTrust
can enhance your organization’s security, review our latest
#cybersecurity
release:
129
336
673
Sandworm Team, Russian GRU Main Center for Special Technologies actors, continue to exploit Exim mail transfer agent
#vulnerability
, CVE-2019-10149.
Patch to the latest version to protect your networks. Learn more here:
16
417
612
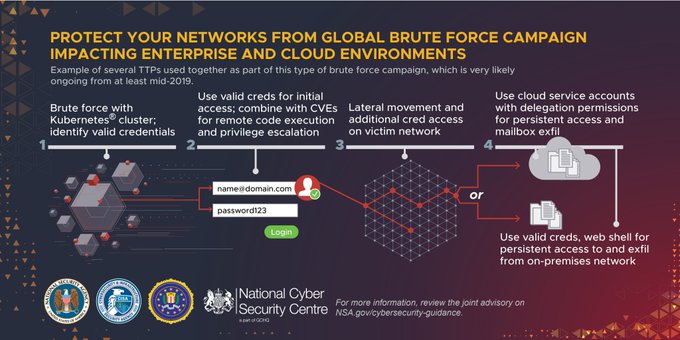
Our recent
#cybersecurity
advisory with
@CISAgov
@FBI
&
@NCSC
publicly exposes a global brute force campaign. Exploitation is likely ongoing. Review our advisory for
#IOCs
and
#mitigation
techniques:
22
333
555
Our UEFI Secure Boot Customization
#cybersecurity
report explains how system admins can customize Secure Boot to better protect against firmware threats, including the recent
#BootHole
vulnerability CVE-2020-10713. Read the detailed recommendations here:
9
272
533
A proof of concept exploit has been released for Windows Netlogon vulnerability CVE-2020-1472. We expect it to be used.
Install the patch and implement additional instructions in Microsoft article KB4557222.
Remember to patch CVE-2020-1472—an elevation of privilege vulnerability in Microsoft’s Netlogon. Read more at .
#Cyber
#Cybersecurity
#InfoSec
2
119
114
11
334
512
Today’s
#cybersecurity
release recommends how enterprises can adopt the encrypted DNS protocol DoH without sacrificing security control. Network owners and admins must understand the benefits/risks before adopting. Read more:
16
201
354
CVE-2020-10713 poses significant risk to Linux and Windows systems. Follow the mitigations in our
#Cybersecurity
Advisory to protect against this GRUB2
#BootHole
vulnerability.
12
183
276
#Mobile
devices store and share device
#geolocation
data by design. To limit risk of your location data being exposed, follow the guidance in our newest
#cybersecurity
information sheet
23
174
261
#BlackMatter
#ransomware
-as-a-service has been targeting U.S. critical infrastructure since July 2021. We partnered with
@CISAgov
and
@FBI
to share the advisory with actor TTPs and mitigations.
11
179
311
As
#CyberMonth
comes to a close, don't forget the work doesn't stop here! Join our team and play a role in helping others
#BeCyberSmart
21
85
297
Protect against the
#Conti
#ransomware
threat using the
#cybersecurity
guidance from
@CISAgov
,
@FBI
and NSA. Understand Conti group TTPs and take immediate action:
19
156
295
Actors are forging SAML authentication to access protected data in the cloud.
@msftsecresponse
has observed similar techniques and additional TTPs. Visit their blog for more countermeasures:
17
128
262
People’s Republic of China-sponsored actors are targeting U.S. critical infrastructure, pre-positioning for disruptive actions. We’ve joined with
@CISACyber
,
@FBI
, and others to address this activity. Read our advisory now:
49
128
280
Ransomware incidents targeting critical infrastructure were on the rise in 2021. Protect against the threat using the joint cybersecurity guidance from
@FBI
,
@CISAGov
,
@CyberGovAu
, and
@NCSC
to help reduce the risk of compromise. Read more here:
27
135
257
Fancy Bear doesn’t hibernate – they’ve been abusing popular routers since 2022. To counter this Russian state-sponsor activity, we’ve joined
@FBI
,
@CNMF_CyberAlert
, and international co-sealers to release actionable guidance. Read our report:
25
160
260
Chinese state-sponsored malicious cyber actors are exploiting publicly known
#vulnerabilities
. Network defenders should take action to protect against this activity.
For a full list of CVEs & related mitigations review our latest
#cybersecurity
advisory:
14
172
246
Log4j vulnerabilities continue to be exploited–keep watch for updates from vendors. Read the advisory with
@CISAgov
,
@FBI
,
@CyberGovAU
,
@NCSC
,
@CERTNZ
&
@cybercentre_ca
for a summary of the threats and mitigations to defend your IT and OT assets.
36
129
250
Thousands of cybersecurity students and network defenders have used
#Ghidra
to build and research current technologies since its release — head over to to check it out.
40
68
223
We expect to see an increase in targeting of managed service providers. This joint advisory with
@NCSC
,
@CISAgov
,
@FBI
,
@CyberGovAU
, and
@cybercentre_ca
highlights key actions for MSPs and their customers to secure communications and other sensitive data.
42
128
211
Microsoft has released a powershell script for deploying critical
#mitigations
related to the Microsoft Exchange Vulnerabilities. If network defenders can't patch in a timely fashion, use the released script to shrink the attack surface.
View the script:
10
141
225
Cybersecurity Awareness Month is almost here! We are looking forward to another great year of partnership with
@DHSgov
and
@CISAgov
to kick off
#CyberMonth
and promote best practices in cyber!
#BeCyberSmart
50
98
227
CVE-2020-1350 represents significant risk to Windows DNS servers.
#Patch
or apply the mitigation steps today, you should expect adversaries are hard at work writing exploits for this
#vulnerability
. Check out our detailed guidance:
14
131
196
Our latest
#cybersecurity
product helps sys admins
#detect
and replace outdated TLS encryption protocol implementations with updated configurations to ensure data is being effectively protected. Read more:
13
97
180
Updates to our
#Kubernetes
Hardening Guide with
@CISAgov
are live! Thanks to all who reached out with feedback to help make the guidance more comprehensive — including more detailed info on logging and threat detection in addition to other clarifications.
22
103
181
In October 2019,
@NSAGov
established a directorate dedicated to preventing and eradicting cyber threats in support of our
#cybersecurity
mission. Our
#YearInReview
outlines key milestones and mission outcomes achieved.
32
83
159
#OperationalTechnology
owners and operators will benefit from our recent
#Cybersecurity
Advisory on how to evaluate risks to their systems & make informed decisions to prevent and detect malicious activities. Review the pragmatic evaluation methodology:
7
94
179
Round two! NSA has partnered again with
@CISACyber
,
@FBI
, and other U.S. and international agencies to provide guidance and harden targets against living off the land techniques employed by People’s Republic of China and Russian state-sponsored actors.
67
74
178
#CodebreakerTechTip
: Having proficiency with an advanced text editor can make it easier to examine large or complex text files. Two popular editors: emacs and vi. Our preference? No comment.
20
39
173
Minimize the risk of malicious PDFs affecting your environments. Our latest technical report includes updated
#configuration
recommendations for
#Adobe
Acrobat Reader—including for the newer cloud features.
18
84
168
Is your leadership asking about PRC threats to your systems? Along with
@CISACyber
and other partners, we’re releasing an executive overview of the February 2024 joint cybersecurity advisory on PRC actor Volt Typhoon activity. Read now:
10
84
175
Ransomware tactics and techniques are rapidly evolving. Learn what you can do to
#StopRansomware
.
21
91
165
We chase and eradicate threats all across the globe.
@CYBERCOM_DIRNSA
and
@NSA_CSDirector
sat down to talk about the state of cybersecurity and how NSA defends the nation 24/7.
Watch their conversation, then read our Year in Review report:
67
81
168
Dave Luber has started as
@NSAGov
's new Director of Cybersecurity
@NSA_CSDirector
. He now leads our critical mission to prevent and eradicate threats to National Security Systems and the Defense Industrial Base. Welcome, Dave! Learn more about him here:
28
53
168
It takes collaboration to secure Operational Technology. Morgan Adamski, Director of
@NSAGov
's
#Cybersecurity
Collaboration Center, spoke with
@DragosInc
,
@ENERGY
, and
@CISAgov
about threats to these systems and how
#Partnerships
play a key role in securing them.
11
49
158