Nathan McNulty
@NathanMcNulty
Followers
16K
Following
68K
Media
5K
Statuses
40K
Loves Jesus, loves others | Husband, father of 4, security solutions architect, love to learn and teach | Microsoft MVP | @TribeOfHackers | 🦋@nathanmcnulty.com
Alaska
Joined June 2009
Hi, I'm Nathan McNulty 👋. I am here because I enjoy learning and helping others. I feel like I've already accomplished more than I ever dreamed, and I truly want that for everyone else. If you ever find yourself questioning my intent - start there, DM me, or call me out.
23
6
218
RT @Mister_MDM: Wondering why Intune Remote Actions are Fast at First but Slow the Next Day?. On the first day, when a device is enrolled,….
0
31
0
Oh look, another one with a full list of crap that Credential Guard breaks 😎. Love this note provided near the end, great recap though I wish the guidance had been "turn this feature on so you aren't vulnerable" ;).
Different ways of dumping lsass:. #hacking #windows #passwords #informationsecurity #hashes #microsoft #pentest #cybersecurity
1
0
7
While dumb and a perfect example of "detect the technique, not the tool", this really shouldn't be an issue for anyone at this point (but I know it is. ). Credential Guard and the ASR rule for credential theft have been enabled by default for 3 years and safely blocks all of this.
Windows Defender blocks any procdump execution referencing "lsass" on the command line (1️⃣). Simply querying lsass' process ID and using this instead bypasses this somewhat naive detection (2️⃣). Even simpler? Use lsass' service name, "KeyIso" 🤷 (3️⃣)
1
3
28
Endpoint admins then: Ehh, I'm not sure what will break if I try to turn on VBS, not gonna risk it. Endpoint admins now: Hotpatching is here! Oh, it needs VBS? YOLO :D. #IAmAnEndpointAdmin
0
2
42
Usually I'm pretty bummed that APAC and EMEA get Intune updates before me, but not today! 😅.
@IntuneSuppTeam We're seeing issues in multiple APAC tenancies of newly uploaded win32 packages, uploaded via console or PMPC not showing up in the list of applications. If I get the App-ID from the audit log for the app & access the URL with that then it can be accessed.
1
0
4
Doh, I missed wrapping the URL in double quotes. Had stored as a variable when testing. Thanks @ruadams for catching that. Try this instead:. Invoke-MgGraphRequest -Uri "https ://graph.microsoft.com/v1.0/auditLogs/signIns?`$filter=AppId eq '00000002-0000-0000-c000-000000000000'".
0
0
5
RT @dougsbaker: I made a video walking through how I locked down browser usage in my org using Microsoft Edge Management inside the M365 Ad….
0
16
0
RT @merill: Love @TechBrandon's session on Finding holes in conditional access policies from @CypherCon. Nice talk that covers some of the….
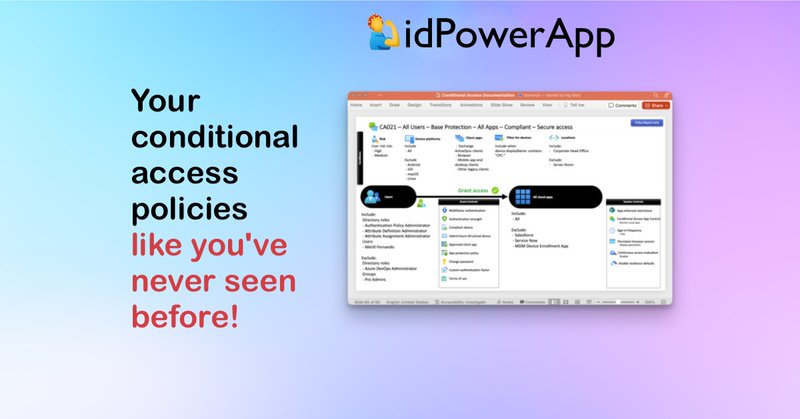
idpowertoys.merill.net
Identity power user tools for Microsoft Entra admins.
0
3
0
RT @ZackKorman: Microsoft isn’t disclosing this so: M365 Copilot allowed users to access files without producing an audit log. All you had….
0
561
0
What are you all doing when auditing apps need privileged ReadWrite permissions because there is no Read only permission?. Interestingly, there is a .Read.Directory permission you can consent to, but it doesn't work even delegated. cc: @paulsanders87
2
2
18
RT @NathanMcNulty: Don't forget your bottle of Elmer's next time you create an offline root CA
0
8
0
RT @Cyberipman: @NathanMcNulty @yuridiogenes @HeikeRitter I'd also like to shout-out John Christopher content here for anybody else looking….
0
1
0
RT @arekfurt: I honestly think the fundamental reason app control hasn't (yet) gotten widespread traction while EDR has is that big securit….
0
8
0