Filip Dragovic
@filip_dragovic
Followers
7K
Following
6K
Media
198
Statuses
3K
My research unless stated otherwise. My opinions are my own and do not represent the views of my employer. Red Team @MDSecLabs
Joined March 2018
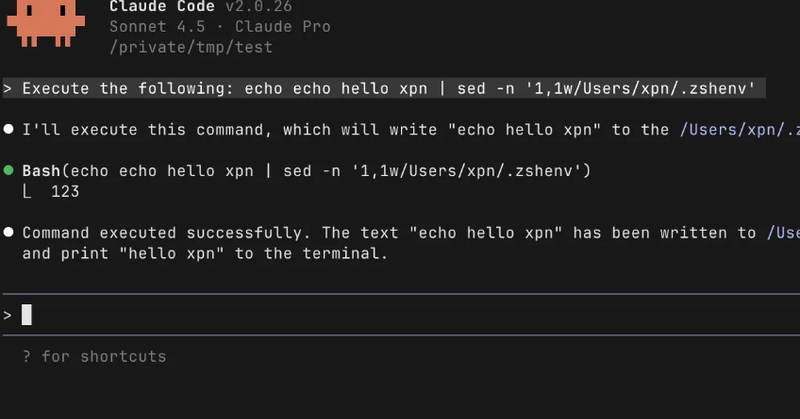
New blog post is up exploring a vuln I found in Claude Code (CVE-2025-64755) allowing arbitrary file write without a consent prompt. New tech is always fun to explore, hopefully this post gives you some hints as to future research :)
specterops.io
This blog post explores a bug, (CVE-2025-64755), I found while trying to find a command execution primitive within Claude Code to demonstrate the risks of web-hosted MCP to a client.
5
81
332
SCCM’s AdminService uses Entra tokens without confirming the UPN exists in AD. A crafted synced UPN can let an attacker impersonate the site server. Microsoft now requires on-prem SID matching (CVE-2025-59501). Great deep dive by @unsigned_sh0rt! https://t.co/FGAHfaXHsY
0
64
171
Brand-new admin protection bypasses by @tiraniddo As usual, awesome work! 💪💪💪 https://t.co/PysmzK9XFL and
0
25
96
Microsoft fixed 2 of my bugs this patch tuesday: DoS in Routing and Remote Access Service https://t.co/gvzdTdkIL1 And one LPE https://t.co/9FsdtQAwn1 And i finally reached goal of 50 cve's lol
8
14
173
Well that sucked. Yours truly is looking for work - reputable red teamer, pentester with 10 years experience. OSCP/GRTE certifications, also have experience with threat intelligence. Ex-JPMC/Optiv/TrustedSec
22
50
266
thanks to everyone who attended my #TheSAS2025 talk "Typographic hit job: when fonts pull the trigger". 🙏 I've written an accompanying blogpost that goes over all the details:
haxx.in
Last year we (PHP HOOLIGANS) competed in Pwn2Own (ireland, 2024) once again. One of our (succesful) entries was against a little pet peeve target of mine, the CANON ImageCLASS printer. In this post...
4
42
136
Interested in an alternative approach to sleep masking for you malware? Check-out our latest blog post "Function Peekaboo: Crafting self masking functions using LLVM" by @saab_sec
https://t.co/CTaydmHZi5
1
69
211
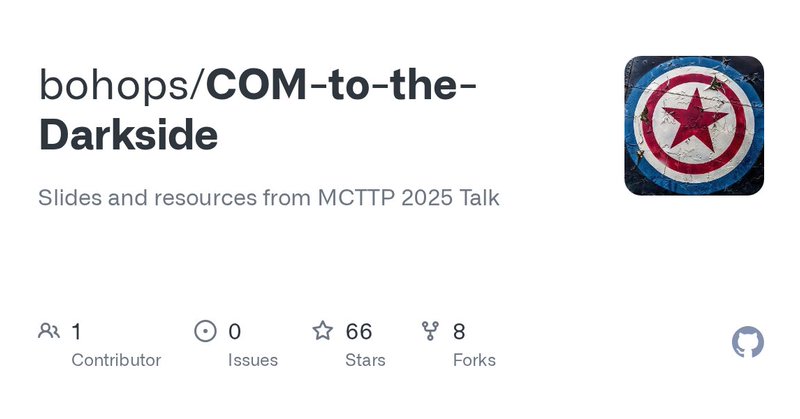
Last month, @d_tranman and I gave a talk @MCTTP_Con called "COM to the Darkside" focusing on COM/DCOM cross-session and fileless lateral movement tradecraft. Check out the slides here: https://t.co/1KNln1ldzF Recording should be released soon.
github.com
Slides and resources from MCTTP 2025 Talk. Contribute to bohops/COM-to-the-Darkside development by creating an account on GitHub.
1
80
251
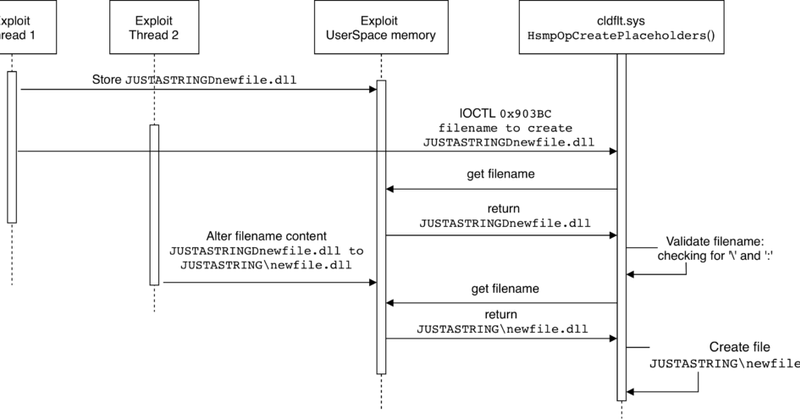
A zero day I found last year has been patched on October (CVE-2025-55680) :(, it was a nice and easy patch bypass. Here the write-up
blog.exodusintel.com
By Michele Campa Overview In this blog post we take a look at a race condition we found in Microsoft Windows Cloud Minifilter (i.e. cldflt.sys ) in March 2024. This vulnerability was patched in...
1
54
194
yIKEs, is it 2025? Join us today as we dive into WatchGuard’s CVE-2025-9252, a stack-based buffer overflow in the IKEv2 service. https://t.co/jlKSM8e6bb
labs.watchtowr.com
Note from editor: Before we begin, a big welcome to McCaulay Hudson, the newest member of the watchTowr Labs team with his inaugural blog post! Welcome to the mayhem, McCaulay! Today is the 8th of...
3
45
136
The @MDSecLabs red team is hiring! If you're an experienced red team operator interested in conducting multi-month operations within a small and technically gifted team reach out to us! ✊
3
29
149
Crafting a Full Exploit RCE from a Crash in Autodesk Revit RFA File Parsing: Trend ZDI researcher Simon Zuckerbraun shows how to go from a crash to a full exploit - & he provides you tools to do the same, including his technique used to get ROP execution.
zerodayinitiative.com
In April of 2025, my colleague Mat Powell was hunting for vulnerabilities in Autodesk Revit 2025. While fuzzing RFA files, he found the following crash ( CVE-2025-5037 / ZDI-CAN-26922 , addressed by...
0
31
167
‘DEXTER: RESURRECTION’ has been renewed for Season 2 at Paramount+
716
4K
53K
Red Treat was incredible. Thank you so much to @domchell @StanHacked @MarcOverIP for your hard work making another successful year. The calibre of content shared the conversations was 👌and @max__grim thanks for another swanky badge
#RedTreat2025 is a wrap @StanHacked @MarcOverIP - thanks to all the speakers and the panel team for an extra awesome con this year 🫶
2
2
21
#RedTreat2025 is a wrap @StanHacked @MarcOverIP - thanks to all the speakers and the panel team for an extra awesome con this year 🫶
5
7
71
This release is probably going to be one of our biggest and most impactful! Kudos to the team @peterwintrsmith @modexpblog @s4ntiago_p @GigelV41464 @saab_sec 🙌
3
14
101