Dave Cossa
@G0ldenGunSec
Followers
2K
Following
3K
Media
17
Statuses
845
Adversary Simulation @xforce/ Frequent reader of the first page of Google results / Occasional reader of the second page of Google results
USA
Joined September 2017
Azure Arc is Microsoft's solution for managing on-premises systems in hybrid environments. My new blog covers how it can it be identified in an enterprise and misconfigurations that could allow it to be used for out-of-band execution and persistence.
ibm.com
Explore how Azure Arc can be identified in environments, misconfigurations in deployment can allow for privilege escalation, an overprovisioned Service Principal can be used for code execution and...
7
84
190
Our initial access team has a deep dive blog out this week on creating .NET serialization gadgets by hand (or, alternatively, just using the new .NET deserialization library in VulnCheck's open-source go-exploit framework for your exploit dev needs)
vulncheck.com
Vulnerability intelligence that predicts avenues of attack with speed and accuracy.
0
39
100
If you're into serious red teaming with a crazy skilled team we've got a US based opening!
ibmglobal.avature.net
3
35
135
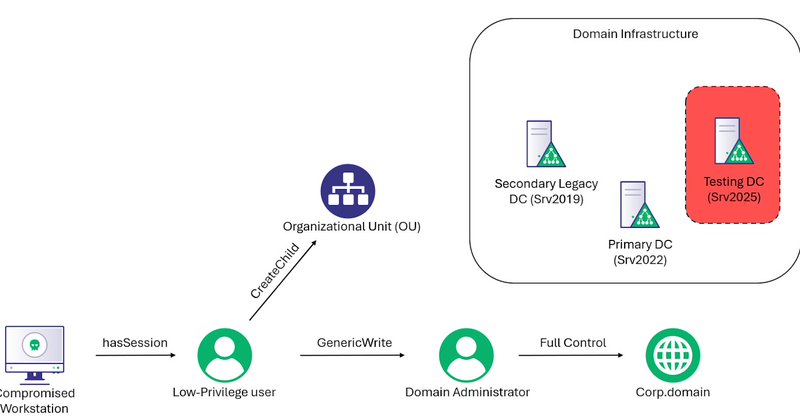
As a fun side project - I’ve started tracking vendors whose guides ask customers to create ESC1-style certificate templates, leaving an entire environment exposed 😅
medium.com
This post isn’t about vendor-bashing. With attacks against Active Directory Certificate Services (ADCS) increasing, I want to show how…
5
39
140
Venom C2 tool drop! 🐍 During a recent red team engagement we needed a simple python agent that needs no dependencies to setup persistence on some exotic boxes we landed on. Some had EDR so we didn't want anything off-the-shelf. The server, agent, and client were made
10
90
421
Any Canadian friends with strong red team backgrounds looking for an AdvSim spot? https://t.co/Ba8V6QcYoP
ibmglobal.avature.net
1
12
43
AdminSDHolder is kinda my jam. I wrote the e-book on it. If you work with Activity Directory, I highly recommend you give this a skim, or at least check the spoilers in the blog.
AdminSDHolder: the AD security feature everyone thinks they understand but probably don't. 😬 @JimSycurity went to the source code to debunk decades of misconceptions — including ones in Microsoft's own docs. Read more ⤵️ https://t.co/Vo9XksEfmn
2
34
195
Microsoft (kinda) deprecated DES in SCCM which caused some of the policy related tradecraft to break. The HTTP module in SCCMHunter and mssqlkaren have been updated to support AES-256. Thanks to @Blurbdust for helping get the fix into pxethief (which I stole from, ofc).
1
11
40
Today, I am releasing the COM-Fuzzer. Gain insights into COM/DCOM implementations that may be vulnerable using an automated approach and make it easy to visualize the data. https://t.co/RBVXP01UK4
github.com
Gain insights into COM/DCOM implementations that may be vulnerable using an automated approach and make it easy to visualize the data. By following this approach, a security researcher will hopeful...
4
60
205
Forget common backdoors — a DLL hijack in Windows Narrator can grant SYSTEM-level persistence at login. In our new blog, @Oddvarmoe shows how attackers abuse accessibility features and what defenders should monitor. Read now!
trustedsec.com
2
72
196
Last month, @d_tranman and I gave a talk @MCTTP_Con called "COM to the Darkside" focusing on COM/DCOM cross-session and fileless lateral movement tradecraft. Check out the slides here: https://t.co/1KNln1ldzF Recording should be released soon.
github.com
Slides and resources from MCTTP 2025 Talk. Contribute to bohops/COM-to-the-Darkside development by creating an account on GitHub.
1
80
251
Credential Guard was supposed to end credential dumping. It didn't. @bytewreck just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️
specterops.io
Uncovering the protection mechanisms provided by modern Windows security features and identifying new methods for credential dumping.
4
310
653
Coercing machine authentication on Windows 11 /2025 using the MS-PRN/PrinterBug DCERPC edition, since named pipes are no longer used. Kerberos fails in this case due to a bad SPN from the spooler, forcing NTLM fallback.
4
85
283
Remotely enable the EFS service for Win11 systems? No problem with rpcping. Just worked for me from remote with a low privileged user. 🧐
Service triggers can be a pentester’s secret weapon, letting low-priv users quietly fire up powerful services. In our new blog, @freefirex2 breaks down the types of service triggers that exist and how they can be activated with little to no code required.
2
44
213
I feel like @YuG0rd's briefly mentioned new dMSA account takeover mechanism in his last blog didn't get enough attention. A new account takeover mechanism is on the horizon. I wrote a blog detailing it, releasing with a new BOF I wrote called BadTakeover https://t.co/fyUkDYKAeP
specterops.io
After Microsoft patched Yuval Gordon’s BadSuccessor privilege escalation technique, BadSuccessor returned with another blog from Yuval, briefly mentioning to the community that attackers can still...
3
44
107
Service triggers can be a pentester’s secret weapon, letting low-priv users quietly fire up powerful services. In our new blog, @freefirex2 breaks down the types of service triggers that exist and how they can be activated with little to no code required.
trustedsec.com
Service triggers can be a pentester’s secret weapon, letting low-priv users quietly fire up powerful services like Remote Registry and EFS. Learn how they…
2
61
159
tooling link is kinda buried at the end of the blog. Standalone decryption POC: https://t.co/4vDuHiYFKS Integration into existing "decryptcredentials" method in SQLRecon: https://t.co/0lVAWOxufk (will also be merged into main SQLRecon)
gist.github.com
GitHub Gist: instantly share code, notes, and snippets.
0
3
17
Ever been on an SCCM site server and *this* close to a DA pw that you couldn't decrypt for some reason? Check out my new blog looking at encryption in use within SCCM sites configured for High Availability and accompanying tooling to recover passwords:
ibm.com
Follow IBM X-Force as they work out the secrets to decrypting credentials vaulted by Microsoft’s System Center Configuration Manager (SCCM).
3
59
141
Can we eliminate the C2 server entirely and create truly autonomous malware? On the Dreadnode blog, Principal Security Researcher @0xdab0 details how we developed an entirely local, C2-less malware that can autonomously discover and exploit one type of privilege escalation
9
104
342
Getting some downtime in EU post-@OffensiveAIcon . Thank you to all the community, sponsors, co-organizers, and speakers that helped make it such as amazing first year! A few more days to relax, then it’s back to the grind, exciting things coming!
0
5
24