Jim Sykora
@JimSycurity
Followers
3K
Following
206K
Media
2K
Statuses
19K
I enjoy security, technology, learning, books, & the great outdoors. Trying to be human & kind. Opinions = mine. He/Him/Hän
Minnesota, USA
Joined May 2019
Ope. Updated my profile to a custom domain. https://t.co/VNAQDJj5lK
0
0
0
BloodHound OpenGraph isn’t just about AD anymore. In his latest Risky Biz interview, @jaredcatkinson breaks down how OpenGraph now maps attack paths across GitHub, AWS, SaaS, CI/CD, and beyond, allowing defenders to see what attackers see. 🎧: https://t.co/RrzPKgQmJD
2
7
27
I'm so happy to see @NathanMcNulty voted the Security Super Star of the year and winning the Clippys at @wpninjasus So very well deserved Nathan! @m0bilej0n Folks, let's make this the @NathanMcNulty gratitude thread. Let him know how awesome he is in the replies.
49
13
194
Blogs are up!
Wanting more from today's #BHEU talk on SCOM? Check out this two part blog series! 1️⃣ @unsigned_sh0rt maps SCOM’s roles, accounts, & trust boundaries, then shows how attackers can chain insecure defaults into full management group compromise. https://t.co/Ai4TqTtc4O 🧵: 1/2
1
41
127
Wanting more from today's #BHEU talk on SCOM? Check out this two part blog series! 1️⃣ @unsigned_sh0rt maps SCOM’s roles, accounts, & trust boundaries, then shows how attackers can chain insecure defaults into full management group compromise. https://t.co/Ai4TqTtc4O 🧵: 1/2
specterops.io
TL:DR; SCOM suffers from similar insecure default configurations as its SCCM counterpart, enabling attackers to escalate privileges, harvest credentials, and ultimately compromise the entire manage...
1
47
116
bloodhound-cli from @SpecterOps is a sort of companion helper tool for BloodHound to perform actions like updating, starting, checking logs and config, resetting the admin password etc. https://t.co/qCFjXyp0Gd (binaries available)
0
10
31
Stack spoofing isn’t dead. Hear from @klezvirus at #BHEU on how modern detection still breaks, and unveils the first CET-compliant stack spoofing framework. Learn more ➡️ https://t.co/3ffbujgNPE
2
21
44
SCOM monitors critical systems, but insecure defaults make it a powerful attack vector. At #BHEU, @unsigned_sh0rt & @breakfix show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. https://t.co/bxW5PYyhyl
0
31
70
SCOM monitors critical systems, but insecure defaults make it a powerful attack vector. At #BHEU, @unsigned_sh0rt & @breakfix show how to abuse SCOM for credential theft, lateral movement, and domain escalation, plus how to defend it. https://t.co/bxW5PYyhyl
3
39
134
Wake up, it's Wednesday! Join us for today's Wednesday Offensive with @JimSycurity discussing AdminSDHolder! See you at 130pm ET 🔗 https://t.co/HgPkoGT5M7 If you can't make it (or even if you can) be sure to check out Jim's whitepaper on AdminSDHolder 🔗 https://t.co/hRz5qrc2Pd
2
1
7
Don't miss @JimSycurity TOMORROW on The Wednesday Offensive as he discusses his new e-Book, "AdminSDHolder Misconceptions and Misconfigurations." Read the e-Book ➡️
specterops.io
AdminSDHolder is an object and associated process in Active Directory Domain Services (AD DS) that helps protect specific sensitive and highly privileged accounts from being manipulated. This topic...
🔔 Friendly neighborhood reminder 🔔 Tomorrow on The Wednesday Offensive we have @JimSycurity talkin about AdminSDHolder! Join the conversation at 130pm ET 🔗 https://t.co/HgPkoGTDBF
#hacking #infosec #cybersecurity
0
2
19
🔔 Friendly neighborhood reminder 🔔 Tomorrow on The Wednesday Offensive we have @JimSycurity talkin about AdminSDHolder! Join the conversation at 130pm ET 🔗 https://t.co/HgPkoGTDBF
#hacking #infosec #cybersecurity
0
2
4
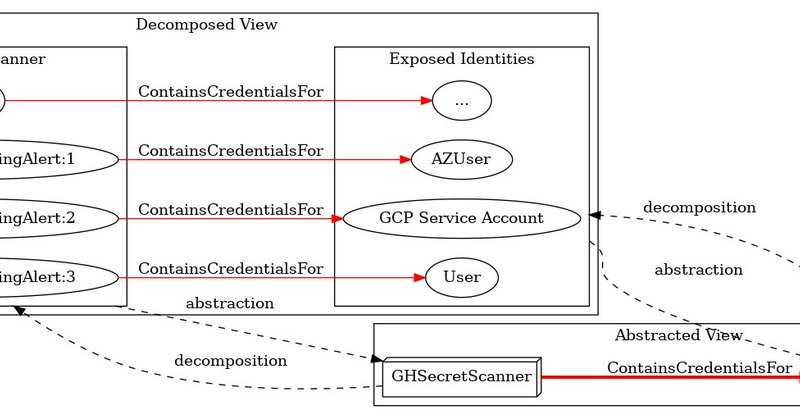
Released my first blog post today: https://t.co/fQDVp2XKyn And released SecretHound, a BloodHound OpenGraph extension for secrets: https://t.co/tFZQOOPFBM
specterops.io
Presents a framework using technology subgraphs, decomposition, and graph abstraction to model hybrid attack paths in BloodHound OpenGraph.
0
40
111
See ya next week on the Wednesday Offensive!
Great discussion today about unique methods for exfiltration using Microsoft services! Next week we have @JimSycurity discussing AdminSDHolder See you next Wednesday at 130pm ET 🔗 https://t.co/HgPkoGTDBF
#hacking #infosec #cybersecurity
1
0
3
November 13th meeting details are up! Join us to hear Meander's talk "Back to Basics: Why we get it wrong, and how to get it right" Details below: https://t.co/wfxwZPq99E
0
2
3
This is (probably) the last time I‘ll nag you with TaskHound. Since my org doesn’t allow me to use memes in our official blogs I finally took the hint and stopped procrastinating. My personal Blog is now live :). https://t.co/Sp2aj2Y0EO (Disclaimer: may contain sarcasm and memes)
2
20
84
The Azure AD Broker plays a key role in Entra ID sign-in & token handling, but how well do we really understand it? @winternl_t unpacks its on-disk cache, how to decode it, & the security implications. 🔐
specterops.io
This post documents the AAD Broker's storage format, how to unpack it, and discusses potential security implications.
1
34
104
AdminSDHolder is kinda my jam. I wrote the e-book on it. If you work with Activity Directory, I highly recommend you give this a skim, or at least check the spoilers in the blog.
AdminSDHolder: the AD security feature everyone thinks they understand but probably don't. 😬 @JimSycurity went to the source code to debunk decades of misconceptions — including ones in Microsoft's own docs. Read more ⤵️ https://t.co/Vo9XksEfmn
2
34
195
Got an idea for a @BSidesCharm 2026 Village? Submit it to our CFV - opening on Fri, 10/31 @ 2000 - keep this link handy - https://t.co/ZMd0fDAsM2
0
3
3
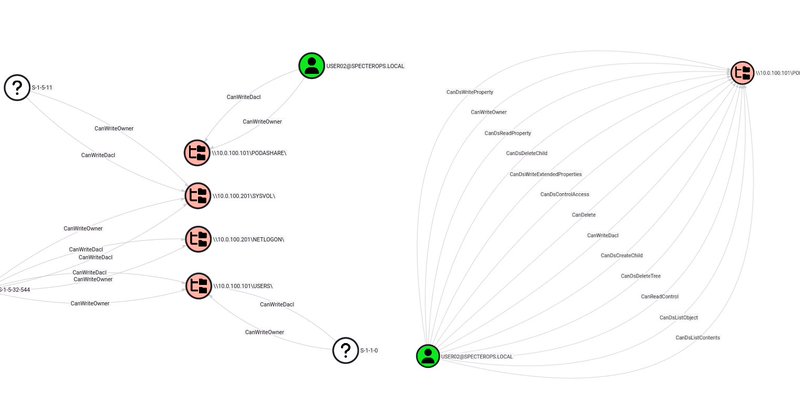
I have released an OpenGraph collector for network shares and my first blogpost at @SpecterOps on the subject! You can now visualize attack paths to network shares in BloodHound 👀 https://t.co/2e2DBIndcU
specterops.io
ShareHound is an OpenGraph collector for BloodHound CE and BloodHound Enterprise helping identify attack paths to network shares automatically.
3
94
225
I'm SO hyped to finally make MSSQLHound public! It's a new BloodHound collector that adds 37 new edges and 7 new nodes for MSSQL attack paths using the new OpenGraph feature for 8.0!. Let me know what you find with it! - https://t.co/Hh089SaVOS - https://t.co/geO0HXTykf
6
215
632