Dylan Tran
@d_tranman
Followers
2K
Following
2K
Media
52
Statuses
314
salsa sultan, verde villain, condiment connoisseur Adversary Simulation @xforce Red Team @wrccdc Former: @NationalCCDC+@wrccdc & @globalcptc @calpolyswift
please dont hurt me
Joined June 2020
Had a lot of fun digging into COM stuff with @bohops recently! We ended up finding a way to laterally move without dropping a file. https://t.co/F6NahVpuHP
ibm.com
New research from IBM X-Force Red has led to the development of a proof-of-concept fileless lateral movement technique by abusing trapped Component Object Model (COM) objects. Get the details.
12
177
532
This was a really fun talk. It was even more fun rewriting all my slides 3 AM the day we were speaking.
Last month, @d_tranman and I gave a talk @MCTTP_Con called "COM to the Darkside" focusing on COM/DCOM cross-session and fileless lateral movement tradecraft. Check out the slides here: https://t.co/1KNln1ldzF Recording should be released soon.
2
4
27
I feel like @YuG0rd's briefly mentioned new dMSA account takeover mechanism in his last blog didn't get enough attention. A new account takeover mechanism is on the horizon. I wrote a blog detailing it, releasing with a new BOF I wrote called BadTakeover https://t.co/fyUkDYKAeP
specterops.io
After Microsoft patched Yuval Gordon’s BadSuccessor privilege escalation technique, BadSuccessor returned with another blog from Yuval, briefly mentioning to the community that attackers can still...
3
44
106
We're putting out the transcript for our talk - Deductive Engine: Human Inspired Taint Reasoning at OffensiveAICon. Have fun reading! https://t.co/ye08VRKpYT
research.pwno.io
This is a transcription for the talk Deductive Engine - Human Inspired Taint Reasoning on Offensive AI Con (OAIC), fantastic conference and great talks! (one of my favorite venue - Oceanside, San...
0
7
31
Ever been on an SCCM site server and *this* close to a DA pw that you couldn't decrypt for some reason? Check out my new blog looking at encryption in use within SCCM sites configured for High Availability and accompanying tooling to recover passwords:
ibm.com
Follow IBM X-Force as they work out the secrets to decrypting credentials vaulted by Microsoft’s System Center Configuration Manager (SCCM).
3
59
140
kernel hackers go serverless ring0 → cloud 9 ☁️ ?? brb pwning yr gpu nodes ✨
25
123
623
Proud to have you here @bohops & Dylan Tran #mcttp #hansesecure #meetfriends #itsecurity
@HanseSecure
3
9
24
You want to load your shellcode in .NET without calling VirtualProtect? Use RuntimeHelpers.PrepareMethod to create a predictable RWX memory region for you. This method also doesn't require a delegate function pointer, since you override a .NET method. https://t.co/8oavXwyGEv
github.com
load shellcode without P/D Invoke and VirtualProtect call. - Mr-Un1k0d3r/DotnetNoVirtualProtectShellcodeLoader
2
94
336
Excited to be presenting "Keep COM and Hijack On: Redefining Windows Session Hijacking" at Black Hat Arsenal Europe this December. Looking forward to connecting with many of you there! 🤟 https://t.co/QPV9dUpqru
1
14
57
Super excited for this!
In 3 weeks, @d_tranman and I will be giving our talk, "COM to the Darkside" at @MCTTP_Con in the Offensive Track. The talk will focus on 90's MCP technology and will deep dive into some fun (D)COM topics. See you there!
1
1
29
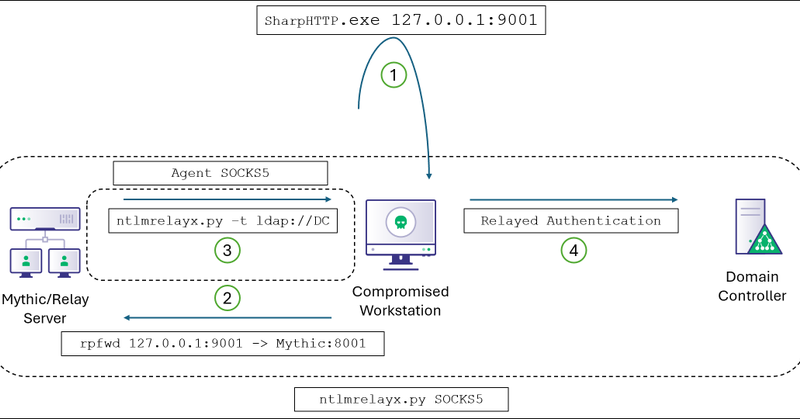
I Just documented a cool way to authenticate proxied tooling to LDAP in an AD environment using C2 payload auth context, without stealing any tickets or hashes! Keep tooling execution off-host and away from EDR on your Red Team assessments! https://t.co/VLE2Kh4idY
specterops.io
TL;DR When operating out of a ceded access or phishing payload with no credential material, you can use low-privilege HTTP authentication from the current user context to perform a proxied relay to...
5
118
412
Hi everyone, I was the captain of the the captain of the winning team for the 20th NCCDC season. Over the past few months, I’ve taken the time to write up my advice, experiences, and concerns about CCDC in a blog. You can read here: https://t.co/x9FGe0esBb
#CCDC #cybersecurity
akshayrohatgi.com
A recollection of every strategy and philosophy that took me as far as one can possibly go in CCDC, paired with honest critiques and observations regarding the competition itself.
0
3
4
Shoutout to @nos3curity @bri5ee @baseq_twt @_c0ve for teaching me how to SSH, HTB, etc. 4 years ago. its been a fun road since
1
0
26
full time time. i can't use the intern code excuse anymore GG
20
2
114
My first @SpecterOps blog! Ever wanted to collect Active Directory information from LDAP for a Red Team? Using LDAP's more OPSEC-considerate cousin: ADWS can be used to improve upon the already present advantages of using smaller-scaling LDAP queries. https://t.co/6SFxGDpQkL
specterops.io
Learn how to perform stealthy recon of Active Directory environments over ADWS for Red Team Assessments
1
105
336
Call For Speakers closes this Friday 7/18. Tell your friends. Tell your favorite offensive AI researchers. 🏃💨
sessionize.com
The first conference dedicated to offensive AI cybersecurity, coming to Oceanside, San Diego October 5-8, 2025.Offensive AI Con is an invite-only tech...
0
12
16
Azure Arc is Microsoft's solution for managing on-premises systems in hybrid environments. My new blog covers how it can it be identified in an enterprise and misconfigurations that could allow it to be used for out-of-band execution and persistence.
ibm.com
Explore how Azure Arc can be identified in environments, misconfigurations in deployment can allow for privilege escalation, an overprovisioned Service Principal can be used for code execution and...
7
84
189
This is my research project in creating read, write and allocate primitives that can be turned into an injection in order to evade certain telemetry which I presented last year in RedTreat. I hope everyone likes it \m/. https://t.co/GY37MMfCGl
trickster0.github.io
It has been a while, this is my research on trying to change the IOCs of a common remote process injection flow and the end result. I presented this in RedTreat in 2024 and I thought it was about...
6
93
263