Johan Carlsson
@joaxcar
Followers
4,172
Following
156
Media
95
Statuses
1,127
Father and developer during the day, looking for bugs at night 🐞. Using Twitter for infosec only. Also on: @joaxcar @infosec .exchange
Joined January 2022
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Rafah
• 851978 Tweets
#เพลงขึ้นใจ
• 524014 Tweets
GW最終日
• 461263 Tweets
NUNEW 3RDMV IS OUT
• 277489 Tweets
#マリカにじさんじ杯
• 253556 Tweets
#CDTVライブライブ
• 233484 Tweets
ENGFA IN NUNEW 3RDMV
• 205762 Tweets
井上尚弥
• 199720 Tweets
Inoue
• 139960 Tweets
シェリン
• 101697 Tweets
マリカ杯
• 62679 Tweets
フルサイズ
• 59686 Tweets
ボクシング
• 48792 Tweets
#ドレミファドン
• 37201 Tweets
モンスター
• 30082 Tweets
#BF_Masterplan
• 28548 Tweets
ジェシー
• 20632 Tweets
ハマスタ
• 16870 Tweets
井上の試合
• 16310 Tweets
井上ダウン
• 14986 Tweets
井上選手
• 13077 Tweets
筒香ホームラン
• 12745 Tweets
逆転ホームラン
• 10795 Tweets
逆転3ラン
• 10648 Tweets
マリカ事変
• 10508 Tweets
Last Seen Profiles
Pinned Tweet
I joined
@gregxsunday
on his podcast a while back. Realized I did not have a tweet with it to “pin”. Here is that tweet. Good intro to what I am doing if someone is curious
1
13
90
Yesterday I made it into top 5 on
@GitLab
bug bounty program 🥳, at the same time crossing 100k in bounties from the same.
Some people are asking me how to get started or where and what to look for. I thought I could share a practical guide if anyone care for a thread [1/6]
26
172
940
My first disclosure to reach 100 up-votes on
@Hacker0x01
. Disclosures have been the number one learning resource for me, so to see people finding an interest in my own reports makes me happy! Also thanks
@gitlab
for allowing full disclosures, contributing to this great resource
6
21
259
Another amazing
@fransrosen
report to study! Guess the arkoselabs[.]com XSS impacted a lot more sites, but nice usage of it here on GitLab in chain to ATO
1
33
163
Finally made it past 3000 reputation. The last 1k took a long time as I have had less time to hunt. For information 3k puts you at top 550 at
@Hacker0x01
, and miles from top 100
11
1
135
I'm glad to see that quite a few people found this interesting!
My solution (and the one that others found) goes like this:
\"-alert(1)}})<!--
1
13
115
Nice bug! Don't really like this "its a third party tool" argument to lower the bounty, think the impact should be the measurement. Always good to look for mentions of this in the program scope
7
9
113
This one was weird "we had a regression and many others reported it, so we will lower the bounty to 10%". I mean, either you have a vulnerability or you dont. Blaming regression was a new one..
13
7
87
@G0LDEN_infosec
@aszx87410
@terjanq
@kevin_mizu
@garethheyes
are a good start. Gareths book, the three other have a lot of posts on blogs etc. Things like this
2
31
87
What about
x.y.z("test-INJECT")
should not be too hard
15
13
80
This report to GitLab by
@ryotkak
shows a great way to use the "dirty dance none happy path OAuth feature", discussed in
@fransrosen
's blog post, to escalate a chain of open redirects to account takeover
1
19
74
Some personal highlights 2022 on
@gitlab
:
- Most valid reports in 2022 (22)
- Made it to top 4 on leaderboard
- 120k bounties
- At least one valid report per month
Great program, great team!
5
0
73
Another XSS in
@GitLab
. This one used an unsanitized URL for the payload, and a poorly sanitized HTML element to increase the impact probability. Delivered to the GitLab server by a spoofed ZenTao server.
2
7
73
Until recently I have taken zero notes and have to re-google everything all the time. The new me is using
@GitLab
to structure my research 😎
Thanks go out to
@realArcherL
,
@dee__see
, and
@ajxchapman
for amazing tips in
2
22
72
Here we go again! Still no sign of the 20% policy in the policy
@Hacker0x01
😊. Clear rules are important, the guy here spent a lot of extra time working on this issue without info about the hidden rules..
2
4
68
I spent quite some time on this challenge bu
@kevin_mizu
. Ended up finding a new jQuery CSPP gadget using $().on() event creation
Did a writeup on the process of finding the gadget 👇
1
11
66
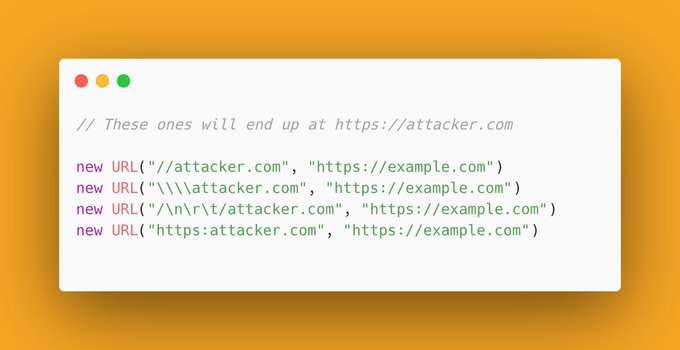
There are some good and common ways to gain redirects, like "@" and "." but I have also had a lot of success with "//". A lot of simple filters check if the URL is "relative" by checking if it starts with a slash, forgetting that //attacker[.]com is not relative.
Freaking good redirect validation bypass payload:
http://attacker[.]com\@test[.]com
The backslash will be normalized to a slash by the browser and result in the OR. I see this issue a lot.
(Obviously [.] is not a part of the payload, it prevents X from turning it into a link)
3
23
176
1
8
67
Great talk by
@spaceraccoonsec
outlining how to approach the changing landscape of bug-bounty/infosec. The point about plateauing in skill level by getting stuck finding and reporting similar bugs really resonated with me.
0
16
57
Great post by
@garethheyes
. I have used the form trick multiple times. I also find it strange that does not include it in their "safe example" (or as a warning). This could be one of the reasons why it's so often overlooked
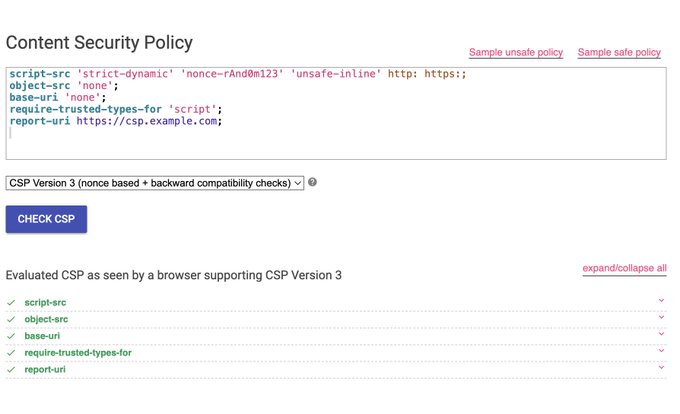
Are CSP's getting in the way of scoring that Bug Bounty you have been working on? 😫
Lucky for you, our research team (
@PortSwiggerRes
) has released some new techniques using Form Hijacking to bypass that protection and get you hacking again; enjoy!
2
60
233
1
6
57
A bit of an older interview, but wow this was gold! Thanks
@NahamSec
and
@spaceraccoonsec
for sharing (years ago)
1
11
56
Tweet explained
1. reportError is "new" as of Chrome 95
2. It only takes 1 argument. The second arg here is just an inline assignment
3. You need the = before alert as the string produced by the error is "Uncaught <payload>" and eval needs valid syntax
Nice one! Fun to dig into
5
4
55
Found a duplicate high severity bug on
@GoogleVRP
. Will nevertheless count it as my first valid bug on their program 🥳
Getting that duplicate email is not a great feeling, but it at least shows that finding Google bugs are not out of reach
2
1
53
Must admit, I did not know what this Hackvertor thing by
@garethheyes
was all about. After watching this video, I will not be able to live without it! 🙇♂️
1
6
52
Finally got another payout! I can now pay my salary for April as well 😅
@joernchen
no, I have only had to pay myself for one month so far. The next one is due in a week. Let's pray for some more payouts! (on a serious note, I had the economy for all months from the get-go and would not have done this otherwise). But it did pay more than my day job
1
0
4
4
2
51
From what I can see this is just an UI bug. I would recommend
@Hacker0x01
to fix this promptly as a lot of people are getting confused and making allegations against triagers (tip: dont!). The dupe is same program (all the time)
@jobertabma
#bugbountytip
1
1
49
Nice and clean XSS in GitLab. Worth noting here that the CSP bypass works for all scripts generated by other scripts decorated with a valid nonce. The trust is inherited. In this case jQuery is loaded with a nonce. Included scripts are a great place to look for CSP bypasses
0
5
47
@garethheyes
@Rhynorater
@avlidienbrunn
@jub0bs
@LiveOverflow
Hey thanks for inspiration!
x.y(alert(1));function x(){}
5
5
46
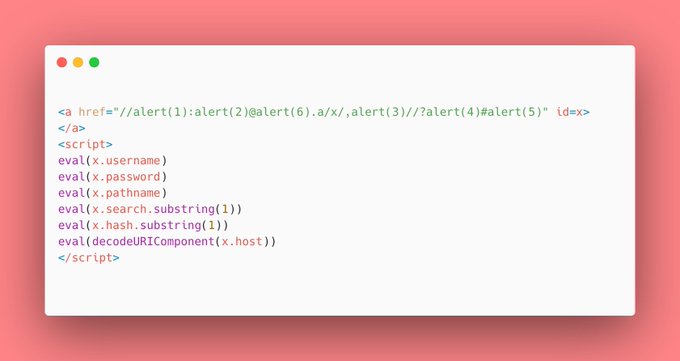
Let's keep the inspiration flowing. The last three could probably be done better, but I am quite happy with the pathname one.
Wait. What. Hehe.
https://alert(1)@
example. com
<a href=/ id=x>test</a>
<script>
eval(x.username)
</script>
Inspired by:
4
22
175
2
7
46
This is what deep knowledge of your target can do for you while hunting for bugs! Another amazing escalation of a "trivial issue" by
@wcbowling
Getting at the
@gitlab
CTF flag
0
6
46
If you follow these steps you will have learned a LOT about security, DOS issue, GitLab, setting up environments and replicating vulnerabilities. You will also most certainly be in a great position to finding your first bug on the GitLab
@Hacker0x01
program. [6/6]
2
3
44
This report is a great example of the goldmine that
@Hacker0x01
Hacktivity is. The report is a bit confusing, and it took a couple of tries to recreate based on the description. But I had never heard of the Service Worker API before, learning so much from this one!
0
5
43
@renniepak
@0xH4rmony
<script/src="//0-a%2enl"></script>
34 chars, browsers are nice enough to correct the missing space
3
6
40
Another great post on hoisting by
@brutelogic
! Missed this one when doing my own research. Interestingly the payload from my post work on the second example (undefined2.php) without hijacking atob
%27-alert(1));function%20myObj(){}//
2
5
40
Not the most advanced bug, but a good one to look for. I have found multiple instances of this in multiple programs. The bug type is also covered in
We all know path traversals. But did you hear about a client-side path traversal? There are few resources about this bug class so many hackers don't check for it. Don't be one of them! Start by watching my explanation of
@joaxcar
's $6,580 bug in GitLab!
3
28
136
0
9
40
This right here! Not that I ever found a RCE, but this mindset applies to other bug types. For me XSS is part of impact. Bugs that lead me there are usually HTML injections
@intigriti
It’s depends how you look for RCE
Some look for RCE as bug
Some look for RCE as impact
As example LFI to RCE (the bug is LFI and the Impact is RCE)
I look for RCE as impact not bug
& I automate on bugs that can led for RCEs
6
19
170
3
7
39
@IM_23pds
It's fake, the writeup is just a rewrite of this one and is also not getting it right. The bug is not in Grafana, it was in Aiven. Don't know why anyone would do this
6
3
39
Great interview with
@samm0uda
by
@gregxsunday
. Youssef's approach to bug bounties really resonates with me, will come back and rewatch this one for sure. Thanks for taking the time Youssef!
Last week, I published a video saying $5.5k is my highest bounty. Today, I’m uploading an interview with a hunter who doesn’t bother reporting $4-5k bugs and only focuses on the big ones. It's
@samm0uda
, TOP1 on Facebook leaderboard since 2020. Enjoy!
12
54
322
0
6
36
Turns out that the last one is wrong. That trick only works if you change the schema in the new URL
new URL("http:a.a","
https://b.b")
new URL("https:a.a","
http://b.b")
or
new URL("file:etc/passwd","
https://b.b")
1
10
35
It's been a long winter... I also realized I had broken the challenge... well here is the long-awaited solution.
"in%0balert%60%60in"
or in plain English
"in(mysterious space)alert``in"
1
5
36
@Rhynorater
using XSS to add a form and steal autofill password 🙂
this one can sometimes bypass some other restrictions, like XSS on a subdomain. But requires a great program, a great PoC, and some smooth report writing!
1
2
33
@PinkDraconian
@PortSwigger
Yes, but if you have XSS you can do this by just adding your own form, no need to find a form
document.body.innerHTML = `<form><input><input id=x type=password></form>`
alert(x.value)
4
0
31
Had a fun chat with
@gregxsunday
, not used to the audio format so it starts out a bit stumbling on my part, but hope someone might get some enjoyment out of it 😊
Other people's reports are a great learning resource but it's even better to ask them about methodology and techniques.
From my interview with
@joaxcar
, you will learn why he was successful in bug bounty since day one and how he climbed to GitLab's TOP4
3
21
114
2
1
32
Programs should just stop shoehorning everything into CVSS. A “one off” leak of some random data can have impact ranging from informative to critical. Just keep a separate bounty table for leaks, and you dont have to bend CVSS to match what you want to pay
@disclosedh1
@bebiksior
While I do agree with the overall assesment of medium severity, the reasoning they give for the CVSS is pretty shit.
Setting user interaction to required with the reasoning : "A staff member that owns the form misconfigured permissions which lead to being able to access the…
4
2
57
0
4
27
@caseyjohnellis
Then, give us the actual purpose!? 😀
Are platforms hosting the VDPs for free? Or BB programs, for that matter. It better not be that platforms are doing this to profit 🤯
Sry for sarcasm, but sometimes it sounds like hunters are the only ones trying to monetize this space
3
2
30
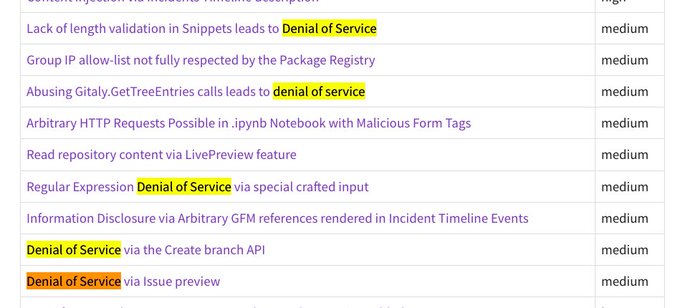
In this thread, I gave the advice to look for DOS bugs in GitLab. Looking through subsequent security-releases that was great advice! Too bad it is really hard to follow even ones own advice sometimes 😀
2
1
27
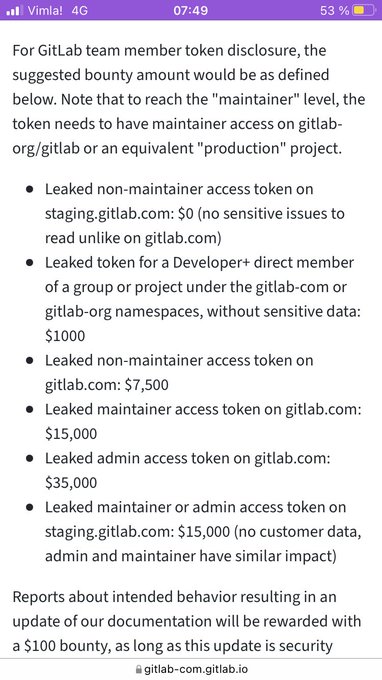
@therceman
You can read about their bounty calculation here
These levels are usually for GitLab tokens giving access to their own repos. But you're right they do not accept other user tokens, so do not report those
2
4
26
This will be my first LHE. Super excited! Also super nervous... looking forward to meeting some of the hackers that I have admired since starting on this journey into cybersecurity
Gear up, cyber knights! ⚔️
The countdown begins for the Knights of Elektron Live Hacking Event, a collaboration between Intigriti and
@IntelSecurity
's Project Circuit Breaker! 🌐
The upcoming live hacking event will be unlike anything they’ve ever done before. This Friday,…
6
29
92
2
0
26