huli
@aszx87410
Followers
5K
Following
5K
Media
163
Statuses
3K
Taiwan / Front-end Engineer <=> Security Researcher. Interested in web. CTF player at @Water_Paddler
Joined January 2016
🚀Exciting News! Introducing my latest work: Beyond XSS. This series of articles aims to introduce front-end security topics, perfect for frontend devs and those intrigued by frontend security. Suitable for all skill levels from beginners to intermediates.
aszx87410.github.io
As a software engineer, you must be familiar with information security. In your work projects, you may have gone through security audits, including static code scanning, vulnerability scanning, or...
4
84
290
RT @kevin_mizu: I'm happy to release a script gadgets wiki inspired by the work of @slekies, @kkotowicz, and @sirdarckcat in their Black Ha….
0
154
0
RT @terjanq: For this year Google CTF I created yet another Postviewer challenge called Postviewer v5². The challenge featured a seemingly….
gist.github.com
Postviewer v5 writeup - Google CTF 2025. GitHub Gist: instantly share code, notes, and snippets.
0
38
0
RT @J0R1AN: Double-Clickjacking, or "press buttons on other sites without preconditions". After seeing and experimenting with this techniqu….
jorianwoltjer.com
Combing a lot of browser tricks to create a realistic Proof of Concept for the Double-Clickjacking attack. Moving a real popunder with your mouse cursor and triggering it right as you're trying to...
0
48
0
RT @slonser_: Today I used a technique that’s probably not widely known in the community. In what cases could code like this lead to a vuln….
0
178
0
RT @intenttoship: Blink: Intent to Deprecate and Remove: Remove auto-detection of ISO-2022-JP charset in HTML.
0
25
0
RT @tyage: In addition to this amazing discovery, there was another middleware bypass with the `__nextLocale` URL query that was fixed in 2….
gmo-cybersecurity.com
Another (A Bit Earlier) Next.js Middleware Bypass Vulnerability: CVE-2024-51479 についてのページです。セキュリティブログでは、脆弱性診断技術やサイバーセキュリティに関する情報を発信しています。イエラエセキュリティはWEB・スマートフォンアプリの脆弱性診断(セキュリティ診断)、ペネトレーションテストなどハッカーによ...
0
23
0
RT @rootxharsh: New Blogpost - We identified a vulnerability in Discourse where a misconfiguration in Rails send_file + Nginx's internal di….
0
36
0
RT @zhero___: while waiting for the big article to come (soon), I share with you a small article concerning a small research which led to a….
0
29
0
RT @osec_io: NEW: A few months ago, we uncovered an authentication bypass in Web3Auth that could have led to full account takeover. In thi….
0
36
0
RT @salvatoreabello: It's possible to do CSS exfiltration under default-src: 'self'. Learn how:
0
9
0
RT @kevin_mizu: For this challenge, it was necessary to abuse a discrepancy between the DOM and the rendered page in Firefox's cache handli….
0
22
0
RT @gregxsunday: Cross-Site POST Requests Without a Content-Type Header by @lukejahnke.#BBRENewsletter85
https://t.….
0
14
0
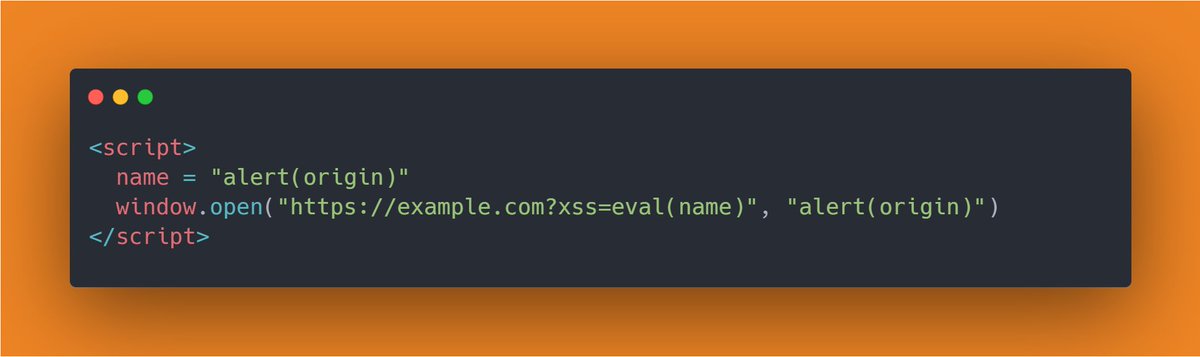
RT @icesfont2: x = open("/");.setTimeout(() => {.x.history.pushState(1,1,"/cookie");.setTimeout(() => {.x.location = "javascript:'zzz'";.se….
0
5
0
RT @kevin_mizu: My @HeroCTF #web challenges write-ups are now available! :D. Here's a short list of the topics cov….
0
32
0
RT @kinugawamasato: Here is a bypass fixed in DOMPurify 3.1.7. It works only if special settings are used. Notice why the comment is closed….
0
49
0
RT @ambionics: At long last: Iconv, set the charset to RCE (part 3): in this final part of the iconv series, @cfreal_ demonstrates how you….
ambionics.io
In this blog post, we will explore how we can exploit CNEXT, but blind, covering the cases where we have a file read primitive, but cannot get the output.
0
55
0
finally finished my writeup(more like a note actually) for a few interesting web challenges in HITCON CTF & corCTF & sekaiCTF 2024. I didn't play all the challenges but still learn a lot from the writeup/solutions posted by others.
blog.huli.tw
It’s been a while since I wrote writeup. I’ve wanted to write for a long time but kept procrastinating. For something like CTF writeups, speed is quite important because most discussions happen in Dis
1
30
117