Mathias Karlsson
@avlidienbrunn
Followers
17K
Following
2K
Media
28
Statuses
1K
Web security fiddler. Bug bounty bastard. Sometimes I cut shapes.
Joined December 2011
RT @kevin_mizu: I'm happy to release a script gadgets wiki inspired by the work of @slekies, @kkotowicz, and @sirdarckcat in their Black Ha….
0
162
0
RT @slonser_: My new research.Escalation of Self-XSS to XSS using modern browser capabilities.
blog.slonser.info
Disclaimer: This article is intended for security professionals conducting authorized testing within the scope of a contract. The author is not responsible for any damage caused by the application of...
0
180
0
Inspired by @gynvael old stream here (although tool cant help with all tricks described. yet :) ). You should watch it.
0
1
12
I made a tool to help test archive (zip/tar) extraction bugs (synk working directory into archive, add path traversals, links, permissions, etc):
github.com
Archive Alchemist is a tool for creating specially crafted archives to test extraction vulnerabilities. - avlidienbrunn/archivealchemist
1
31
171
RT @slonser_: Today I used a technique that’s probably not widely known in the community. In what cases could code like this lead to a vuln….
0
179
0
RT @kalmarunionenDM: #𝗞𝗮𝗹𝗺𝗮𝗿𝗖𝗧𝗙 𝟮𝟬𝟮𝟱 𝗶𝘀 𝗷𝘂𝘀𝘁 𝗮𝗿𝗼𝘂𝗻𝗱 𝘁𝗵𝗲 𝗰𝗼𝗿𝗻𝗲𝗿 - 𝗰𝗼𝗺𝗲 𝗰𝗼𝗺𝗽𝗲𝘁𝗲 𝘄𝗶𝘁𝗵 𝘁𝗵𝗲 𝗯𝗲𝘀𝘁 𝗰𝗼𝗺𝗽𝗲𝘁𝗶𝘁𝗶𝘃𝗲 𝗵𝗮𝗰𝗸𝗲𝗿𝘀 𝗳𝗿𝗼𝗺 𝗮𝗿𝗼𝘂𝗻𝗱 𝘁𝗵𝗲 𝘄𝗼𝗿𝗹𝗱 𝗮𝗻𝗱 𝘄….
0
24
0
RT @ryotkak: I recently developed and posted about a technique called "First sequence sync", expanding @albinowax's single packet attack.….
flatt.tech
Introduction Hello, I’m RyotaK (@ryotkak ), a security engineer at Flatt Security Inc. In 2023, James Kettle of PortSwigger published an excellent paper titled Smashing the state machine: the true...
0
247
0
RT @kinugawamasato: found an interesting way to read text placed on the closed shadow DOM.
github.com
This trick only uses a local font installed by default. No need to use remote fonts or SVG fonts. I wrote the details in the comments of the PoC below. The basic idea comes from https://demo.vwzq.n...
0
14
0
RT @thomasrinsma: Just released the write-up for CVE-2024-4367, a bug I found recently in PDF.js (and hence in Firefox), resulting in arbit….
codeanlabs.com
A vulnerability in PDF.js found by Codean Labs. PDF.js is a JavaScript-based PDF viewer maintained by Mozilla. This bug allows an attacker to execute arbitrary JavaScript code as soon as a malicious...
0
225
0
RT @pilvar222: My talk for @1ns0mn1h4ck is now available on youtube! Hope you'll enjoy it! :D.
0
58
0
RT @dustriorg: Solution to WMCTF2020's Make PHP Great Again 2.0, or how to use filters with `require_once` —
0
14
0
RT @garethheyes: I've built a brand new version of my fuzzing tool Shazzer🚀. - Easy fuzz browser behaviour.- Find….
shazzer.co.uk
An app to enable to fuzz all sorts of browser behaviour. Share your fuzz results with the world and discover new bugs!
0
93
0
RT @bbuerhaus: Reversing and Tooling a Signed Request Hash in Obfuscated JavaScript. Thanks to @hackinghub_io for….
0
162
0
RT @samwcyo: This tweet reminded me of a time when I was hacking on Apple's bug bounty program. I found, of all things, a base64 encoded Ha….
0
239
0
RT @aszx87410: I haven't played CTF for a while cause I am busy with other stuff like new job and moving to a new place(I am in Tokyo now!)….
blog.huli.tw
Due to being busy lately, I haven’t been participating in CTFs as much in the past two or three months. However, I still come across some interesting challenges on Twitter. Even though I don’t have ti
0
38
0
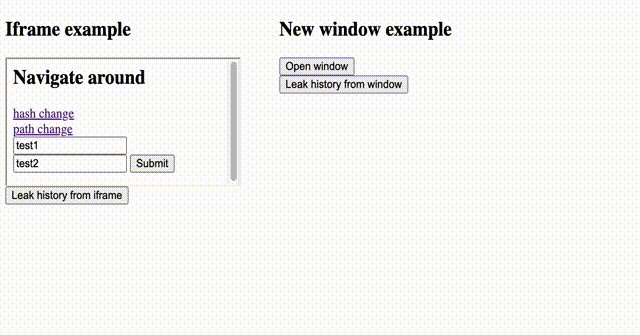
RT @joaxcar: I have finally done my first proper bug write-up! This one is about a SOP bypass in Chrome (escalated to ATO) using the Naviga….
joaxcar.com
Last year, I discovered a Same-Origin Policy (SOP) bypass in Chrome that allowed an attacker to leak the full URLs of another window’s navigation history. While attacks could be conducted cross-ori...
0
109
0
RT @WeizmanGal: So the implementation for the challenge was not great (my bad!) but I did see some interesting answers, as well as the one….
0
4
0