Intigriti
@intigriti
Followers
199K
Following
17K
Media
4K
Statuses
13K
Bug bounty & VDP platform trusted by the world’s largest organisations! 🌍
Joined May 2016
A full week into #BugQuest2025! 🔥 Yesterday, we shared a quick (and simple) tip to uncover hidden directories. Today, we're taking content discovery a step further by fuzzing with multiple HTTP methods! 🤠 Many endpoints and API routes are configured to respond only to
1
3
31
APOL1 Genetic Testing at No Cost to Patients! Are you incorporating APOL1 genetic testing into your workflow? Discover No-Cost APOL1 Genotyping Program for eligible patients sponsored by Vertex Pharmaceuticals. Learn more today!
17
35
200
We're now 6 days into #BugQuest2025, and we're still maintaining our focus on assets that most hunters skip! 🤠 Yesterday, we shared a method to identify hidden assets related to your target. Today, we're tackling a common mistake: ignoring subdomains that redirect! 👀 Just
0
6
34
Need a simple scanner to test for React2Shell at scale? 🤑 React2shell-scanner by @assetnote is a Python-based command-line tool that detects CVE-2025-55182 and CVE-2025-66478 in Next.js applications. It even includes support for bypassing WAF filters! 😎 🔗
4
59
401
Today marks day 5 of #BugQuest2025, and we're still trying to uncover assets in the most unexpected places! 👀 Yesterday, we shared a simple method to find forgotten hosts. Today, we're using something even more hidden in plain sight: copyright notices! 🤠 Most developers
0
3
28
@Krevetk0Valeriy @hoyahaxa @LaxmanMuthiyah That was it! We hope you've learned something new (and enjoyed) this thread! If you have enjoyed this thread: 1. Follow us @INTIGRITI for more of these threads! 🐛 2. Retweet the first Tweet to share it with your friends 💙
1
1
6
@Krevetk0Valeriy @hoyahaxa 5️⃣ How I Found A Vulnerability To Hack iCloud Accounts @laxmanmuthiyah details discovering an account takeover vulnerability in Apple's forgot password endpoint that bypassed multiple security measures, earning an $18,000 bounty! https://t.co/vO7DhXYhkC
1
0
4
@Krevetk0Valeriy @hoyahaxa 4️⃣ Password Reset to Admin Access This security researcher documents how a temporary password reset token granted full admin authorization in API calls, allowing complete access to all data and functions in the environment! https://t.co/FxKAXpTwBI
medium.com
While testing a web application that used a web GUI over the top of an API, I noted the calls to the API where authorized with a JWT token…
1
0
3
@Krevetk0Valeriy @hoyahaxa 3️⃣ Gaining Access to Protected Components This security researcher shares how exported Android activities can be exploited to access protected components and content providers, exposing sensitive data stored within apps! https://t.co/j5zCwg4t9W
blog.mzfr.me
In the previous post I talked about what activities are and how we can exploit exported activities. In this post, I’ll show you how an attacker might be able to access the components which are...
1
0
3
@Krevetk0Valeriy 2️⃣ SSRF in ColdFusion/CFML Tags and Functions @HoyaHaxa documents dozens of unexpected ColdFusion tags and functions that can process URLs, leading to SSRF vulnerabilities when handling user input! https://t.co/g67REEdXSk
hoyahaxa.com
1
1
4
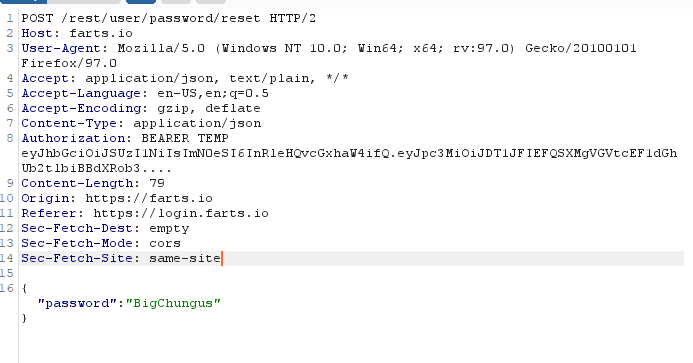
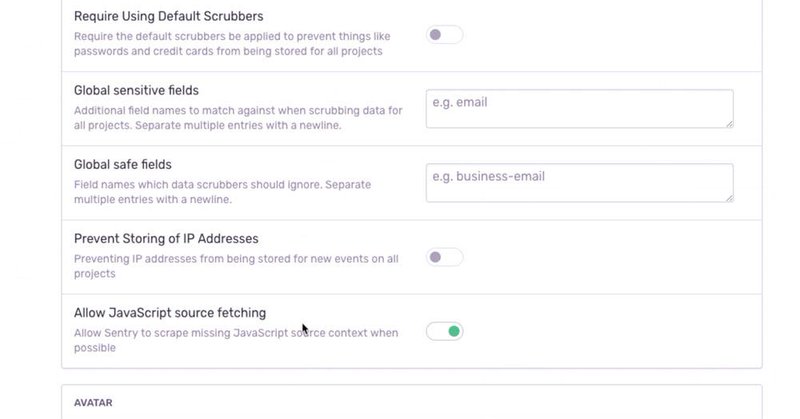
1️⃣ SSRF Vulnerability due to Sentry Misconfiguration @Krevetk0Valeriy shares how misconfigured Sentry instances with source code scraping enabled can lead to blind SSRF vulnerabilities, allowing attackers to make requests to internal services! https://t.co/XRrfd5HeW3
krevetk0.medium.com
That story happened when I saw that disclosed report.
1
0
5
We just dove into our shelf of archived bug bounty write-ups from the most notable hackers! 🤠 In this issue, we selected 5 compelling articles (that are still relevant today) to share with you, from which you can learn something new! 😎 🧵 👇
1
12
90
We're 4 days into #BugQuest2025, and are still attempting to expand our attack surface... 🤠 Yesterday, we explored a unique method to find hidden, related assets. Today, we're diving into a goldmine that many bug bounty hunters often overlook: hosts with certificate issues! 👀
0
6
61
Want to find more vulnerabilities with Google search? Make sure to also have look at our blog! 👇 https://t.co/8L0jp4OWVH
intigriti.com
Google dorking is another way to leverage search engines to discover hidden assets and endpoints to increase your chances of finding vulnerabilities.
0
1
8
Google dorking is an effective recon method for discovering new hosts, paths & parameters! 🤠 Google Dorks for Bug Bounty is a list of the most common Google search queries to perform content discovery. It also comes with a tool to pre-fill your queries based on your target! 👀
3
46
331
Day 3 of #BugQuest2025 is live now! Yesterday, we shared an interesting method for discovering assets that have never been tested before. 👀 Today's tip further expands on identifying hidden assets with favicon hashes! 🤠 These seamless images that appear in your tab are much
2
8
75
Day 2 of #BugQuest2025 is live now! And we knew you would make it, that's why we made today extra special! 🎁 The easiest way to find more bugs is to discover assets that have never been tested before 🤠 Virtual host fuzzing is one of the most underutilized methods for
3
12
130