dru1d
@_dru1d
Followers
932
Following
15K
Media
134
Statuses
2K
Husband. Hacker. Adversary Simulation team lead. OSCP.
127.0.0.1
Joined September 2009
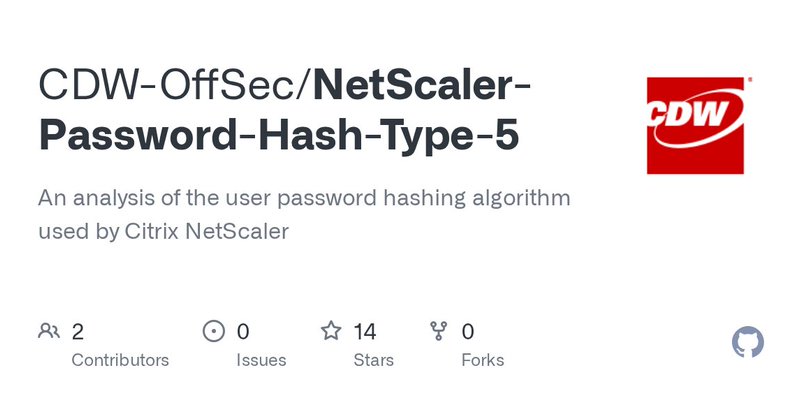
Here’s a short write-up covering some research Ian Odette (@wikibinge) and I conducted so that our team would have a documented method for cracking Citrix NetScaler system user passwords.
github.com
An analysis of the user password hashing algorithm used by Citrix NetScaler - CDW-OffSec/NetScaler-Password-Hash-Type-5
1
34
47
RT @Octoberfest73: Fixed the issue in Koppeling, was missing a single line of code to fix up the RVA of the Name field within the IMAGE_EXP….
github.com
Im having issues with the Cloners (both .NET and python) when I try to reference a DLL other than Functions.dll. I build Theif.dll with the Dyn-Net build (I removed the post-build event that does t...
0
2
0
RT @vector35: WARP speed ahead! Want to learn more about the future of function matching in Binary Ninja (and hopefully your other favorite….
binary.ninja
Binary Ninja is a modern reverse engineering platform with a scriptable and extensible decompiler.
0
5
0
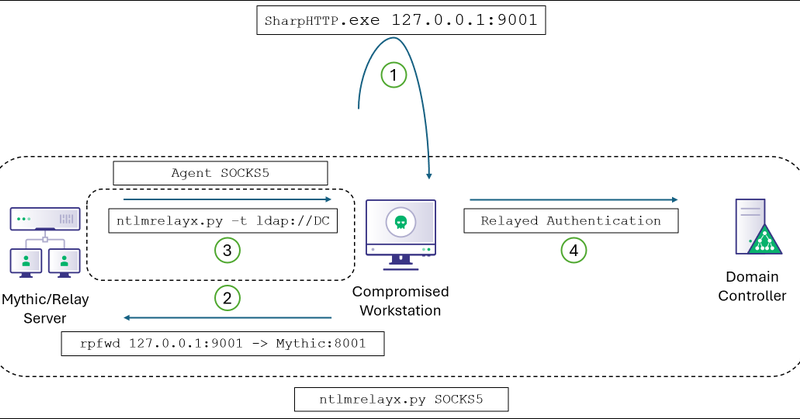
RT @_logangoins: I Just documented a cool way to authenticate proxied tooling to LDAP in an AD environment using C2 payload auth context, w….
specterops.io
TL;DR When operating out of a ceded access or phishing payload with no credential material, you can use low-privilege HTTP authentication from the current user context to perform a proxied relay to...
0
99
0
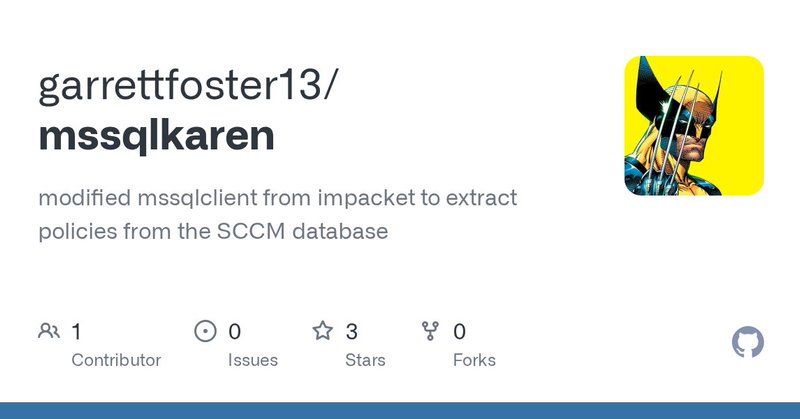
RT @unsigned_sh0rt: I automated the POC for stealing policies from MP relays from this blog into a modified version of mssqlclient https://….
github.com
modified mssqlclient from impacket to extract policies from the SCCM database - garrettfoster13/mssqlkaren
0
42
0
RT @kyleavery_: if you want to train a model yourself with GRPO:.1. find a verifiable task: 2. add a new reward fun….
github.com
Fully open reproduction of DeepSeek-R1. Contribute to huggingface/open-r1 development by creating an account on GitHub.
0
13
0
RT @phrack: At long last - Phrack 72 has been released online for your reading pleasure! . Check it out: https://t.….
0
327
0
I had a blast learning and working through some cool bug classes! It turns out the FAFO method can be useful for learning new things. 😂.
A few hours left - leaving it open until the morning on West Coast. Only 3 winners 🤭. Congrats @malware_owl and @_dru1d !!.
0
2
10
RT @LowLevelTweets: i love how software was trending towards being more secure. more sanitizers shipping with clang. more software being w….
0
289
0
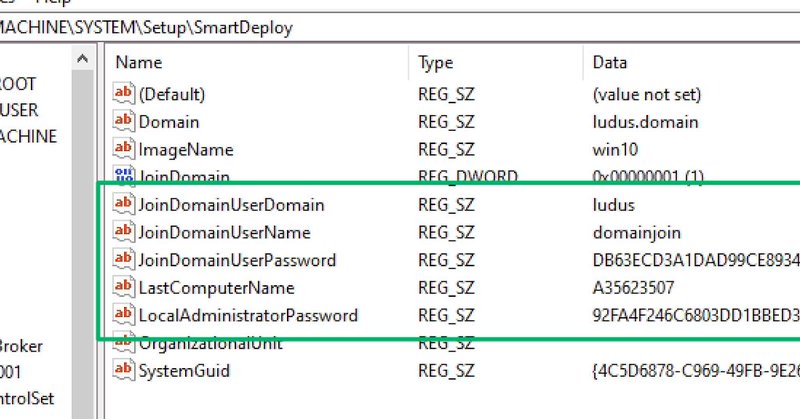
RT @SpecterOps: PDQ SmartDeploy versions prior to 3.0.2046 used static, hardcoded encryption keys for cred storage. Low-privileged users co….
specterops.io
TL;DR: Prior to version 3.0.2046, PDQ SmartDeploy used static, hardcoded, and universal encryption keys for secure credential storage. Low-privileged users may recover and decrypt privileged creden...
0
51
0
RT @unsigned_sh0rt: WSFC misconfigurations can turn your domain into one big fustercluck. I'm sharing fustercluck today as part of my #BHUS….
github.com
POC tool to abuse windows server failover clusters - garrettfoster13/fustercluck
0
51
0
RT @unsigned_sh0rt: My presentation starts in 20 minutes! Oceanside C level 2. Hope to see you there! #BHUSA
0
2
0
RT @unsigned_sh0rt: I pushed updates to SCCMHunter as part of my Arsenal demo at #BHUSA today! New features include a relay module for TAK….
github.com
[1.1.10] - 2025-08-06 Added Relay Module Added a new module to support TAKEOVER-5. Operators can relay coerced authentication to the SMS Provider role to compromise SCCM. HTTP Module Thanks ...
0
48
0
RT @SpecterOps: 👋 Say hello to Nemesis 2.0, a streamlined, Docker Compose-based platform that is laser-focused on file triage. After intro….
specterops.io
Nemesis 2.0 is a complete rewrite of the Nemesis file enrichment pipeline with a simplified and extensible architecture, new interface, and a focus on file triage and operator workflows.
0
31
0
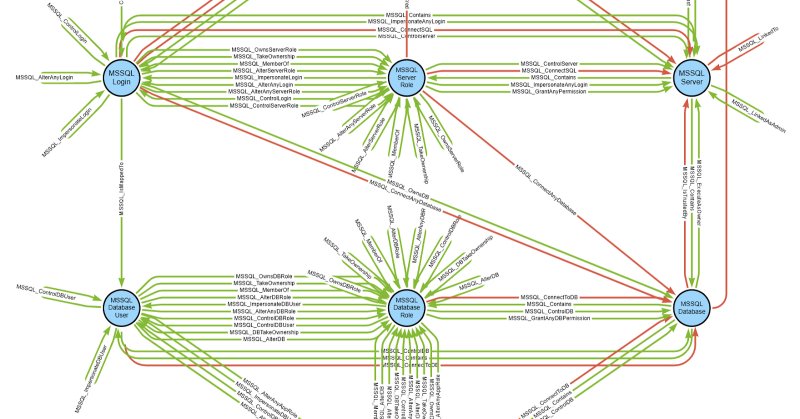
RT @SpecterOps: MSSQLHound leverages BloodHound's OpenGraph to visualize MSSQL attack paths with 7 new nodes & 37 new edges, all without to….
specterops.io
TL;DR MSSQLHound is a standalone PowerShell collector that adds 7 new nodes and 37 new MSSQL attack path edges to BloodHound using the new OpenGraph feature that was released in version 8.0. This...
0
52
0
RT @SpecterOps: BloodHound OpenGraph makes adding nodes and edges simple, but building effective attack graph models? That's where the real….
specterops.io
TL;DR OpenGraph makes it easy to add new nodes and edges into BloodHound, but doesn’t design your data model for you. This blog post has everything you need to get started with proper attack graph...
0
21
0
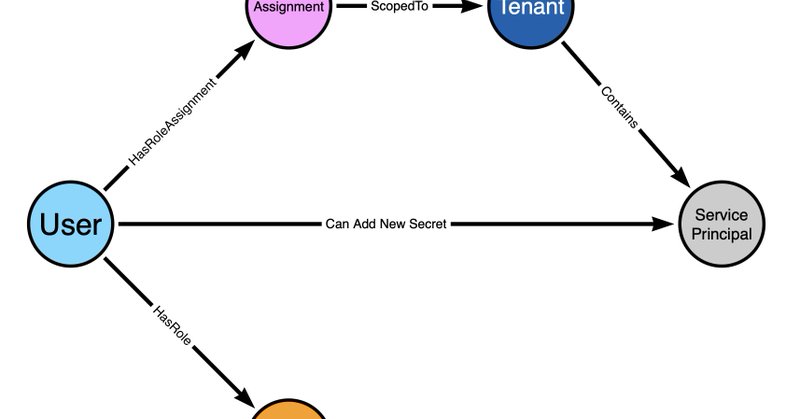
RT @SpecterOps: Entra Connect sync accounts can be exploited to hijack device userCertificate properties, enabling device impersonation and….
specterops.io
How Entra Connect and Intune can be abused via userCertificate hijacking to bypass conditional access and compromise hybrid domains
0
59
0