Justin Bui
@slyd0g
Followers
4K
Following
5K
Media
92
Statuses
2K
I break computers and skateboards | red/blue/whatever let's make security better | Offensive Security @Snowflake | Prev @Zoom @SpecterOps
Joined March 2012
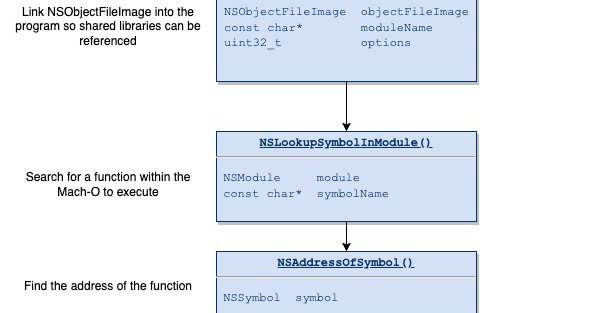
Took some time recently to dive into in-memory Mach-O execution on macOS. I dig into the API calls necessary to perform reflective code loading, present my Swift implementation, cover nuances on Big Sur vs Monterey, and how to detect it on Monterey!.
slyd0g.medium.com
This blogpost will describe the concept of loading executables in-memory on macOS and how to detect it.
9
58
152
RT @jaredcatkinson: Data is gold and Snowflake is full of it. BloodHound now understands Snowflake’s access model. Map who can reach your….
0
27
0
RT @Frichette_n: ec2-instance-connect:SendSSHPublicKey might be my on of my favorite API calls. Have privilege at the control plane and wan….
0
2
0
Some Python code that leverages FFI to interface with macOS libraries to pull the unique hardware UUID. An alternative to the system_profiler binary that may be useful :).
gist.github.com
GitHub Gist: instantly share code, notes, and snippets.
0
2
16
This is so cool :). "Santa also supports file access authorization (FAA), restricting access to specific files and ensuring . approved applications . can interact with them. We’ve leveraged this to secure browser cookies on Figma laptops".
figma.com
Here's how we scaled Santa, an open-source binary authorization tool, across all Figmates’ laptops to boost endpoint security while keeping workflows seamless.
1
2
9
RT @wtsdev: It's a write-up a year in the. waiting. Enjoy everyone!.
wts.dev
A security research blog.
0
13
0
RT @d_tranman: Had a lot of fun digging into COM stuff with @bohops recently! We ended up finding a way to laterally move without dropping….
ibm.com
New research from IBM X-Force Red has led to the development of a proof-of-concept fileless lateral movement technique by abusing trapped Component Object Model (COM) objects. Get the details.
0
179
0
RT @GrahamHelton3: I see we're doing the quarterly open source tools/research debate again. I'll just say this:. Phishing got much harder w….
0
52
0
RT @patrickwardle: . and a big mahalo to the (many) brilliant researchers whose work laid the foundation for this! 🙏🏽 .
0
3
0
Really awesome work by @patrickwardle, simple and elegant :).
A side effect of 🍎's privacy mindset: in-memory payloads remain largely invisible/inaccessible to macOS security/3rd-party tools. Apple nuked their reflective code loading APIs - but was that enough? 🫣. From #OBTS v7:."Restoring Reflective Code Loading".
0
0
4
RT @DefSecSentinel: #MacOS defense products that rely solely on reactive measures like YARA or a "magic" Machine Learning Model, that relie….
0
19
0
RT @BillDemirkapi: Just Published 👉 Secrets and Shadows: Leveraging Big Data for Vulnerability Discovery at Scale! Impacted orgs include Cr….
billdemirkapi.me
Modern technologies like the cloud have made rapidly developing scalable software more accessible than ever. What risks has cloud computing introduced for the sake of convenience?
0
19
0
RT @_ColeMurray: I recently read through Meta's Llama 3 paper. Their approach to synthetic data for code generation is interesting. I dug i….
0
4
0
Really cool approach to mapping out nested permissions in @SnowflakeDB check this post out! :).
There's been lots of reporting on the campaign against.Snowflake DB, so I thought it'd be useful to look at it from an Attack Path PoV. This post shows how you can create an graph for your SNOW deployment & what that tells us about the campaign.
0
1
6
RT @SnowflakeDB: There has been a lot of attention on a cybersecurity incident involving Snowflake. We want everyone to have the latest and….
0
21
0
RT @0xMatt: PSA for Cybersecurity folk: Our co-workers are tired of being "tricked" by phishing exercises y'all, and it is making them hate….
security.googleblog.com
Matt Linton, Chaos Specialist In the late 19th and early 20th century, a series of catastrophic fires in short succession led an outraged pu...
0
165
0