Julien | MrTuxracer 🇪🇺
@MrTuxracer
Followers
30,225
Following
418
Media
234
Statuses
4,321
Freelancer | Full-time #BugBounty | @Hacker0x01 H1-Elite & $1,500,000 Hacker | ❤️ IDA Pro
Unicorn Planet
Joined December 2011
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Rio Grande do Sul
• 134797 Tweets
Madonna
• 126157 Tweets
Boeing
• 119118 Tweets
Nathan
• 92350 Tweets
Irak
• 64008 Tweets
عدنان البرش
• 41958 Tweets
#SRHvRR
• 35919 Tweets
Olimpiade
• 28951 Tweets
Bhuvi
• 22955 Tweets
KPLC
• 19730 Tweets
Bruno Mars
• 19651 Tweets
Marselino
• 19279 Tweets
زياد
• 17375 Tweets
Ernando
• 14499 Tweets
Canna
• 14176 Tweets
ALGS
• 12294 Tweets
Guinea
• 12169 Tweets
Hubner
• 12081 Tweets
Last Seen Profiles
Pinned Tweet
As promised: Here's the first $10,000
@Intel
bug (aka CVE-2022-33942) that allows to bypass the authentication of Intel's DCM by spoofing Kerberos and LDAP responses.
Exploit inside, enjoy 🥳
#BugBounty
#security
18
257
822
Yay! I've finally crossed the magical 1,000,000 USD
#BugBounty
mark on
@Hacker0x01
!!
Thanks for providing me with a great platform to hack on 😎 A very special thanks goes to my favorite private program 🍻!
So here are some stats:
-Paid through 571 reports (741 total)
1/4
110
106
2K
I just got a $15,000
#BugBounty
for a UUID-based IDOR that led to an account takeover 🥷
Interestingly, the application used some fixed UUIDs like 00000000-0000-0000-0000-000000000000 and 11111111-1111-1111-1111-111111111111 for some _administrative_ users 🤷♂️
35
143
1K
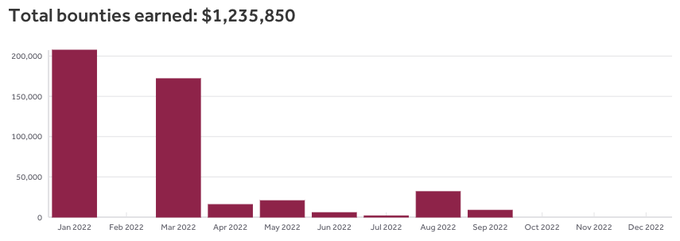
I've just crossed the $500,000 mark in total bounties for this year! Most of it came through
@Hacker0x01
(again 😎), but
@intigriti
supplied another nice chunk!
Up next: I will publish a couple of write-ups about some of my 5-digit bugs from
@Intel
🥳
#BugBounty
76
40
1K
As promised: Here's my story about 8 CVEs resulting in a plugin removal and more than $30,000 in bounties!
I've chained 3 of them to go from unauthenticated to admin, aka how to exploit a blind SQL Injection via XSS.
#BugBounty
#security
20
298
834
October was - by far - my best
#BugBounty
month ever! I made 160k USD from 40 bugs across
@Hacker0x01
and
@synack
with almost zero automation involved.
I usually don't talk about my bounty income, but I'm quite proud of my work TBH 🙂 So here's a little bit of statistics. (1/3)
48
59
768
As promised: Smuggling an (Un)exploitable XSS
It took me a couple of days to completely exploit this, but it was worth the effort. Thanks for the maximum
#BugBounty
!
14
231
605
Yay, I’ve just scored my highest single
#BugBounty
of 50,150 USD for a SQL Injection 🥷
Found using a custom, target-specific active scanner profile - thanks to
@Agarri_FR
for all the tweaks and tipps taught in your course 👌🔥
26
33
518
I'm going to drop 6 CVEs soon that eventually led to WordPress's removal of the affected plugin and more than $30,000 in bounties.
Source code review ftw. 🥷
#BugBounty
#security
15
40
514
Yay! I've completed my "$300k in 2022"
#BugBounty
goal much earlier than expected: Made $395k in bounties through
@Hacker0x01
and
@intigriti
since the beginning of 2022 🥷
Thanks to my favorite programs on H1 and
@intel
🍻
Here are some stats:
(1/3)
My
#BugBounty
/
#security
goals for 2022:
-Earn 300k USD in bounties
-Hack more on
@SynackRedTeam
again
-Get the
@offsectraining
OSWE, OSEP and onto the road to OSEE
-Do more binary exploitation again
-Submit something to
#Pwn2Own
-Resurrect my blog
6
9
207
54
46
505
I recently found a nice ATO that got me a 30,000 USD
#BugBounty
:
App is tenant-based allowing to register the same user on different tenants.I've found an endpoint disclosing the email activation token for new user accounts on your own tenant (so no mail access required).
(1/3)
14
79
454
During my interview with
@NahamSec
I've shared a very handy
#BugBountyTip
for wide-scope
#BugBounty
programs:
Look for Google Analytics Tracking IDs (UA-XXXXXX-X) and use i.e. to discover more assets sharing the same ID.
3
148
436
Here we go! Chaining a Stored XSS and a SQL Injection to compromise an Uber Wordpress.
Bonus point: I've used a quiz 🙃 (and both are still 0-days)
#BugBounty
#togetherwehitharder
#h14420
8
179
381
I've just RCE'd a 3-year-old
#BugBounty
program on its core app behind CloudFlare with a chain of 3 bugs.
I've already said it a dozen times, but again: program age doesn't tell you anything. 😈
11
17
347
Over the past 3.5 months, I've conducted a small GDPR case study involving the
#BugBounty
platforms
@Hacker0x01
,
@Bugcrowd
,
@synack
,
@intigriti
, and
@zerocopter
. The results are...interesting.
#privacy
#GDPR
15
118
328
My latest CVE found through pure source code review: A full unauthenticated SSRF affecting Acronis Cyber Backup, allowing to do nasty stuff with backup emails. 🦄
#security
#BugBounty
8
95
290
I recently got a nice surprise from
@IntelSecurity
: a $10,000
#BugBounty
for a bug they have found internally resulting from one of my report comments.
That's the first time _ever_ in my bounty career that a team proactively rewarded an internal finding!
That's next-level 🔥
12
13
284
How to get RCE on all client systems + an MVH belt. All about my recon-intensive, yet simple RCE from last year’s H1-3120 event 😎
#BugBounty
#BugBountyTip
#security
3
121
278
Since the year is almost over, here's my
#BugBounty
recap of 2022:
-I've earned more than $500,000 in bounties which is almost twice my goal
-Got the OSWE certification from
@offsectraining
-Successfully resurrected my blog
-Did more binary exploitation (no blogs yet)
1/2
My
#BugBounty
/
#security
goals for 2022:
-Earn 300k USD in bounties
-Hack more on
@SynackRedTeam
again
-Get the
@offsectraining
OSWE, OSEP and onto the road to OSEE
-Do more binary exploitation again
-Submit something to
#Pwn2Own
-Resurrect my blog
6
9
207
11
12
262
Over the past year, I've spent a lot of time building my own recon/automation/continuous scanning tool from scratch. I've learned a lot about Python/Flask, MongoDB, RabbitMQ, Vue.js and Bootstrap during this time, which makes it even better 🙂
#BugBounty
13
37
251
Dear XSS pros:
I'm looking for a bypass to the following blacklist:
javascript
<script>, <script
all on* handlers
data:
<iframe
href=java
<base, <base>
<svg
Keywords aren't stripped, but the entire request is blocked if encountered.
50/50 bounty split!
#BugBounty
#security
30
51
240
A
#BugBounty
program downgraded my P1 to a P3 claiming that exploitation could have been prevented by a WAF or manual intervention.
Important point: They neither have a WAF nor have prevented me from attacking them for _days_
Me: WTF?!
@Bugcrowd
: 🤷♂️🤷♂️🤷♂️🤷♂️
21
9
231
Woohoo! Another one of my
#BugBounty
#security
goals of 2022 is completed!
Just got a happy mail from
@offsectraining
that I've passed their OSWE exam 😎 It was quite a nice challenge and I'll post a review soon for those of you thinking about taking the course.
8
6
228
My first bug of 2023:
A quite crazy authentication bypass affecting a firewall vendor.
Keep an eye out for CVE-2023-22620 😎
#security
#BugBounty
11
10
223
My
#BugBounty
/
#security
goals for 2022:
-Earn 300k USD in bounties
-Hack more on
@SynackRedTeam
again
-Get the
@offsectraining
OSWE, OSEP and onto the road to OSEE
-Do more binary exploitation again
-Submit something to
#Pwn2Own
-Resurrect my blog
6
9
207
I've just been invited to a private
#BugBounty
program on
@Hacker0x01
that pays decent bounties.
Interestingly, the same company also runs a private program on
@Bugcrowd
with exactly the same scope, but no bounties at all.
This is next level shit. Seriously.
18
11
202
Thanks everyone who reached out! 😎
I've found a valid payload that requires adding the following (and ONLY this) sequence of %27%00%20, which confuses their filter for whatever reason and let me inject an on-handler after that sequence.
WTF.
Dear XSS pros:
I'm looking for a bypass to the following blacklist:
javascript
<script>, <script
all on* handlers
data:
<iframe
href=java
<base, <base>
<svg
Keywords aren't stripped, but the entire request is blocked if encountered.
50/50 bounty split!
#BugBounty
#security
30
51
240
2
34
205
After almost two days of recon against a single WAF-protected host, I finally popped it today 😎 Persistence is key!
#BugBounty
7
13
201
I've been doing a lot of patch-diffing-to-exploit stuff recently and thought about posting more of such n-day analyses on my blog. So targets are bugs that have only seen a patch but no public exploit.
What do you think?
#BugBounty
#security
23
2
204
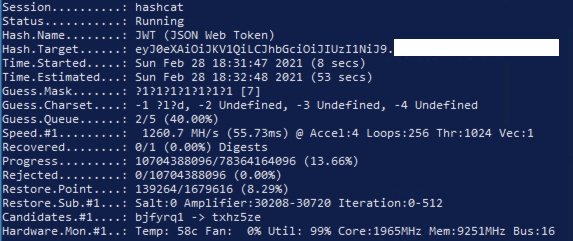
If you were able to crack a JWT secret key but there are still some unguessable parameters in the payload just like a UUID, try sending an empty payload instead. This granted me admin rights more than once.
#BugBountyTip
#BugBounty
3
36
200
This made my day:
A
#BugBounty
program (respectively their incident response team) locked all of my accounts to prevent me from exploiting their systems 👌
Me: Found an IDOR to enable all of my accounts again 😎
Also me: Disabling their accounts *could* be fun too 🥳
7
8
199
Sounds like someone is looking at your data closely...
Protip: Host your own instance of xsshunter-express or ezxss to avoid leaking potentially sensitive data to this company.
#BugBounty
#security
13
34
196
✅ Found my first RCE of 2022 through source code review 😎 it took me two days to exploit and required a bug and a feature.
#BugBounty
8
3
195
OK, here's another one of my RCE stories. If you really like pain, then this one is for you 😉 Shout-out to
@Hacker0x01
for supporting and defending transparency and disclosure principles!
#BugBounty
#security
3
57
192
My girlfriend and I have just started on our round-the-world trip! So for the next 1-2 years you will see me hacking from many different places just like this 😎 Thanks
#bugbounty
for making this possible!
16
7
193
My advice to those who think about doing
#BugBounty
full-time:
Don't go full-time if you only live from month to month! Build up some savings before going that route. Personally, I'm able to survive 3 years without having to find a single bug using my savings.
(1/2)
13
28
190
Here are my
#BugBounty
#security
goals for 2023:
-$250k in bounties
-Pass
@offsectraining
OSED and take their AWE training at BlackHat
-More binary exploitation!
-Submit something to
#pwn2own
-Get 10+ CVEs
-More collabs!
8
1
186
I've reported a quite unusual RCE and got almost instantly contacted by the corresponding
@Hacker0x01
program manager telling me how nice that RCE is 😎
It's really about such small things that keep me motivated. In return, I've just submitted my second RCE...🙃
#BugBounty
5
2
176
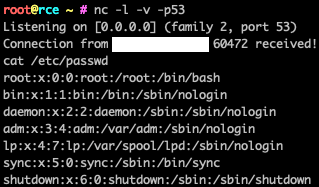
I've just chained 4 bugs to takeover any account:
-1st IDOR to leak account IDs
-2nd IDOR to approve the account transfer
-3rd IDOR to transfer the account
-Missing rate limit on a random 2-bytes owner verification signature
This resulted in a 700 words
#BugBounty
report. 😎
9
10
177
As promised, here's my review of the
@offsectraining
AWAE course and OSWE exam. It's been a great challenge and sharpened my view on how small coding errors can result in impactful bugs.
#security
#BugBounty
3
42
177
After 7 days of excessive JavaScript/C++/Assembly and browser internals, I’ve finally turned my Chrome out of bounds read into a popping calc 👌🦄🎉🍾
My new goal for next year: submit something to
#Pwn2Own
😎
2
5
171
I'm a bit sad that I had to decline my invitation to
#h14420
because
@zoom
is my favorite
#BugBounty
program 😥
But I do have a good excuse: enjoying beautiful Norway! 😎👌
9
1
171
I'm currently sitting on 10+ CVEs covering stuff from incorrect authz and private key disclosure up to a nice SQLi to RCE chain.
I've found almost all of these bugs while hacking on
#BugBounty
programs 🥷
Public disclosures coming soon 😎
6
6
170
So here's the first CVE of my
#BugBounty
collection: It's an unauth XSS affecting SAP Knowledge Warehouse aka CVE-2021-42063.
The bug itself isn't super thrilling, but the advisory tells you why I'll no longer disclose
#security
vulns to SAP.
(1/2)
6
29
168
This sounds like some people at
@Hacker0x01
need to reread the CVSS specification guide. CVSS is about measuring vulnerability impact and not the root cause of how a bug was introduced or how it was discovered…
13
19
168
I’ve submitted a SQLi to RCE chain (via stacked queries) to a
#BugBounty
program to prove max impact, yet the program insists that I have to prove max impact against the database itself, otherwise they’ll rate the whole issue as medium severity.
🤯
19
6
168
After submitting an RCE to a
#BugBounty
program, it took them just 5 minutes to take the whole asset off the internet.
I'm really impressed.
5
4
162
I'm going to publish a new blog post about a critical request smuggling vulnerability (and a 0day) that got me a maximum
#BugBounty
soon.
I'm just waiting for the official ok from the affected program - hopefully right before the weekend 😎
2
5
167
Just got a maximum bounty for a LFI via a vulnerable mPDF implementation, which I've escalated to RCE by SSRFing to some even more interesting stuff.
#BugBounty
Thanks
@JonathanBouman
for the initial exploit vector. Great work 😎!
Just published a new blog. Stealing internal server files from
@IKEA
.com by exploiting a LFI bug in their PDF library. Furthermore an in-depth discussion about Responsible Disclosures. Read more: Would love to hear your opinion and feedback!
16
356
762
5
40
166
I recently purchased the
@offsectraining
Learn Unlimited subscription with access to all their courses to achieve my 2022
#security
goals.
So much awesome stuff to hack! 💪🥷🥳
Yeah, I know, I could have gotten all the stuff from 15 USD Udemy courses too.. /joking, obviously.
14
5
162
I'm so incredibly proud of this 🔥😎
Thank you very much
@Hacker0x01
for this awesome poster and for providing me with a great platform to hack on 🖤🤍
This hacker used a cold mind and hot hacks to lead his colony to victory every single time.🐧 Help us welcome
@MrTuxracer
to H1-Elite! 👏
0
1
55
21
4
164
I haven't done any
#BugBounty
hunting for almost two months and just started again. Result of one evening of hacking:
- IDOR to leak passwords
- 2FA Bypass
Both on a 2+ years old program with 300+ reports. Reminds me of
@zseano
's latest post: "find what works for you".
5
18
152
A
#BugBounty
program on
@Hacker0x01
pays a "flat rate" of $300 for every finding.
It's a company with a market cap of > 20 billion(!!!) dollars, yet people keep reporting stuff.
First-class exploitation of knowledge.
9
9
154
I've only been hacking with my new MacBook for around 3 hours and already found a SQL Injection.
Nice, so it should have paid itself off already 😎 🥳
#BugBounty
4
4
150
I'm really sorry for the admin/dev who has to deal with the unauthenticated critical I have just reported on a Friday evening.
It took me two days to fully exploit this nice chain, and it's definitely worth a write-up.
#BugBounty
10
2
148
I get a lot of DMs about "how to exploit xyz?", but in many cases it seems like there is a lack of understanding about the basics just like how the HTTP protocol works, Same-Origin etc.
I'm here to help, but please take some time to learn the basics first!
#BugBounty
#security
8
17
143
Oh, what a surprise!! I was able to successfully brute-force a SSH login - for the first time ever - on a
#BugBounty
program. Does this count as RCE too? 🙃
#protip
: A sshd listening on a port > 50.000 won't save your test account 🦄
18
17
148
I've completed my first build since 2008:
- AMD Ryzen 9 5950X
- EVGA RTX 3080 FTW3 ULTRA
- MSI MEG X570 Unify
- G.Skill DDR4-3600
- Patriot Viper VP4100
- NZXT Kraken Z73
- Lian Li O11Dynamic XL
- A lot of Corsair lightning
....and it totally serves its
#security
purpose 😎
17
6
138
I've spent a week writing my own Bluetooth fuzzer and it's still far from perfect, but it has already found its first exploitable vulnerability! Yay 🙂
I definitely need more IoT
#BugBounty
programs. 🥷
4
10
138
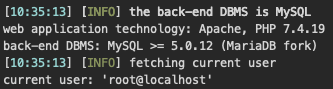
In the first part, I've shown you how to bypass
@Intel
DCM's authentication. In this part, you'll learn how to finally gain Remote Code Execution through an authenticated SQL Injection (aka CVE-2022-21225).
#BugBounty
#security
0
52
137
So the first one who solved this was
@joernchen
with a crazy payload of
${BASH%%[^x][^x][^x][^x][^x][^x]}
(given that the env var BASH points to /bin/sh) which returns / and I got my shell with this one)
Thank you very much dude ♥️
Hey
#infosec
#BugBounty
Twitter😎
I'm looking for a command injection payload within a curl call (backticks can be used) to exec the file /tmp/exp (the full path to the file needs to be given as part of the payload)
max 250 chars, no | / \ : " * ? < and >
7
14
65
4
18
134
I'm currently having some real
#BugBounty
"fun": A program thinks that a path traversal + arbitrary file write ultimately leading to RCE (PoC included) is not an issue... 🤯
So, I've officially requested mediation on
@intigriti
for the first time - let's see how it goes.
8
3
132
I just got two maximum bounties for thick client RCEs through file imports and a custom URI handler. It took me a moment to figure out how to unpack and pack their custom file format but persistence pays off!
I really love binary exploitation😎
#bugbounty
4
5
128
I got a nice maximum
#BugBounty
from
@YogoshaOfficial
today for the two-staged full SSRF with AWS metadata access on a program that is almost two years old! 😎
So remember: Program age doesn't say anything, and there's always something to find!
5
2
130
It's Wednesday and I've already found two entirely different RCEs (deserialization and memory corruption) this week - in two unrelated
#BugBounty
programs.
But both granted me NT AUTHORITY\SYSTEM rights.
Make Windows exploitation great again 😎
4
9
127
I've just chained an information disclosure, a local file inclusion and a juicy /..;/ to get RCE via an Apache Tomcat Manager.
#BugBounty
10
14
125
I've just finished the "Mastering Burp Suite Pro" training by
@Agarri_FR
. Learned about so many little but important details which will definitely improve my hacking efficiency 🥷
100% recommended - it's worth every single Euro!
#security
#BugBounty
3
13
125
Who's ready for an authentication bypass (CVE-2023-22620) and a Heartbleed-like remote memory contents disclosure bug (CVE-2023-22897), both affecting a firewall vendor? 🤔
#security
10
13
126
I’ve found more than one exposed WEB-INF directory on this way. So it’s definitely worth adding this to your check list!
#bugbountytip
#bugbounty
Want to find critical bugs by changing a single header? Do just like
@hacker_
& set your host header to 'localhost' in your next directory bruteforce, the results might be surprising! 🔥
#BugBountyTip
#BugBountyTips
12
229
741
2
32
121
I haven’t done a lot of
#BugBounty
for the past four months or so because I’ve been swamped with pentests from my local clients.
TBH, it feels good to be paid for time rather than outcome every now and then 🤷♂️😬
2
1
124
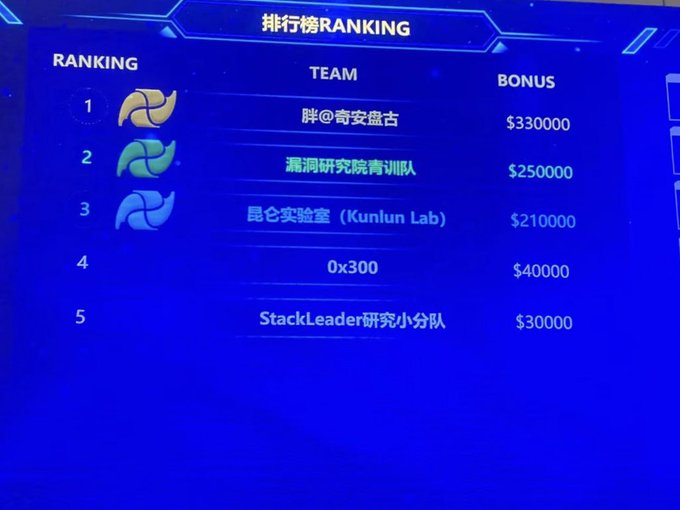
Well, this is an RCE you should really worry about - not that trusted Airdrop shit.
Team PangU pwned iPhone13 Pro remote jailbreak on the day1 of TianfuCup, will take $300k as reward and ranked as
#1
currently.
18
326
1K
4
11
117
While everybody is hacking on
#h12010
,
@dhauenstein
and I have exploited a tricky and uncommon RCE. In Perl. On a production site. In 2020. For real.
Shout-out to
@gkhck_
for doing the recon. 😎
Write-up coming soon.
#BugBounty
6
6
116
I recently got a maximum bounty for: Reflected XSS -> Grabbed user's identity token (no auth) -> Found auth logic error that converted the token w/o the user's pwd into an auth token -> ATO & 2FA Bypass.
Always maximize your impact!
#togetherwehitharder
#bugbountytip
#BugBounty
3
10
113
Yay!
@Intel
finally updated the CVSS score of my CVE-2022-33942 to 10.0 and awarded an additional $5,000
#BugBounty
for it.
Happy to see that they've corrected their error 😎
As promised: Here's the first $10,000
@Intel
bug (aka CVE-2022-33942) that allows to bypass the authentication of Intel's DCM by spoofing Kerberos and LDAP responses.
Exploit inside, enjoy 🥳
#BugBounty
#security
18
257
822
3
8
112
So here's my late writeup about
#h1415
, featuring
@yaworsk
@arneswinnen
@securinti
@smiegles
@SebMorin1
@thedawgyg
@seanmeals
@Corb3nik
@Rhynorater
@prebenve
and
@ngalongc
@filedescriptor
and the whole
@Hacker0x01
team - thanks guys!
#BugBounty
3
38
107
So I did a small experiment (aka CVE-2023-29459 - affecting 100k+ users) to find out how
@redbull
performs regarding responsible disclosure outside their
#BugBounty
program:
It turns out not so well, as you can see in the disclosure timeline.
1/5
5
19
107
I've submitted my first bug of the year at 11:44 and it was accepted and rewarded at 14:26 on
@Hacker0x01
. 2020 is kicking off surprisingly fast 🙃
#BugBounty
5
0
104
I've blindly exploited an unserialize() bug today for my first time ever on a
#BugBounty
program 😎
It was kinda tricky up to the point where I knew the framework in use and the blacklisted PHP functions.
Man, RCE-ing on this way feels so good!
6
2
101
Aaaand the last one: CVE-2023-22897 is a remote memory contents disclosure
#vulnerability
affecting SecurePoint's UTM.
Not as wild as Heartbleed, but still a fun one to find in 2023 😈
#security
1
14
100