Nicolas Grégoire
@Agarri_FR
Followers
26,156
Following
607
Media
346
Statuses
12,987
Web hacker and Burp Suite Pro trainer Refer to for trainings Follow @MasteringBurp for free tips and tricks
South Luberon, France
Joined May 2011
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Rio Grande do Sul
• 175073 Tweets
NO RDM COM CAIO E LUAN
• 137561 Tweets
Madonna
• 127836 Tweets
Tottenham
• 79326 Tweets
Spurs
• 72260 Tweets
Leverkusen
• 61813 Tweets
Palmer
• 56053 Tweets
Hayer
• 38406 Tweets
Maracaibo
• 33278 Tweets
Ole Miss
• 29594 Tweets
Ange
• 28232 Tweets
Aston Villa
• 28206 Tweets
bruno mars
• 26934 Tweets
憲法記念日
• 21170 Tweets
#SVGala9
• 20068 Tweets
Cucurella
• 18321 Tweets
$AAPL
• 17543 Tweets
Chalobah
• 16857 Tweets
Xabi Alonso
• 14217 Tweets
Caicedo
• 13737 Tweets
Anne Hathaway
• 11672 Tweets
Lillard
• 10618 Tweets
Last Seen Profiles
Pinned Tweet
I just updated my "Freebies" page, in order to add the content I recently published:
- the 30' talk given at
@NorthSec_io
- the 70' hands-on workshop streamed during
#nahamcon2023
The page now contains direct links to the slides and videos, enjoy! 🎁
2
103
301
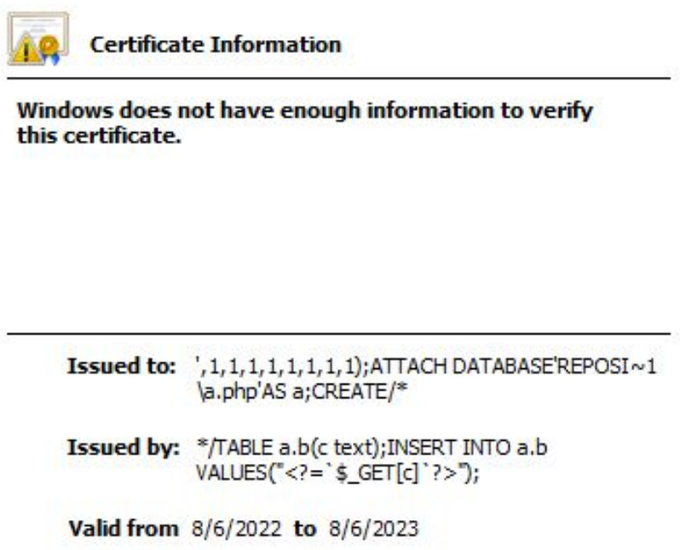
XXE inside a SOAP node: <soap:Body><foo><![CDATA[<!DOCTYPE doc [<!ENTITY % dtd SYSTEM "
http://0x0:22/">
%dtd;]><xxx/>]]></foo></soap:Body>
4
198
528
Not your typical SQLi vector... 😈
I've finally published the advisories regarding the Trend Micro bugs that I shared at
#HITCON
! Do check them out at
@starlabs_sg
's advisory page:
🏌️♂️CVE-2023-32530 is an interesting case of SQLi to RCE:
0
42
167
4
56
335
On Friday, my free
@Burp_Suite
workshop for
#NahamCon
will be published 🎁
You'll get:
- the video itself (70 minutes)
- the slides as a PDF (35 pages)
- two Docker containers hosting the targets
The stream starts at 11:10 AM PDT aka 20:10 CET ⌚️
11
70
300
I published this trick in 2015
When testing for SSRF using a black list, take internal IP addresses and when encoding them, dont encode entire IP. Encode 1 octet of the IP address, or 2 or 3. For Instance: AWS Metadata - 0251.254.169.254 (this got the $160,000 payout in Oct 2018)
#bugbountytip
#bugbounty
14
362
1K
8
80
297
Here’s the slides of the talk I gave yesterday at NorthSec 2023
"Tips and tricks for Burp Suite Pro, ten years later"
#nsec23
@NorthSec_io
5
94
296
If you like this kind of
@Burp_Suite
tips, here's ~100 pages of them. That was published in 2013 but most of it is still valid.
3
109
290
Looking for injectable DTD files *inside* JAR archives may easily be overlooked. A good read from
@iamnoooob
👍
#XXE
2
88
231
Using grep? Dealing with JSON files? Give "gron" a try and then praise
@TomNomNom
for this gem!
5
39
223
I’m suprised that CVE-2018-13382 (a trivial « backdoor » in Fortigate SSL VPN) didn’t get much attention, even after
@orange_8361
´s talks in Vegas...
5
69
213
#ProTip
For a stealthier
@Burp_Suite
usage, tick "Proxy > Options > Miscellaneous > Disable web interface"
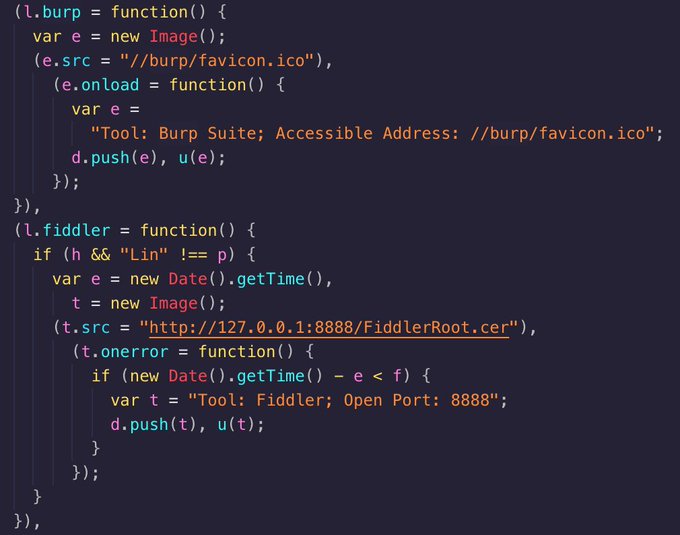
@evilsocket
They've got some fun JS on their website. Among other things, it attempts to detect tools like Burpsuite, ZAP, Fiddler, etc and probably does a pretty good job of it.
0
15
40
3
66
205
#ProTip
When doing content discovery with
@Burp_Suite
Intruder, don't only rely on responses size or status code. A quick Grep Extract on "<title>(.*?)</title>" may go a long way...
1
68
202
This short article I wrote last year about
@Burp_Suite
Intruder somewhat flew under the radar 🤐 Not even sure I posted a link... 🤦♂️
0
62
204
Deep link on mobile app ➡️ Host-relative SSRF ➡️ Account takeover 🦾 (affecting
@Pinterest
)
2
60
194
It appears that
@NorthSec_io
published the video of my talk "Burp Suite Pro tips and tricks, the sequel" 🎬
6
54
193
No need to update my old
@Burp_Suite
Tips & Tricks talk anymore:
@JR0ch17
just killed the game with his
@Bugcrowd
video!
#ImproveYourWorkflow
1
65
181
Something pentesters already know: registering with TRUE as your name may yield interesting results (it also works with NULL, UNDEFINED, CON, PRN, ...)
#BugBountyTips
4
41
174
I'll give one or two _FREE_ workshops covering
@Burp_Suite
v2 in the next months. Stay tuned for dates/location/...
13
25
160
This PE exe, generated by a special GCC, is also a ZIP archive and can be executed on Windows (of course) but also Unix (not limited to Linux) and MacOS 🤯 By
@justinetunney
5
50
160
Whoever uses IP address 192.168.0.100 gets a 15-minute window after reboot to gain RCE as root on some
@TPLINK
devices 🧐
2
15
128
I just noticed that
@Burp_Suite
includes an action named "Forward intercepted Proxy request and intercept the response". I mapped it to Ctrl+Shift+F and OMG it's so useful!
9
37
119
#ProTip
If you need to mix Turbo Intruder with other
@Burp_Suite
extensions (like Hackvertor or Logger++), simply add "engine=Engine.BURP" to RequestEngine(). Note: the custom HTTP stack is _much_ faster than the default one, so this change will slow down things
0
33
120
I've to say that
@WebSecAcademy
, an online self-training by
@Burp_Suite
authors, is really good! 💯
3
23
115
<!ENTITY % pe1 SYSTEM "<?php print $_GET['x'] ?>">
<!ENTITY % pe2 "<!ENTITY &
#37
; pe3 SYSTEM '_%pe1;_://'>">
%pe2; %pe3;
4
44
113
OWASP's example implementation of check_private_ip() is quite naive. It can be bypassed with 0x7f.0.0.1
#SSRF
3
26
115
#ProTip
When brute-forcing static files (f.e. /plugins/$name$/readme.txt), keep an eye on the returned Last-Modified header (possibly via Grep - Extract). A bunch of things can be inferred from the results...
1
30
110
Back to blogging! CSRF-protected forms,
@Burp_Suite
Intruder, and no macros. A step-by-step walkthrough based on
@DVWA
that you can follow along at home...
3
46
108
Finally exploited this MarsDB NoSQL injection :-D Thanks
@owasp_juiceshop
for the testbed, that was fun!
3
24
109
TIL that
http://unix:/var/run/docker.sock:/containers/json
is a valid URL for got, the "Human-friendly and powerful HTTP request library for Node.js" 🤯
1
14
112
LAN-only "XXE over UDP" in Jenkins Swarm plugin, with victim-initiated exploitation: that’s _not_ a common finding! CVE-2019-10309 by
@TalosSecurity
0
54
108
#BurpSuite
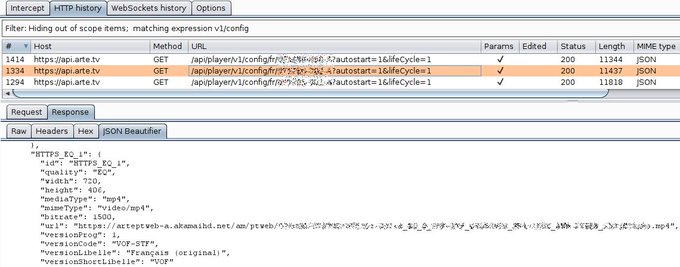
Tip of the day - How to download movies from Arte Replay? Simply access the target page in your browser, then search for "/api/player/v1/config/" in Proxy History and pick a MP4 URL from the JSON response. Give it to wget, you're done!
2
28
107
If you follow me for
@Burp_Suite
related news, let me tell you I recently created a dedicated account called
@MasteringBurp
👀
9
33
104
Thanks
@garethheyes
and
@albinowax
for Hackability, that's really useful in some atypical SSRF scenarios!
1
53
107
SSRF made its way to the
@owasp
Top 10. Finally!
2
13
104
Reminder for
@defcon
attendees: in Europe, we have large hackercamps too! A few differences though: no hotel security (because we use ⛺️), lockpicks are super welcome, no (need for) AC, valued privacy, our own phone network, etc.
4
29
102
SSRF in
@evernote
, by
@NeolexSecurity
🤓 The target URL is base64-encoded in the path, and # is required in order to bypass the whitelist 👍
1
26
95
😮 100+ new followers today🤯 Hi everybody! 👋
Interested in Burp suite? Check my dedicated account
@MasteringBurp
🛠️ Want to deep dive into SSRF? Check my talks 👨🏫
2
7
95
This link is valid and points (unsurprisingly) to a nice article on Unicode URLs
https://🅂𝖍𝐤ₛᵖ𝒓.ⓜ𝕠𝒃𝓲/🆆🆃🅵/
2
13
93
Note sure why "AWS Signer" by
@NetSPI
isn't in the
@Burp_Suite
BApp Store, but it's sooooo useful when interacting with authenticated AWS endpoints (S3, API Getway, ...). And it supports temporary Cognito creds!
1
29
92
I don’t want to boast or anything, but you can get most of these tricks at once by watching my SSRF talk from 2015 😇
#SSRF
Did you know that IPv4 network standards reserve the entire 127.0.0.0/8 address block for loopback purposes? That means any packet sent to one of those 16,777,214 addresses always going to call home
that means that any address 127.X.X.X = 127.0.0.1
#BugBounty
#infosec
8
101
366
3
18
89