Patrik Fehrenbach
@ITSecurityguard
Followers
31K
Following
6K
Media
1K
Statuses
5K
rɪsˈpɒnsəbl dɪsˈkləʊʒə https://t.co/UKFhw5EBwf https://t.co/uCOkOOoNnP
Freiburg
Joined January 2013
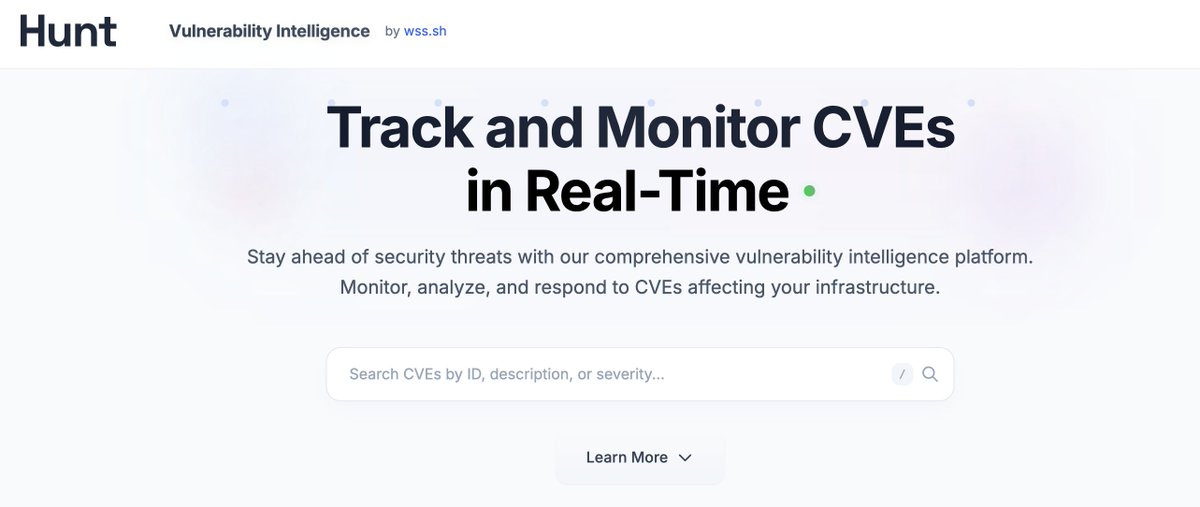
Made a simple dashboard to help track/search CVEs and security vulnerabilities in near real-time. No fancy stuff - just a clean interface to see what's burning in the security world right now. (it's Ivanti🙈) https://t.co/uQ88UEWo0L)
https://t.co/6e32nsFY68 Feedback welcome!
14
113
438
👀 Pre-Auth RCEs and an XXE in Adobe AEM Manager Forms 😏 give it a read!
The @SLCyberSec research team is releasing our final research post for our Christmas in July efforts, two RCEs and one XXE (all pre-auth) in Adobe Experience Manager Forms. One of the RCEs and the XXE still do not have official patches:
1
2
52
The @SLCyberSec research team is releasing our final research post for our Christmas in July efforts, two RCEs and one XXE (all pre-auth) in Adobe Experience Manager Forms. One of the RCEs and the XXE still do not have official patches:
slcyber.io
Vulnerabilities in AEM Forms The Searchlight Cyber Research Team discovered and disclosed three critical vulnerabilities in Adobe Experience Manager Forms to Adobe in late April 2025. As of writing...
6
60
224
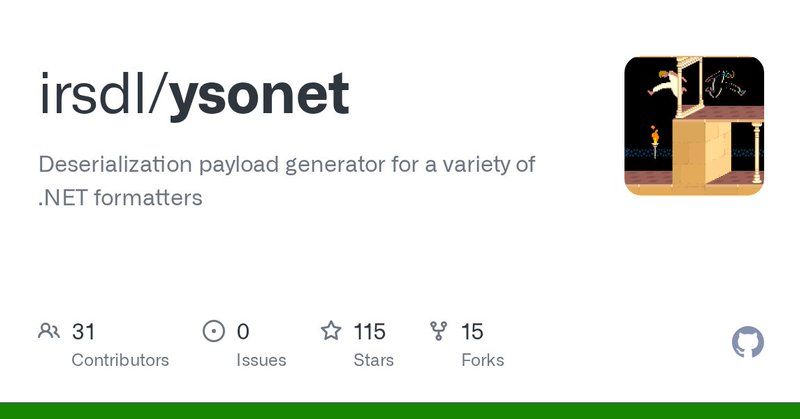
I have launched YSoNet ( https://t.co/9BofGcFaWh) and added #SharePoint CVE-2025-49704 payload generator to it as the first thing. Here is how this can work: Running command: ``` ysonet.exe -p sharepoint --cve=CVE-2025-49704 -var 1 -c "calc" ``` Running C# code: ``` ysonet.exe
github.com
Deserialization payload generator for a variety of .NET formatters - irsdl/ysonet
4
125
479
When applying for a job at McDonald's, over 90% of franchises use "Olivia," an AI-powered chatbot. We (@iangcarroll and I) discovered a vulnerability that could allow an attacker to access the over 64 million chat records using the password "123456". https://t.co/dBqpRpdp9T
ian.sh
When applying for a job at McDonald's, over 90% of franchises use "Olivia," an AI-powered chatbot. We discovered a vulnerability that could allow an attacker to access more than 64 million job...
18
122
469
Hey peeps! As many of you know, I was diagnosed with ALS nearly 2 years ago. I continue to fight a losing battle with it every day. I am determined to live long enough to attend this ALS Walk fundraiser in October. I would sincerely appreciate any small donation you can spare to
10
17
172
Honestly a bit surreal, but I’ll be joining @assetnote as a Security Researcher soon🦆. Excited to be part of such a brilliant team.
32
5
310
How do we turn bad SSRF (blind) into good SSRF (full response)? The @assetnote Security Research team at @SLCyberSec used a novel technique involving HTTP redirect loops and incremental status codes that leaked the full HTTP resp. It may work elsewhere! https://t.co/CTSTEtKiD1
6
180
621
What does it take to hack a @Sonos Era 300 for Pwn2Own? Take a look at our process of adapting existing research, establishing a foothold, and exploiting media parsers for unauthenticated RCE over the network🔥👇 https://t.co/FxSbV3uEBp
1
48
157
Happy Pride Month! Celebrating all the courage it takes to live your truth and love openly. God is love, and whoever lives in love lives in God, and God in them.' - 1 John 4:16 ❣️
0
0
10
Lads, its on
COME AND HACK ALONG WITH US IN LONDON! share this if you can so we can reach more people 😀 https://t.co/GWfqRtT9y9
#hackerone #BugBounty #hackathon
0
0
2
Just waiting on the AI that cleans up AI-generated slop. Should be any day now. 🤌🏻
2
0
11
1/ In late 2023 a former Yuga Labs security researcher was stopped at the airport after law enforcement mistakenly linked them to a $1.1M phishing theft from a Bored Ape owner. Here’s an investigation into where the stolen funds went and who’s actually responsible.
256
593
4K
I made a tool to help test archive (zip/tar) extraction bugs (synk working directory into archive, add path traversals, links, permissions, etc):
github.com
Archive Alchemist is a tool for creating specially crafted archives to test extraction vulnerabilities. - avlidienbrunn/archivealchemist
1
31
171
MITRE’s CVE funding just dried up because the US can’t get its paperwork in order. Maybe global cybersecurity shouldn’t depend on one country’s clown show. Just a thought.
2
2
37