hakluke
@hakluke
Followers
88,338
Following
1,725
Media
779
Statuses
12,753
Hacker, bounties, entrepreneur. I help cybersecurity companies produce amazing content for their blogs and socials. Founder of: @haksecio and @hacker_content
🇦🇺🦘
Joined July 2017
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
Will Still
• 123409 Tweets
Rio Grande do Sul
• 109632 Tweets
#MOONLIGHT_MVTeaser
• 94331 Tweets
プロフェッショナル
• 54135 Tweets
RPWP CONCEPT PHOTO 2
• 47000 Tweets
JOONGDUNK LOVE WORKPOINT
• 34776 Tweets
YOASOBI
• 28234 Tweets
青山先生
• 27947 Tweets
SDカード
• 24528 Tweets
عدنان البرش
• 15686 Tweets
#無責任でええじゃないかLOVE
• 14127 Tweets
VACHSS
• 13809 Tweets
排外主義的
• 13664 Tweets
Last Seen Profiles
Giveaway! 🎉
I'm going to buy someone a new MacBook Pro M2 13".
To enter, retweet this tweet, then follow:
@hakluke
,
@hacker_content
&
@haksecio
.
If you're a cybersecurity org looking for high quality content and social media management, check out 👇
546
2K
1K
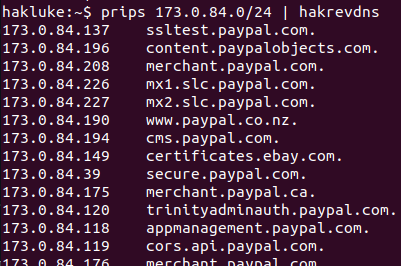
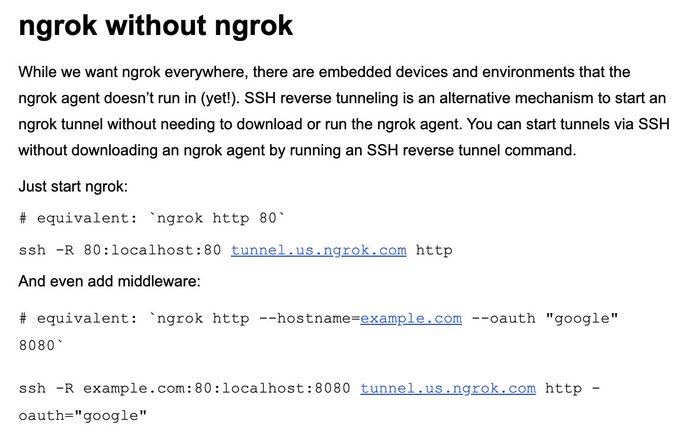
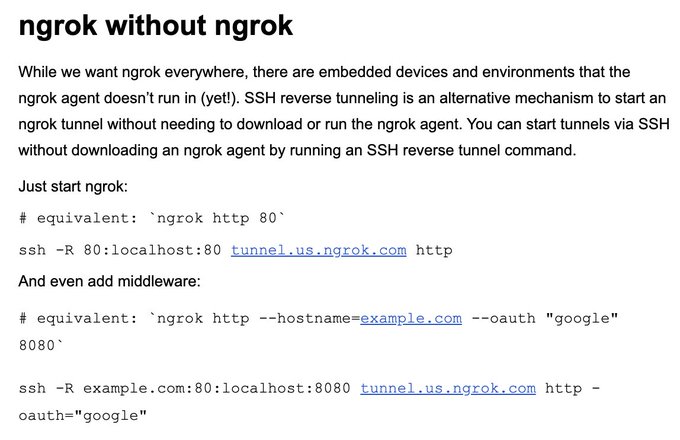
This is my day-to-day hacking tool stack:
🛠️ Burp
🛠️ Nmap
🛠️
@securitytrails
🛠️
@Shodanhq
🛠️
@spiderfoot
🛠
@ipinfoio
🛠️ My own tools ()
🛠️ Everything by
@pdiscoveryio
🛠️ Everything by
@tomnomnom
That covers about 99% of my hacking 🤷♂️
9
261
1K
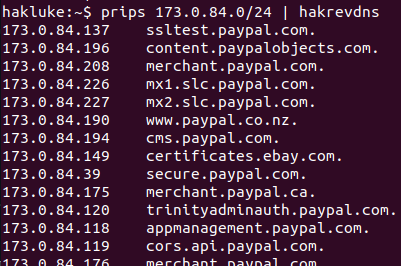
This is my day-to-day hacking tool stack:
🛠️ Burp
🛠️ Nmap
🛠️ Httpx
🛠️
@securitytrails
🛠️
@Shodanhq
🛠️
@spiderfoot
🛠️ My own tools (mostly open source on github)
🛠️ Everything by
@projectdiscoveryio
🛠️ Everything by
@tomnomnom
That covers about 99% of my hacking 🤷♂️
20
145
745
Okay here's the deal.
I'm giving away 100
@TCMSecurity
training courses. 50 of them are the Practical Ethical Hacking course, and the other 50 are Practical Malware Analysis & Triage.
To enter:
1. Retweet this tweet
2. Follow
@hakluke
,
@haksecio
and
@hacker_content
Good luck!
162
845
655
@typjohns
Actually this truck is from a random post on reddit:
The picture is fake, I'd guess the story is too!
47
11
684
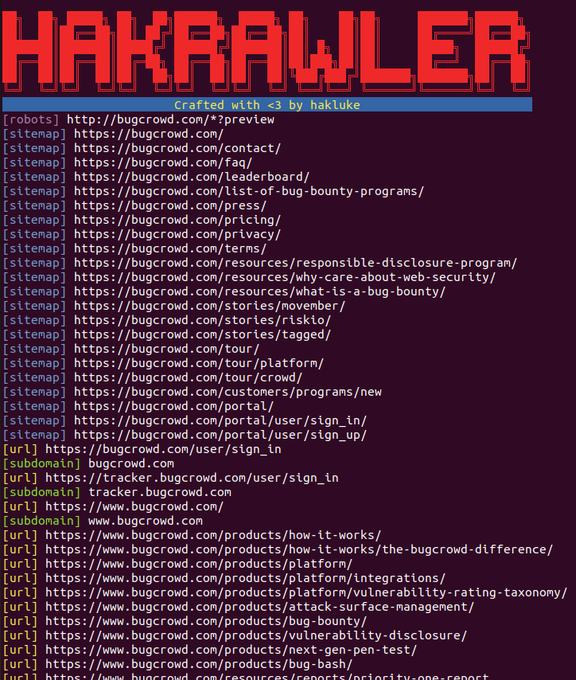
How to hack web applications in 2023: Part 1 🚀
💻 Types of web apps
⚙️ Setting up for testing
🪲 RCE
🐞 SQLi
🐛 XXE
🪳 Insecure Deserialization
🐜 XSS
And that's just Part 1! 😱 👇
#hacking
#pentesting
#bugbounty
12
187
624
Did you know
@Cloudflare
released an open source vulnerability scanner that is based off Nmap and Vulners?
👉 Nmap locally within a container
👉 Push results to cloud
👉 Deploy the scanner on Kubernetes
It looks amazing! How did I only just find out?
6
141
525
I just hit 30k followers 😊
To celebrate giving away 30
@PentesterLab
subscriptions.
To enter, quote tweet this with a message of gratitude to someone that has helped you become a better hacker/human.
Thanks to
@PentesterLab
/
@snyff
who provided 50% of the subs.
❤️🧡💛💜💚
93
78
491
python2 is being deprecated, so it's time to switch:
python -m SimpleHTTPServer
with
python3 -m http.server
Thanks
@rabb1t0x21
!
8
161
460
How to hack web applications in 2023: Part 2 🚀
🪲 SSRF
🐞 Business Logic Vulns
🐛 IDORs
🪳 Authentication Issues
🐜 CSRF
🕷 Directory Traversal
🦟 File Inclusion
And that's just Part 2 😱 👇
#hacking
#bugbounty
#pentesting
9
128
462