Jonny Johnson
@JonnyJohnson_
Followers
8K
Following
4K
Media
286
Statuses
3K
Principal Windows Security Researcher @HuntressLabs | Windows Internals & Telemetry Research
Learning
Joined June 2016
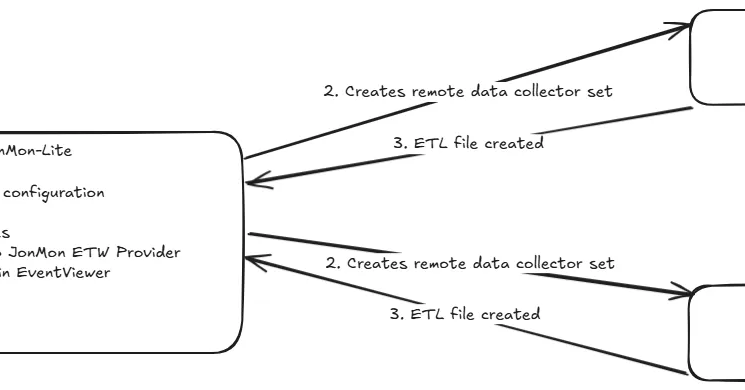
Have you ever wondered if there was a way to deploy a "Remote EDR"? Today I'm excited to share research I've been working on for the past couple months. This dives into DCOM Interfaces that enable remote ETW trace sessions without dropping an agent to disk. Includes a detailed
jonny-johnson.medium.com
As the reader, I’m sure you’re thinking — “oh great, another EDR internals or bypass post”. I can fully understand that sentiment, as…
15
127
376
This is huge news, #sysmon going native in Windows 11 next year. https://t.co/Bmb7bTyPX3 More cool stuff on custom logging coming this week. Watch this space 😎
techcommunity.microsoft.com
Learn how to eliminate manual deployment and reduce operational risk with Sysmon functionality in Windows.
8
59
174
YOOO THIS IS SICK
@JonnyJohnson_ @VikramVenkates9 @DebugPrivilege @33y0re @yarden_shafir All individual courses are 40% off, like "Mastering WinDbg" https://t.co/KJgTgT55V0
0
0
11
I merged a PR from @ScoubiMtl that now includes compatibility with BHCE. Thanks @ScoubiMtl !
github.com
Custom Query list for the Bloodhound GUI based off my cheatsheet - hausec/Bloodhound-Custom-Queries
2
32
106
Today I am releasing a new blog on Windows on ARM! It comes from the perspective of one, like myself, who comes from an x86 background and is new, but, interested in Windows on ARM! ELs, OS & hypervisor behavior (with VBS), virtual memory, paging, & more! https://t.co/jUHls4wupu
connormcgarr.github.io
Analysis of Windows under ARM64: exception/privilege model, virtual memory mechanics, and OS behavior under VHE
2
77
292
Here is the direct link to my talk! https://t.co/FzkvP2eMPg
0
4
10
Had a great time speaking at @SAINTCON on my research about Remote EDR! Thank you to the organizers for having me! Live Steam: https://t.co/HfhAYp4EAA Slides: https://t.co/DGv3KfR7O7 Blog:
1
23
61
And just like that, the first iteration of Alerts to Adversaries is complete! 🎉🎉 This week @Level_Effect and I gave the first offering of Alerts to Adversaries. The class started with classification methodology - a valuable skill for anyone working in Detection Engineering or
3
5
28
Today I am happy to release a new blog post about Pointer Authentication (PAC) on Windows ARM64! This post takes a look at the Windows implementation of PAC in both user-mode and kernel-mode. I must say, I have REALLY been enjoying Windows on ARM!! https://t.co/isnItJ0nb3
preludesecurity.com
Explore how Windows implements Pointer Authentication (PAC) on ARM64—covering bootloader setup, per-process keys, HyperGuard, and memory-safety defenses.
8
64
210
Next week will be the first instruction of Alerts to Adversaries! This will be a super fun course as students will learn OS internals, SOC/Detection Methodology, track alerts to real life scenarios, as well as interact with Microsoft Sentinel / KQL. It’s also the first course
🚨 Alerts to Adversaries starts NEXT WEEK! 🚨 Ready to level up your threat hunting skills with Sentinel? Learn directly from Jonathan Johnson (@JonnyJohnson_), Principal Windows Security Researcher, as he guides you through real-world threat hunting techniques. 📅 October
1
6
32
This is a crucial mental exercise. I think it’s easy for us to just copy and paste things, but there is immense value in truly understanding the operations taking place under the hood.
One of the best advice I gave an intern once was ''It's great that you know how to follow a tutorial online and use Rubeus to perform a Kerberoasting attack, but what is actually happening under the hood and how can we introspect the implementation details?''
0
0
7
Security streams are BACK! 🔴 After focusing on content and live training, we're returning to our Saturday streams starting October 25th. STREAMS: Reverse Engineering 3 - Oct 25 @ 2PM EST Reverse Engineering 4 - Nov 1 @ 2PM EST Malware Analysis Home Lab 1 - Nov 8 Malware
news.leveleffect.com
October 2025 Update
1
3
4
A while back I was curious about the access check that occurs when someone tries to consume from the Threat-Intelligence ETW provider. I decided to write a short blog on the topic. https://t.co/6cpUDSMNF5
jonny-johnson.medium.com
Introduction
0
23
59
Super stoked for the first iteration for this course! If you can, come hang out. All feedback welcome!
🚨 COURSE UPDATE: Alerts to Adversaries 🚨 by Jonathan Johnson (@JonnyJohnson_ ) Link 👉 https://t.co/Jekn46lExR NEW SCHEDULE: 📅 Oct 16-18 (Thursday-Saturday) Thursday 16th: 1-6pm EST Friday 17th: 10am-4pm EST Saturday 18th: 10am-3pm EST We've condensed our training into one
0
1
5
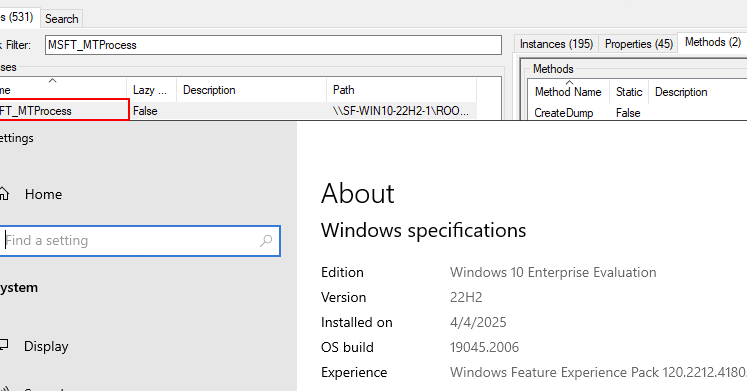
I came across a WMI Win_32 Process replacement with some extra useful functionality. https://t.co/aDX8y8XZUy
specterops.io
TL;DR: Win32_Process has long been the go-to WMI class for remote command execution. In this post we cover MSFT_MTProcess — a newer WMI class that functions like Win32_Process but also offers...
1
34
118
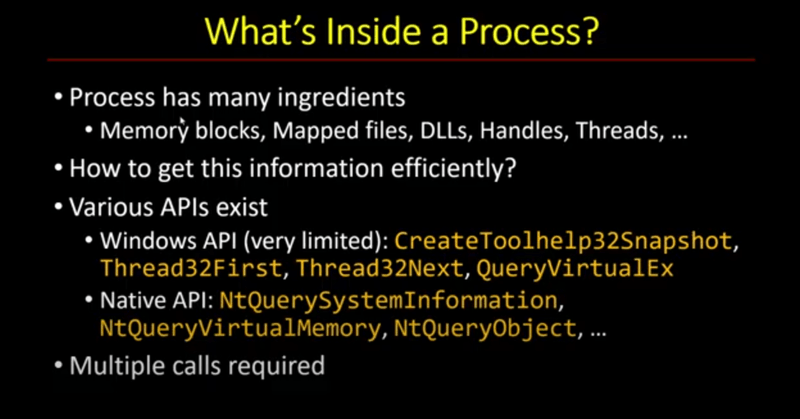
New video: exploring process snapshotting in Windows. Capture threads, memory, and handles with a single API call using PssCaptureSnapshot. https://t.co/BsQKEtdGIG
trainsec.net
Learn how to use process snapshotting in Windows with PssCaptureSnapshot, PssQuerySnapshot, and PssWalkSnapshot. Capture threads, memory, and handles efficiently in one step.
0
22
134
Today I am releasing a new blog post on VSM "secure calls" + the SkBridge project to manually issue them!! This blog talks about how VTL 0 requests the services of VTL 1 and outlines common secure call patterns!!! Blog: https://t.co/xzB1s7HoPO SkBridge: https://t.co/0zO0E1L4Sy
3
100
259
Let's gooo!! First CVE👀? With none other than @wdormann :) https://t.co/fNPkp3YwrE
CVE-2025-59033 The Microsoft vulnerable driver block list is implemented as Windows Defender Application Control (WDAC) policy. On systems that do not have hypervisor-protected code…
6
13
56