@tas_kmanager
Followers
934
Following
3K
Media
38
Statuses
279
☁️🛡️ opinions are mine. food, music and astrophotography when afk. @TheDFIRReport @CuratedIntel #ThreatHunting #DetectionEngineering #DFIR #CloudSecurity
🍁
Joined September 2018
Spent some time today at work playing with @msftsecurity Windows InstallerFileTakeOver LPE (CVE-2021-41379 bypass - https://t.co/jPZB2bTw71) and managed to create some detections on it. Detection will be based on Sysmon/SIEM, here we go... 1/n #threathunting #detection #dfir
1
9
24
🌟New report out today!🌟 From a Single Click: How Lunar Spider Enabled a Near Two-Month Intrusion Analysis/reporting completed by @RussianPanda, Christos Fotopoulos, Salem Salem, reviewed by @svch0st. Audio: Available on Spotify, Apple, YouTube and more! Report:⬇️
5
54
154
#x33fcon 2025 talks: @dirkjan - Bringing Your Own Identity Provider to Entra for Persistence and MFA Bypasses > https://t.co/tQA79Tab2e
3
33
115
It's been a while since I last wrote a KQL query 🎯 Today, I published a blog post about #ZAP response time in #EOP and how we can analyze the timing using #KQL. 🎯 Blog : https://t.co/Hw0vypo0pw * There may already be other approaches or queries to measure ZAP response time
1
7
36
🌟New report out today!🌟 Hide Your RDP: Password Spray Leads to RansomHub Deployment Analysis and reporting completed by @tas_kmanager, @iiamaleks and UC2 🔊Audio: Available on Spotify, Apple, YouTube and more! https://t.co/jL4oy28kS0
thedfirreport.com
Key Takeaways Initial access was via a password spray attack against an exposed RDP server, targeting numerous accounts over a four-hour period. Mimikatz and Nirsoft were used to harvest credential…
1
38
113
We’re seeing a clear trend: attackers are bypassing the endpoint entirely. Not just avoiding traditional EDR-monitored systems by pivoting to embedded and edge devices, but now also operating purely in the cloud. No shell, no malware, no persistence on the endpoint. Just an OAuth
.@Volexity #threatintel: Multiple Russian threat actors are using Signal, WhatsApp & a compromised Ukrainian gov email address to impersonate EU officials. These phishing attacks abuse 1st-party Microsoft Entra apps + OAuth to compromise targets. https://t.co/31cinaoDfB
#dfir
26
316
1K
New table in Advanced Hunting 🎯 OAuthAppInfo table contains information about Microsoft 365-connected OAuth applications !! Make sure you enabled MDA App Governance !! https://t.co/w7f1Lzfsib
learn.microsoft.com
Learn about the OAuthAppInfo table which contains information about Microsoft 365-connected OAuth applications registered with Microsoft Entra ID and available in the Defender for Cloud Apps app...
0
5
28
Just pushed a new versions for #AADInternals and AADInternals-Endpoint modules! Some bug fixes plus support for: 1️⃣ Microsoft Authentication Library (MSAL) 2️⃣ Token Protection 3️⃣ Continuous Access Evaluation (CAE)
2
28
129
If you're up for some Frenglish 😛 my @DEFCON talk about the XZ backdoor is now available on YouTube! And If you are at @BSidesMelbourne, come say hello—I’ll be presenting a shorter version of the talk there. 🤓 #infosec #threatintel
https://t.co/eveLpPNxZh
3
31
82
Very happy to hear my talk has been accepted to @BSidesLondon! 💂🏻🇬🇧 This is something I’ve wanted to do for a long time. Join me to hear about a new resource I’ve created to help prevent ransomware attacks 🔒☣️
1
8
59
Microsoft has been running massive deception campaigns that flood new phishing sites with bogus credentials for bogus companies on MS tenants. When attackers log in, they deliver a torrent of fresh threat intelligence that can be used to defend: #infosec
5
175
671
Between July 2023 and June 2024, Microsoft observed nation-state threat actors conduct operations for financial gain, enlist cybercriminals to collect intelligence, and make use of the same tools and frameworks favored by cybercriminals:
blogs.microsoft.com
Discover the alarming rise in cyber threats, with attacks on Microsoft customers doubling to 600 million per day. The latest Microsoft Digital Defense Report reveals the increasing collusion between...
3
109
216
I created the first draft of a website for the EDR telemetry project to help people quickly compare vendor telemetry visibility. What do you think about it? Are there any specific features you want to see for the website? Built with ChatGPT 4o with canvas (wanted to test it
15
108
439
I am happy to share a new resource I recently created called The Ransomware Tool Matrix: 🔗 https://t.co/2fnq9fc3ge
#CTI #ThreatHunting #ThreatIntel #Ransomware
7
189
491
Our website is up and will be updated with all the latest informations about the conference. Have a look and give us your feedback! https://t.co/8N2jRmZqdO
snowcon.info
SNOWcon 2025 Hacker Winter Camp CFP Opens Soon What is SNOWcon SNOWcon is different from most cybersecurity conferences you have heard of or attended. First, it changes venue every year and plan to...
0
6
10
🎁 Today I'm giving away 3 of our DFIR Labs! 🎁 To enter: ✅Follow me ✅RT & Like this post ✅Reply with which case you'd like to take The winners will be selected in 24 hours. #Giveaway
🎉 Announcing DFIR Labs! 🎉 Introducing our DFIR Labs based on real intrusions from our public reports and private threat briefs! Whether you're starting out or looking to deepen your skills, our labs can help. 1/2
70
90
139
Happening now at #New2CyberSummit: @tas_kmanager and Sylvain Lu share a day in the life of detection engineers. Hear this talk: https://t.co/RKYVH52AYD
#CybersecurityJourney
0
2
4
Would you be interested in testing LSASS dumping simulation ? 🚀 Testing script is available ↓ ↓ ✅ Simulation : https://t.co/DLIPgU2LQd
#MDE #EDR #MDAV #EPP #MicrosoftSecurity
github.com
ResearchDev - XDR & SIEM Detection. Contribute to LearningKijo/ResearchDev development by creating an account on GitHub.
0
4
31
Got a new blog out today with some ideas around hunting for cloud session anomalies - I think this is a super relevant topic with cookie/token theft TTPs being all the rage these days! https://t.co/UJAZcOEgbp
sumologic.com
Learn how to hunt for cloud session anomalies resulting from phishing attacks or stolen cloud credentials. Read how to threat hunt in a cloud-native world where the impossible is possible.
0
17
34
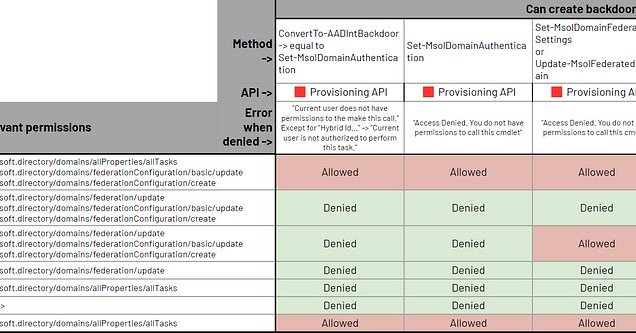
Easily one of the best articles I've read this year! @cnotin: https://t.co/RSiNZW0c97
medium.com
Which Entra ID (ex-Azure AD) roles allow configuring federated authentication, thus allowing persistence and privilege escalation 💥
3
54
153