Kijo Ninja
@kj_ninja25
Followers
2K
Following
2K
Media
269
Statuses
801
Security PM, R&D @Microsoft - Microsoft Defender XDR, Kijo Ninja 🥷 #修行中 - learning C/C++ #Triathlete 🏊♂️ 🚴 🏃♀️ My tweets are my own
Switzerland ~ Japan 🇨🇭🧀 🍫
Joined March 2023
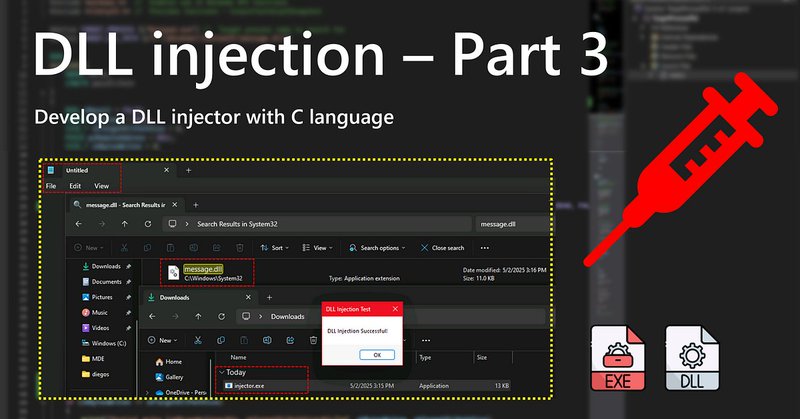
New Blog 🎯.So excited to share the final part of my DLL injection blog 🎉 It covers designing the DLL injection, building the injector, and simulating the injection process!!. ✅ Blog : That’s all for my holiday learning update. I hope you enjoy it 🔥.
systemweakness.com
Final part, Hands-on DLL injection using injector.exe — complete code, simulation results, and common pitfalls in C language
0
41
145
North Korean threat actor known as Jasper Sleet is targeting various industries and companies across multiple countries to gain financial advantage and access sensitive information. ✅ Blog : 🎯 Techniques : VPN, RMM, GenAI tool . #MSTIC #MSFTSecurity.
microsoft.com
Since 2024, Microsoft Threat Intelligence has observed remote IT workers deployed by North Korea leveraging AI to improve the scale and sophistication of their operations, steal data, and generate...
0
0
4
Hello Defenders .I've been writing a few blogs about #BEC activities 🎯 — especially focusing on common attack techniques in Persistence and recent trends showing how BEC attacks are evolving. If you're curious, please check them out 🚀 . ✅ Blog :
0
2
51
📢 Hello New blog !!.The Evolution of Generative AI and the Risks We Can’t Ignore 🎯 . In this blog, I’ve put together a brief summary exploring:.🚀 What kind of risks Gen AI presents.🚀 What #AIjailbreaks are.🚀 How these jailbreaks are carried out.
osintteam.blog
Exploring how AI models are jailbroken using clever prompts that exploit their limitations and override safety filters
0
3
10
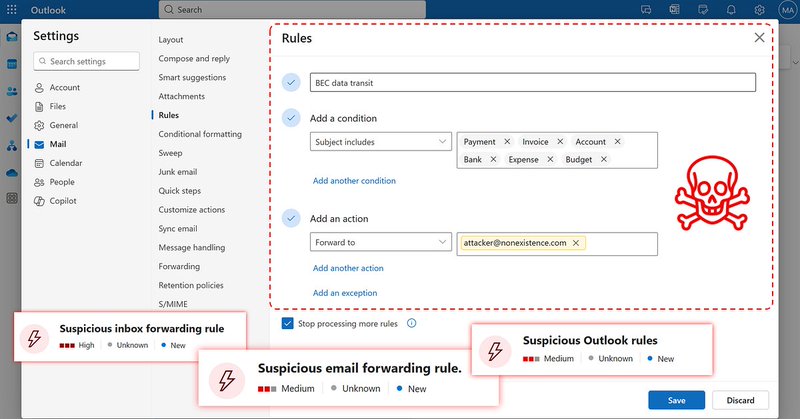
Do you want to know how BEC attacks maintain persistence and exfiltrate your data? 🎯. ✅ Blog : Writing about a forwarding rule creation, detection, investigation and so on !!.If you're curious, please check it out on my tech blog 🚀.
osintteam.blog
Understanding Email Forwarding Rule Abuse in Post-BEC Attacks
0
18
66
RT @msftsecurity: Attackers are getting smarter, but so are we. See Microsoft Defender for Endpoint in action and learn how to supercharge….
microsoft.com
Learn why CISOs prefer Microsoft Defender for Endpoint to secure their device estate across Windows, Linux, macOS, iOS, Android, and IoT devices.
0
11
0
Hello security folks .Great report on recent identity-based attack techniques by @MsftSecIntel 🎯. ✔️ #AiTM credential phishing.✔️ Device code phishing.✔️ #OAuth consent phishing.✔️ Device join phishing.✔️ #QRcode .✔️ Teams phishing like teams phisher.
microsoft.com
Threat actors continue to develop and leverage various techniques that aim to compromise cloud identities. Despite advancements in protections like multifactor authentication (MFA) and passwordless...
0
9
54
New Blog - BEC Starts Here: Tracing the First Entry Technique 🎉. I had a chance to explore common BEC entry points and initial access techniques 🎯, highlighting email threat trends from the past 5 years. If you’re curious, feel free to check it out !!.
osintteam.blog
Understanding the first steps attackers take to conduct BEC fraud and how these techniques have been evolving.
0
10
56
During my holiday, I had the chance to learn about DLL injection and wrote three blog posts documenting my step-by-step learning process 🎯 If you’re curious, feel free to check them out!. ✅ Blog : #Holidaylearning #EndpointSecurity
0
1
4
According to Microsoft research, the education sector is more likely to face identity-related attacks🎯 In fact, 44% of these accounts were never re-enabled after disruption actions were taken. ⚠️⚠️⚠️. ✅Blog : #HolidayLearning.
techcommunity.microsoft.com
Maintaining a robust security posture is essential for any organization. Strong security not only protects sensitive information and assets from cyber...
0
3
10
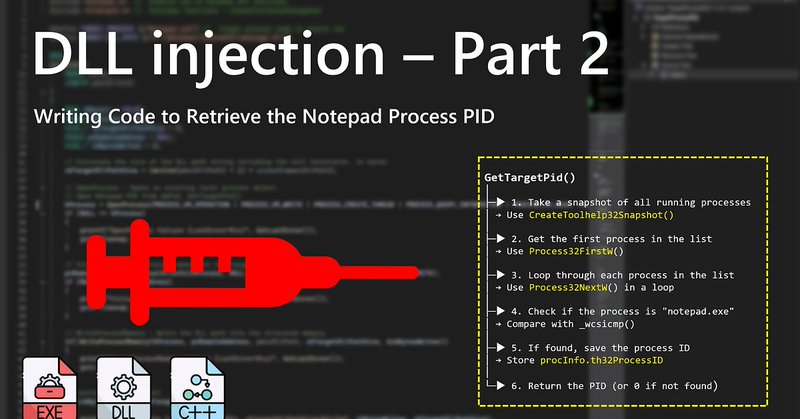
Curious about DLL injection 🚀🚀🚀. In Part 2 of the blog, I covered the function that retrieves the Notepad PID to load the DLL file. If you missed it, you can check out Part 2 here 👉 : #Security #EndpointSecurity
0
0
12
New Blog - DLL injection Part 2 🎉. ✅ Blog : 🚀 Kicking off my coding journey step by step !! Starting with the basics—grabbing Notepad’s PID using C and the Windows API. 🔜 Up next in Part 3: Completed DLL Injection in action. Stay tuned !!.
systemweakness.com
Getting started with writing DLL injection code step by step — GetTargetPid() for Notepad in Windows API, C
0
1
20
Hello everyone !!.I’ll be posting Part 2 of my DLL injection blog this week 🚀🚀🚀. Hope you enjoyed Part 1. If you missed it, you can check it out here - Stay tuned 🎯.#security #cybersecurity #edr #epp.
systemweakness.com
Understanding Windows DLL Injection and Simulating It with Mavinject.exe
0
2
21
Hello defenders.Yes it’s a new blog - DLL injection part 1 🎯🎯🎯. ✅ Blog : I am writing part2, and 3 !! Stay tuned 🔥.
systemweakness.com
Understanding Windows DLL Injection and Simulating It with Mavinject.exe
1
18
106