Patrick Wardle
@patrickwardle
Followers
40K
Following
16K
Media
878
Statuses
10K
🛠 🍎 👾 Objective-See'ing & DoubleYou'ing
Maui, HI
Joined October 2013
Stoked for the next (ad)venture: "DoubleYou" Cofounded w/ long-time friend @hexlogic, we're empowering those building security tools for Apple devices 🍎🛡️. And by bootstrapping this venture, our core value of democratizing security remains our focus!.
techcrunch.com
Patrick Wardle and Mikhail Sosonkin want to sell specific tools to cybersecurity companies focused on protecting Apple devices.
17
31
168
RT @moonlock_lab: @9to5mac 2/7: While digging, our engine flagged a new JSCoreRunner sample with 0 detections on VirusTotal (as of 2025-09-….
0
2
0
RT @moonlock_lab: 1/7: Huge kudos to Mosyle for the original catch and to @9to5mac for spreading the word (. Our La….
0
7
0
RT @quarkslab: The two bytes that make size matter:.Reverse engineering Apple's iOS 0-click CVE-2025-43300 improved bounds checking fix, by….
0
34
0
RT @osint_barbie: Last week brought a wave of articles on mentalpositive and his #macos #stealer . Seems like it’s a prime time to meet the….
0
5
0
RT @khronokernel: This year’s Security Researcher Device application is now open 🎉.
security.apple.com
Get an iPhone dedicated to security research through the Apple Security Research Device program. Learn how to apply.
0
16
0
Was stoked to talk nerdy w/ @KandjiOfficial on their "Patch Me If You Can" podcast! Have a listen 🎙️🎶.
@patrickwardle shares why he thinks Apple is becoming "more friendly" with the external security research community. What's your perspective? Feel free to drop your perspective in the comments. P.S. Watch Patrick's full Patch Me If You Can™ episode here:
1
4
20
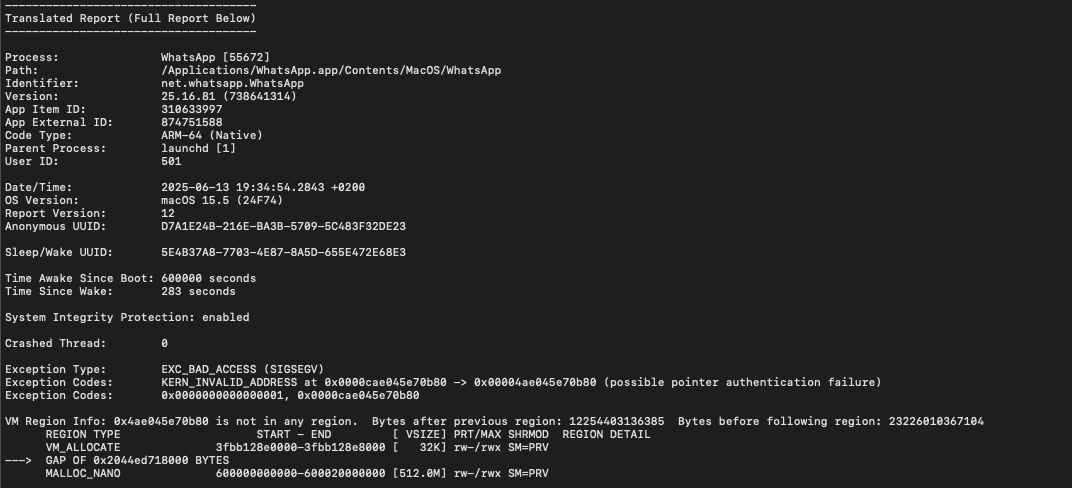
Maybe we should all be taking closer looks at our iOS/macOS WhatsApp crash reports!? 😬 (TBD if related to CVE-2025-55117)
WhatsApp just patched a very fun zero-click bug (CVE-2025-55177)! WhatsApp assesses that it was used partially in conjunction with the iOS RawCamera DNG vulnerability (CVE-2025-43300)
0
12
90
RT @billmarczak: WhatsApp just patched a very fun zero-click bug (CVE-2025-55177)! WhatsApp assesses that it was used partially in conjunc….
0
30
0
RT @OliviaGalluccii: I'm thrilled to share my latest blog post on Mach-Os, its role on macOS, and how it works with Apple's Code Signing an….
0
22
0
RT @g0njxa: In the past days I've been observing a malware campaign using X verified accounts affiliated to account @KindleBookVerse (I see….
0
28
0
RT @osint_barbie: 3/ VT intel: first seen July 18. Still just 2 detections (Ikarus + Google). Earlier only Ikarus flagged it. https://t.co/….
0
2
0
RT @osint_barbie: 2/ Key URL in strings: https://progressdev[.]xyz/salon. Hitting the URL returns an AppleScript starting with: osascript -….
0
2
0
RT @iblametom: 🚨NEW 🚨Russia is mandating a new VK messaging app called Max. We had some researchers take a look and it's tracking basicall….
forbes.com
Security researchers found that Max, which Russia will require to be pre-installed on all phones, is designed to track users, confirming fears the app will be used for surveillance.
0
11
0
RT @objective_see: Who's excited for the #OBTS v8 🍏-themed CTF?. Bring your hacking skills, solve some (Apple) juicy challenges, and win pr….
0
8
0
RT @osint_barbie: 1/ Nice catch by @g0njxa: ads drop #macOS #stealer as well. First stage: signed DMG "Alli-Ai.dmg". Inside: Mach-O file na….
0
31
0
RT @msuiche: 🚨 New blog post: ELEGANTBOUNCER - Catch iOS 0-click exploits without having the samples. Features iOS backup forensics & messa….
0
63
0
RT @objective_see: We've just added this sample, "RustyPages" to our public macOS malware collection!. (pw: infect3….
github.com
macOS Malware Collection. Contribute to objective-see/Malware development by creating an account on GitHub.
0
7
0
New RE Blog Post: RustyPages-Pt1. We RE a Rust dropper, that sets persistence and runs the downloaded next stage, queries @patrickwardle's tools, and quiets notifications. We included relevant IOCs as we continue our analysis of the loader for Part 2. :).
1
6
35