@nordenlund
Followers
101
Following
952
Media
10
Statuses
1K
The 2025 SANS #HolidayHack Challenge launched about an hour ago! Come have some fun building cybersecurity skills in this free @SANSInstitute gift to the community. https://t.co/k9hRtwltm8 New micro-challenges, new gamified world, new music, new game dynamics! Check it out!
3
31
73
🚨 Big News! Version 1.2 of the CTI-CMM framework is here! 🚨 We’re proud to officially debut this release at the FIRST CTI Conference during the talk: 🎤 "Immaturity Can Be Fun: Just Not in a CTI Program" 🎤 by @gertjanbruggink What’s new in v. 1.2? ✨ A brand-new
0
8
17
Automated AI Malware Reverse Engineering with MCPs for IDA and Ghidra Full VIBE RE livestream 🏝️
1
92
367
Special thanks to @mrexodia IDA MCP https://t.co/rr4A2QhYoN Ghidra MCP (thanks @lauriewired ) https://t.co/r2LVdaDQ2z Prompts, sample, and generated reports can be downloaded from Patreon here (free) https://t.co/gJcm6b5rkU
1
6
20
🤓 I just published my notebook on the BlackBasta chat log leak! It’s a dynamic @marimo_io notebook you can run in your browser—no setup needed. Be patient, though—it takes a few seconds to load as the notebook is heavy. Here is what I did 👇 ➡️ Generated diagrams to vizualise
6
46
167
🤓 I took a quick look at the BlackBasta chat log leaks, there are some interesting findings. Here is my full analysis process using Python and generative AI. A small thread👇
4
39
180
⚠️PSA: Curated Intel members in DFIR have noticed a trend in exploitation of CVE-2024-57727 in the SimpleHelp RMM tool to deploy Medusa ransomware. ➡️ This tool is often used by IT Managed Service Providers (MSPs) to remotely control customer endpoints and have been impacted.
2
20
45
ICYMI: In October 2024, we released the CTI Research Guide. It aims to help practitioners learn more about how to effectively perform the collection, processing, analysis, and production stages of the CTI lifecycle. 🔗 https://t.co/OMToNzb8vS
1
21
65
You likely aren't collecting all available events to the Unified Audit Log First, not all events are enabled or retained optimally. Consider creating this policy in the Purview portal (leave users and record types blank to collect everything). Retention is based on license...
8
38
234
🤓 Quick interesting tool for data extraction with LLM. Extract Thinker is a document intelligence tool to extract and classify structured data from documents, like an Object-Relational Mapping system for document processing workflows. Pretty useful if you need to process a
2
18
64
https://t.co/Egu4pYn2uR This repository is a compilation of all APT simulations that target many vital sectors,both private and governmental. The simulation includes written tools, C2 servers, backdoors, exploitation techniques, stagers, bootloaders, and many other tools
3
54
152
🙌 6 Things That Will Take Your CTI Report to The Next Level These six best practices will raise the level of your threat intelligence reports. Make sure to include them! 🚦 Classify the Sensitivity of Your Report Use an information classification framework like the Traffic
1
3
4
Good checklist for offboarding employees. https://t.co/euo8gyYBev Use in conjunction with this: https://t.co/hgWZAgyjgd
learn.microsoft.com
Block access to Microsoft 365 so a former employee can't sign in, secure organization data, and allow other employees to access their email and OneDrive data.
3
52
285
This looks promising - The Cloud Threat Hunting Field Manual: Azure https://t.co/dkR3X7cCJV
3
73
303
Today cybersecurity industry leaders launched the Cyber Threat Intelligence Capability Maturity Model @CTIcmm designed to support organizations of all sizes in CTI. 📑 Get your copy and start growing your program: https://t.co/l1sbAVCAPi 🔗 Learn more: https://t.co/pKXWg8vs79
0
26
36
🚨 LOLRMM Day 1 and 2 update 🚨 🔥 Spec created. Everything validates against it. 🔥 328~ RMM YAML's. Filled with artifacts. We're still working to clean a few things up - dupes, incorrect items added. We're going to need the most ❤️ here from the community. 🔥CSV, JSON API
6
40
138
MemProcFS 5.10 released! Support for Windows 11 24H2 added! MemProcFS - super fast memory forensics of live memory and memory dumps!
github.com
MemProcFS. Contribute to ufrisk/MemProcFS development by creating an account on GitHub.
0
109
314
We're launching major upgrades to our scanning engine! 🌐 Live Browsing: Interact with websites in real-time, dismiss alerts, solve CAPTCHAs, and more. Real Device Scanning: High-fidelity scans with actual mobile devices. Blog: https://t.co/25liSRLzdw
4
100
345
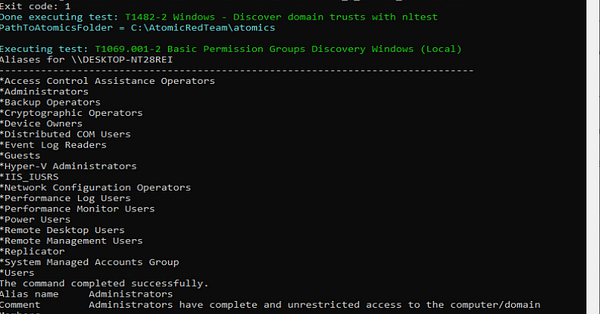
Most excellent write up! Simulating a Akira Ransomware Attack with Atomic Red Team by Sebastian Kandler
link.medium.com
We all know about the risks of Ransomware Attacks, we did our homework and prepared a lot of expensive security tools, set up an SOC…
2
64
219