herrcore
@herrcore
Followers
11,899
Following
475
Media
850
Statuses
8,162
Explore trending content on Musk Viewer
#DebateINE
• 513711 Tweets
Xóchitl
• 473372 Tweets
Claudia
• 428927 Tweets
Maynez
• 170912 Tweets
#CandidataDeLasMentiras
• 121592 Tweets
#DebatePresidencial2024
• 115449 Tweets
Suns
• 98003 Tweets
Real Life
• 89131 Tweets
Anthony Edwards
• 64779 Tweets
昭和の日
• 64191 Tweets
#KAMIGATA_BOYZ
• 58357 Tweets
Timberwolves
• 50873 Tweets
Beal
• 50689 Tweets
Davido
• 49256 Tweets
Wizkid
• 48325 Tweets
DDAY SB19 JAPAN CONCERT
• 45934 Tweets
Durant
• 32682 Tweets
Texcoco
• 32173 Tweets
Booker
• 31205 Tweets
カミガタボーイズ
• 29375 Tweets
TheKingdomsCC x Bright
• 25891 Tweets
為替介入
• 25407 Tweets
Slayer
• 22064 Tweets
ThanksSTY ThanksERICK
• 13964 Tweets
MakinKOMPAK ItuKEREN
• 13709 Tweets
Finch
• 12658 Tweets
Ant Man
• 12163 Tweets
スレイヤー
• 11725 Tweets
Last Seen Profiles
Coming soon...
🤖
#OALabs
VM Installer for Malware Analysis 🤖
We have been working hard to put together a Boxstarter script like FLARE-VM to setup a Windows 7 (x86) VM with all the tools you need to follow our tutorials!
Should be released by Monday stay tuned ...
6
165
454
🤖 VM Installer for Malware Analysis 🤖
Released! Boxstarter script to setup a FREE Windows 7 VM with all the tools you need to follow our tutorials!
Step-by-step install guide
📺 Tutorial video 📺
#OpenAnalysisLive
#OALabs
5
216
422
📺 New Tutorial Video 📺
Reverse engineering C++ malware with IDA Pro: classes, constructors, structs, and more! A first in our series moving beyond malware triage and onto full
#ReverseEngineering
.
#OpenAnalysisLive
#MalwareAnalysis
9
169
407
⚡️Malware Analysis - Quick TIP⚡️
How to unpack process injection with x64dbg one breakpoint!
If you enjoyed this check out our other reverse engineering tutorials on YouTube 😃
#OpenAnalysisLive
#ReverseEngineering
#Malware
4
148
397
📺 New Tutorial Video 📺
Step-by-step reverse engineering
#REvil
ransomware with
#IDA
. What to do once you have unpacked the malware 👨🏫
#OpenAnalysisLive
#MalwareAnalysis
3
127
322
Just found this awesome talk from 2017...
“Everything You Ever Wanted to Know About DLLs”
Highly recommend for folks who are getting started with reverse engineering.
🤜🤛
@JamesMcNellis
1
95
314
📺 New Tutorial Video 📺
Intro to scripting with Python and
#IDAPro
🐍
Learn how to automate resolving the
#REvil
#ransomware
dynamic API calls ⚙️
#OpenAnalysisLive
#MalwareAnalysis
#IDAPython
4
122
294
🎬 New tutorial video 🎬
Unpacking Gootkit malware (stage 1) with IDA and x64dbg!
A little bit of everything in this one... IDAPython scripting, dynamic IAT, memory dumping, debugging, etc.
#OpenAnalysisLive
#malware
#unpacking
3
144
276
🚀 Launch Day 🚀
It’s official this project that
@seanmw
and I have been a part of for 5 years is now available as a free public Beta!
Automated malware unpacking!
#malware
#ReverseEngineering
#automation
#tools
3
121
253
I've mentioned this before but it's worth repeating...
If you want to learn how to reverse engineer structs in
#IDAPro
I highly recommend these two tutorials from .
@moveax41h
Best way to level up your
#reverseengineering
🤓🤓🤓🤓
0
116
231
Nice post from .
@theRealJohnPeng
describing how to use IDAPython to decrypt the stack strings in
#Gootkit
malware. Great introduction for anyone interested in getting started with IDA scripting : )
#malware
#IDAPro
#IDAPython
2
95
208
📺 New Tutorial Video 📺
In this tutorial we cover a malware reverse engineering fundamental - how to identify and decrypt RC4! 🔐
#OpenAnalysisLive
#ReverseEngineering
2
84
197
🎬 New tutorial video 🎬
Unpacking Emotet / Geodo malware using x64dbg (stage 1)
And an interesting case of IAT rebuilding using a python script 🐍
#OpenAnalysisLive
#malware
#unpacking
#tutorial
#x64dbg
6
115
194
📺 New Tutorial Video 📺
Join us while we use
#x64dbg
to unpack
#troldesh
/
#shade
#ransomware
and then we use IDA PRO to quickly decrypt strings and resolve dynamic imports with one very lazy trick! 🤓
#OpenAnalysisLive
#ReverseEngineering
#Malware
4
90
193
⚡️Malware Debugging - Quick TIP⚡️
Level up your malware debugging by disabling ASLR in your analysis VM! We show you how, and why this makes x64dbg and IDA work together so well 💪
#OpenAnalysisLive
#Debugging
3
82
184
🐰 Holiday weekend? 🐰 Time for some more malware unpacking tutorials! Stay tuned : ))
#OpenAnalysisLive
#Unpacking
#Tutorial
1
71
182
Working on a little holiday malware unpacking tutorial 🤓
... then the eggnog kicked in so I made this instead 🥃🤣🤣
#SelfInjectionPE
#Unpacking
#Malware
#TikTok
4
48
174
With the recent conversation about easy affordable access to training, just wanted to post a reminder to check out our
#ReverseEngineering
channel...
We do tutorials, take requests, and answer your questions!
Please RT for everyone learning to RE <3
1
93
170
🎬 New tutorial video 🎬
Analyzing Adwind / JRAT Java Malware!
Decompiling Java, deobfuscation, API hooking, config extraction, automation with Python, we cover it all!
#OpenAnalysisLive
#malware
#adwind
#jrat
5
106
165
Awesome
#MazeRansomware
automated deobfuscation work from
@shamrockhoax
!
Obfuscation libraries in malware seem to be the future so it’s great to see tools like this!
0
68
153
📺 New Tutorial Video 📺
Unpacking
#REvil
(sodinokibi)
#ransomware
with
#x64dbg
. And a dirty hack to fake the IAT for dynamic imports 😉
#OpenAnalysisLive
#MalwareAnalysis
1
67
148
📺 New Tutorial Video 📺
We cover our 5 most used
#IDAPro
plugins for
#MalwareAnalysis
… and how to install them ⚙️
1
44
146
🎬 New Tutorial Video 🎬
Analyze JavaScript and VBScript Malware With API Hooking and x64dbg!
Also a demo of the frida-wshook tool from .
@seanmw
🛠️
#OpenAnalysisLive
#Malware
#WScript
#DFIR
6
77
143
🎬 New Tutorial Video 🎬
Statically deobfuscating and unpacking malware with Python scripts in IDA Pro!
#OpenAnalysisLive
#Malware
#IDAPro
#Automation
3
86
143
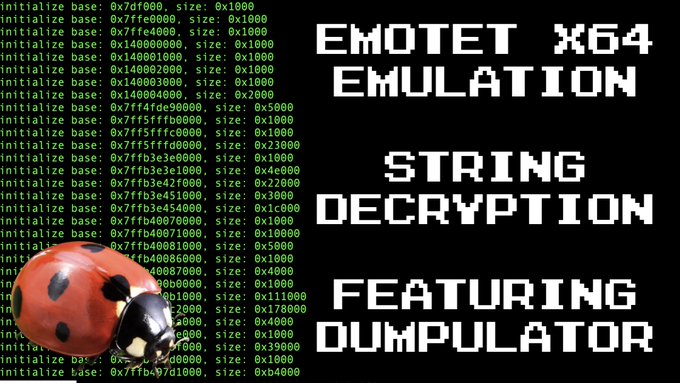
📺
#OALABS
Tutorial 📺
Using
#Dumpulator
#Emulation
to decrypt strings in the new 64-bit
#Emotet
malware
4
46
140
🎬 New Tutorial Video 🎬
“Why didn’t it run in my sandbox?”
Reverse Engineering Anti-VM Detections
#OpenAnalysisLive
#ReverseEngineering
#Malware
#DFIR
0
69
139
📺 New Tutorial Video 📺
Unpacking Gootkit Part 2 - Debugging Anti-Analysis Tricks With IDA Pro and x64dbg
We take a second look at
#Gootkit
#malware
and their new anti-analysis tricks... we also cover unpacking PE-overwrite packers.
#OpenAnalysisLive
0
78
136
🐍 Python3 Tips For RE 🐍
Wanted to share a few
#Python3
#tips
that really helped speed up my
#ReverseEngineering
🚀
2
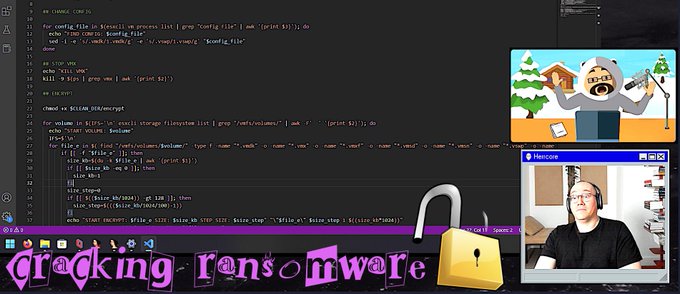
35
136
For those who have been asking…
How do I stay safe while handling malware 😅
🔓We just unlocked this
#OALABS
tutorial for everyone…
** no it’s not another VM setup tutorial, feel free to share with anyone getting started with malware analysis ❤️
0
41
131
🎬 New tutorial video 🎬
Unpacking Princess Locker and Fixing Corrupted PE Header
(with help from our 🦔 friends)
Process dumping with x64dbg and rebuilding the PE header, the fundamentals of unpacking!
#OpenAnalysisLive
#MalwareAnalysisForHedgehogs
3
60
129
Inspired by the awesome work from .
@hasherezade
and .
@struppigel
we’re starting our own RE/analysis tutorial series!
3
72
128
📺 New Tutorial Video 📺
Join us as we reverse engineer
#WarzoneRAT
🐀🔍
Lots of IDA tips in this one and we include the IDC so you can follow along at home ✅
#malware
#OALabs
0
34
127
😲Leaked Conti Hacking Manual😲
👋 Join us LIVE tomorrow 12EST
Special guest
@m0rv4i
will walk us through the
#conti
#ransomware
affiliate training manual from a
#RedTeam
perspective
0
33
127
📺 New Tutorial Video 📺
Learn how to automaticaly decrypt
#REvil
strings with
#IDAPro
and python 🐍
The 4th part in our reverse engineering
#ransomware
deep-dive series. 👾🔍
#OpenAnalysisLive
#Malware
#tutorials
1
51
125
📺 New Tutorial Video 📺
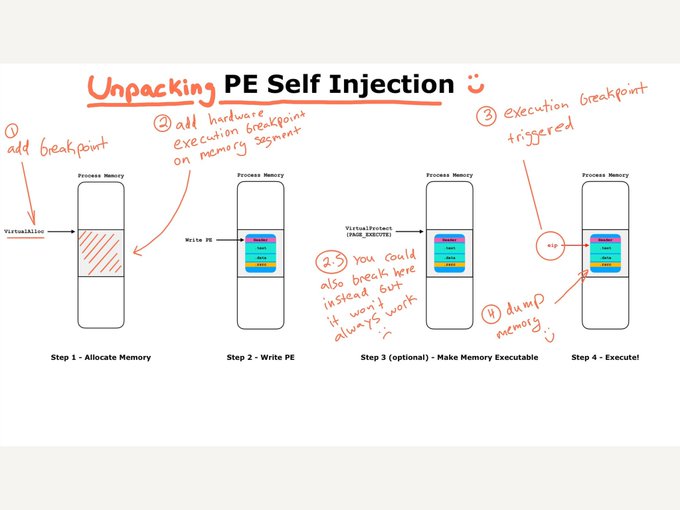
Unpacking and Extracting The TrickBot Config!
We use x64dbg to unpack
#TrickBot
from a multi-stage packer with both process injection and self injection. Then we use a Python script to extract the config!
#OpenAnalysisLive
0
70
121
📺 New Tutorial Video 📺
It's been a while but we're back! And we are talking about "FUD" packers... how do they work from the malware developer's perspective, and how to unpack them!
#OpenAnalysisLive
#OALabs
#ReverseEngineering
1
49
120
🎬 New/Old Tutorial Video 🎬
Unpacking VB6 Packers With IDA Pro and API Hooks!
We've been too busy to create a new video but we found this classic tutorial in our archives. Join us for this blast from the past 😸
#OpenAnalysisLive
#unpacking
#malware
0
69
118
On a related note … I made (another) simple IDA plugin for copying disassembly as hex encoded bytes. Nice for binary searching, and building Yara rules : )
#IDAPython
#ReverseEngineering
#Tools
1
58
113
📺 New Tutorial Video 📺
Join us with special guest .
@JershMagersh
for an introduction to analyzing malware with
#WinDbg
. Everything you need to get started debugging!
#OpenAnalysisLive
#ReverseEngineering
1
53
115
📺 New Tutorial Video 📺
We are back! Join us for Part 1 of our deep dive into
#ReverseEngineering
an IRC Botnet!
#OpenAnalysisLive
1
37
112
📺 New Tutorial Video 📺
Join us for some quick tips to speed up your malware triage with
#BinDiff
and
#IDAPro
!! 🚀
#OpenAnalysisLive
0
43
114
📺 New Tutorial Video 📺
#ReverseEngineering
an IRC Botnet, Part 2
Join us as we use
#x64dbg
and
#IDAPro
to recover structs from injected memory and annotate our binary 🦾
#OpenAnalysisLive
#Malware
1
44
113
📺 New Reverse Eng Tutorial…
Vulnerable Antivirus Driver Used by
#Ransomware
😱
Join us and find out how?!
#OALABS
2
35
112
Last week we took a look at
#TheUndeclaredWar
on stream… it wasn’t pretty 😂
#base64
Check us out on Twitch, Thursdays and Sundays 1300EST… we do actual reverse engineering
#OALABS
9
14
109
New tutorial video 🎉
How To Defeat Anti-VM and Anti-Debug Packers With IDA Pro!
#DFIR
#ReverseEngineering
2
56
110
🚀🚀 Quick
#OALABS
Tutorial
It’s hard enough to learn how to
#ReverseEngineer
… it’s even harder if you are learning
#assembly
at the same time!
💖Here are two tips that can help by enabling asm instruction hints in
#IDA
and
#x64dbg
2
38
112
📚New Tutorial Unlocked
We unlocked this
#tutorial
for free because we get asked this all the time by new
#ReverseEngineering
students… why is the
#debugger
not breaking on “main”?
#OALABS
0
30
108
🚀 Quick Tips For Unpacking 🚀
Made a quick video tutorial covering how to unpack this sample with a few breakpoints and OllyDbg. We are huge fans of ID-Ransomware, keep up the good work Michael!
#malware
#QuickTips
#OpenAnalysisLive
Anyone have a recent unpacked version of
#Hermes
2.1 (.HRM extension)
#Ransomware
? Currently struggling to unpack one, Scylla keeps dumping ntdll.dll lol. Sample: fbeb92ac0acf03216f8430687734d2f72f57a85c994f0f0ea01e65c26e37d92d
2
4
14
2
46
103
New tutorial video is live!
Sandbox tips for faster reverse engineering 💪🤓
#DFIR
#ReverseEngineering
0
48
104
📺 New Tutorial Video 📺
We are back! Join us while we
#ReverseEngineer
#PrnLoader
!
❌❌❌👇
This is one of the weirdest loaders I have ever seen... they use a pr0n video to decrypt an
#emotet
payload! 😳
4
35
104
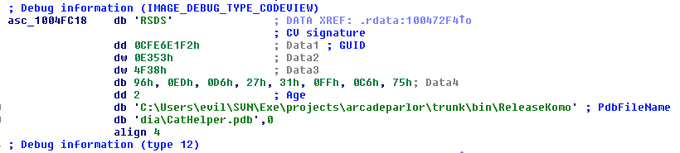
Do
#adware
devs know they are evil? Apparently yes they do.
This is a real debug path from adware…
http://t.co/15mg9nvAFP
6
112
96
This is awesome!
@nullandnull
released a script to translate between the old
#idapython
6.x API and the new IDA 7.0 one!
😺
Now you can easily convert your old scripts!
😺
#IDAPro
#Python
#reverseengineering
1
61
97
We teamed up with
@fwosar
to analyze
#ESXiARGS
#ransomware
which has been tearing across vulnerable VMWare servers on the internet!
We reverse engineer both the deploy script and the elf binary… with some banter along the way 😸
#OALABS
0
26
97
⏲️ Unpacking Quick Tip Tutorial ⏲️
Unpacking
#Remcos
malware from a VB6 packer with
#x64dbg
and one breakpoint!
#OpenAnalysisLive
#MalwareAnalysis
3
58
97
📢 Quick Tip Tutorial Video 📢
Have you noticed x64dbg is crashing when you try to analyze recent malware samples?? We explain why, how we worked around it, and their fix in the new release of the debugger!
#malware
#x64dbg
#OpenAnalysisLive
2
46
92
❓Reverse Engineering AMA❓
#OALABS
and guests answer your questions! New questions each day until new years 🥂
Huge thanks to 💕
@huettenhain
@psifertex
@struppigel
@dr4k0nia
@c3rb3ru5d3d53c
@JershMagersh
@dodo_sec
@washi_dev
📺 Playlist:
0
28
94
This blog is fantastic! Great RE tips and detailed tutorials. Hat tip to whoever is behind it 👍
#DFIR
#RETutorials
1
39
92
🎬 New Tutorial Video 🎬
Part 1 of 2 where we analyze Bokbot /
#IcedID
malware. We unpack the first two stages covering process injection and UPX with
#x64dbg
and
#IDAPro
!
#OpenAnalysisLive
#OALabs
#ReverseEngineering
3
47
85
📺 New Tutorial 📺
We have just unlocked an
#OALABS
Patreon tutorial for everyone…
🚀 Unpacking (
#VMProtect
3) Night Sky Ransomware x64
We use
#VMPDump
to fix the imports and a simple trick to recover the virtualized OEP 😇
1
24
87
😸😸 They are here! 😸😸
Malware Triage: Analyzing Malscripts - Return of The Exploits!
Hard copies for workshop attendees only but if you want a personalized PDF just send us an email info
@openanalysis
.net
#DEFCON
#OALabs
#Workshops
#MalwareAnalysis
8
31
87
📺 New Tutorial Video 📺
Join us with special guest
@mrexodia
for a demo of
#Dumpulator
a binary
#emulator
!
🙌 Easy to use
#Python
, emulation in 5 lines of code
⚙️ Complete Win32/64 env for emulation (minidump)
👾 One-click
#malware
config extraction
0
23
86
🚨We are live on Twitch
All
#Emotet
all afternoon … we will be slowly reversing their new binary…
#REandChill
🍹👾
2
23
82
🎬 New Tutorial Video 🎬
Unpacking Themida 2.x 64bit ... without actually unpacking : )
If a packed sample does process injection we can dump it instead of unpacking!
#OpenAnalysisLive
#malware
#unpacking
4
44
81