The Haag™
@M_haggis
Followers
9K
Following
24K
Media
2K
Statuses
6K
Threat Researcher | Co-Host of Atomics on a Friday | LOLDrivers & Atomic Red Team Maintainer | I'm Everywhere and Nowhere - BSG.
127.0.0.1
Joined March 2007
We are excited to announce the launch of our latest project: https://t.co/eU7leJu9DQ. The inception of this project was sparked by the emergence of the BlackLotus bootkit. Bootloaders/kits - a subject I had never delved into before. My explorations into bootloaders and bootkits
bootloaders.io
6
128
307
The latest msInvader released @BlackHatEvents simulates Storm-2372 post-compromise techniques and introduces Azure attack paths like Key Vault lateral movement. Turn realistic attack telemetry into better detections Check it out ! 📺 https://t.co/OjleJuQZ9q
#EntraID #Azure #M365
1
3
8
Vendors realizing customers now know their data is being monitored by the EDR/MDR/XDR/NDR service they bought:
8
7
63
Relive HOOD Summit '25: Enter the Mainframe. Watch the livestream now: https://t.co/cLhiCw7bpH
27
101
856
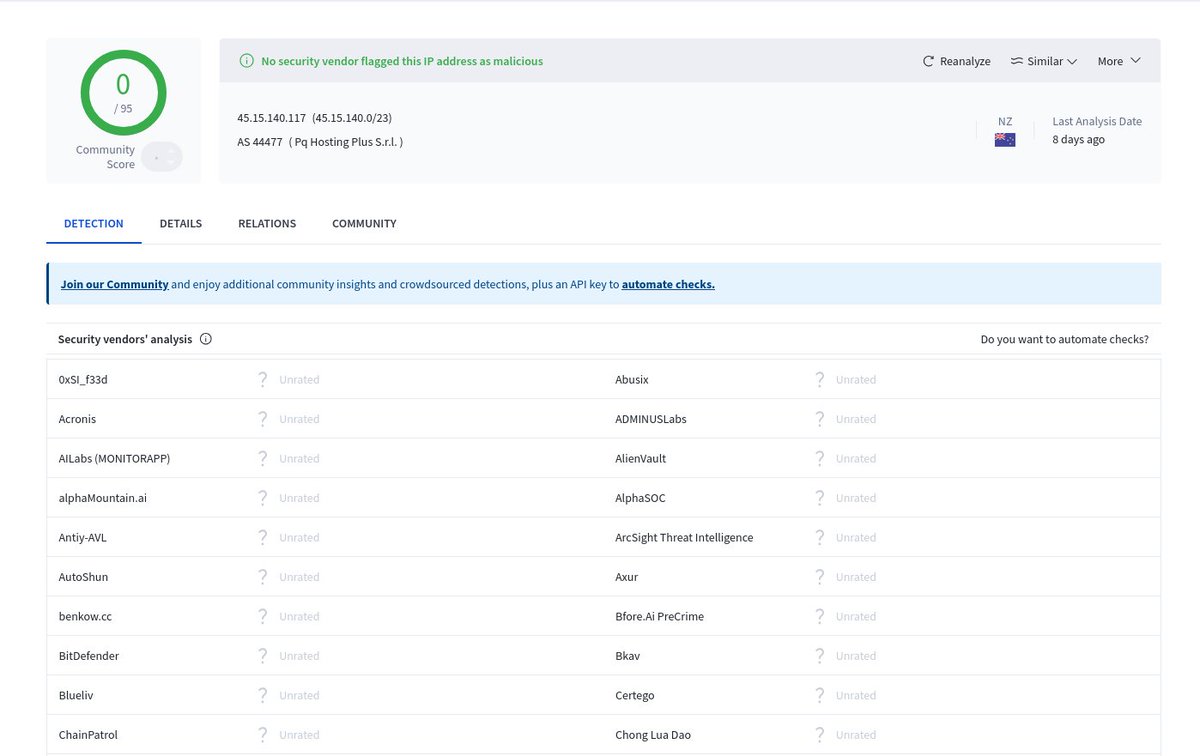
Actor mass exploiting CVE-2025-31324 (SAP Netweaver RCE) from 45.15.140.117 ( Pq Hosting Plus S.r.l. ) 🇳🇿 VirusTotal Detections: 0/94 🟢 Payload contains an obfuscated webshell 📷
0
7
20
Lua: still pulling strings behind the scenes in gaming. • Chrollo - Lua script hook for Garry’s Mod; lets you capture/edit scripts on the fly. https://t.co/RNIFJ3xkZr • Script-Enforcer Bypass - Patch that re-enables lua_openscript_cl, running scripts undetected.
0
0
1
Quantum Cloud-native Zero-trust Elastic Autonomous Multiverse Blockchain Neural Synergistic DeFi LLM
0
0
2
Make America Fentanyl Free supports President Trump’s efforts to end the fentanyl crisis.
160
153
1K
Lua: Watching Since the Beginning. 🌙👁️ 2024–2025 reminded us that Lua isn’t just nostalgia: Redis - CVE-2024-46981 & CVE-2024-31449 let authenticated users abuse the embedded Lua VM for RCE. 📎 https://t.co/MflCE2Mseh OpenWrt LuCI - CVE-2024-51240 turned a Lua-driven web UI
0
4
5
While I’m frantically debugging last issues of the upcoming @DefusedCyber Research tier, a sneak peak from the cutting room floor showcasing some new features: - live mode - exploit tracking - new and more broad detection capabilities and vulnerability tagging almost ready to
1
4
15
Lua: still stealthy, still relevant. In 2025, we saw Line Runner - a Lua webshell embedded in Cisco ASA firewalls by the ArcaneDoor crew, executed via WebVPN customization (CVE-2024-20359) to run arbitrary Lua tasks. https://t.co/UQZeZPVkyd And remember 2024? Gamers chasing
0
5
19
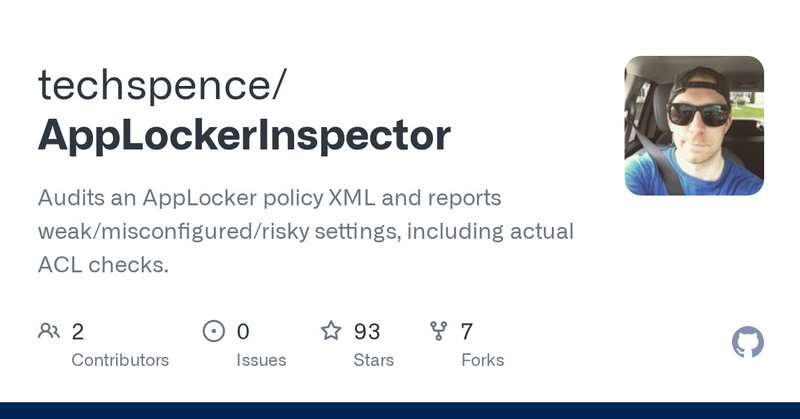
AppLocker can be your best friend or your worst enemy. If you use broad path rules, permissive publisher rules, or allow “Everyone”… Might as well not even use AppLocker 👉Audit your rules with AppLocker Inspector https://t.co/MVFz0PS0qx
github.com
Audits an AppLocker policy XML and reports weak/misconfigured/risky settings, including actual ACL checks. - techspence/AppLockerInspector
4
32
131
My job is done here. :)
@NotNordgaren @_RastaMouse @bohops @M_haggis This looks very interesting. I need to start playing with LUA.
2
0
7
We hired Care Bears to run the 5050 AI Safety incubator. They went all in.
4
6
15
People forget sometimes how old skool the power of Lua really is. 🌙💻 Back in 2012, researchers dissected Flame - one of the most sophisticated cyber-espionage tools ever discovered. 🕵️🔥 It wasn’t just massive in size (20MB+ modular framework) or sneaky in capability
0
6
12
Everyone’s hyped on the first "AI-powered ransomware" 📰🤖 (PromptLock)… but no one’s talking about the real cosmic truth: it was LUA-powered. 🐪✨ LLMs may be the headline… but Lua is the engine running beneath the machine. The hidden script of creation strikes again. 🔮💻Ω
1
3
12
I hope you all know how restrained I am…. Daily…. From posting about Lua lol
1
0
4
Top things I learned while analyzing fake CAPTCHA sites 🧩🔍 1️⃣ You can build a page in under 100 lines of HTML/JS that quietly drops commands into the clipboard 🖱️📋 2️⃣ Most security layers focus on network traffic 🌐 …but these tricks live in the presentation layer 🎭 3️⃣
0
6
27