Mr.Un1k0d3r
@MrUn1k0d3r
Followers
13K
Following
3K
Media
23
Statuses
1K
I don't know how to search on Google so I do research on my own and tweet about it. Hacking as a life style https://t.co/a05mevChzu
Joined January 2012
We are going live tonight at 7 Pam EDT. How Azure and Entra ID can be misused as part of a red team exercise. More information below. #Azure
#RedTeam
https://t.co/YhgFRD8Weh
linkedin.com
Tonight I will continue to show how Azure and Entra ID can be misused as part of a red team exercise. We are going to code the tool live and explore Azure functionality that could be leveraged to...
0
0
7
For some reason, Azure is assumed to be secure by design, which is not the case. Validating the default user permissions is important to ensure that everything that can be hardened is hardened. #Azure #RedTeam
https://t.co/1q8AxyuTSY
fr.linkedin.com
Français plus bas Another week, another Azure advice. We've previously talked about application permissions, phishing vectors, and more. Today, let's talk about Azure configuration itself. When was...
0
9
77
We are hiring for a senior red teaming / pentest role at CYPFER. Interested in applying, feel free to reach out to me. 100% remote role; more information here: https://t.co/SasPPGBBFS
#redteam #hiring #pentest
linkedin.com
We are hiring for our Offensive team. If you are interested in red teaming and traditional pentesting in a highly motivated team, this is your opportunity. If doing R&D, writing your own tools, and...
0
5
10
We are going live tonight at 7 PM EDT. Tonight's session is about Microsoft Azure. We will do a deep dive into how it can be abused as part of a red team. We will automate the process by writing a complete tool to perform attacks and reconnaissance. https://t.co/Efv3aYp2in
0
0
3
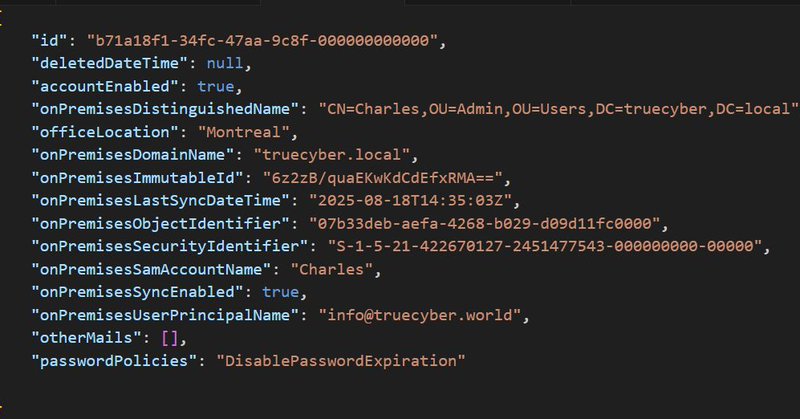
The Azure Graph API /beta/users endpoint is definitely an interesting one, as it now includes on-premise Active Directory information, which was not included in the previous /v1.0/users. https://t.co/CDFZYE0eZd
#Azure #RedTeam #Graph
fr.linkedin.com
Français plus bas I showcased a few interesting Azure applications that can be used to gather more information than allowed by default, including ways to bypass UsersPermissionToReadOtherUsersEnabl...
5
14
93
Interested in attack vectors in Azure. I have documented another example to have read permission on all the applications exposed in the tenant and more. Blocking default applications is crucial to prevent such vectors. https://t.co/U8w6xRoOtm
#Azure #RedTeam
linkedin.com
Français plus bas Interested in learning more about Azure built-in applications that can be misused? Here is another one that allows you to list all the applications deployed within your tenant. A...
0
33
137
I'm working on a useful tool that allowed me to discover quite a few interesting attack vectors in Azure. UsersPermissionToReadOtherUsersEnabled bypass MFA bypass Privileges escalation And more https://t.co/ad8gsRx3ha
#Azure #RedTeam
fr.linkedin.com
Français plus bas Nowadays, Azure tenants prevent user enumeration by setting UsersPermissionToReadOtherUsersEnabled to false. This feature blocks user enumeration within a tenant. However, Azure is...
1
17
142
We are going live tonight at 7 PM EDT. Tonight's session is about running your own LLM locally and building a simple cross-platform .NET client interface to interact with it. The private LLM is quite useful during red team exercises. https://t.co/wHGC8v8NjE
#redteam
0
2
13
You want to load your shellcode in .NET without calling VirtualProtect? Use RuntimeHelpers.PrepareMethod to create a predictable RWX memory region for you. This method also doesn't require a delegate function pointer, since you override a .NET method. https://t.co/8oavXwyGEv
github.com
load shellcode without P/D Invoke and VirtualProtect call. - Mr-Un1k0d3r/DotnetNoVirtualProtectShellcodeLoader
2
94
334
It's time for the long weekend sale! Get 50% OFF when you purchase both the Coding Class and the Red Team Training for just $400 (regularly $800). This includes over 200 hours of videos and source code. More details here https://t.co/YXPrhZsavw
#redteam #discount
2
4
14
We are going live tonight at 7 PM EDT. Tonight's session is about understanding the underlying concepts of Active Directory Certificate Service (ADCS) and how certificate templates can be audited using C#. https://t.co/Efv3aYp2in
0
5
16
Tomorrow at 10 AM, I’ll be presenting a live webinar with CYPFER, where we’ll explore a technique for executing malicious code within a .NET environment. This method is particularly noteworthy because .NET is installed by default on Windows systems. https://t.co/VNkYeyR801
linkedin.com
Save the Date: Tomorrow at 10 AM, I’ll be presenting a live webinar with CYPFER, where we’ll explore a powerful technique for executing malicious code within a .NET environment. This method is...
0
0
7
Next week, I will present a live webinar covering an interesting technique for executing shellcode using built-in .NET capabilities. https://t.co/OITN7kh0oq
#redteam #webinar
linkedin.com
Next week, I will present a live webinar covering an interesting technique for executing shellcode using built-in .NET capabilities. Join us on August 6 to explore some of the tradecraft we developed...
0
2
19
We are going live tonight at 7 PM EST. Tonight's session is about auditing and searching for misconfigured GPOs using C# during a red team exercise. https://t.co/Efv3aYp2in
0
0
3
We are going live tonight at 7 PM EDT. Tonight's episode is about writing your own SOCKS5 proxy that can serve as your complete C2, allowing you to perform all operations remotely. https://t.co/Efv3aYpA7V
1
1
38
How would you describe the world situation in 2025? Three words maximum!
6
0
5
We are going live tonight at 7 PM! Tonight's session is about incorporating sandbox evasion techniques into your malware using C and C#. https://t.co/Efv3aYp2in
0
0
6
The upcoming live session will be presented live from @NorthSec_io this Friday, May 16, 2025, at 1 PM EST. We will be chaining a novel technique in .NET that does not require any RWX memory allocation or external APIs. https://t.co/wHGC8v8NjE
0
0
11
If you are in Athens for @TheOffensiveX. Come say hi during my training or talk.
Offensive X Trainings Are Live From malware analysis to bypassing EDR and breaking AI, these are deep-dive, hands-on sessions run by the pros. Featured Trainings: – Advanced Malware Analysis with Théo Letailleur (@Synacktiv) – 2 Days – Strategic AI Penetration with
1
1
4
You are interested in attending the @HackSpaceCon 2025 conference? I will give away 5 tickets. All the information here:
linkedin.com
🎫 I'm giving away 5 tickets to Hack Space Con 2025! 🎫 Want to win one? It’s simple! Just tell me about your favorite vulnerability in the comments, and I’ll randomly pick 5 winners this Sunday. We...
0
3
4