Kurosh Dabbagh
@_Kudaes_
Followers
1K
Following
909
Media
70
Statuses
2K
nt authority\kurosh https://t.co/MCEI38ndVE https://t.co/w6aiUt7YlZ
Madrid
Joined January 2013
Tangled is a social engineering platform that weaponizes calendar event processing in Outlook and Gmail to deliver spoofed meeting invites that are automatically added to a user's calendar without interaction. https://t.co/vz4ulB2SL3 Technical breakdown:
github.com
Open-source offensive security platform for conducting phishing campaigns that weaponizes iCalendar automatic event processing. - ineesdv/Tangled
2
44
146
Meetings You Didn’t Plan, But We Did In this post, @ineesdv breaks down how calendar event processing in Outlook and Gmail can be abused to deliver spoofed meeting invites that are automatically added to a user's calendar without interaction ➡️Read more: https://t.co/7RApljHair
0
21
19
[RELEASE] As promised, I’m releasing the first blog post in a series. It covers the gaps still present in current stack-based telemetry and how Moonwalking can be extended to evade detection logic and reach “on-exec” memory encryption. Enjoy ;) https://t.co/4Yf28y7cT4
klezvirus.github.io
TL;DR
8
99
312
This Thursday, our colleague @_Kudaes_ will be at @NavajaNegra_AB presenting Activation Context Hijack: a new code execution technique for Windows environments. ➡️ More info: https://t.co/KLCb6lWNDw
0
15
18
Although direct access to disk is not new at all, especially when it comes to forensics, I think this approach could be useful in a number of contexts during a RT engagement. https://t.co/dwXVVUA3b2
github.com
Direct access to NTFS volumes. Contribute to Kudaes/MFTool development by creating an account on GitHub.
2
8
43
I just released MFTool, an NTFS parser that builds an in-memory map of a volume, allowing you to: - Read any file without opening a handle - Get the contents of locked/deleted files (registry hives, pagefile.sys, etc) - Perform fast, in-memory searches across the entire disk 🔗👇
4
43
175
Exciting times. I'm publishing Dittobytes today after presenting it at @OrangeCon_nl ! Dittobytes is a true metamorphic cross-compiler aimed at evasion. Use Dittobytes to compile your malware. Each compilation produces unique, functional shellcode. https://t.co/761G96JDF1
12
97
259
Four months of development and maintenance have yielded considerable results. With the new changes introduced, the old demo was somewhat obsolete, so I decided to upload a new one where you can better see the current improvements to Neo4LDAP. https://t.co/F0vHKFP93w
1
4
5
AvePoint has fixed a vulnerability in DocAve, Perimeter and Compliance Guardian discovered by our researchers @m1ntko and @Calvaruga. This vulnerability can be used to achieve Remote Code Execution (RCE) in affected systems. ➡️ Advisory: https://t.co/bD9hLomlG1
0
8
8
Proactively creating processes with Protected Process Light (PPL) protection will give you more opportunities to abuse these processes. Detailed article: https://t.co/wjihHSarqB
zerosalarium.com
Abusing the Clipup.exe program by using the CreateProcessAsPPL.exe tool to destroy the executable file of the EDRs, Antivirus.
0
25
109
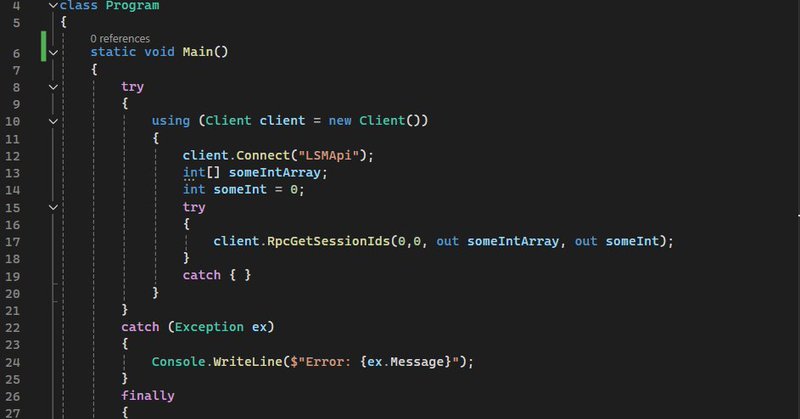
I wanted to find out if you could start the WebClient service remotely, so I ended up digging into it
specterops.io
A walkthrough to answer the question: "Can you start the WebClient service remotely as a low privileged user?"
1
59
124
I remember that I had to do some research online on how to make exploits for vulnerabilities over MS-RPC. With this blog, I hope to fill the gap on the lacking information available online on how to make these yourself. https://t.co/1YLS5ZY4A3
incendium.rocks
Showcasing some different ways to craft exploits for vulnerabilities over MS-RPC
1
53
137
This is so much! 🔥🔥😎 Found two new Potato triggers just today. Not only Potato but can also be used for LPE as remote auth is done which could be relayed to LDAP without Signing enabled. Or relayed to ADCS for a certificate. https://t.co/H83AIxtskn
github.com
Gain insights into MS-RPC implementations that may be vulnerable using an automated approach and make it easy to visualize the data. By following this approach, a security researcher will hopefully...
5
182
580
Who doesn't love a sequel? Part one our series on secure #enclaves for #offensive operations highlighted how enclaves work and how to develop your own. Part two is out now and shares what we discovered while digging into enclave internals: https://t.co/oe9A6Rp4tt
1
19
35
I'm excited to share 𝗥𝘂𝘀𝘁𝗶𝗰𝟲𝟰. A Modern 64-bit 𝗣𝗼𝘀𝗶𝘁𝗶𝗼𝗻-𝗜𝗻𝗱𝗲𝗽𝗲𝗻𝗱𝗲𝗻𝘁 Shellcode Template for 𝗪𝗶𝗻𝗱𝗼𝘄𝘀, written 𝗶𝗻 𝗥𝘂𝘀𝘁! #rustlang #CyberSecurity #redteam
https://t.co/SF87YMJJrZ
github.com
64-bit, position-independent implant template for Windows in Rust. - safedv/Rustic64
2
26
109
Windows 11 24H2 broke a popular malware evasion technique! The Lloyd Labs self-deletion method now fails because of NTFS changes, so I spent time with kernel debugging to figure out why and how to fix it. Full technical breakdown:
7
105
334
Im happy to announce Neo4LDAP — a query and visualization tool focused on Active Directory environments. It combines LDAP syntax with graph-based data analysis in Neo4j, offering an alternative approach to tools like BloodHound. https://t.co/Y2g5wt8jCM 🧵: 1/4
3
28
56
hOw Do I lEaRn MaLwArE StUfF If you're new to malware stuff, and want to learn malware stuff, go to our paper collection. If you read 10% of our malware analysis paper collection (took notes, seriously understood it), you'd be a fuckin' monster. If you know how to code
Malware paper statistic breakdown: Windows malware development papers: 721 papers Malware analysis papers: 12,293 papers Linux malware development papers: 65 papers ICS/SCADA malware papers: 94 papers
39
166
2K
Attacks against AD CS are de rigueur these days, but sometimes a working attack doesn’t work somewhere else, and the inscrutable error messages are no help. Jacques replicated the most infuriating and explains what’s happening under the hood in this post https://t.co/eF5nhHfPuS
1
110
316
I've just released Eclipse, a PoC of what I call Activation Context Hijack. This technique redirects any application to load an arbitray DLL, allowing to inject code into any trusted process. More info available on Github.
github.com
Activation Context Hijack. Contribute to Kudaes/Eclipse development by creating an account on GitHub.
5
85
216