Orange Cyberdefense's SensePost Team
@sensepost
Followers
9K
Following
759
Media
169
Statuses
2K
Work like hell, Share all you know, Abide by your handshake, Have fun. - Dan Geer
The World
Joined May 2010
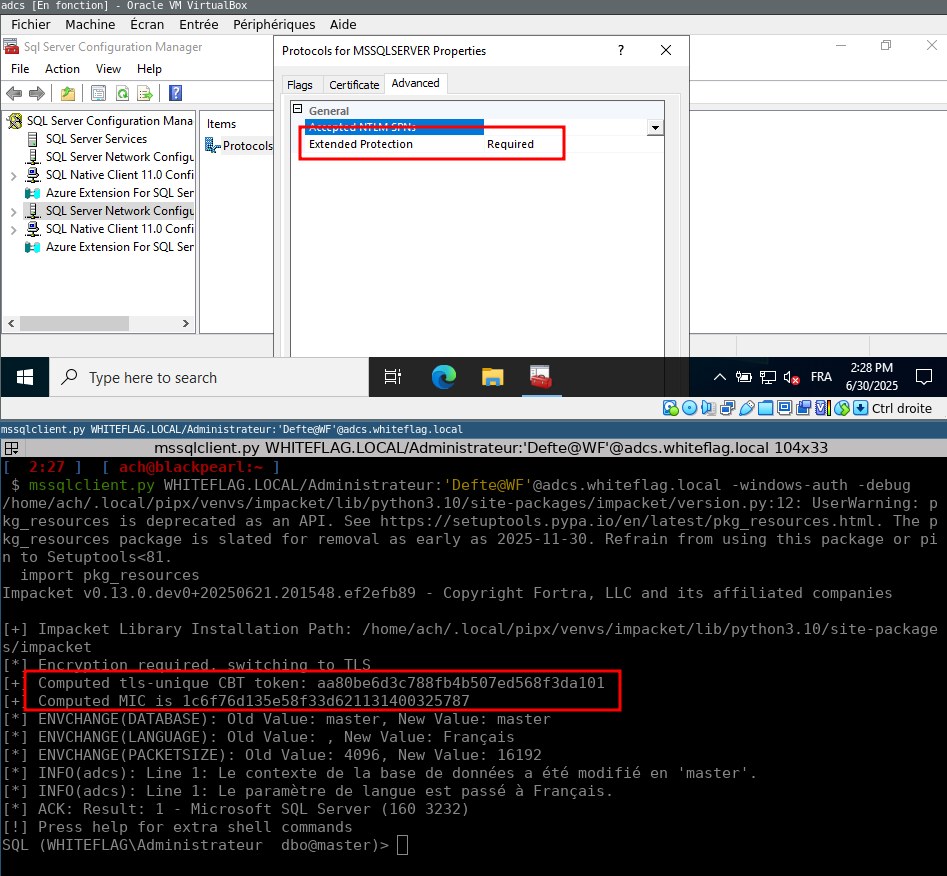
Reverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s Storytime from Aurelien (@Defte_), including instructions for reproducing the test environment yourself. (link below)
3
113
355
After @felmoltor argued about dependency confusion & supply chain attacks & was confused with the feasibility of doing this in 2025, he decided to take a practical approach & create his own tool 📷 to detect Orphan and Misspelled packages 📷:
0
5
11
Did we mention it's all in the cloud and you can get extended lab access and office hours after support . .
Wifi hacking can be a useful tool, but people are out here grinding on WPA2 handshake cracking tutorials & menu driven attack tooling. When @sensepost built the 3rd iteration of our wifi hacking course for @BlackHatEvents - we did it to show what really works & how it works. 1/7
0
1
2
RT @yestinj: Visiting the @sensepost offices today, such nostalgia, and the new office is really nice 🤩
0
1
0
@Defte_ After identifying a mistake relating to NTLMv1 being enabled in the test environment, the blog has been updated with an errata section.
0
0
1
The S is for Security. How to use WinRMS as a solid NTLM relay target, and why it’s less secure than WinRM over HTTP. By @Defte_. Writeup: PR to impacket:. Demo:
1
44
120
RT @leonjza: Whipped together a SOCKS5-over-any-transport feature today for the c2 & implant used in @sensepost purple teaming / emulation….
0
21
0
RT @Hack3rBot: Time to sign up for @BlackHatEvents trainings. I attended @codemachineinc last year, highly recommended! Also if not your ar….
0
1
0
Dropping Teams malware via the browser’s cache - part II of @Defte_'s Browser Cache Smuggling covers his Insomni’hack talk with end to end weaponisation Demo:
0
29
75
GLPI (popular in France & Brazil) versions 9.5.0-10.0.16 allow hijacking sessions of authenticated users remotely. The details & process of discovering the vulnerability is detailed by @GuilhemRioux here:. Tooling:
0
3
14
RT @GuilhemRioux: Glad to publish a blog post on a critical vulnerability I found some months ago on GLPI, that impacts all default install….
github.com
GLPI vulnerabilities checking tool . Contribute to Orange-Cyberdefense/glpwnme development by creating an account on GitHub.
0
44
0
RT @sensepost: Using frida-trace to hook thousands of methods in one go and get clean, readable output for large, obfuscated mobile apps 📲.….
0
23
0