Marcos Díaz
@Calvaruga
Followers
141
Following
858
Media
0
Statuses
90
Tangled is a social engineering platform that weaponizes calendar event processing in Outlook and Gmail to deliver spoofed meeting invites that are automatically added to a user's calendar without interaction. https://t.co/vz4ulB2SL3 Technical breakdown:
github.com
Open-source offensive security platform for conducting phishing campaigns that weaponizes iCalendar automatic event processing. - ineesdv/Tangled
2
42
142
Meetings You Didn’t Plan, But We Did In this post, @ineesdv breaks down how calendar event processing in Outlook and Gmail can be abused to deliver spoofed meeting invites that are automatically added to a user's calendar without interaction ➡️Read more: https://t.co/7RApljHair
0
19
18
Our colleagues @_Kudaes_ & @ineesdv will be at #HackOn2024 presenting an alternative approach to ROP-based sleep obfuscation technique to evade memory scanners. ➡️ Read more: https://t.co/stknNHL5Zd
0
17
33
Enhanced version of secretsdump from #Impacket to dump credentials without touching disk. This feature takes advantage of the WriteDACL privileges held by local administrators to provide temporary read permissions on registry hives. https://t.co/gRtlOdNejE
github.com
This PR allows to remotely extract hashes from the SAM and SECURITY (LSA Secrets and cached credentials) registry hives without touching disk. There is no need to save these registry hives to disk ...
3
127
306
As someone involved in the AWS offsec space, I want to share why I strongly do NOT recommend the HackTricks AWS Red Team Expert course. The author of it is a plagiarist, stealing content from other creators and is directly profiting off of it through sponsorships. A 🧵
7
75
331
🖱Did you know that your wireless mouse can be spoofed to take control of your computer? The @Tarlogic Innovation team has developed #BSAM, the first methodology to audit #Bluetooth devices and avoid situations like that 👇 https://t.co/MaqU7mhKaW
tarlogic.com
Tarlogic has developed a Bluetooth security assessment methodology to help companies protect millions of smart devices
0
10
11
The @NavajaNegra_AB conference is just around the corner! @_Kudaes_ will be on-site to talk about malware development and EDR evasion. ➡️ Read more: https://t.co/zFZgCnNb1d
1
12
26
Watchguard has fixed 4 vulnerabilities in Watchguard EPDR discovered by our researchers @antuache and @Calvaruga. These vulnerabilities can be used to turn-off the defensive capabilities of the product and achieve privilege escalation. ➡️ Advisories: https://t.co/uJGhFsI5VR
0
14
23
In our latest post, @xassiz introduces a new technique to obtain cleartext passwords from MSSQL by abusing linked servers through the ADSI provider. ➡️ Read more: https://t.co/KUDKJiV4KY
1
35
40
Boas Xente! Dende o Barbanza RC queremos acercar o mundo do rugby a maior xente posible polo que este sabado 6 de Maio imos montar un pequeno adestramento e comida posterior. Se algun dia pensaches en probar este marabilloso deporte, este é o teu momento! (1/2)
1
15
16
Have you ever tried exploiting a Spring Boot Actuators RCE but the restart endpoint was disabled? ⬇️ Abuse this behaviour using this #TrickOrThreat by @antuache
0
15
27
Windows Local Privilege Escalation via StorSvc service (writable SYSTEM path DLL search order Hijacking) /cc @antuache @_Kudaes_ ➡️ https://t.co/8XMvewhgFn
3
128
300
💥One shell to HANDLE them all New approach to escalate privileges from a web shell by abusing open token handles. #RedTeam /cc @_Kudaes_ ➡ https://t.co/8KWQw4q5U5
1
36
78
AutoDial(dll)ing Your Way - Lateral Movement and LSASS SSP using AutodialDLL, a new blog post and tool release (DragonCastle) by @TheXC3LL
https://t.co/NbOrI2rskn
7
110
231
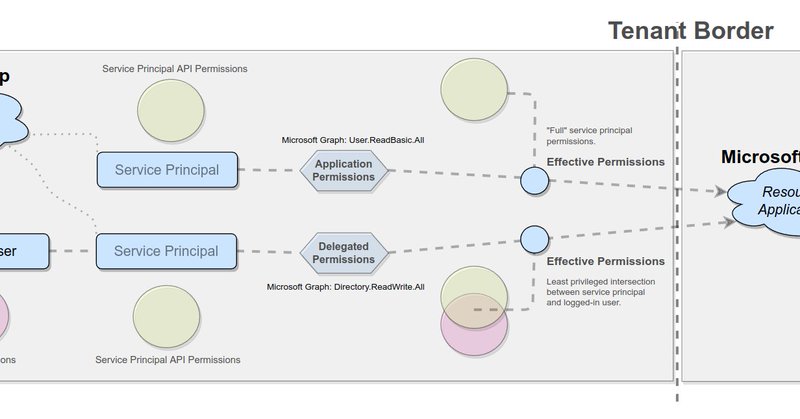
New blog post about Azure AD Principals and access permissions. https://t.co/QKIoerKn8I
csandker.io
This blog post will untangle the question of 'who has access to what' in an Azure Active Directory environment. A PowerShell tool will also be released to automatically enumerate this.
0
32
59
I just discovered that people copy texts from internet into a github book, then ask money and sponsors because of the great effort of doing ctrl + c && ctrl + v. What a trick!
3
2
21
We've extended @nopfor\ntlm_challenger with MSSQL support! This is useful when network segmentation prevents from reaching the SMB port ➡️ https://t.co/8UIOqGtj7i
0
19
25
Minor changes to @ly4k_\Certipy to make it compatible with @AlmondOffSec\PassTheCert. Now you can use both PKINIT and Schannel when dealing with ESC4! Find out more 👇 https://t.co/HCcoDdeZGP
github.com
Hi @ly4k! We've noticed that, when exploiting ESC4, the CT_FLAG_IS_CA flag (present in the default SubCA template) generates a certificate that is not compatible with PassTheCert, which use...
0
18
33
🦥 Everyone learned to run pip install colorama to exploit Atlassian Confluence RCE (CVE-2022-26134), so let’s see how the vulnerability works under the hood. Here we show our simplified payload which demonstrates a workflow inside the vulnerable code ⤵️
1
88
257
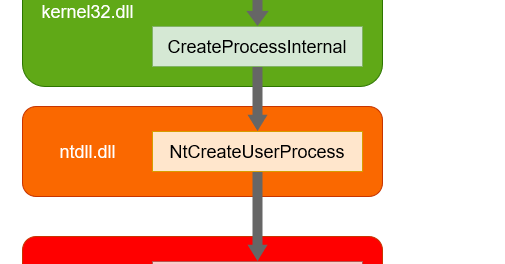
Finally developed a minimal PoC for NtCreateUserProcess(). Here's something I'd like to share about it. #redteam #maldeve #infosec
https://t.co/vpN4lN41Xd
captmeelo.com
Here's my journey on how I developed a 'minimal' PoC to make NtCreateUserProcess work.
19
193
512