klez
@KlezVirus
Followers
8K
Following
6K
Media
109
Statuses
1K
Independent Cyber Security Researcher - Opinions are my own
Italy
Joined December 2014
[RELEASE] After a little wait, I'm happy to present SilentMoonwalk, a PoC implementation of a TRUE call stack spoofer, result of a joint research on an original technique developed by namazso, done with my friends @trickster012 and @waldoirc. Enjoy! ;) https://t.co/C5QBzNawza
github.com
PoC Implementation of a fully dynamic call stack spoofer - klezVirus/SilentMoonwalk
14
238
587
Forgot to put the repo in the blog, my bad https://t.co/QD5eX4wqzP
github.com
CVE-2025-59501 POC code. Contribute to garrettfoster13/CVE-2025-59501 development by creating an account on GitHub.
SCCM’s AdminService uses Entra tokens without confirming the UPN exists in AD. A crafted synced UPN can let an attacker impersonate the site server. Microsoft now requires on-prem SID matching (CVE-2025-59501). Great deep dive by @unsigned_sh0rt! https://t.co/FGAHfaXHsY
0
30
81
Section 10/12 of the UDRL/Sleepmask course is finally complete. By far the most complicated / longest to write. Super excited to finish this out and get it into people's hands!
4
22
140
So far, I have spent sleepless months writing custom libs and loaders for my red teaming assessments and its still going on =) After going through all this, I have decided to write a blog about some mistakes I made and why you shouldn't make them. Finally, I would like to
3
24
212
@nickeverdox There are other usable instructions to do that, like vpgather/vpgatherqq ;) https://t.co/o3r3l74qjy I've mentioned the "rep movs" there too, but I'm not sure you actually need ERMSB? Although I've explicitly called out vpgather is usable for EPT/#VE later, in PagedOut 6 zine.
Outrageous technique: barely legal use of x86 CPU instruction enables you to catch and 𝗰𝗮𝗻𝗰𝗲𝗹 impeding pagefault before it actually happens. ③: catch PAGE_GUARD or invalid access ⓪: do previously illegal reads at high IRQL, safely #vpgatherqq #vpscatterqq scatter/gather
1
4
20
Today I am releasing a new blog on Windows on ARM! It comes from the perspective of one, like myself, who comes from an x86 background and is new, but, interested in Windows on ARM! ELs, OS & hypervisor behavior (with VBS), virtual memory, paging, & more! https://t.co/jUHls4wupu
connormcgarr.github.io
Analysis of Windows under ARM64: exception/privilege model, virtual memory mechanics, and OS behavior under VHE
2
77
293
Welcome back Hasherezade (@hasherezade) to our RE//verse review board! Hasherezade, a malware analyst and software engineer from Poland, is known for her impactful work in cybersecurity and reverse engineering. @hasherezade has created several open source tools including PE-bear,
9
32
378
Today I am happy to release a new blog post about Pointer Authentication (PAC) on Windows ARM64! This post takes a look at the Windows implementation of PAC in both user-mode and kernel-mode. I must say, I have REALLY been enjoying Windows on ARM!! https://t.co/isnItJ0nb3
preludesecurity.com
Explore how Windows implements Pointer Authentication (PAC) on ARM64—covering bootloader setup, per-process keys, HyperGuard, and memory-safety defenses.
8
64
211
💣 We caught @ycombinator–backed @gecko_sec stealing two of our CVEs, one on @ollama , one on @Gradio. They copied our PoCs, claimed CVE IDs, and even back-dated their blog posts. Here’s the full story 👇
26
130
856
[Crystal Kit] Evasion kit for Cobalt Strike. https://t.co/RYlbXGn1bQ
github.com
Evasion kit for Cobalt Strike. Contribute to rasta-mouse/Crystal-Kit development by creating an account on GitHub.
8
87
331
By exploiting the antivirus's clone service technique and hijacking libraries via the Cryptographic Provider, the IAmAntimalware tool can inject code into processes that are whitelisted and protected by #antimalware. #itsecurity #cybersecurity
https://t.co/sltel6v1Ci
zerosalarium.com
IAmAntimalware employs new red team techniques by cloning services of Antivirus. Allow inject code into processes whitelisted, protected by Antivirus
1
12
50
I’ll be teaching how EDR REALLY works this Friday at BSIDES NOVA https://t.co/G6AeYHxWf2. It’ll be a medium level course where we analyze malware and its telemetry found in EDR, then try to build hunts around it. Great for attackers and defenders. Hope to see you there!
0
7
42
Close your eyes and ✨imagine: From a low-integrity process (from LPAC even), you can inject your data anywhere you want: privileged tasks, PPL/protected processes, the OS kernel itself, and VTL1 trustlets. Now open your eyes. It is not hypothetical. It is the reality. Page 33.
https://t.co/o4CGqi5qR0 ← we've just released Paged Out! zine Issue #7
https://t.co/ZEuR7WtUAL ← direct link https://t.co/DFuGBWFb4D ← prints for zine collectors https://t.co/8VN5hGyEux ← issue wallpaper Enjoy! Please please please RT to spread the news - thank you!
5
8
82
Lateral movement getting blocked by traditional methods? @werdhaihai just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code.
specterops.io
DCOM lateral movement BOF using Windows Installer (MSI) Custom Action Server - install ODBC drivers to load and execute DLLs
1
116
284
You got access to vsphere and want to compromise the Windows hosts running on that ESX? 💡 1) Create a clone into a new template of the target VM 2) Download the VMDK file of the template from the storage 3) Parse it with Volumiser, extract SAM/SYSTEM/SECURITY (1/3)
7
107
490
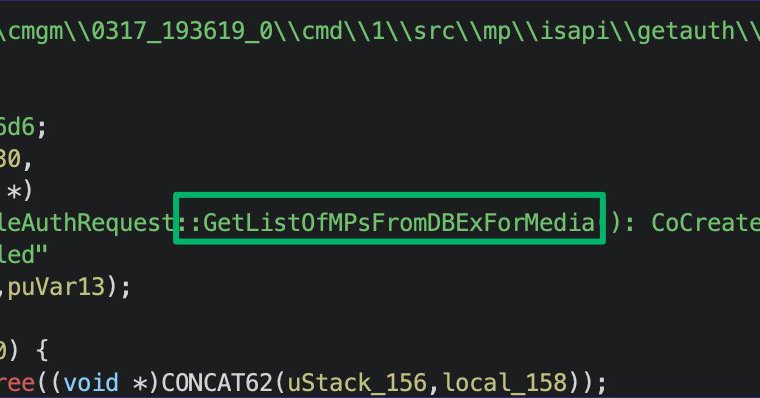
Added CRED-8 to Misconfiguration Manager, which is @unsigned_sh0rt's MP relay to dump machine policy secrets. MM link: https://t.co/yMNHpWeb2z Blog link:
specterops.io
Network Access Account, Task Sequence, and Collection Settings policies can be recovered from SCCM by relaying a remote management point site system to the site database server.
1
24
84
Introducing Wyrm, currently in pre-release - a bit of a hobby project which I am working towards v1.0 for, a Red Team C2 framework which one day will hopefully rival Cobalt Strike, Sliver, etc in terms of capability. Come check it out here! https://t.co/DDkEJfwnta
#redteam
11
56
244
In addition to this, we've added a new plugin-based and extensible stage 1 framework we've dubbed the Stager Kit -
0
5
13
Excited to present with @breakfix at #BHEU @BlackHatEvents where we'll be sharing our research on attacking System Center Operations Manager! @SpecterOps
3
19
79