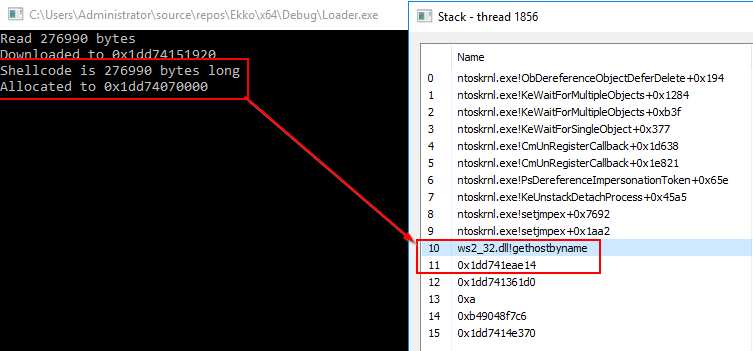
hasherezade
@hasherezade
Followers
89K
Following
24K
Media
1K
Statuses
24K
Programmer, #malware analyst. Author of #PEbear, #PEsieve, #TinyTracer. Private account. All opinions expressed here are mine only (not of my employer etc)
Poland
Joined July 2013
My new blog for Check Point Research - check it out! 💙 // #ProcessInjection : #WaitingThreadHijacking.
Thread Execution Hijacking is one of the well-known methods that can be used to run implanted code. In this blog we introduce a new injection method, that is based on this classic technique, but much stealthier - Waiting Thread Hijacking. Read More :
13
132
440
RT @netspooky: Cleaning up the decompilation of a firmware binary can be such a meditative activity. Delicately defining data, fixing misid….
0
4
0
RT @YungBinary: Seeing a (potential new?) python-based backdoor we're tracking as #PyNightshade for the second time delivered via #ClickFix….
0
27
0
RT @Mandiant: CORNFLAKE.V3 malware spotted in an access-as-a-service operation using the ClickFix technique. 🥣. UNC5518 uses fake CAPTCHA p….
0
39
0
RT @Ryan_Daigler: The covert narcissist’s pattern often begins when they encounter someone they envy or feel threatened by. Their first mov….
0
63
0
RT @RecordedFuture: The Lumma infostealer isn’t just #malware, it’s an ecosystem. Our latest Insikt research reveals how affiliates use new….
0
15
0
RT @Securityinbits: There are plenty of malware‑analysis tools - but pe‑sieve (@hasherezade) + YARA Forge (@cyb3rops) is one of the sharpes….
0
48
0
RT @Myrtus0x0: Prepare yourself for some deep lore; what conti malware family does bumblebee have massive overlap with.
0
6
0
RT @thomasrinsma: You can now read my WASM->JS escape write-up online. Full PoC is included at the end of the article. .
0
35
0
RT @vmray: 🚨Alert: Internet Archive abused as hosting service for stealthy malware delivery. 🔍This delivery chain is another example of leg….
0
51
0
RT @Mandiant: The 12th Annual Flare-On Challenge kicks off Sept 26 at 8PM EST!. Reverse engineering pros, from Windows to Web3 (with a YARA….
0
76
0
RT @steventseeley: As it turns out, @orange_8361 and I have more in common than I had thought! If you love old school PHP quirks and CTF tr….
0
61
0
RT @chompie1337: I've been asked countless times how to learn VR & xdev. The answer is always: "do something you think is cool". It's hard….
github.com
Binary Exploitation Phrack CTF Challenge. Contribute to xforcered/PhrackCTF development by creating an account on GitHub.
0
126
0
RT @7hesage: Hey there! In our new research, I analyzed the details of in the wild privilege escalation vulnerability in clfs.sys. You can….
bi.zone
We look into the clfs.sys driver vulnerability that allows attackers to escalate privileges within the operating system
0
19
0
RT @b1ack0wl: the article I wrote for @phrack is online!. thanks to @richinseattle for encouraging me to submit an article and to @netspook….
0
48
0
RT @allthingsida: Here's a quick introduction video about the new IDA Domain API. @HexRaysSA .
0
22
0